A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The holiday season is upon us, and that means all the big-box stores are competing against each other to offer the best prices on electronics. What was once a 24-hour period of flash deals the day after Thanksgiving has now become a holiday in and of itself — Black Friday is an event you don't want to miss.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

The concept of video game etiquette is foreign to many people, including a disgraceful number of frequent gamers. The combination of anonymity and role-playing in online games can lead people to be dicks in all sorts of obnoxious ways, making a fun activity distinctly less fun for everyone. Watch this video to learn about proper online gaming etiquette in the context of Call of Duty Black Ops. These lessons extend to most games, however, and practicing them will results in people liking to pl...

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates how to use color as value in the art of portrait painting.

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates how to do an underpainting for portrait painting.

Sessions Online School of Fine Arts brings you this tutorial video on painting. Search WonderHowTo for Sessions Online School of Fine Arts for more art tutorials. This video art lesson demonstrates what is needed in preparation for portrait painting.

If you're a small business operator and AT&T is your carrier, you'll want to take advantage of the AT&T Online Account Management portal for small business customers. This video shows how to request an online registration code (required to register your account), how to use it to register your account, and how to set up your username and password.

Uh oh, you've forgotten your AT&T Online Account Management password! No worries, this simple guide shows you how to regain access to the site and reset a new password. Your AT&T Online Account Management portal is vital to keeping your information up to date, so make sure you know how to NOT get locked out.

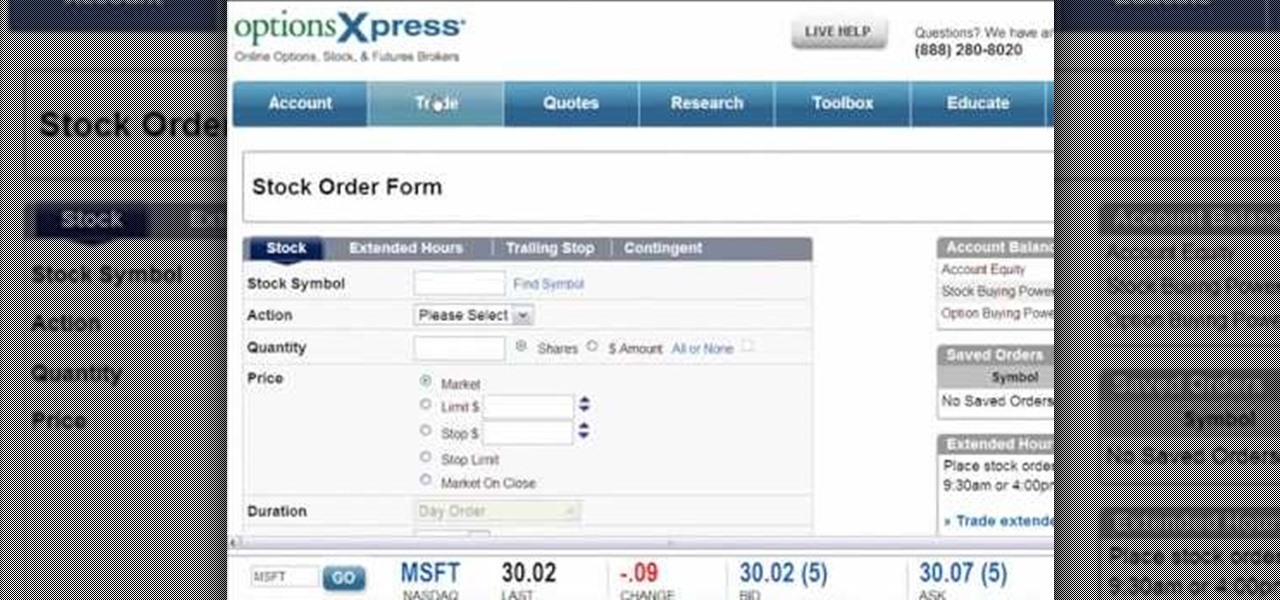
In this tutorial, we learn how to safely buy and sell stocks and shares online. First, go online to your broker and open an account. You can do this through Options Xpress. Now, press on the stock button located at the top. On this page, you will be able to type in the stock symbol, then type in the rest of the information before you place your order. Once you do this, you will have bough a stock in just minutes online! If you want to sell a share, you will do the same process, except underne...

