Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Oops, you've forgotten who you are again. Well, at least what your AT&T Online Account Management username is. No worries, it's easy to recover and this simple how-to will show you the way. Stop trying to guess and get your answer pronto!

If you're looking for an easy way to manage your AT&T phone bill and cut down on paper usage, this how-to is for you. Using AT&T Online Account Management portal for small business customers, you can manage your account and billing prefrences.

In this video tutorial, we learn how to create and share digital scrapbooks with Scrapblog, a new virtual scrapbooking platform. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started creating your own scrapbooks online, watch this how-to from the folks at popSiren.

Forget Skype. Google's in the market for online phones, and their answer lies within Gmail. It's call Google Voice and Video Chat, and it allows you to make free domestic phone calls from within North America (United States & Canada). This phone service is indeed free, but it does charge for international rates. This video walks you through some of the features, so you can start making free online phone calls with Google Voice.

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...

Friends tired of you forgetting plans? Missing important business appointments? Use your personal computer to improve your organization! Many software programs can help. This video shows you how to sync a compatible online calendar with Outlook 2007, and never miss another appointment again!

This video tutorial is in the Computers & Programming category which will show you how to use the online discussion site Voice Thread. Voice thread enables you to create an online discussion with your students. In this video you will learn how to open an account, how to open a thread and how to post a comment on it. Go to the site. On the right hand top corner you will find a coffee cup. If you click on that, it will ask you for a username, password and email for opening an account. After you...

Got your eye on that new Phllip Lim clutch on Net-A-Porter.com? Save up for an investment piece you'll use for the rest of your life by selling some of your old clothing to a consignment store or online.

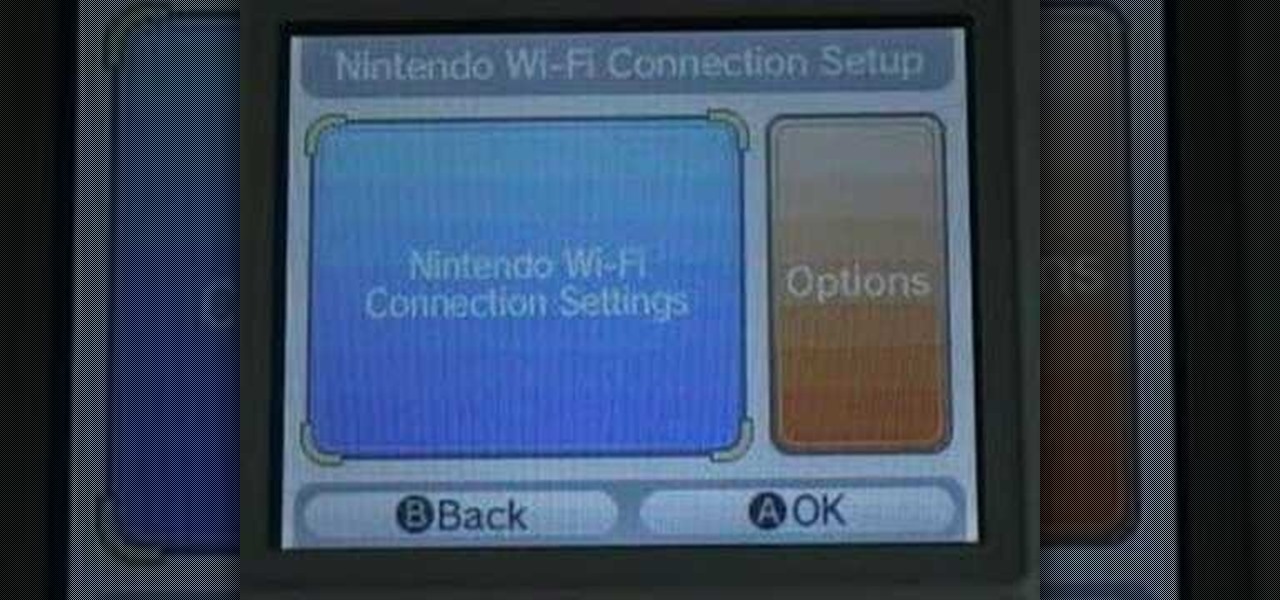
Did you think you needed to buy a Nintendo DSi to get online? Well, think again! In this video tutorial, learn how to connect your regular Nintendo DS to WiFi, from anywhere. Follow along with this step by step video and learn how to set up your wireless internet on your Nintendo DS. It is fast, easy and requires no download. You will be online in no time.

