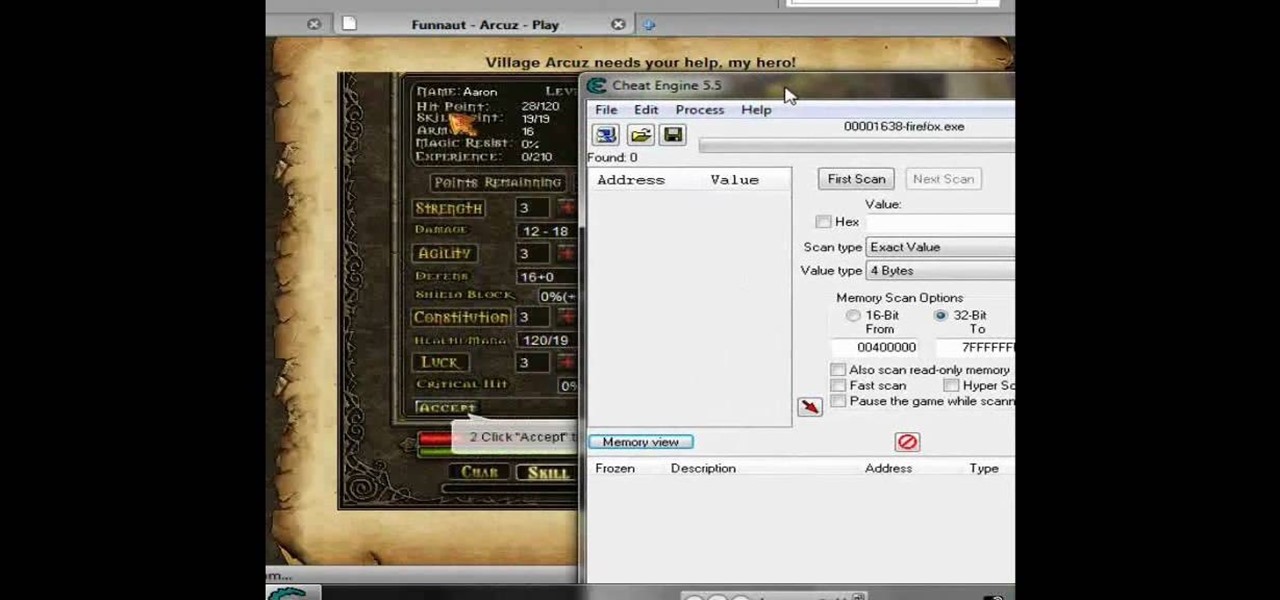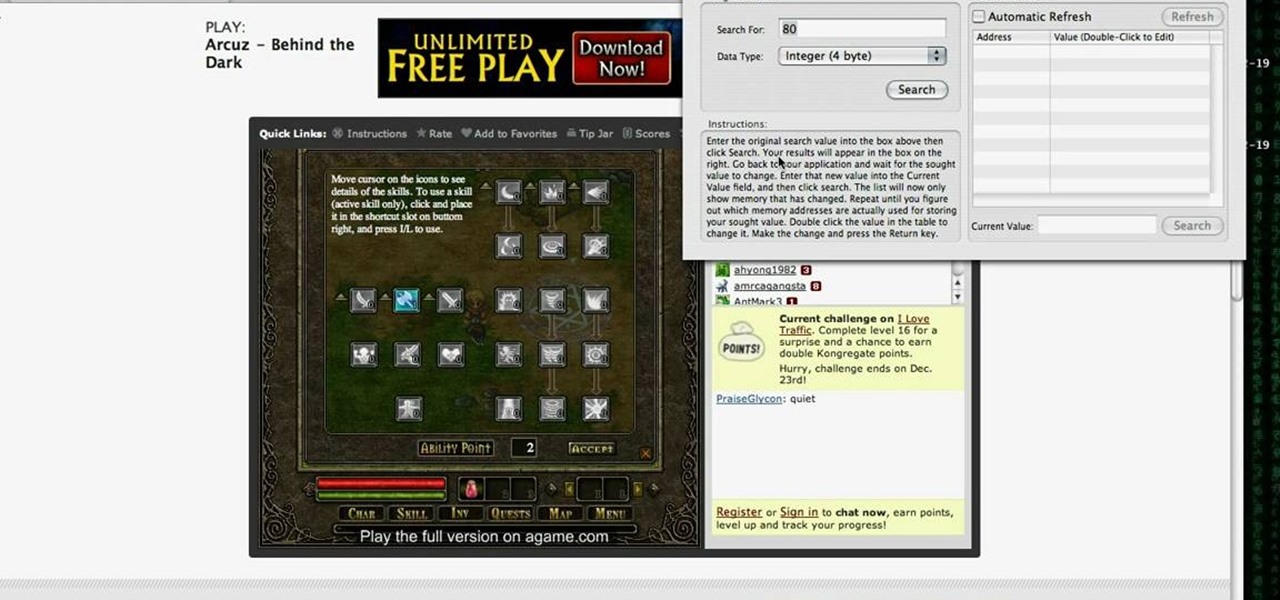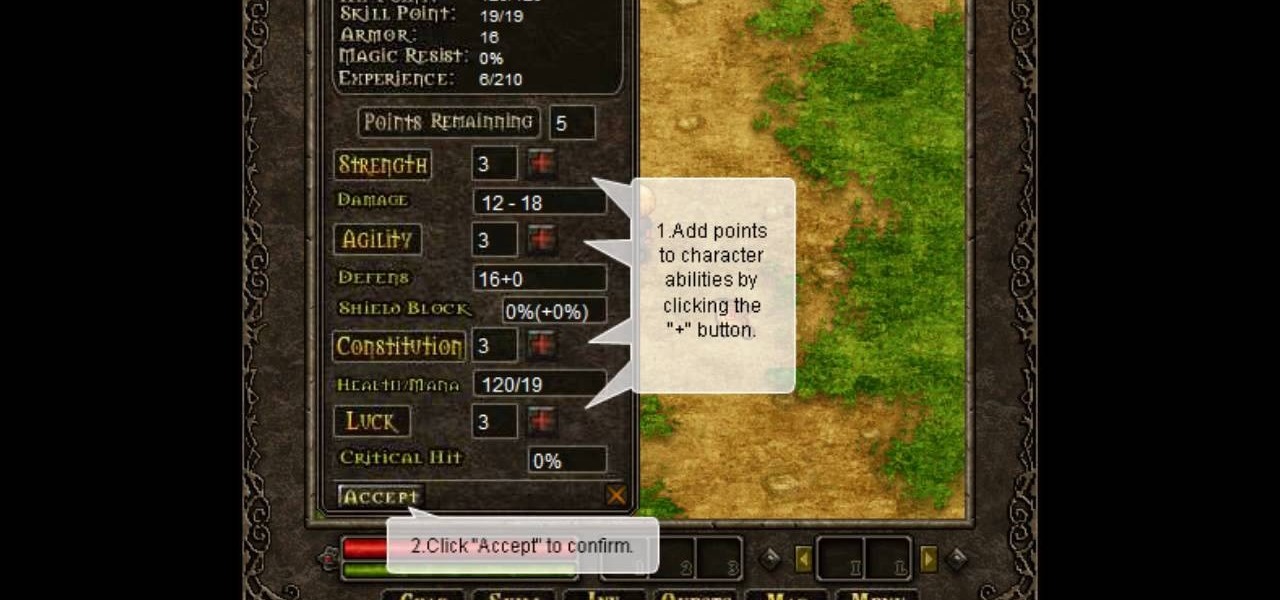
Want more gold? How about more skill points? You may need them in the game Acruz. But how do you get more, more, more? Well, with Cheat Engine, you can get more gold and skill points, with no real hassle.