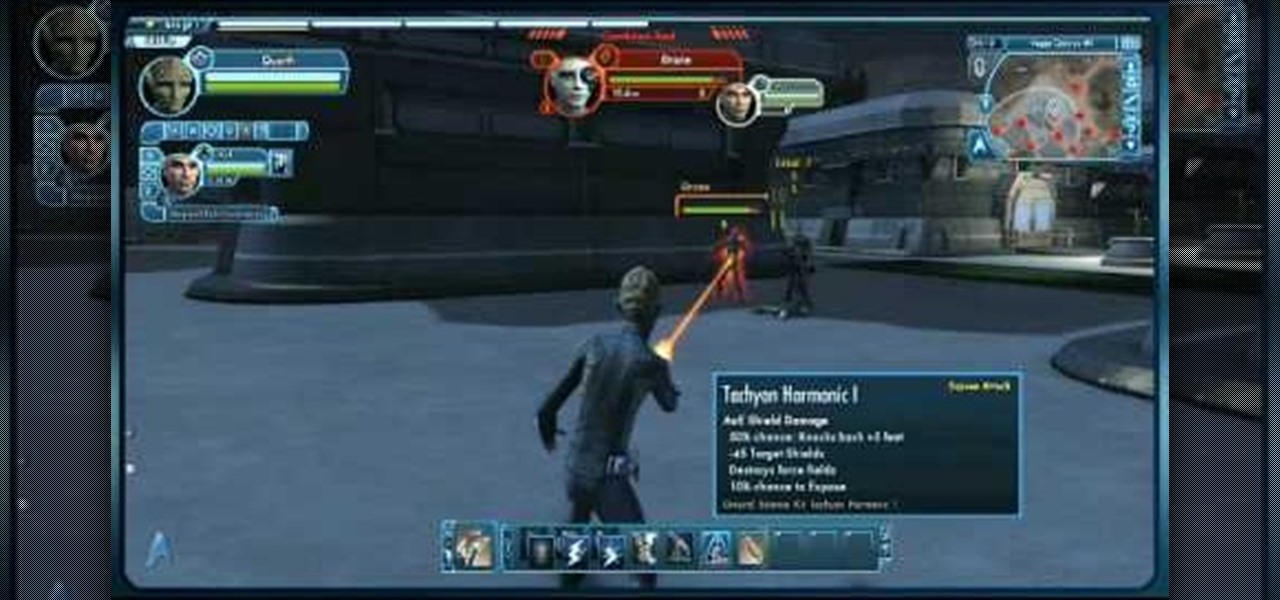
Don't be just another red shirt! Here's a detailed tutorial showing you how to engage in ground combat when exploring a planet. Make sure you've equipped the right weapons and know how to use their expose and exploit functions!

If you want to tool around in the user interface of Star Trek Online and modify your client, this video shows you how. Do note that Cryptic doesn't support modding, and it could break your system. But if you want to alter the mouse pointer or your camera point of view, here's how!

Kits are something your character might come across while playing Star Trek Online - special items which will augment or improve your character's specific skill set. This short video explains what kits do and how you find and use them.

Part of the fun of an online game is being able to chat with your friends! This tutorial goes over how you can use the in-game chat system to join a chat channel. It also gives you a few channels useful for everyone to join, especially new players. Or create your own channel. Avoid pirate corporations!

