AT&T Online Account Management portal for small business customers is a great place to manage a sea of information, BUT, it won't do you any good unless you know how to log in. This clear how-to shows you how to enter your AT&T username and password so you can manage your account online.

MetaRL is a site you can sign up with that will let you accrue points that you can cash in for free online currency in your favorite online game. It's a very secure and perfectly legal way to get game currency without having to hack your games.
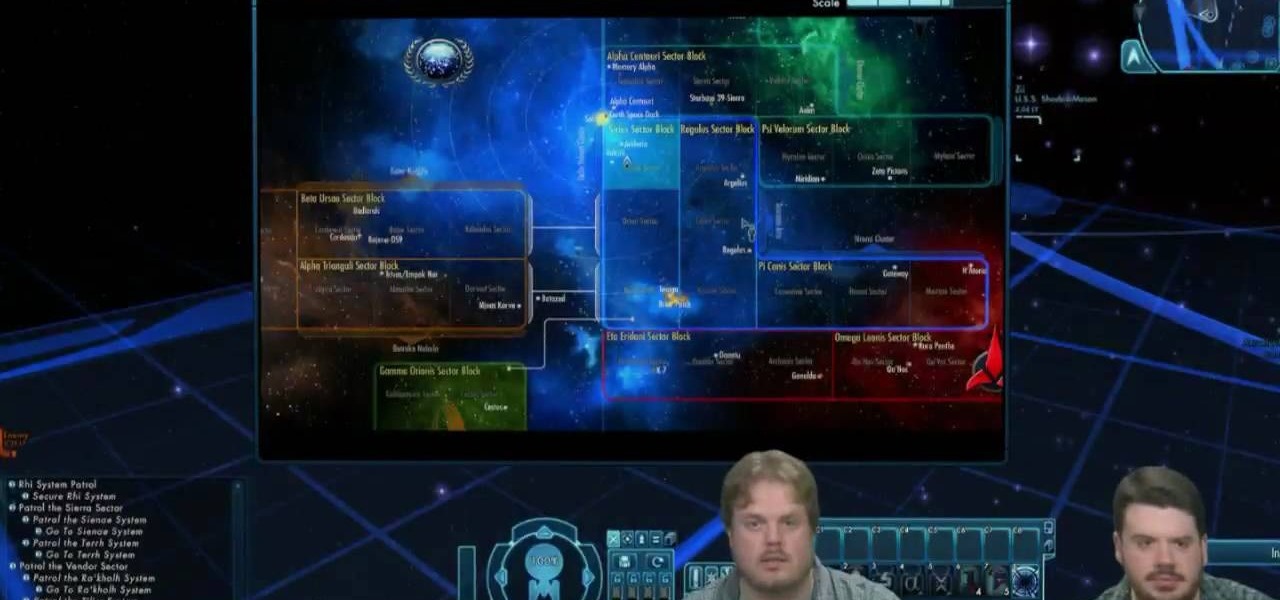
Know your way around sector space when you're playing Star Trek Online. This tutorial shows you how to interact with the sector map in the game and get to where you're trying to go, and what you might find as you travel through space.
Crafting is someting you can do in Star Trek Online after you complete the Scientific Mandate mission at level 4. Once you do, you'll gain the ability to craft items. This tutorial shows you what to do once you acquire this ability.

