With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

Working with Oracle, odds are you may, on occasion, need to build an Oracle database from MySQL. Happily, this DreamCoder tutorial will walk you, step by step, through the process. To learn how to build an Oracle database from MySQL data, take a look!

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

This video series come straight from Google. It's about their new web-based product called Google Voice, which provides you with one phone number for all of your phones (landline, cell phone, etc.), giving you full online control of your telephone experience. Google Voice also allows you to make free domestic calls anywhere in the United States and Canada, gives you a cool voicemail account that's just like an email account, and many enhanced calling features.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

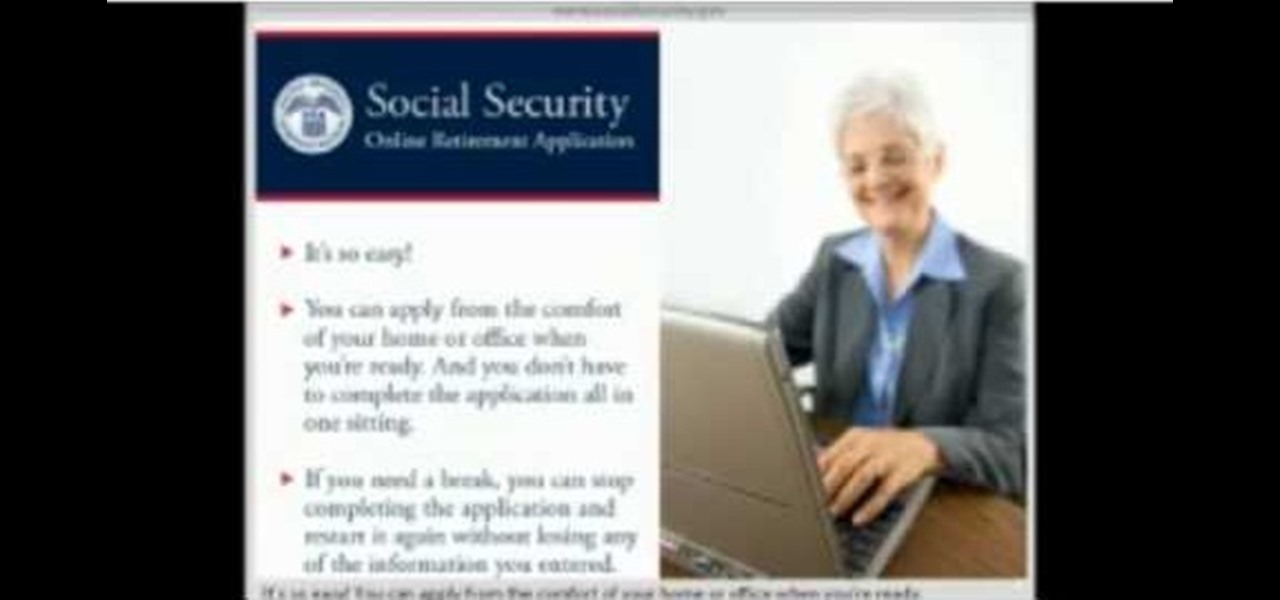
When you decide its time to retire, you will most likely need to cash in your Social Security benefits. In this official two part tutorial, presented by the American Social Secuity Administration, learn exactly how to use their website and apply online. Applying online is very easy, and takes a lot less time than applying in person. By applying online for social security, you will bypass all of the long lines and waiting that usually happens in one of the offices. Plus, you won't ever have to...

In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight.

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

If you're new to DreamCoder for Oracle, one of the first things you may want to know how to do is to monitor a remote Oracle database. Happily, this tutorial will walk you, step by step, through the process. To learn how to monitor a given Oracle database remotely via DreamCoder for Oracle, take a look!

One of the coolest parts of DC Universe Online is it's tremendously complex super hero character creation system. The system i pretty daunting at first, but this video will guide you through making an awesome character that will be the envy of your guildmates online.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

It's time to boldly go where no man has gone before! This video walks you through the first few minutes of Star Trek Online, including how to customize both your character and ship, and a quick rundown on hand to hand combat in the game.

If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Fighting in space is one of the aspects of Star Trek Online, and how you fight will depend on what strategy and tactics you employ. This tutorial goes over a few options and tricks to help you fight your best as a ship.

Space combat is one of the major aspects of Star Trek Online. This video walks you through one of the introductory missions of the game, and shows you how to use your ship to fight, pick up passengers and even fight the Borg!