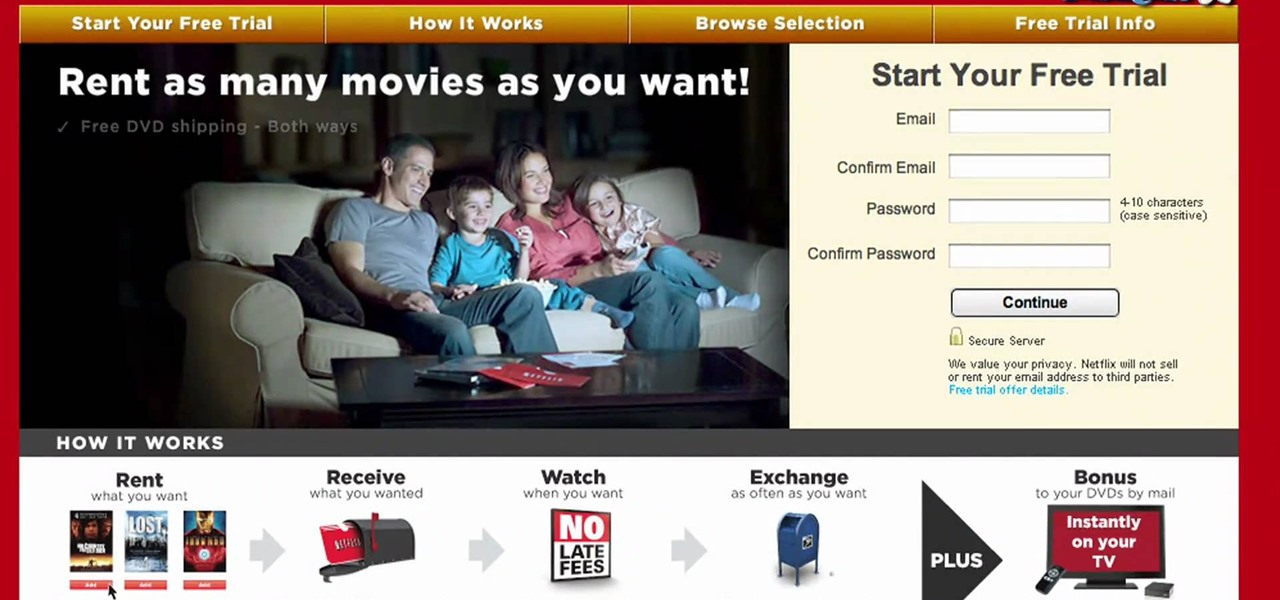
Dying to try online dating, but worried that the guy that you're digitally winking at is really a cyber stalker? Then watch this Dating Advice how-to video to learn how to date and decode online dating profiles. With this online dating translator you are sure to keep all the cyber stalkers out of the running.

