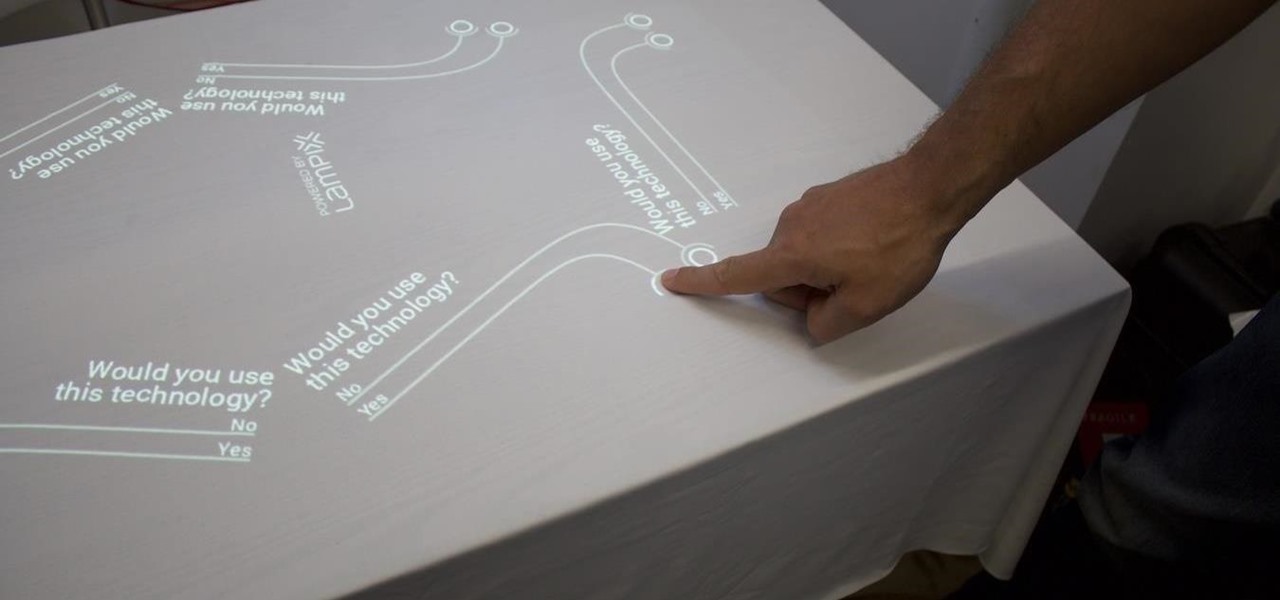
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates how to use color as value in the art of portrait painting.

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates how to do an underpainting for portrait painting.

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates what is needed in preparation for portrait painting.

If you're a small business operator and AT&T is your carrier, you'll want to take advantage of the AT&T Online Account Management portal for small business customers. This video shows how to request an online registration code (required to register your account), how to use it to register your account, and how to set up your username and password.

Uh oh, you've forgotten your AT&T Online Account Management password! No worries, this simple guide shows you how to regain access to the site and reset a new password. Your AT&T Online Account Management portal is vital to keeping your information up to date, so make sure you know how to NOT get locked out.

If you want to tool around in the user interface of Star Trek Online and modify your client, this video shows you how. Do note that Cryptic doesn't support modding, and it could break your system. But if you want to alter the mouse pointer or your camera point of view, here's how!

