Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

Google just unveiled it's biggest search product in recent memory, except this time the search giant is looking to take over the world of virtual objects.

For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.
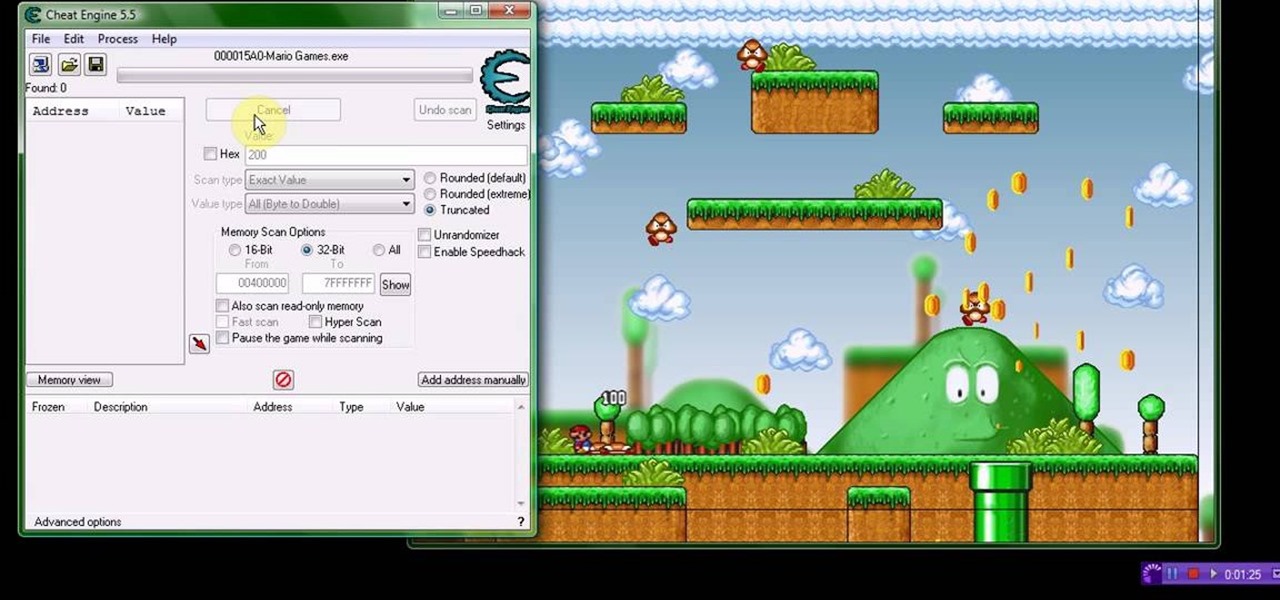
Mario hacks, cheats, glitches. How to play and hack the flash game Mario Games. Watch this video tutorial to learn how to hack Mario Games with Cheat Engine 5.5 (09/30/09). Download Cheat Engine.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...
Before you can work in MS Access 2010, you'll need to learn how to work with it. See how to navigate the Ribbon interface when working in Microsoft Access 2010 with this guide. Whether you're new to Microsoft's popular database management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Backstage view in your own Acces...