Spotify is a free, ad-supported program that allows you to listen to music online for free. The music is everything from indie labels to the top 100 charts. This guide will help you learn how to listen to music using a Spotify account.
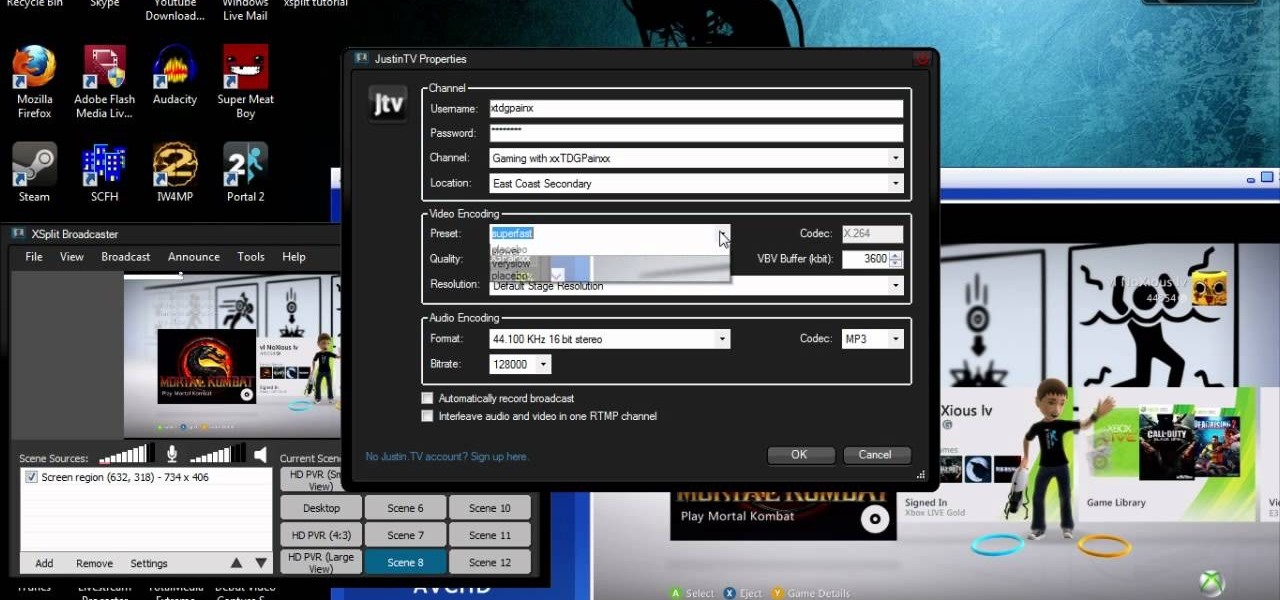
If you want to stream your Xbox 360 and PS3 games online so that others can watch you play console games on Twitch.TV or Own3d.TV, this guide will help. You'll need to own a Hauppauge HD PVR and have access to XSplit Broadcaster, a program that streams video sources from your computer to popular streaming websites.