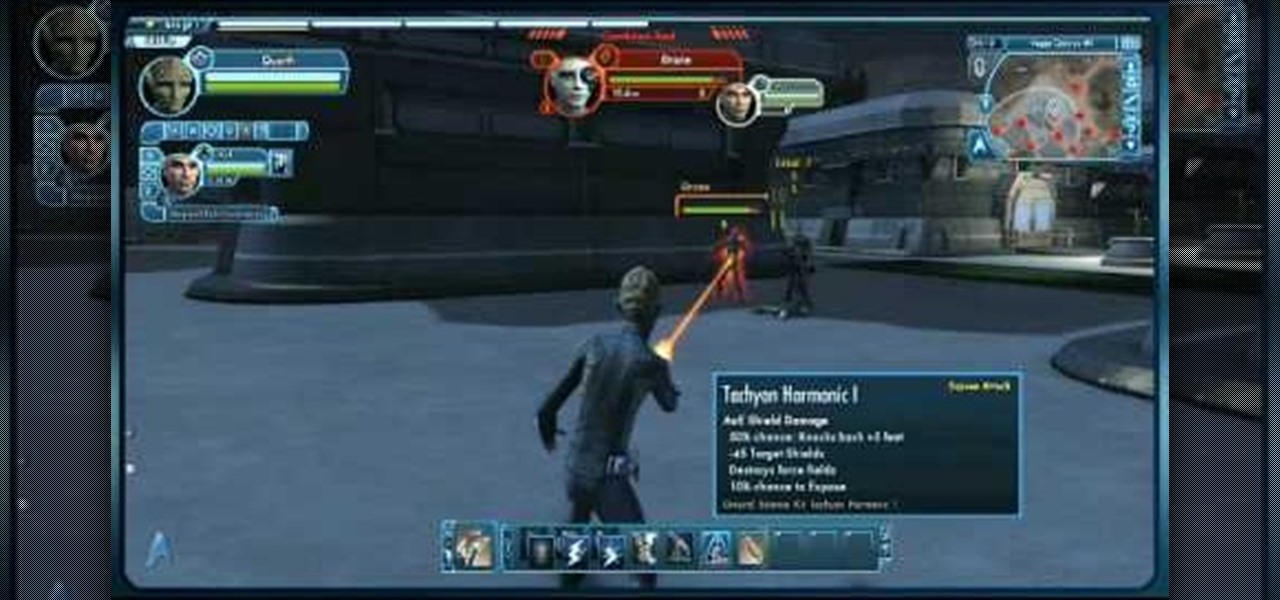
Kits are something your character might come across while playing Star Trek Online - special items which will augment or improve your character's specific skill set. This short video explains what kits do and how you find and use them.

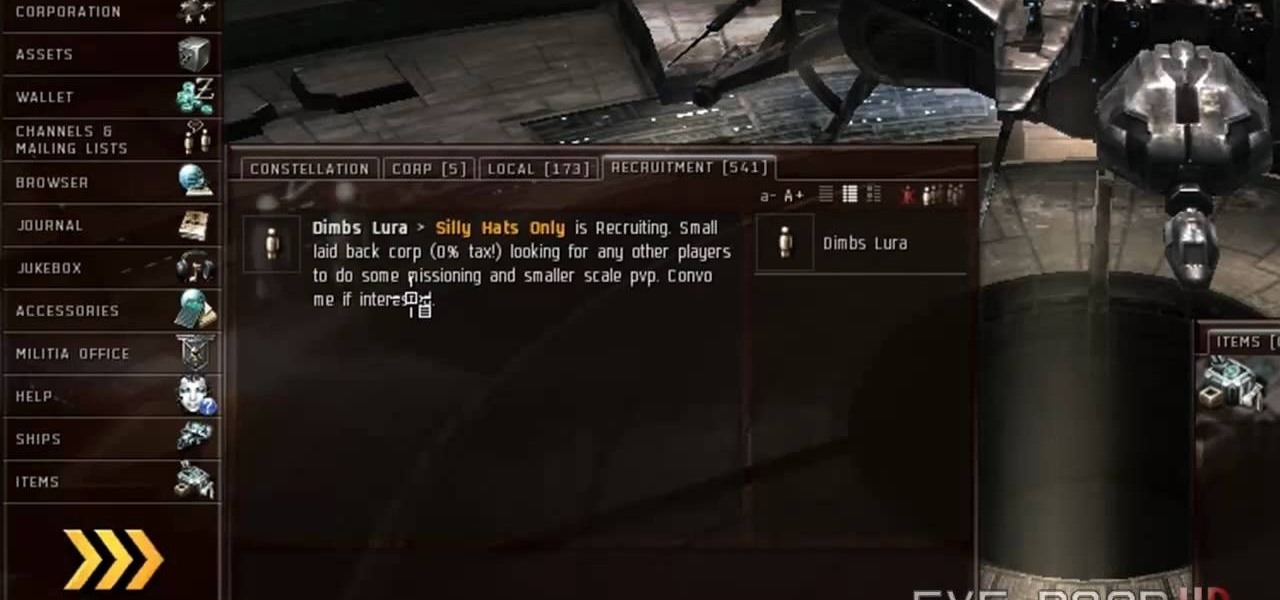
Part of the fun of an online game is being able to chat with your friends! This tutorial goes over how you can use the in-game chat system to join a chat channel. It also gives you a few channels useful for everyone to join, especially new players. Or create your own channel. Avoid pirate corporations!