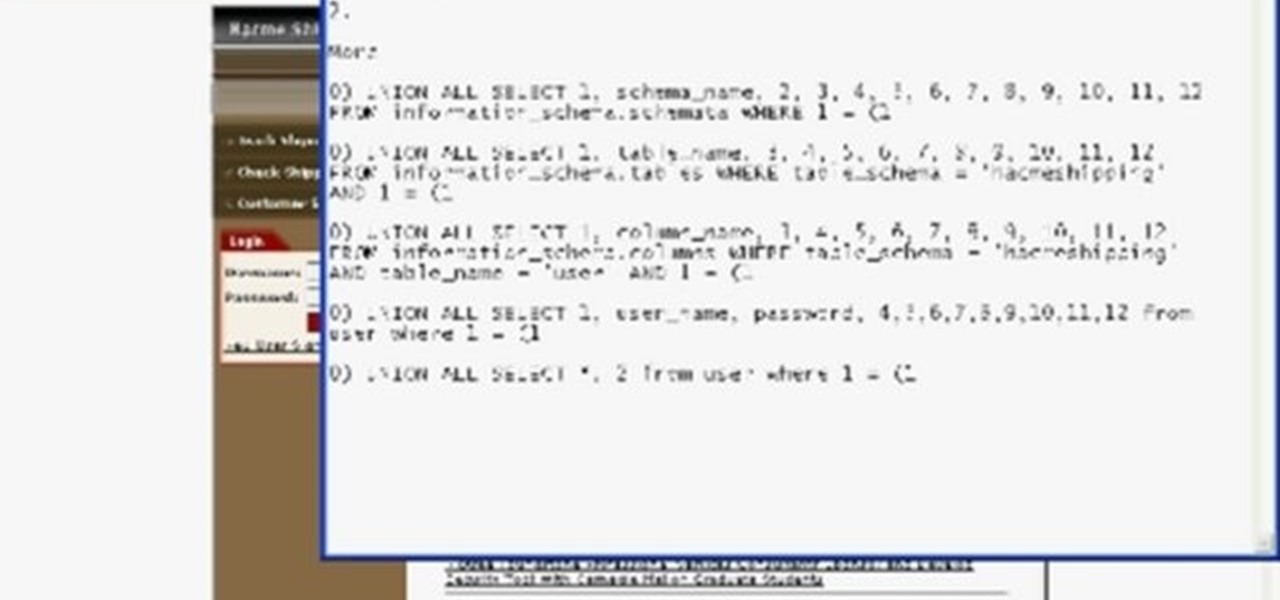
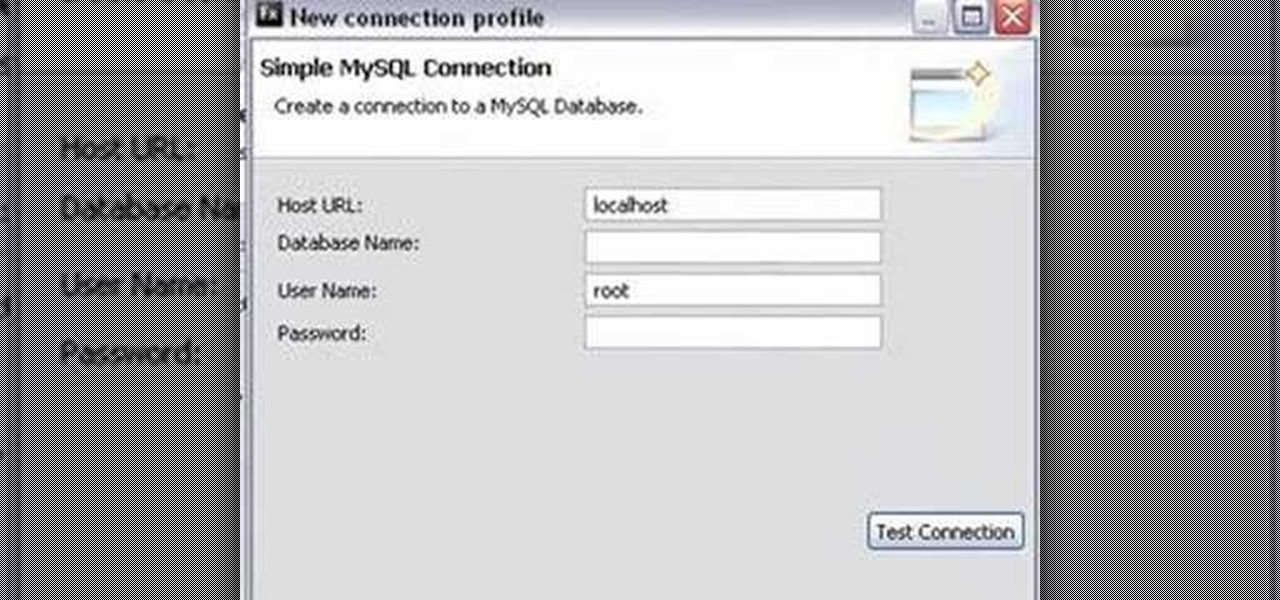
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