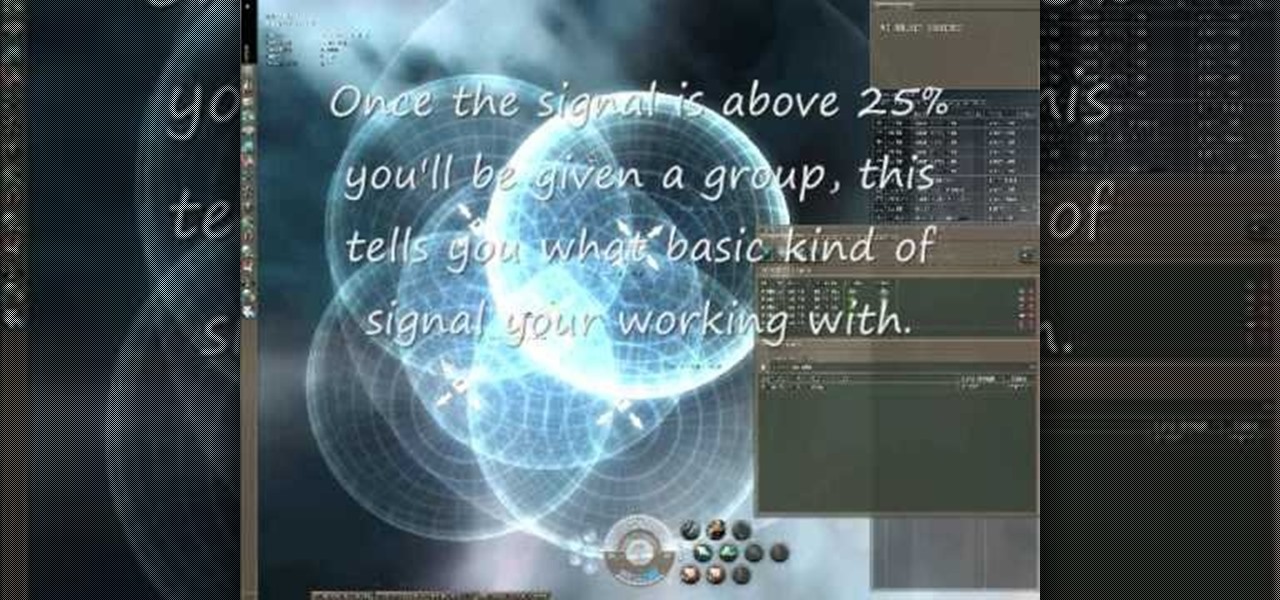
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.

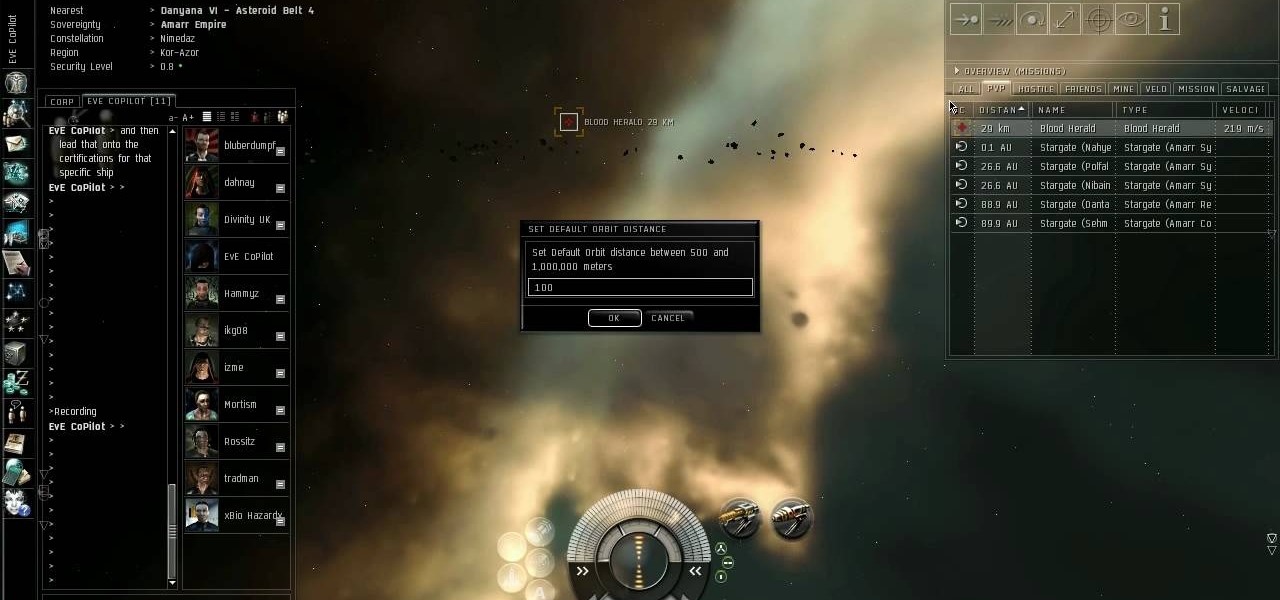
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