Ever wanted to find out who stole the cookie from the cookie jar? Take a page from crime scene investigators and get the proof you need.

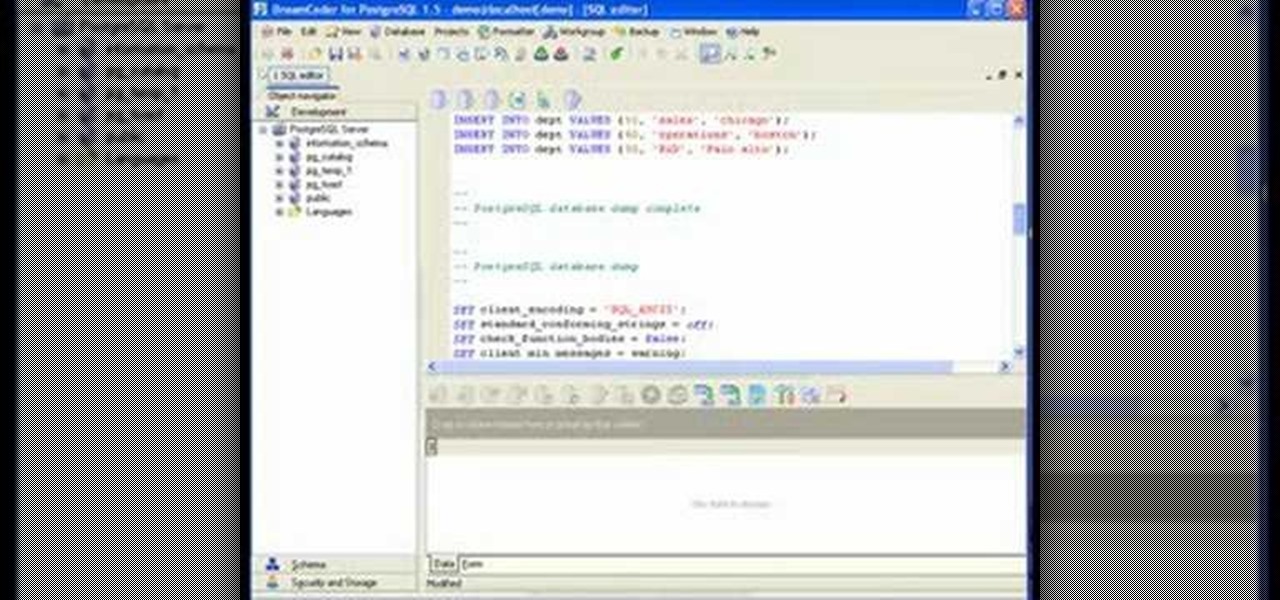
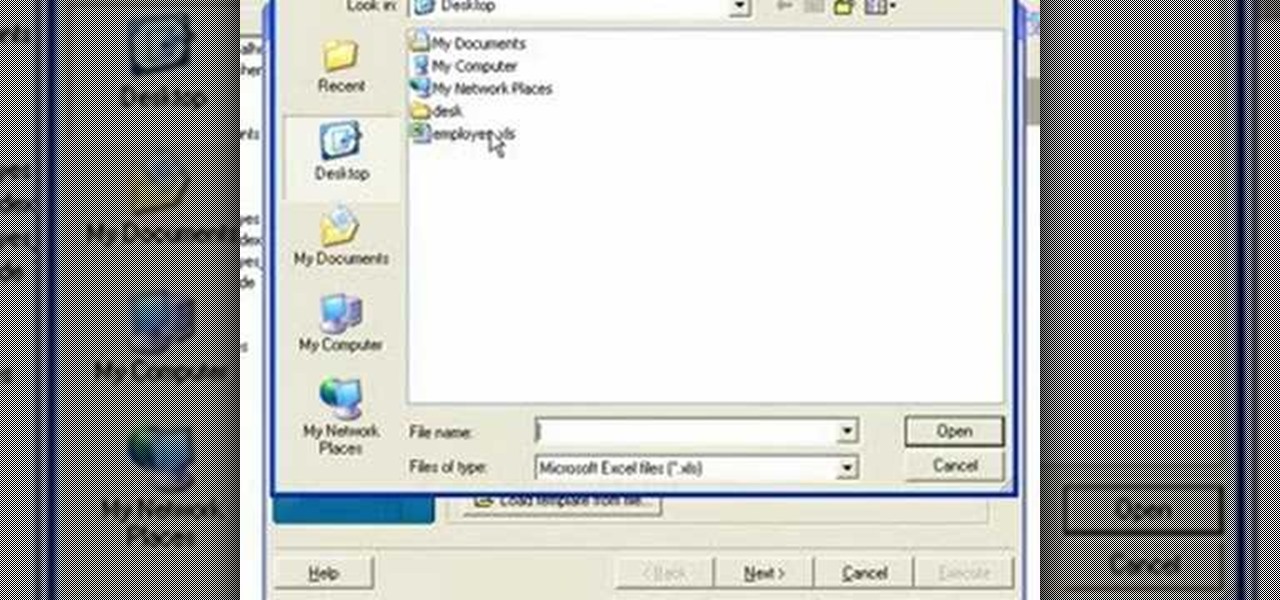
If you're new to DreamCoder for PostgreSQL, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your PostgreSQL databases with ease. For step by step instructions, consult this how-to.