This video explains one of the newer features of Star Trek Online and how to use it - the Accolade System. Also covered are the mechanics behind your ship's shields, and how to use that math to your character's advantage.
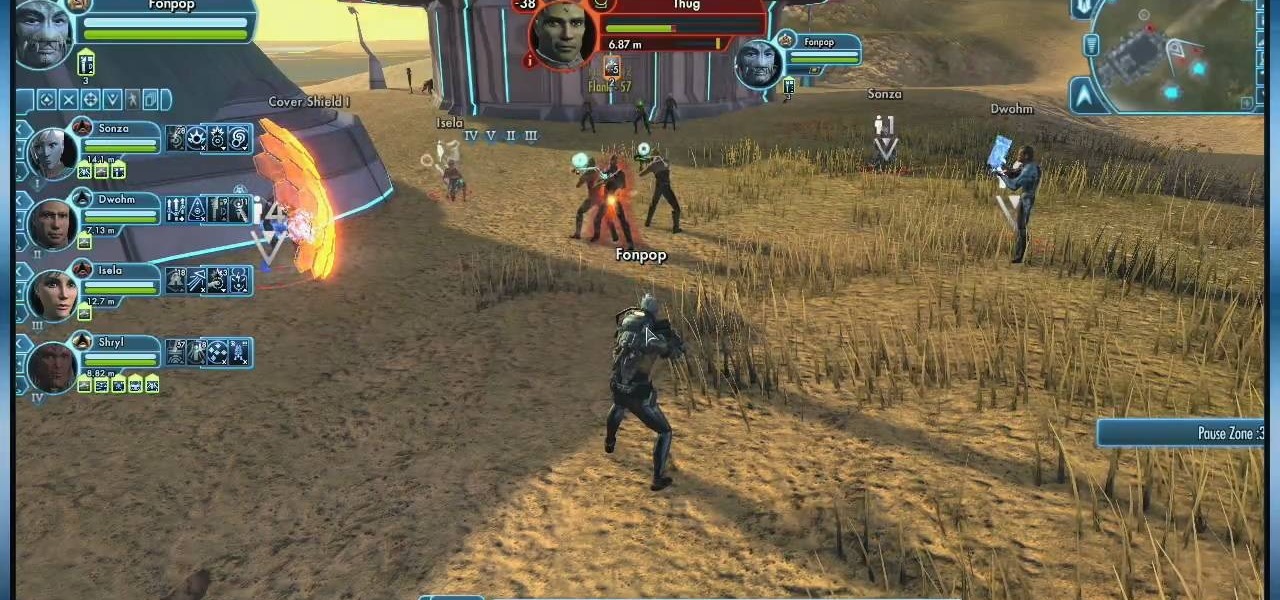
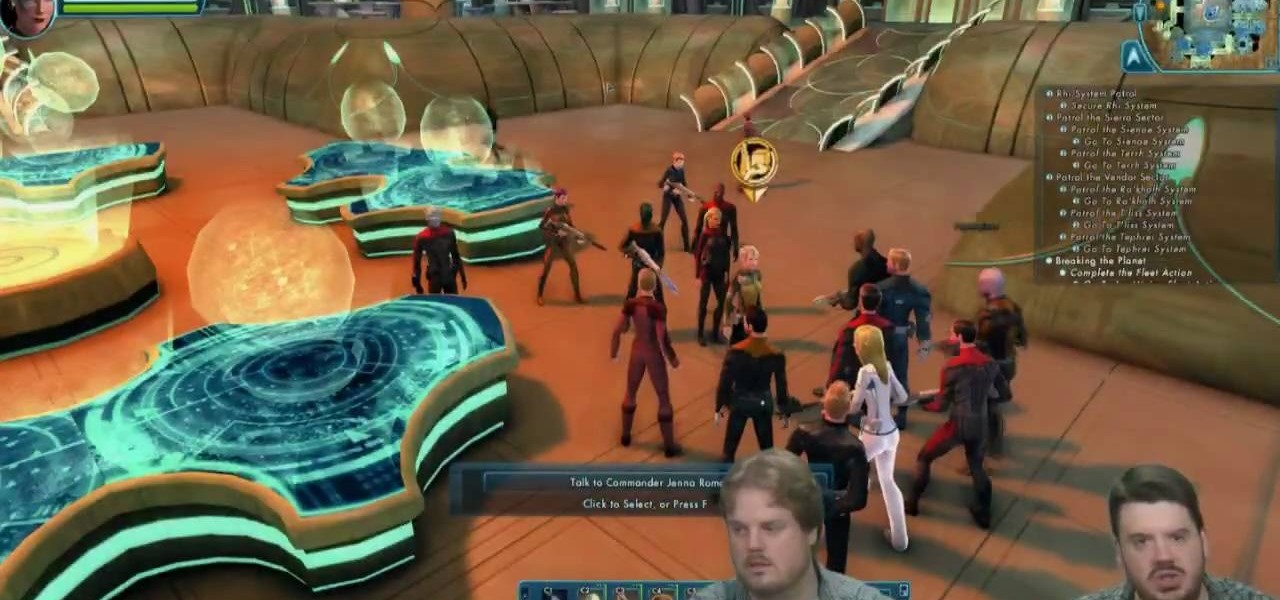
It's entirely likely to encounter hostile natives when exploring a new planet in Star Trek Online. Fortunately, you can easily outflank your enemy and triumph over the odds by using your Away Team. This video shows you a few strategy tips to decrease casualties.

