Imagine… your friend is drinking an ice-cold soda out of his/her styrofaom cup, and everything's fine, until… it's starts leaking everywhere! It could be utterly hilarious, or disastrously evil, depending on who your target is.
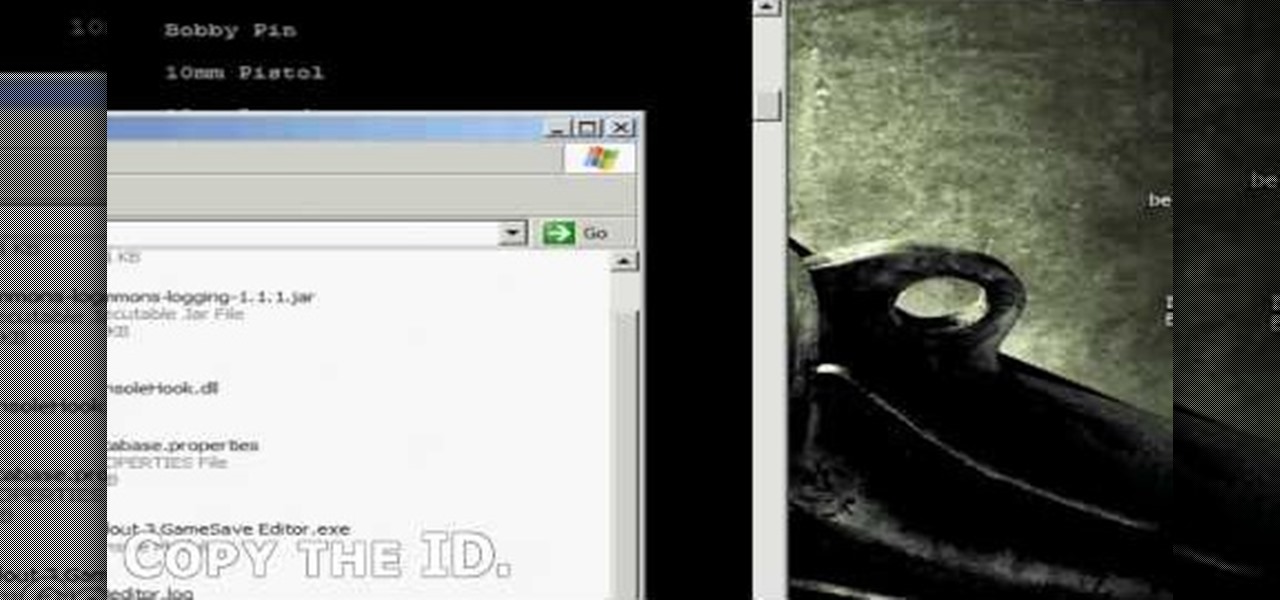
Fallout 3 is one of the most popular and biggest (content-wise) games on the XBox 360, and has thus become a popular target for hackers to mod. This video will show you how to mod your Fallout 3 saved game from the XBox 360 version using some FREE software. This does not include Modio, the popular for-money save game editor that many hackers use. Here are the files:

Four time abs is an excellent exercise for working the lower abdominals and abs workout. Try this out to tone your lower abs, which typical crunches can't get to.

Learn how to create a character rig when animating 3D models in Blender. Specifically, this clip addresses the following topics: Bone creation, splitting and re-parenting. Weighting with bone heat, mirrored weight painting and posed weight painting. IK setup, bone roll, and pole targets. Advanced foot rig with control to pivot off of the heel, toe, ankle or ball and control to lift the toes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or...

Despite what the name may imply, triceps kickbacks don't involve kicking of any sort. Rather, this tricep-sculpting exercise move involves getting down to a near squat position and bringing a dumbbell forward and back, keeping the shoulders stead and down.

Lock and load! In this Xbox 360 tutorial, you're taken for a nifty little ride by the guys at Achievement Hunter. The main target: an easter egg. And not just any cool easter egg, it's one that puts you, somewhat, in contact with another zombie basher from a different game, Dead Rising. Yes, in this Left 4 Dead 2: The Passing, easter egg hunt, you'll be reading a little message left to you from the man himself, Frank West. So sit back and prepare for the worst. Enjoy!