AT&T Online Account Management is full of usefull tools to manage your AT&T account. Whether you're dealing with your smartphone account, landline or any other AT&T product or service, this is a quick and easy way to dial it in so it works for you.

Back up your computer data and save your time, money and valuable information using these helpful tips. There are several options to backing up and storing your important data, ranging from tiny keychain USB drives to backing up your files online. This informative and lighthearted video from Kipkay shows you how.

Now that Thanksgiving is less than a week away, the holiday season is in full swing. And that means you're probably busier than ever, what with all the decorating, cookie baking, and present buying and wrapping.

Lord of the Rings Online is now free to play! This tutorial demonstrates how character creation works, so you can design your own dwarven, elven or human hero of Middle Earth. Your appearance is influenced by your origin, which is demonstrated in this video as well.

The purpose of this video is to highlight the proper uses of the tank during online multiplayer mode in Call of Duty: World at War. The tank can be a really useful piece of equipment, but using this wagon effectively can be tough, especially when playing other, more skillful players online. Hopefully, after this video, you'll be the one on top.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

In this video tutorial, viewers learn how to upload large files online for free. The website recommended in this video is Load2All It does not host any files, but it provides a interface to upload the file to several other sites at once. If the file exceeds the limit for any given site, Load2All will automatically split the file into RAR files, upload it into several mirrors and provides one download link. This video will benefit those viewers who have a large file...

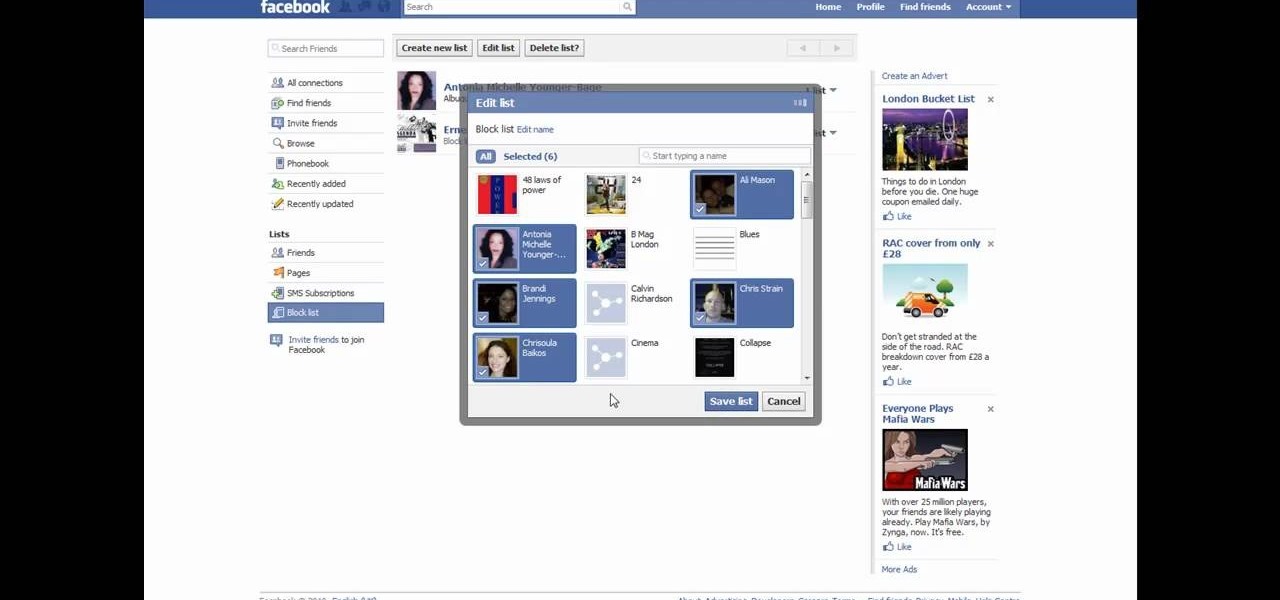
If you would like to use your Facebook chat but are hiding from a particular friend, check out this tutorial. Sometimes you just aren't in the mood to talk to certain people and you don't want them to see that you are online. In this video, you will learn how to create block lists so that only certain groups will be able to contact you and see your online status. Follow along with this step by step and decide who you talk to and when.