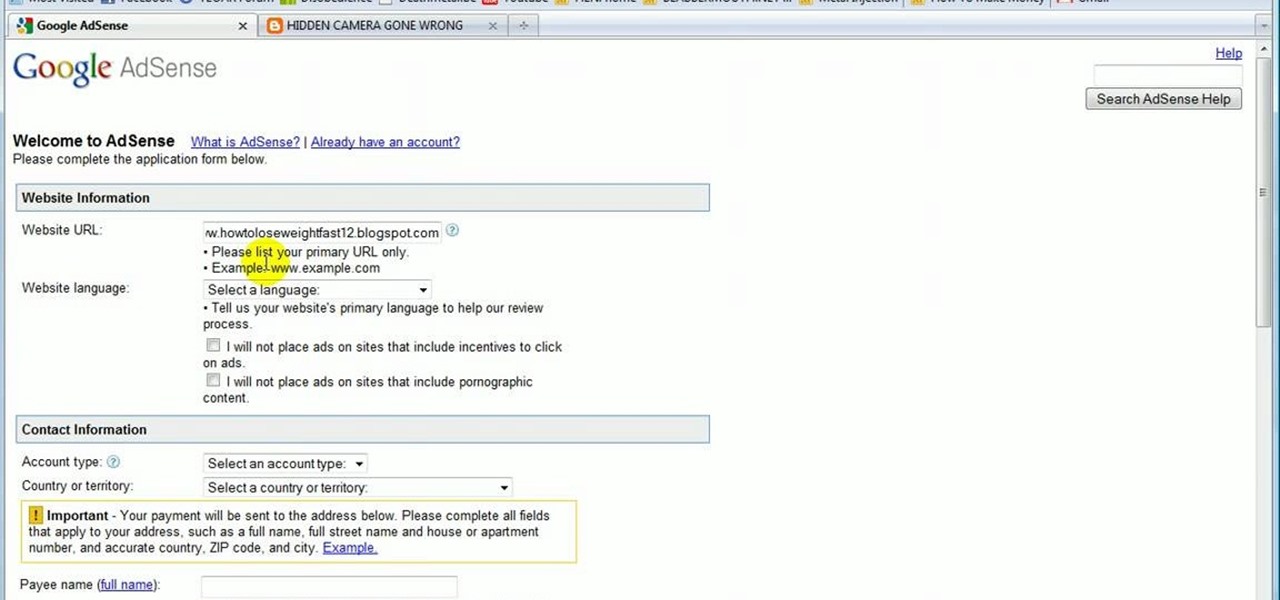
Online advertisements are a sure shot way to making money online. This video will demonstrate how to open a Google Adsense account and make some money.

Tired of those bulky alarm clocks in your bedroom? Get rid of the darn thing and use your computer. There's an online alarm clock at onlineclock.net that saves space in your bedroom and keeps simplicity in mind, with simple red number digits and a black background.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

