Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

Earlier this year, rumors began to swirl regarding Apple's upcoming iPhone SE 2. They predicted an A10 processor and a glass back for wireless charging, all at a price point at least $150 cheaper than the iPhone 7. While it wasn't poised to turn heads like the iPhone X, it would have been a reasonable upgrade for many users looking for a more budget-oriented Apple device.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The augmented reality feature in Pokémon GO is one of the key components that draw people in to the popular Android and iPhone game. Indeed, there's nothing quite like the sight of a Pokémon standing around in an otherwise uninteresting parking lot.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

There may be worse feelings than sitting around waiting for food delivery, but I don't want to know what those are. Especially when your local delivery guy misses your address for the eighth time. But soon, Domino's Pizza will take that stupid human error right out of the equation in the form of a robot that's only 3 feet high.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Hello friends. This is actually my first how to.

Hello everyone! Hope everyone having good day!! I wanted to share an easy way to locate an appropriate exploit from the EDB, get it compiled, and run it all from inside the terminal.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Aside from the most basic functions, most of us are pretty useless when it comes to Photoshop. Yes, we can all add filters, but who wants to see everything in black-and-white or sepia? Why not change a sunflower blue, your hair pink, or your lips purple—without having to spend hours with editing software.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Here's a way you can turn a mousetrap into a fun little handgun that shoots up to 40 feet! This is a great project because it can be made with simple materials, very basic tools, and in just a few minutes!

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

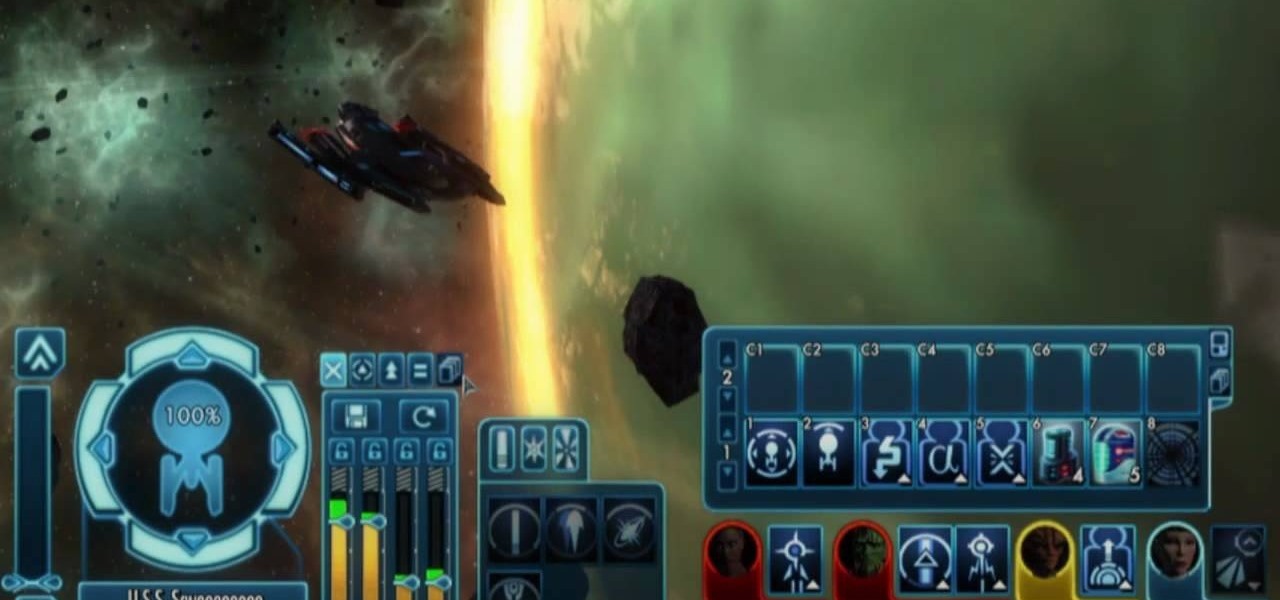
Fighting in space is one of the aspects of Star Trek Online, and how you fight will depend on what strategy and tactics you employ. This tutorial goes over a few options and tricks to help you fight your best as a ship.