You must have a certain attitude to appreciate practical jokes and pranks. Your friends (or targets) may not appreciate pranks as much as you, especially messy ones. The messy pranks are the ones that are less likely to provide a laugh from your victims, at least not right away. This ketchup prank is one of those.

Brooke Burke and Autumn Calabrese walk the viewer through a super-effective, targeted butt workout, doable in your living room in only 5 minutes. The first exercise, a "Heel Press", is done from your hands and knees. Keeping your head in line with your spine and your belly button tucked in, press one heel toward the ceiling, then bring it all the way into your chest. Brooke recommends 15-20 reps on each leg. The next exercise, "Crossovers", builds on the Heel Press. After pressing your heel t...

This is footage from B.F. Skinner's psychological tests on shaping behavior.

One of the coolest parts of DC Universe Online is it's tremendously complex super hero character creation system. The system i pretty daunting at first, but this video will guide you through making an awesome character that will be the envy of your guildmates online.

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

Another major retailer is putting all its chips in on the relentless rise of selfie culture. Sally Beauty is rolling out kiosks to try-on "some of its best" hair dyes in 500 of its stores throughout the US. The in-store augmented reality-powered kiosks invite you to view yourself on video, overlay a punky (or otherwise) hair color, and snap a selfie on the screen to share your #glowup with friends.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

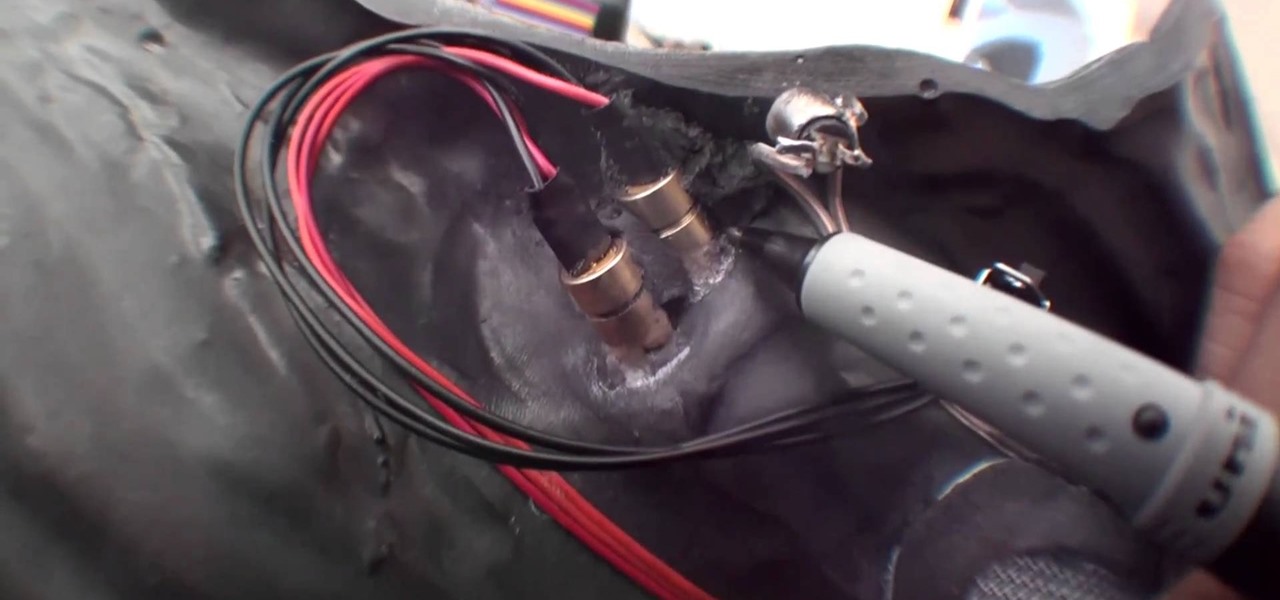
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