Doom Box explains how to do a hero setup for Guild Wars called "Discordway", so that you can clear hard mode the easy way.

A little precaution can go a long way to securing your online banking experience. Use these tips from Tekzilla.

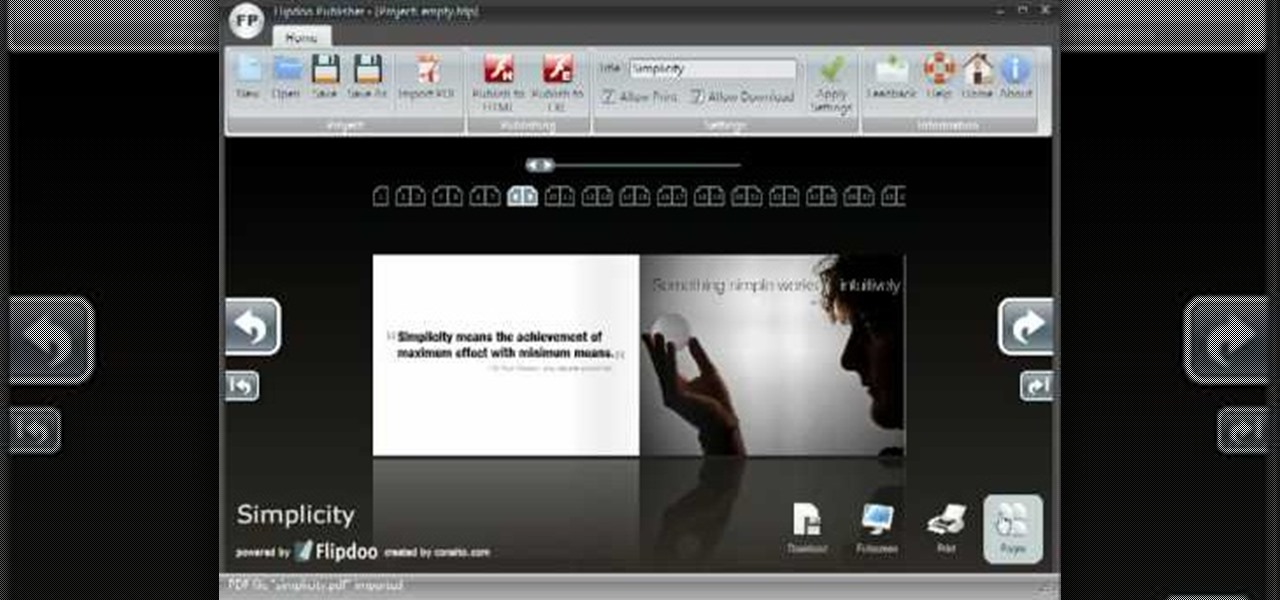
If you'd like to create a cool presentation with Flash, check out this video and the Flash plug-in flipdoo. Flipdoo allows you to build stunning flash flip books for both online and offline use in minutes. You don't need any additional software. Import your PDFs, configure book look & feel and publish. This is the best way to create digital ( electronic ) editions such as any type of publications, magazines, brochures and catalogues. Flipdoo Publisher is a Windows desktop application that hel...

The internet has created amazing new standards for how closely information can be followed. If you want a portable analog unit that will monitor one important piece of online info continuously and have some DIY electrical knowhow, watch this video. It will show you how to use an Arduino Ethernet Shield to make an internet meter to monitor email, stocks, and other online info on a simple analog display. You will need to know some PHP to make this work.