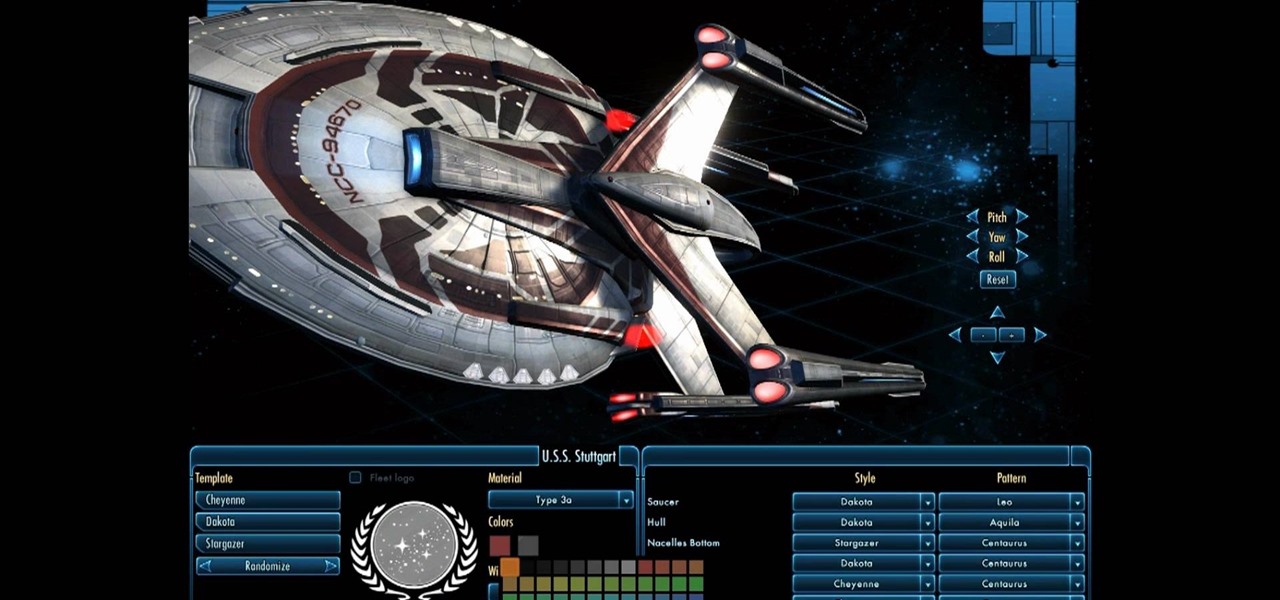
In Star Trek Online, not only do you play an individual character, you can also play your own ship while on space missions! And just as the characters are customizable, so are the ships! This tutorial shows you how to customize your ship to get it just the way you want it.

Part of what makes EVE Online so much fun is the option to explore different moons, planets and asteroid belts. However, it can be dangerous. This tutorial explains the equipment you'll want and the best way to explore in a non-combat situation.

Need to find a good agent for your character when playing EVE Online? Starting from docking your ship in the station, this tutorial shows you how to find the best agent possible to help out your character in the game.

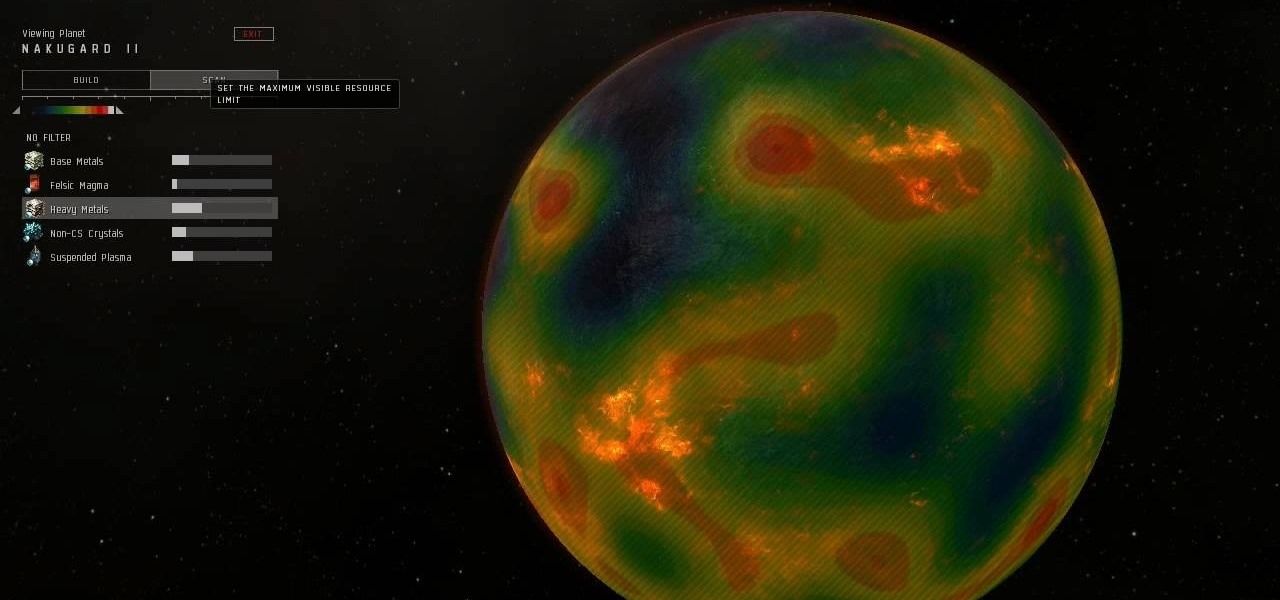
Planetary Interaction is a feature of the EVE Online expansion, Tyrannis. This video guide shows you how to use this new function. Choose your own planet, buy the command center and start exploiting its resources for your own gain!