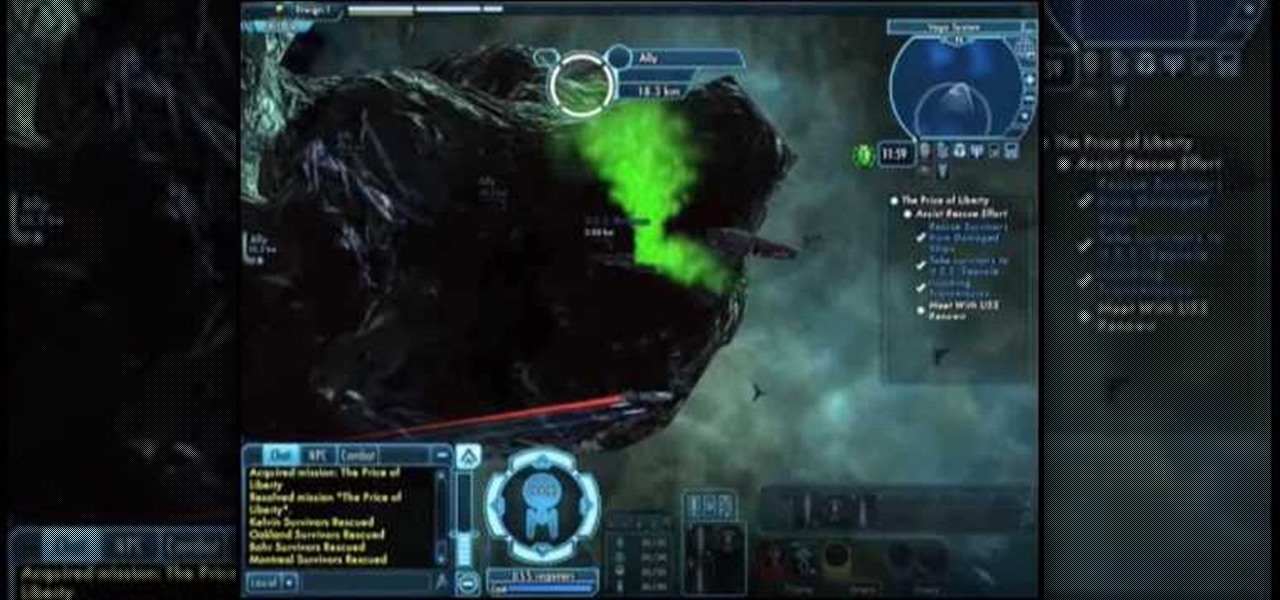
Space combat is one of the major aspects of Star Trek Online. This video walks you through one of the introductory missions of the game, and shows you how to use your ship to fight, pick up passengers and even fight the Borg!

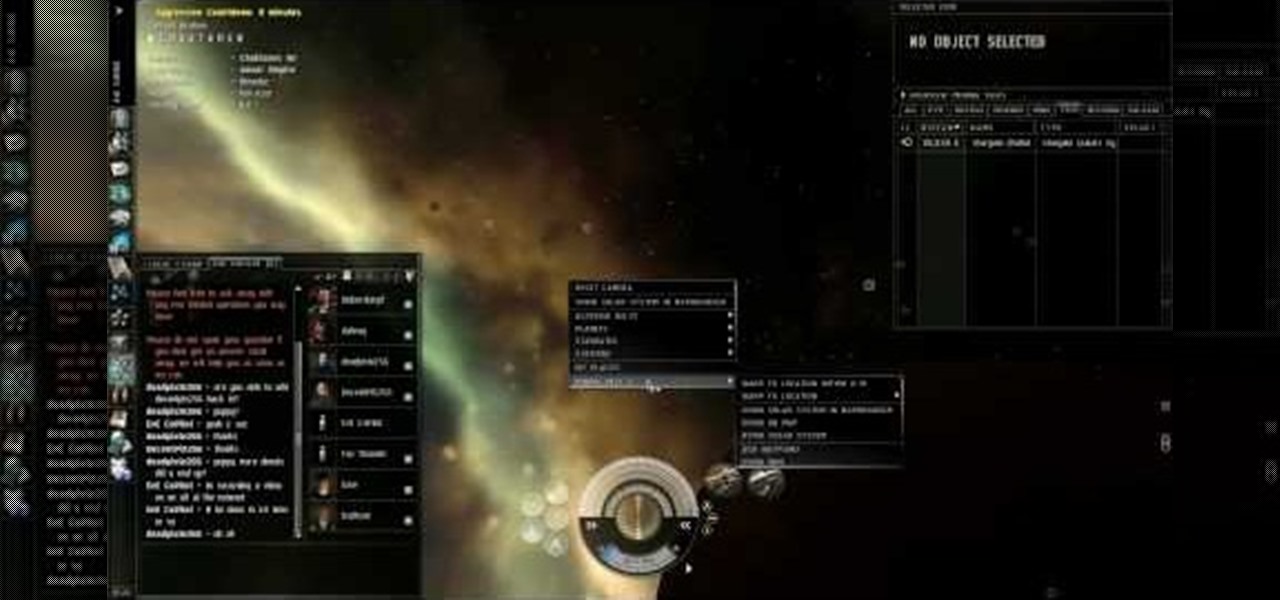
Mining is one of the best ways to earn resources when you play EVE Online. This tutorial includes everything you need to know in order to profit from mining - all you need is a ship and a mining laser!