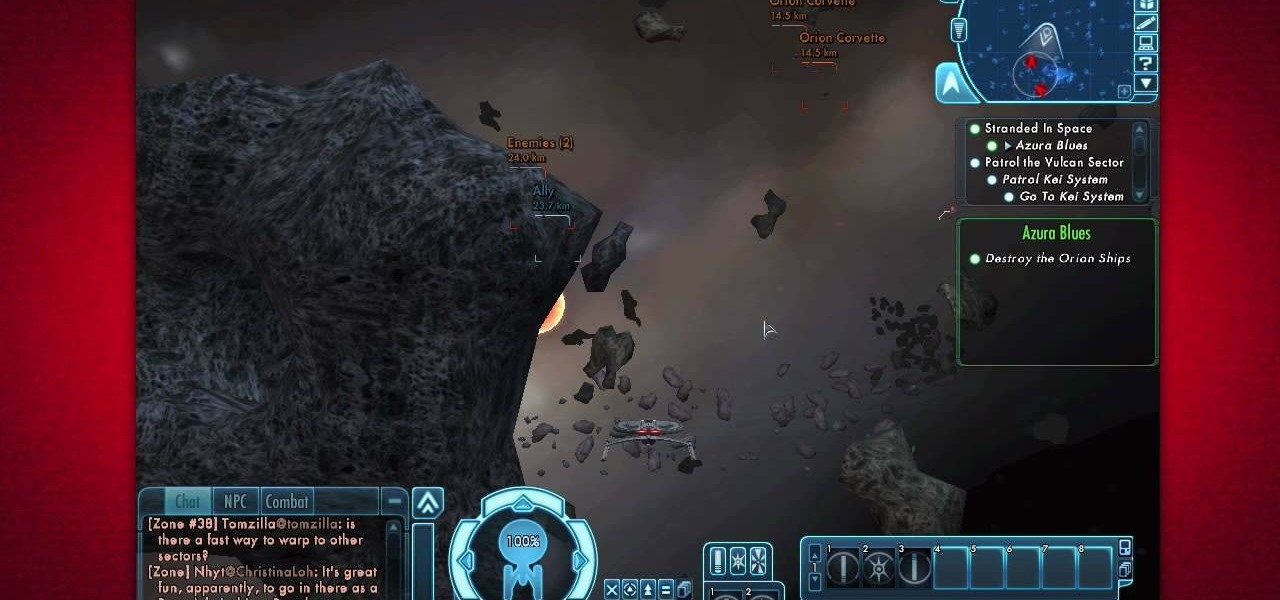
Mining is one of the best ways to earn resources when you play EVE Online. This tutorial includes everything you need to know in order to profit from mining - all you need is a ship and a mining laser!

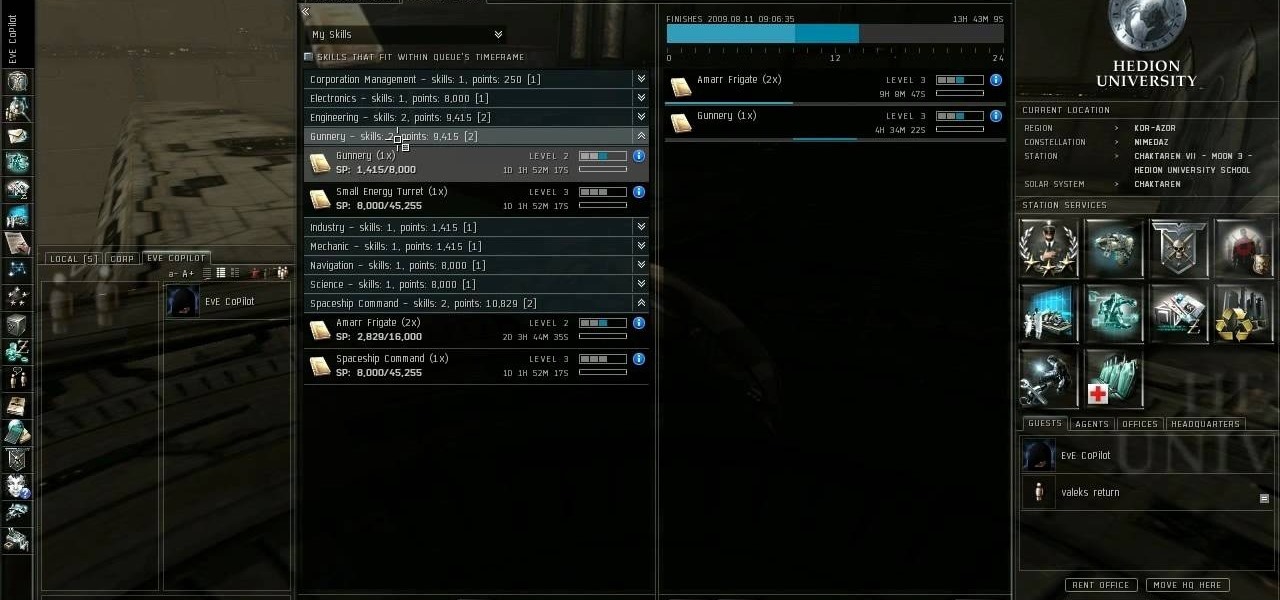
Make sure your character progresses the way you want! This tutorial explains how character attributes and skill training work within EVE Online so you can maximize your character's potential in the game. This tutorial also explains how to navigate the character sheet function. Always be learning at least one skill!

Are you passionate about both Star Trek and Apple products? It's indeed possible to run Star Trek Online on an Apple Mac! This shows you how to download two separate mods that will allow you to play Star Trek Online on your Mac.

Have some last minute edits to make to your photos before you publish them online? Don't have time to download and install software to your computer? This video guide has five free online photo editing services to share. For detailed instructions, and to get started editing your own digital images online, watch this free video tutorial.

This is a great video series from Yanik Chauvin demonstrating how to use Photoshop Express online for free. This great tool is a wonderful resource for those who can't afford Photoshop but still need to do basic photo editing.

This tutorial shows you how to download and use old roll playing games like those from an NES OR SNES to learn languages online. Make sure to watch the second video or you won't get very far.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.