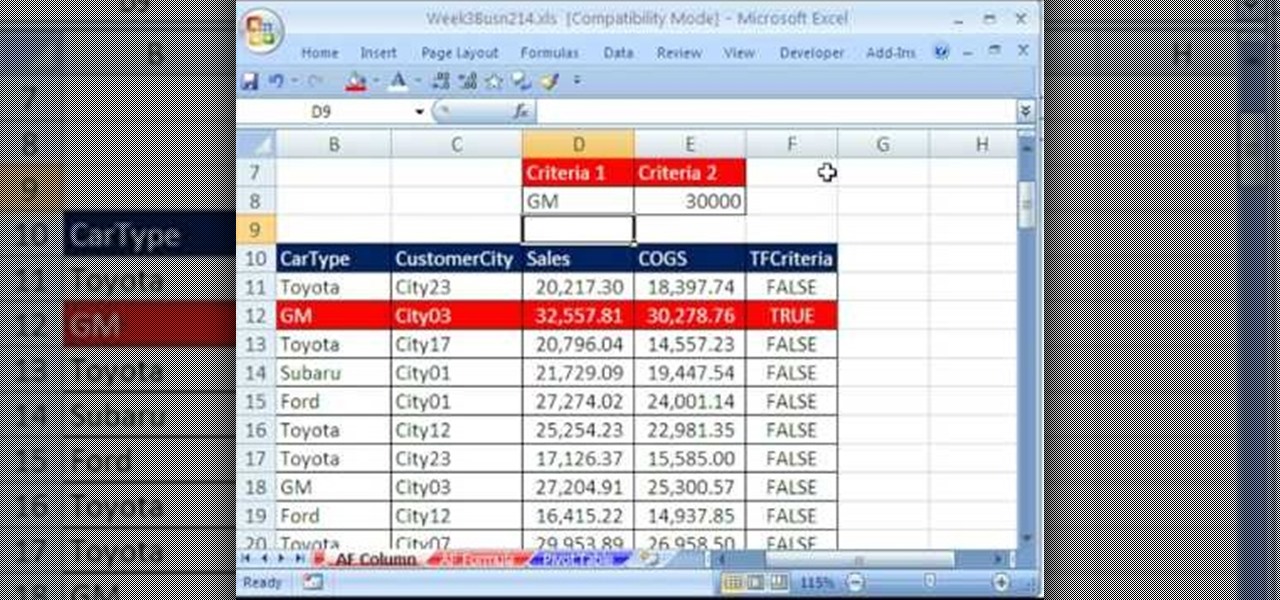
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 20th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to summarize survey data with a pivot table (grouping & report filter), COUNTIFS function (4 criteria), SUMPRODUCTS formula, SUMPRODUCTS & TEXT functions and DCOUNT database function.

Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 19th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about using Advanced Filter to extract data from an Excel List/Table/Database. See these 7 Advanced Filter examples:

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 244th installment in their series of digital spreadsheet magic tricks, you'll learn how to use advanced filtering to extract records from a database (table or list) based on 1 criterion (criteria) and place reesults on a new sheet worksheet.