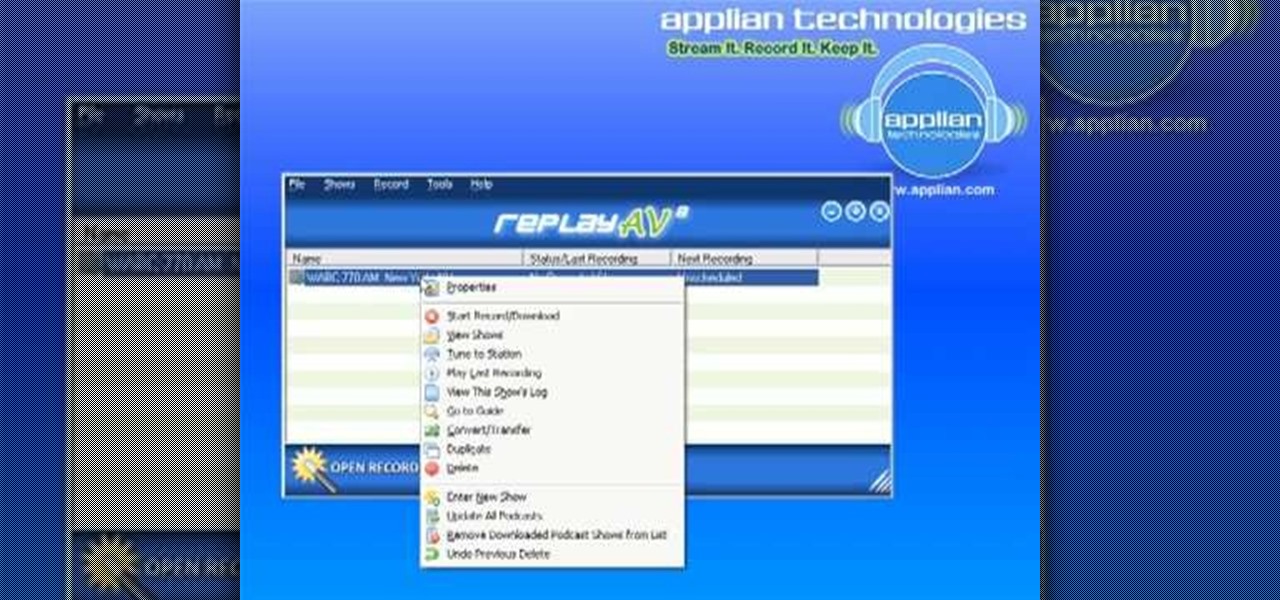
Replay AV is the newest software to come out for downloading steaming audio from the web. Replay AV allows you to download audio from different sources all over the web. You can even record radio broadcasts and set your account to record the station. This video will show you how to add a radio station to Replay AV.

If you're wondering what FoWsc stands for in Guild Wars and what it's all about, here's your lesson. Dooom Box teaches us everything we need to know when it comes to Fissure of Wo Speed Clear: The basics, the parts, the teams, and more.