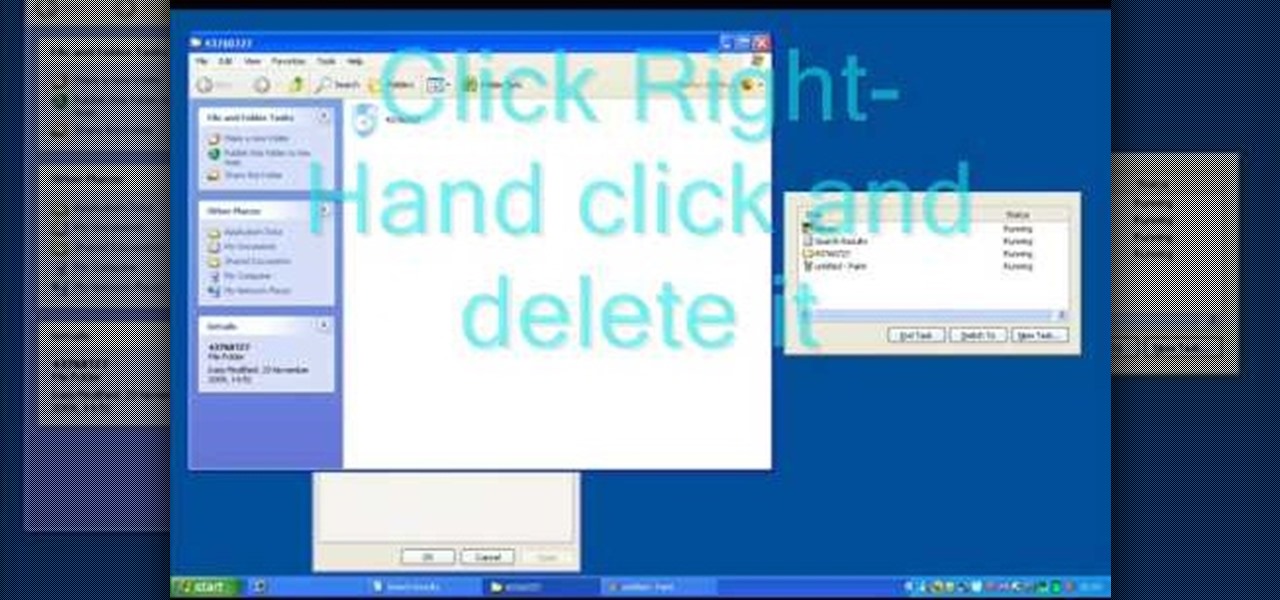
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

In this tutorial, we learn how to throw a crazy gyroball in wiffle ball. You will first stand still with the ball in your hand grasping it lightly, when you go to throw the ball, throw with force and spin your body around. This should make the ball go straight into the target almost every time you throw it. Keep practicing this until you have the hand placement correct. Try moving your hand in different positions around the ball so that the grasp makes the ball move in the right direction. Af...

In this Golf video tutorial you will learn how to avoid slicing with your driver off the tee in golf. First and foremost make sure that your grip is correct. The next point is allowing the club to sit on the ground the way the manufacturer wanted it. The next important lesson is to ensure that your feet and your shoulders are aligned straight down the target. And the last and the most important point to remember is to swing back to the ball with your hips first. Don’t use your arms first. If ...

Jim McLean shows us how to do an eight step swing in this video. You start the swing in the "address" or universal position. The first step is to move the club three feet back from the ball in a uniform motion. Position two is moving the club half way back where the club is pointing down the target line. Position three is a three quarter golf swing is when your elbows are level and the shaft of the club is pointing into the plane line. Position four is preparing to swing forward. Position fiv...

This video is on Golf and will show you how to use the variable tee drill to cure a pull shot in golf. This video is from Golf Link. A typical problem for somebody who tends to pull the ball is they position the ball too far forward. So, when they are setting up, the shoulders are actually looking left. By the time the club head reaches the ball during the swing, they are swinging around to the left producing the pull. The variable ball position drill will cure this problem. Place a club on t...

In this video tutorial, viewers learn how to use the hand rollover to cure a hook shot in golf. A reason why people hit hook shots is because when they come to impact, they roll their hands too early and too much. Therefore closing the club face and causing the ball to go left. To correct this, when you're coming to impact, rotate into a position where the back of the left hand is facing the target. This will square the club face. This video will benefit those viewers who enjoy playing golf a...

In this video tutorial, viewers learn how to cure slices by rolling the wrist. Some people hit slice shots because they strike with a underhand or reverse position. The correct way is when your hand comes back for impact, it should rotate into position with the back of the left hand facing the target. If the back of your left and is facing anywhere else, the ball will slice. A drill that users can do is to use their wrist watch as a guide. Start with it at a 45 degree angle. When you swing, i...