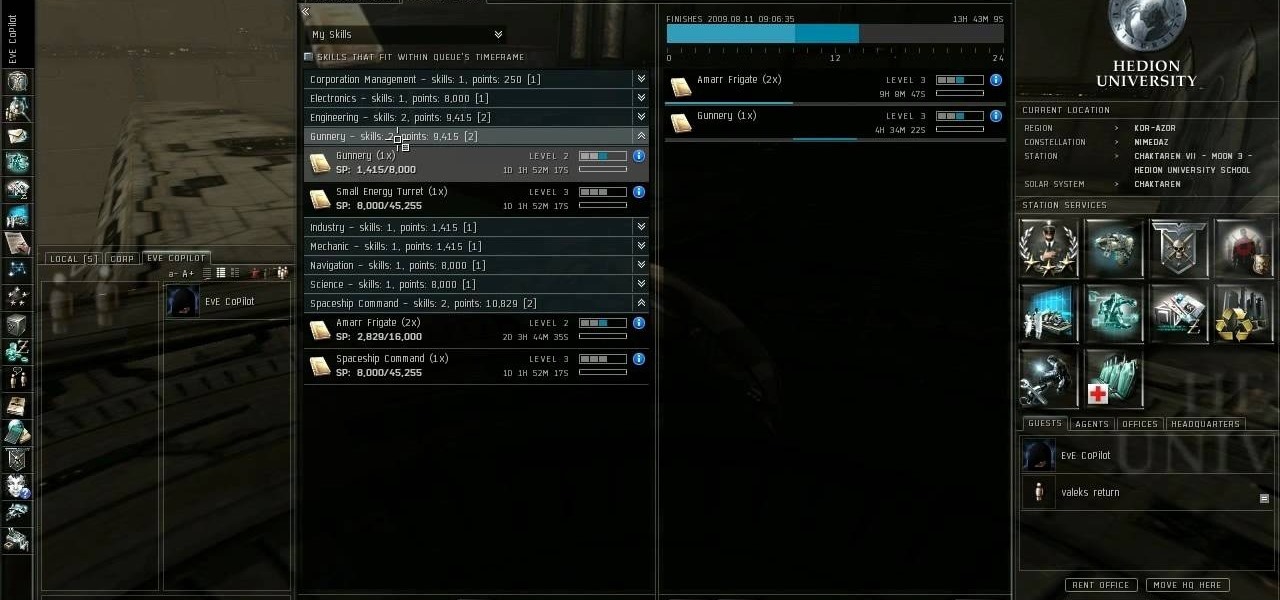
Make sure your character progresses the way you want! This tutorial explains how character attributes and skill training work within EVE Online so you can maximize your character's potential in the game. This tutorial also explains how to navigate the character sheet function. Always be learning at least one skill!

Have some last minute edits to make to your photos before you publish them online? Don't have time to download and install software to your computer? This video guide has five free online photo editing services to share. For detailed instructions, and to get started editing your own digital images online, watch this free video tutorial.

This is a great video series from Yanik Chauvin demonstrating how to use Photoshop Express online for free. This great tool is a wonderful resource for those who can't afford Photoshop but still need to do basic photo editing.

With the convenience of internet poker games, everyone wants to play Texas Hold'em online. If you know the rules and good strategy you will have the advantage. The rules of an online Texas Hold'em tournament differ from game to game. Learn the basic structure of most online Texas Hold'em tournaments with this how to video. This lesson is a must have for anyone who wants to start playing Texas Hold'em poker tournaments online. You'll be a pro in no time with this Texas Hold'em tutorial.

Here is a beginner's guide to getting going on this highly addictive online word game, WordSteal. Watch the first video for registering and logging in, the second for creating a game, and the third for joining a game.

This tutorial shows you how to download and use old roll playing games like those from an NES OR SNES to learn languages online. Make sure to watch the second video or you won't get very far.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.