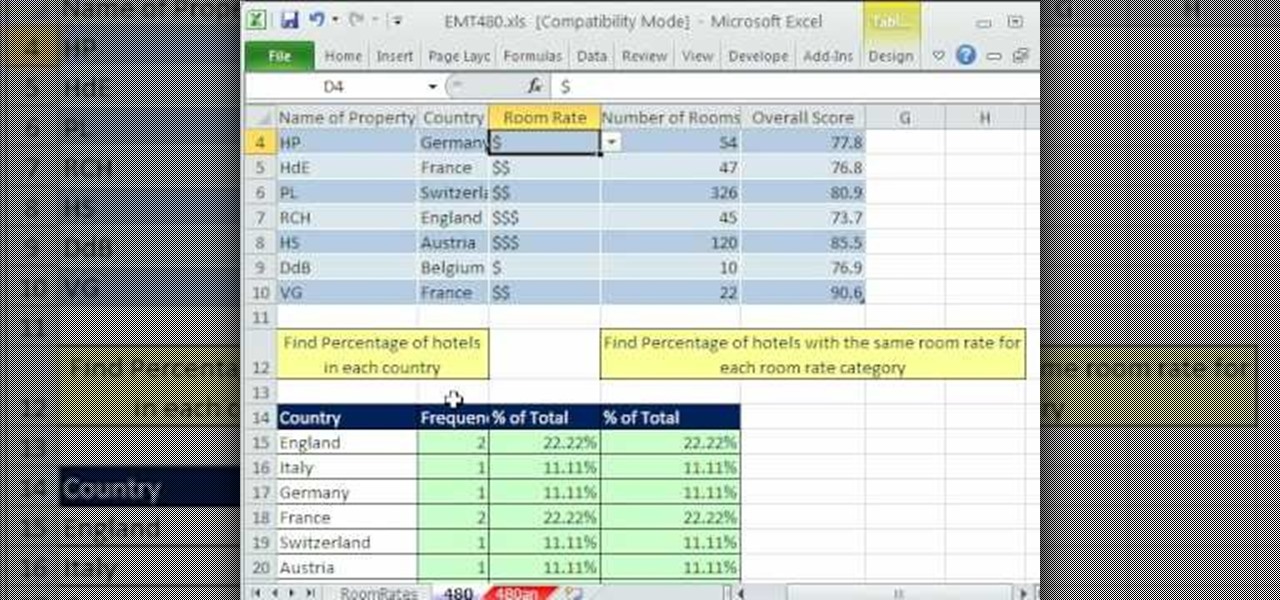
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 480th installment in their series of digital spreadsheet magic tricks, you'll learn how to calculate a percentage of total from a database data set when the variable of interest is text (word). This is accomplished with recourse to the COUNTIF, SUM & COUNTA functions.

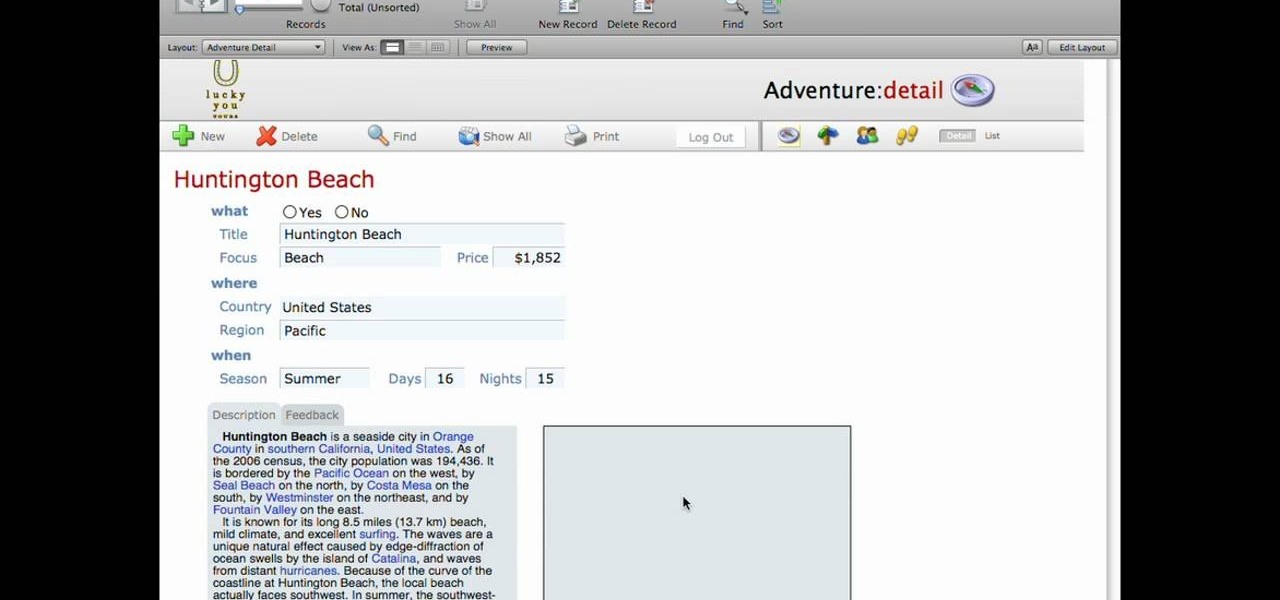
This lynda.com video tutorial shows how to use container fields with FileMaker Pro 10. When you want to create fields in FileMaker database you have the choice on what kind of fields you want to make. Many general fields are self explanatory like text, date etc., but there is a special kind of field called the container field. FileMaker Pro container field is a versatile data type in that it can store any kind of binary data. Container fields can be used to hold binary data in four broad clas...