Wondering how you can finally use that Paragon? Dooom Box shows how to finally start using the Paragon using the Imbagon build in Guild Wars in what he calls the "Imbaguide".

In this video, Dooom Box shows us how to farm raptors quickly an easily using a warrior necro. Clear the raptor cave in under a minute in hard mode using a WARRIOR! Farm.

Curious about the Norn Fighting Tournament? In this video, Dooom Box gives some great tips on the Norn Fighting Tournament in Guild Wars, and some great insight on how to beat Magni The Bison.

Play Acruz online and hack it, too! With this handy hack, you can cheat your stat points, levels, and money. You just need Cheat Engine.

If you want more money, character points, and skill points on Arcuz online, then this video should solve your dilemma. Just use Cheat Engine.

Customizing your user account online for Ford's new SYNC system is a cinch. Simply go to the website and customize news and sports, vehicle health reports, and your personal favorites. You can even start out by adding your favorite destinations for turn-by-turn directions later. Learn how to customize your Ford SYNC online user account.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

After you've spent your Thanksgiving afternoon working through that turkey, mashed potatoes, and three different kinds of pie, you might find yourself heading to the mall to claim some unbeatable Black Friday discounts on iPhone 11, 11 Pro, and 11 Pro Max. You don't have to go in blind, though. Check out our guide below to make sure you're saving as much as possible on the iPhone you really want.

After hosting an augmented reality experience using its Snapchat Landmarker technology at the Statue of Liberty, Snap is now giving creators the opportunity to create their own Lenses with Lady Liberty.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

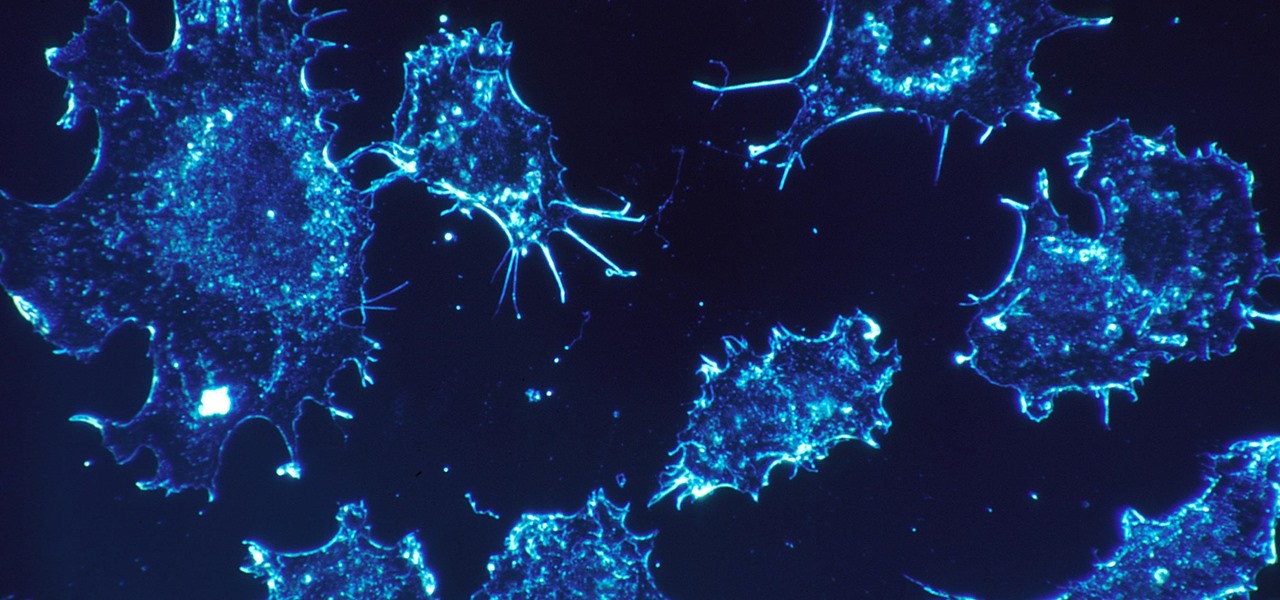
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!