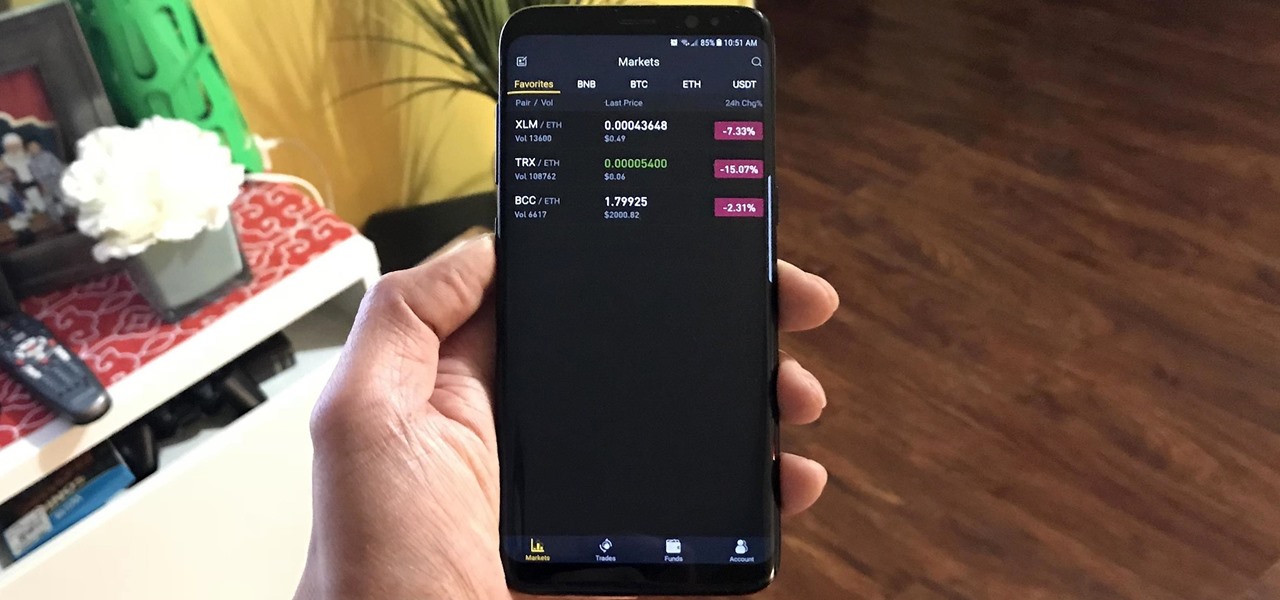
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

Want to hand out lollipops to your kid's class for Valentine's Day? Then don't just phone it in by scouring the shelves at Target the night before for some Dora the Explorer paper valentines that you'll tape to the lollipops.

After you purchase your first car in Gran Turismo 5 on the PlayStation 3, you'll unlock the National B License Tests. The first one (B-1) is a stopping challenge, and if you want to learn how to get the gold trophy, this video gives a perfect example of how to get it.

Going for a Predator outfit for Halloween or as a cameo in your film, you want to try to get as close to the real thing as possible. In this video you will learn how to perfectly align LED lights to create the targeting lights that the predator uses for its canon with a quick tutorial!

Christina Hendricks, who plays Joan Holloway on "Mad Men," recently rendered a male reporter speechless during a live interview. And honestly we're not surprised.

Back to school is the best time of the year to flaunt new clothing and accessories you scored during the summer. But since so many of us shop at the same places these days (come on, when was the last time you visited Target?), it's very likely you'll end up with a dress or necklace that someone else already has.

A bedbug is a small brownish, blood-sucking insect. Usually, infestation brings emotional trauma. So, the problem is greater than the physical problem, since the bugs bite at night, while the victim sleeps. Often, the bites are mistaken for dermatological conditions, until the bugs are found. Typically, bedbugs are going to be within 10-15 feet of your bed. They will usually be along the rim. They will also be underneath the box spring. There will be in the nightstands. There will also be blo...

Justin Bieber has just become the newest Proactiv spokesperson, showing that no matter how many people are looking at you (he performs for crowds of thousands), you never want acne on your face. While you may head back to your classes with fewer people paying attention to your face, pimples can still be quite the pain in the ass.