In this four-part video, learn how to create a CMS with PHP and MYSQL. The basics of a simple CMS are split up in the following four parts:

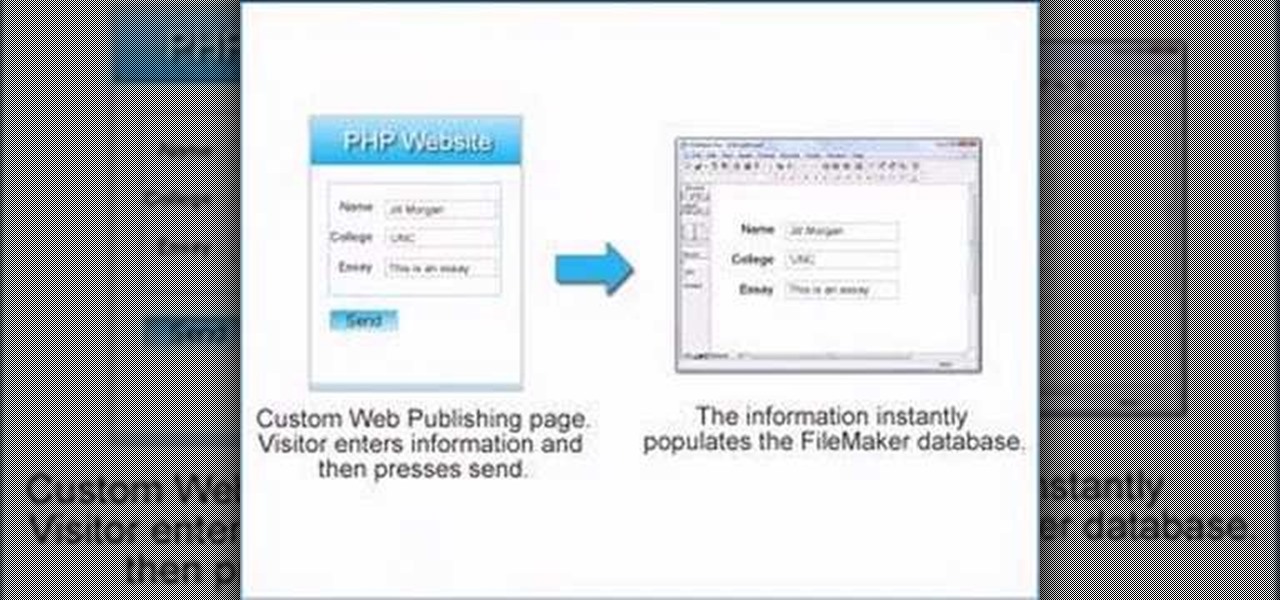
This tutorial demonstrates how to create what is called a complete client-server web application which consist of a Web Application, PHP, and MySQL. The tutorial shows how to automatically generate the PHP necessary to talk to a MySQL database using Adobe Flex Builder 3.

This tutorial on the companion Tech Ease for Mac site shows you how to use Inspiredata to collect, organize, and visualize data using several types of diagrams supported by the program. The movies were recorded on a Mac, but Inspiredata is a cross-platform program so the steps shown should work on the Windows version of the program as well. Inspiredata works like a database system that allows you to add notes and more.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