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...

In this video, Dan and Jennifer will teach you how to be safe while trying to meet girls or date online. Learn tips and tricks to avoid common scams such as identity theft and fraud, as well as things to look out for and early warning signs that your potential lover may not be all she says she is. Dan and Jennifer will also show you how to watch out for one of the most common scams online: "cam girls". Don't fall for that fake girl that acts like she's totally into you but really just wants y...

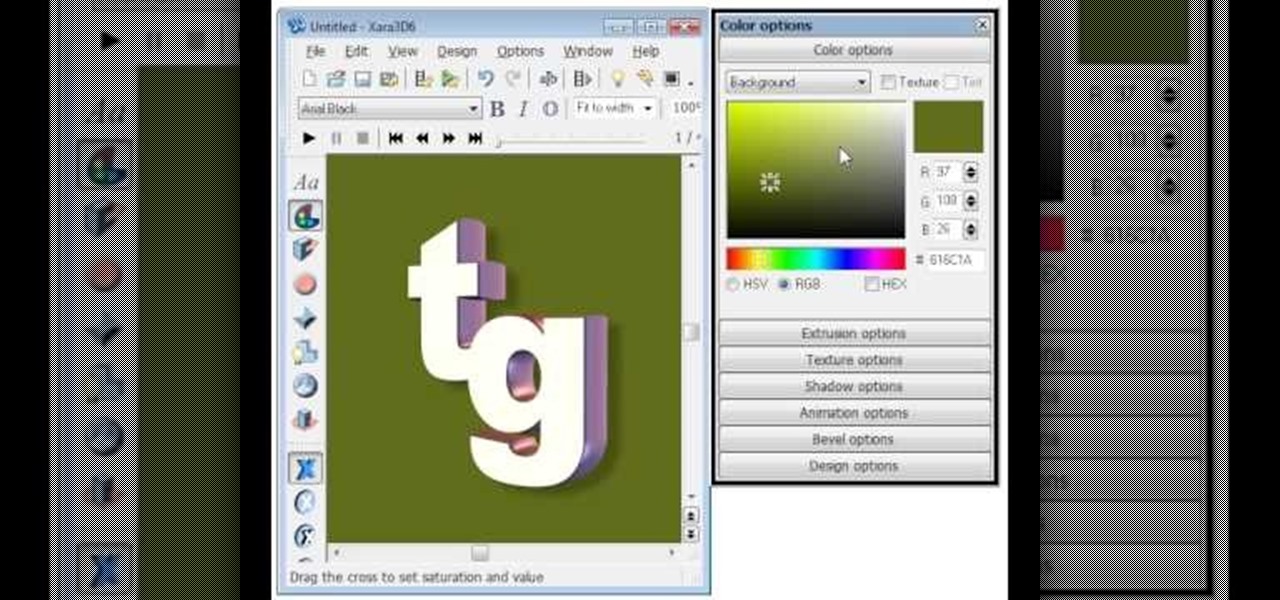
EggBram walks you though changing background colors in Xara3D and shows where to find the transparency setting. This is a simple walk through in high detail, very visible. Xara has been a part of internet development from the very beginning. Xara one of the original Internet service providers when it came about in the 1990s. Xara does most of its work online and has millions of customers online around the world. Xara Online is a leading edge online web service that gives you solutions for a m...

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

If you frequently fill out online forms, and are looking for a way to save time, you're in luck: With this video tutorial, you'll learn to use your keyboard, instead of your mouse, to fill in online forms and visit web sites. Make time for this time-saving tutorial.

Things a little quiet on the online dating front? Need some online dating advice from the experts? Maybe you're looking for love with all the wrong adverbs and dating SEO. SEO is short for search engine optimization. Take a little time to soup up your profile and those dates will start a'rolling in with this how to dating video.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Here is a video that shows 90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.)

90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.) By forming your target material into an efficient ball, you will be able to start a fire even with very small lenses. Like less than an inch across small. The finer the individual fibres, and the more densely they are packed, the more effective is your ball of smigtin (smoulde...

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

For those of us living in any of the 49 states other than New York on Thanksgiving Day, checking out the famous Macy's Thanksgiving Day parade at New York is more a dream than reality. While the parade airs every Thanksgiving on television, it's also possible to catch the festivities online.