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is how to import data to a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. Take a look!

This MS Office software tutorial gives tips and tricks on integration between Access and Outlook. Access is Microsoft's database software and Outlook is the email software. So if you need to work with your database and email at the same time, check out this tutorial on integrating Access 2007 with Outlook 2007.

SQLite is a small C library that implements a self-contained, embeddable, zero-configuration SQL database engine. SQLite implements a large subset of SQL-92 and stores a complete database in a single disk file. The library footprint is less than 250 KB making is suitable for use in embedded devices and applications where memory space is scarce.

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

AT&T Online Account Management portal for small business customers is a great place to manage a sea of information, BUT, it won't do you any good unless you know how to log in. This clear how-to shows you how to enter your AT&T username and password so you can manage your account online.

MetaRL is a site you can sign up with that will let you accrue points that you can cash in for free online currency in your favorite online game. It's a very secure and perfectly legal way to get game currency without having to hack your games.

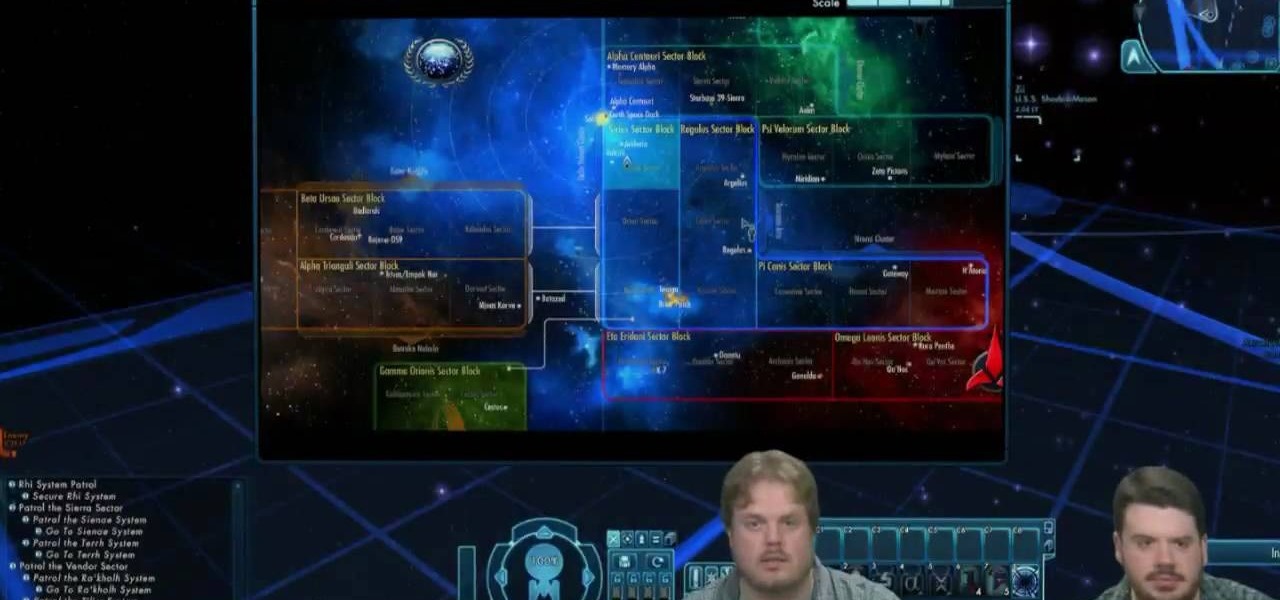
Know your way around sector space when you're playing Star Trek Online. This tutorial shows you how to interact with the sector map in the game and get to where you're trying to go, and what you might find as you travel through space.

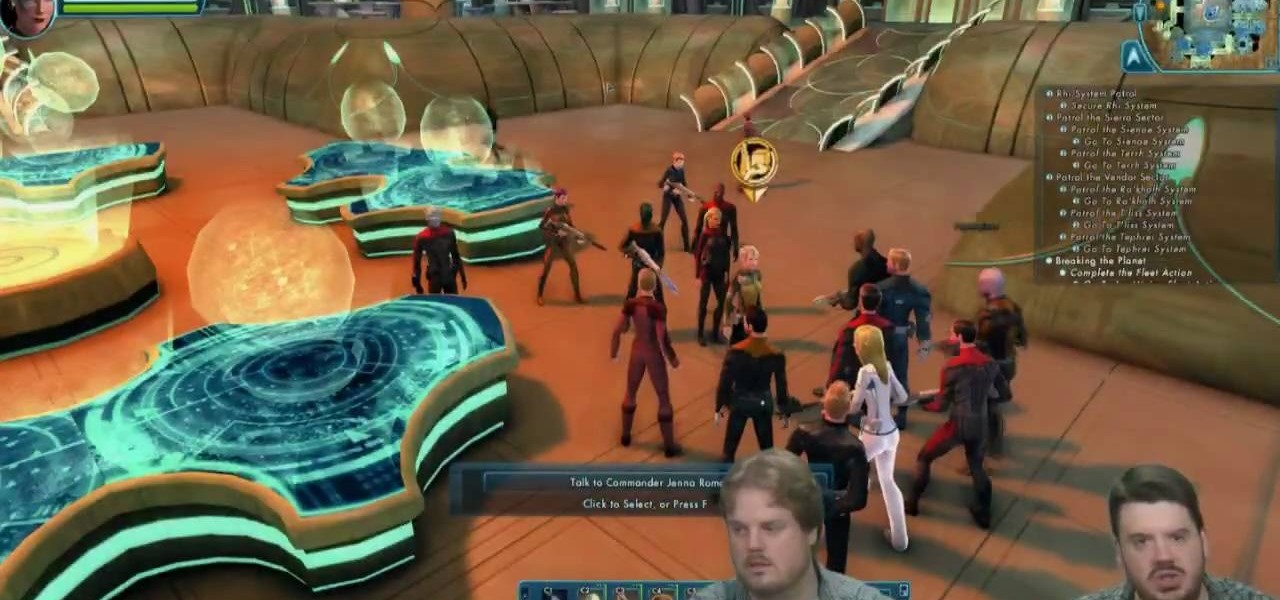
Crafting is someting you can do in Star Trek Online after you complete the Scientific Mandate mission at level 4. Once you do, you'll gain the ability to craft items. This tutorial shows you what to do once you acquire this ability.