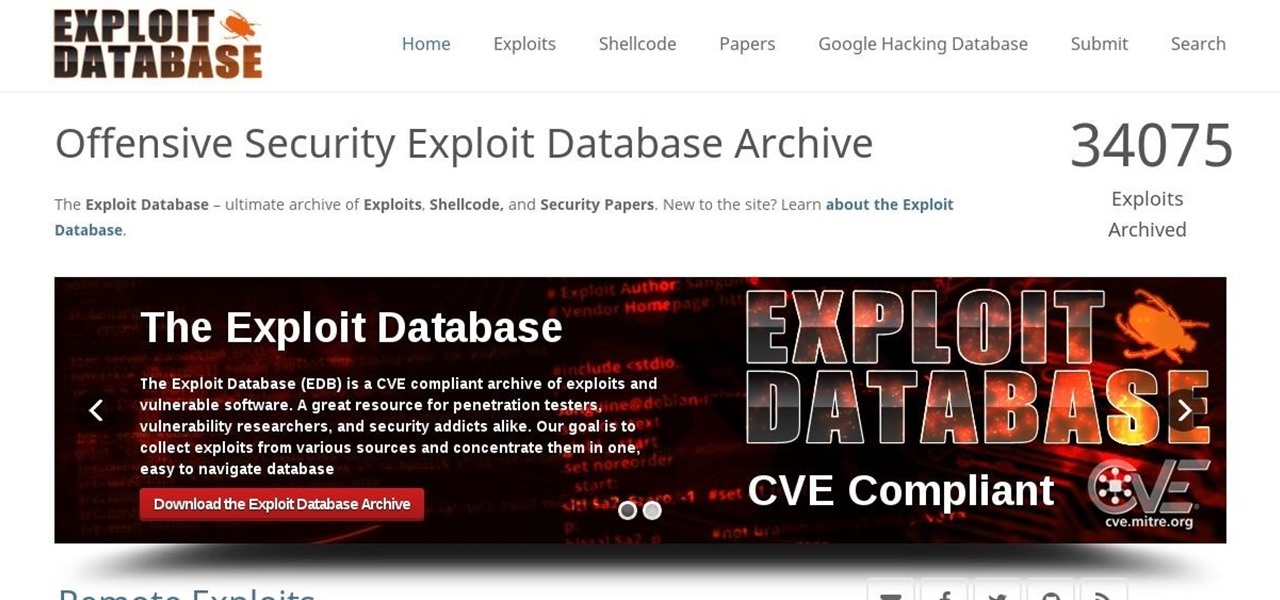
Hello everyone! Hope everyone having good day!! I wanted to share an easy way to locate an appropriate exploit from the EDB, get it compiled, and run it all from inside the terminal.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

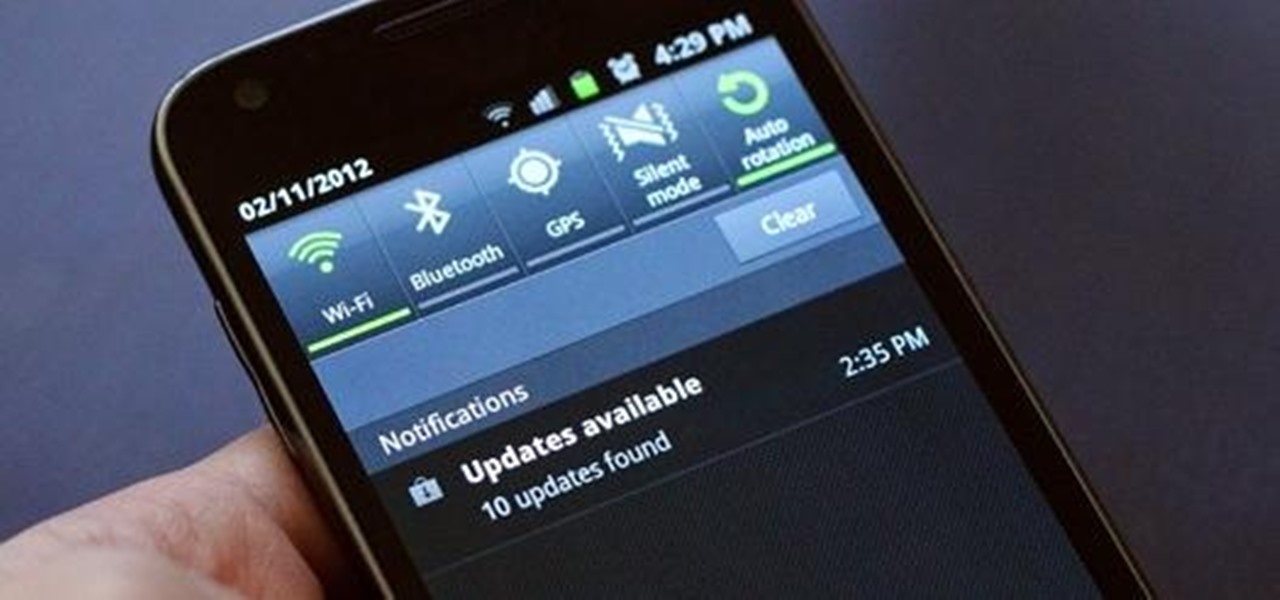
With the Google Play store on your Android device, it's a relatively easy process to check all of your application updates. All you have to do is launch the Market app, go to the My Apps section, and from there you'll be able to see all of the available updates for your applications, which should be positioned at the top of the list. The problem with this process is that many times, you'll go days or weeks and quite possibly even months without checking the Google Play application market, lea...