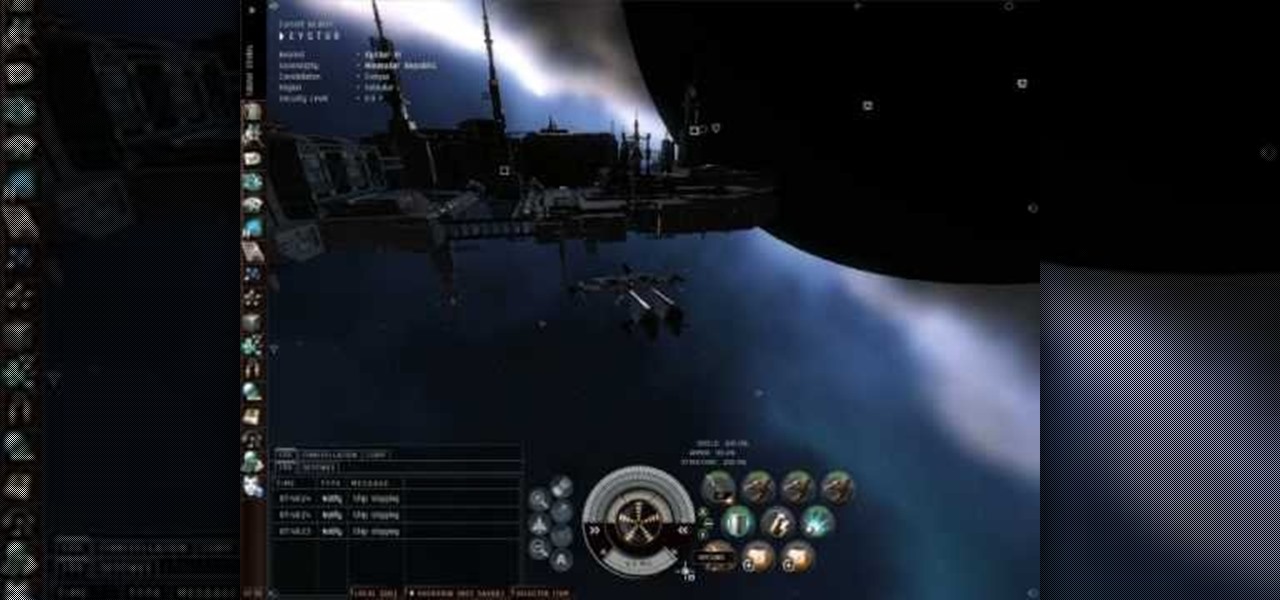
Weapon grouping has become available in the Quantum Rise expansion for EVE Online. This allows you to load ammunition for up to three separate weapons at a time - useful in a dogfight! This tutorial shows you how to group your weapons to take advantage of this new feature.

Selling isn't easy. And it isn't any easier online, at least, until you get set up. It sure beats the streets. But how do you get ready to sell online?

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play the basics in Evony online. See exactly what the game Evony is!

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

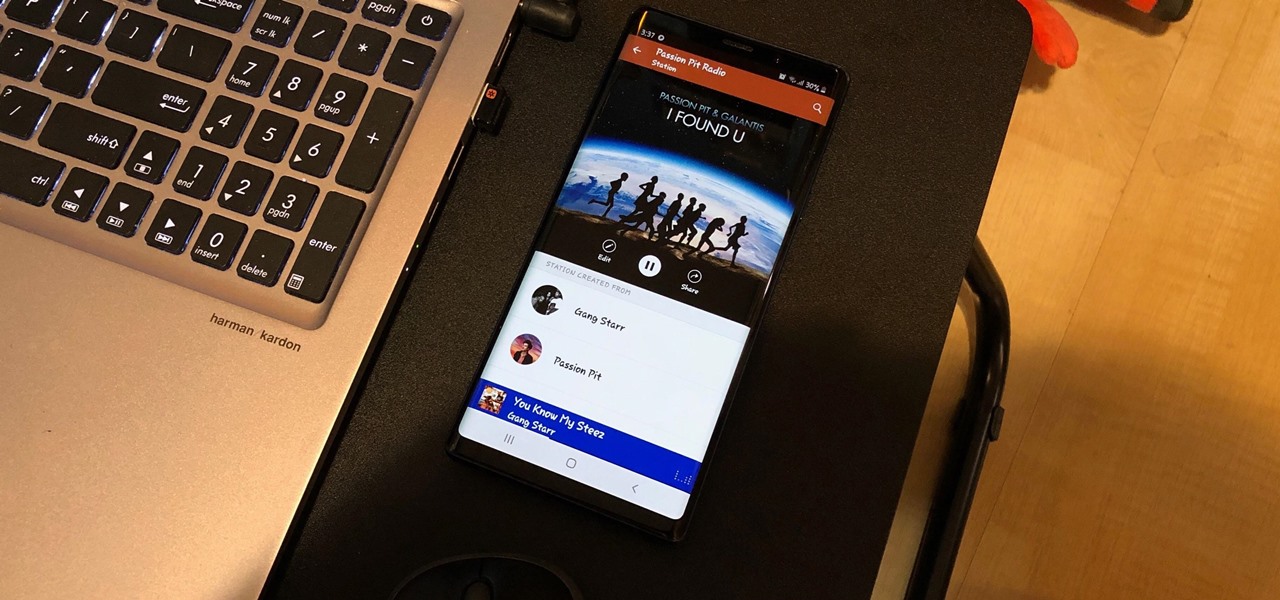
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.