This video explains one of the newer features of Star Trek Online and how to use it - the Accolade System. Also covered are the mechanics behind your ship's shields, and how to use that math to your character's advantage.

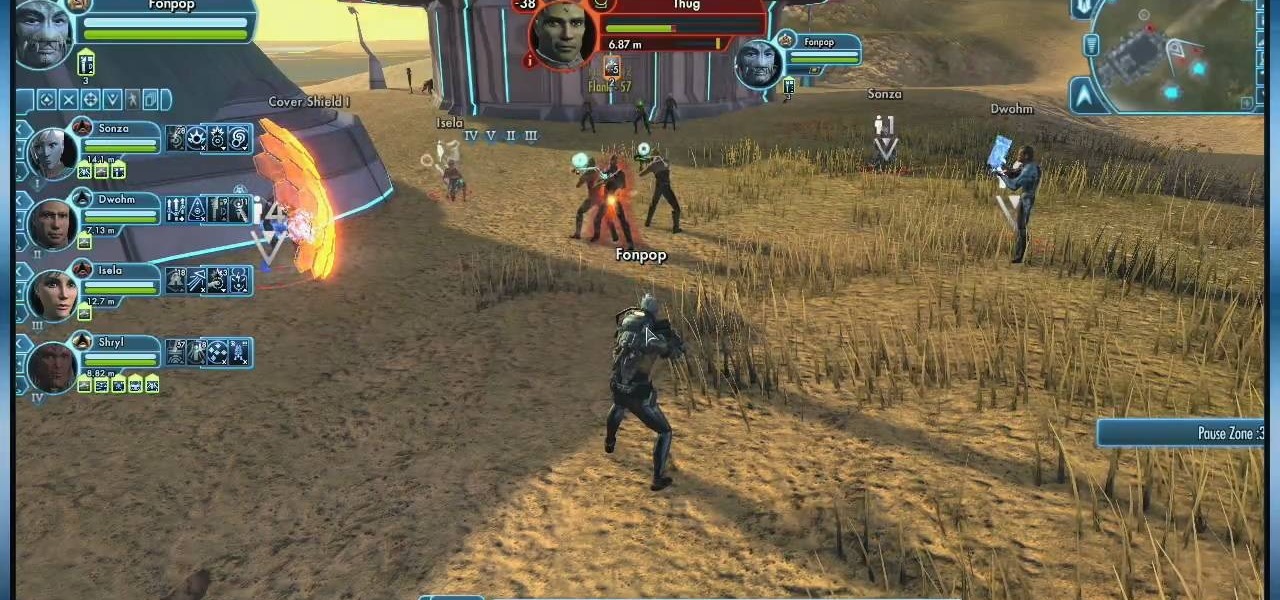
It's entirely likely to encounter hostile natives when exploring a new planet in Star Trek Online. Fortunately, you can easily outflank your enemy and triumph over the odds by using your Away Team. This video shows you a few strategy tips to decrease casualties.