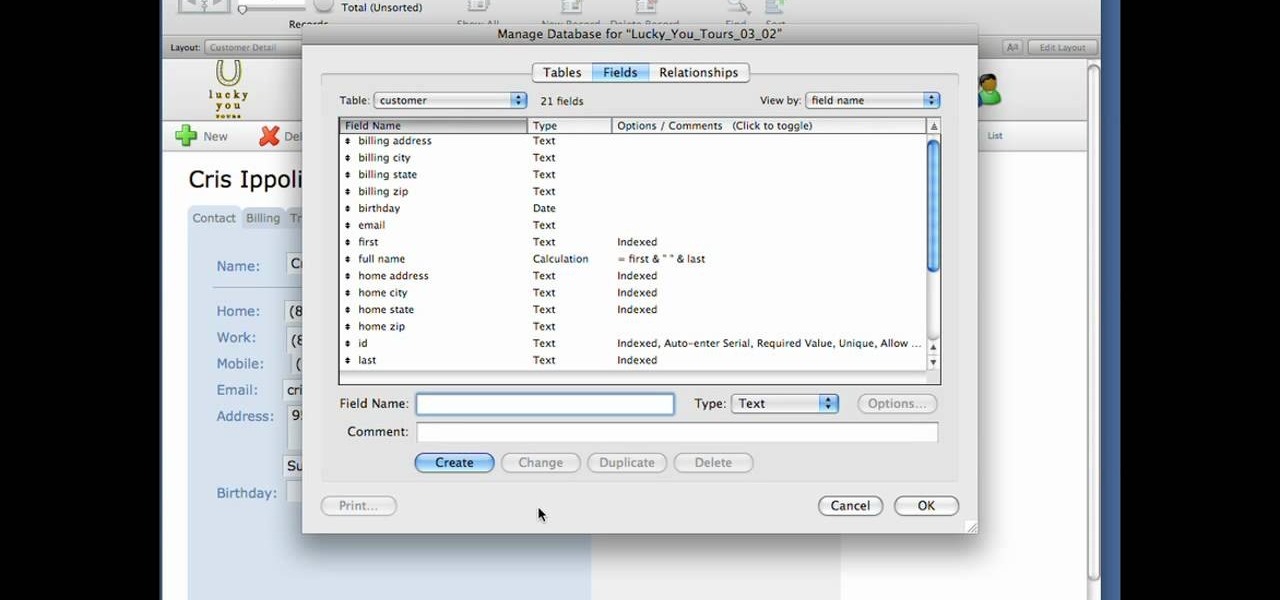
If your into data based business,then this one's for you. Text field's are very much important while making a data based solution in FileMaker Pro 10.You can go to file menu>manage>database and there is the field's tab. Text field is used for storing text and no other such use. Text field's can hold up to 2GB of information. It can help to store raw data and formatting information, i.e., color,point size as well as type face.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Amazon is currently offering over $80 in free Android apps in the Amazon Appstore, but only for Friday and Saturday, so make sure to grab them quick before they all go back to normal price. Highlights include the Fleksy Keyboard (normally $3.99), Oxford Dictionary of English with Audio (normally $24.99), and EasyTether (normally $9.99).

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

FileMaker hosting and the top two reasons for hosting a FileMaker database are covered in this two part series. The second series is a complete step-by step tutorial for setting up your database for remote hosting.