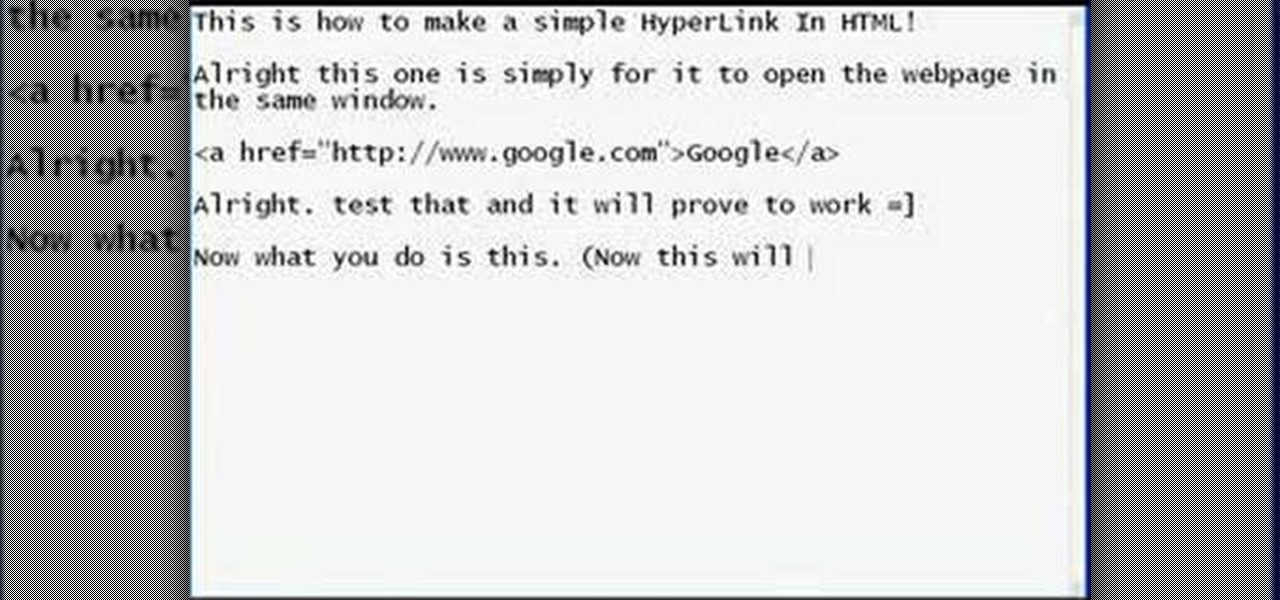
This how to video shows how to put an HTML hyperlink on a web page. It starts with the basic code to simply insert the link and have that link open in the same window. The code appears as follows: <a href="http://www.website.com">Text that will show up on the page </a>. The example used is Google, so it would be, <a href="http://www.google.com">Google</a>. The video then explains how to create a hyperlink that shows up in a new window. Sticking with the Google reference it would read <a href=...

Prepare for the ultimate Wizard101 walkthrough. These 14 videos show just about every aspect of Wizard101 gameplay. So get ready for an educational know-all guide.

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt explains how he teaches the BEEF method of shooting. The work BEEF is an acronym for a ball shooting concept in basketball. The B stand for balance, the E for eyes, the second E for elbows, and the F for follow-through. To have good balance it is important to have you feet about shoulder width apart. Your eyes should always be focused on a target, and your elbows should be in line. Finally follow through means it sh...

This how to video shows you a six pack abs workout that will help you tone and tighten your stomach. Learn three of the best abdominal sculpting exercises to target your midsection.

This pilates how-to video illustrates the Swimming exercise. This pilates exercise is good for core stabilization, upper back extension and hip extension. This is good to improve back strength and those deep abdominal stabilizers.

This video pranking tutorial shows how to make a ketchup bomb out of ketchup and aluminum foil. The ketchup bomb will explode on contact with the target and make a sticky, staining, red mess. It's easy to make the ketchup bomb during lunch, saving the practical joke for whenever you're ready to strike. Learn how to make a ketchup bomb by watching this instructional video. Use this as inspiration for one of your April Fools Day pranks!