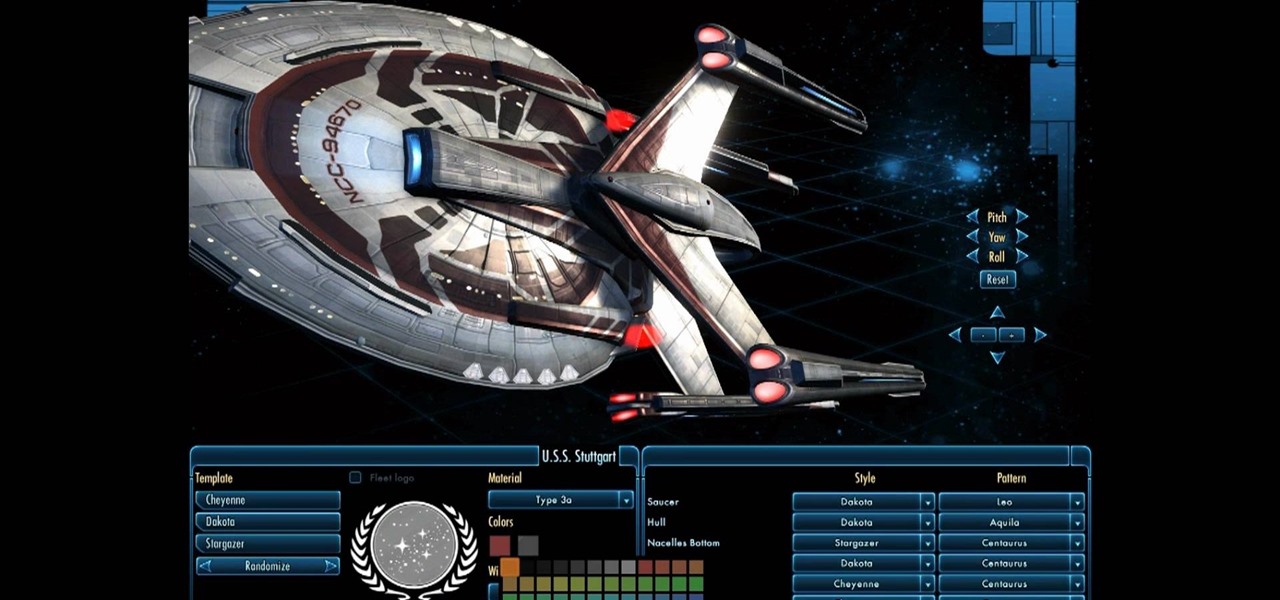
In Star Trek Online, not only do you play an individual character, you can also play your own ship while on space missions! And just as the characters are customizable, so are the ships! This tutorial shows you how to customize your ship to get it just the way you want it.

Part of what makes EVE Online so much fun is the option to explore different moons, planets and asteroid belts. However, it can be dangerous. This tutorial explains the equipment you'll want and the best way to explore in a non-combat situation.

Need to find a good agent for your character when playing EVE Online? Starting from docking your ship in the station, this tutorial shows you how to find the best agent possible to help out your character in the game.

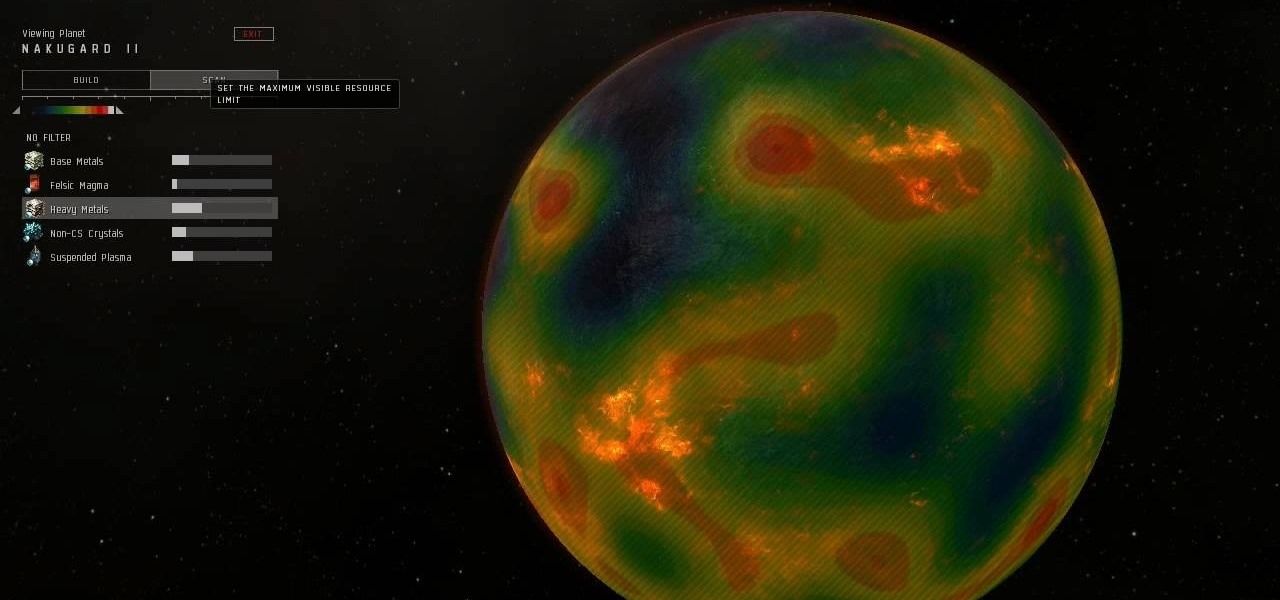
Planetary Interaction is a feature of the EVE Online expansion, Tyrannis. This video guide shows you how to use this new function. Choose your own planet, buy the command center and start exploiting its resources for your own gain!

Learn how to access the PS3 secret recovery menu by following this tutorial. You will need a PS3, PS3 remote, and a USB charger cable. Hold the power button on your system. Listen for three beeps (as you keep your finger on the power button). The third beep will turn your system off. Repeat this process, but this time, you will hear only two beeps (one beep followed by a quick double beep). Turn your TV on and it will tell you to connect your controller to the PSP. Connect your USB cable to t...

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

If you frequently fill out online forms, and are looking for a way to save time, you're in luck: With this video tutorial, you'll learn to use your keyboard, instead of your mouse, to fill in online forms and visit web sites. Make time for this time-saving tutorial.

With the convenience of internet poker games, everyone wants to play Texas Hold'em online. If you know the rules and good strategy you will have the advantage. The rules of an online Texas Hold'em tournament differ from game to game. Learn the basic structure of most online Texas Hold'em tournaments with this how to video. This lesson is a must have for anyone who wants to start playing Texas Hold'em poker tournaments online. You'll be a pro in no time with this Texas Hold'em tutorial.

Here is a beginner's guide to getting going on this highly addictive online word game, WordSteal. Watch the first video for registering and logging in, the second for creating a game, and the third for joining a game.

Things a little quiet on the online dating front? Need some online dating advice from the experts? Maybe you're looking for love with all the wrong adverbs and dating SEO. SEO is short for search engine optimization. Take a little time to soup up your profile and those dates will start a'rolling in with this how to dating video.

The newly enhanced focus from Magic Leap on enterprise, announced on Tuesday, also came with a few companies opting to weigh in with their experiences developing for the platform.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...