Wolves in Sheep's Clothing: So, yes, that means there are more than one wolf in sheep's clothing. Hit the map marker and this mission will immediately kick off. You need to check the nearby street in front of a large, regal building to find a certain somebody. The area is marked green on your map, so don't waste time anywhere else. Just turn on eagle vision and, once you've spotted the target, a cut scene will take over.

Arivederci: Or is that Arrivederci? This mission won't take long. As long as your notoriety is at zero (and it has to be), this mission is a piece of cake. You have to escort Ezio's mother and sister across town to the city's exit. The city is temporarily packed with guards, but they'll pay you no mind, even if you run. Just avoid bumping into guards and you'll be a-okay.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. Sure, you can go online and send the first flowers you see, but a little thought and planning will go a long way toward impressing her. You will need a friend or relative of the recipient. Send her favorite. If she’s ever mentioned a favorite flower, buy that. You’ll get bonus points for listening to her. If you have no clue, ask a friend or relative of hers ...

Work out the butt and thighs with press exercises. Learn about butt and thigh presses in this dumbbell fitness video. Take action: place feet higher or lower depending on target area, bring thighs to chest without rolling hips, but do not lock knees. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting an...

Learn how to do incline barbell presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

How to unlock everything - all of the hidden characters and stages - Super Smash Bros Brawl (SSBB) for the Nintendo wii.

Ever since Snapchat rebuffed its acquisition attempts, Facebook has morphed Instagram with features from Snapchat, such as stories, chat, and, of course, augmented reality.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

You never want to stop learning. Whether you're facing a career pivot or want to better understand the vocation you've chosen, there's always room for growth. The most successful workers are those who make education a lifelong pursuit.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

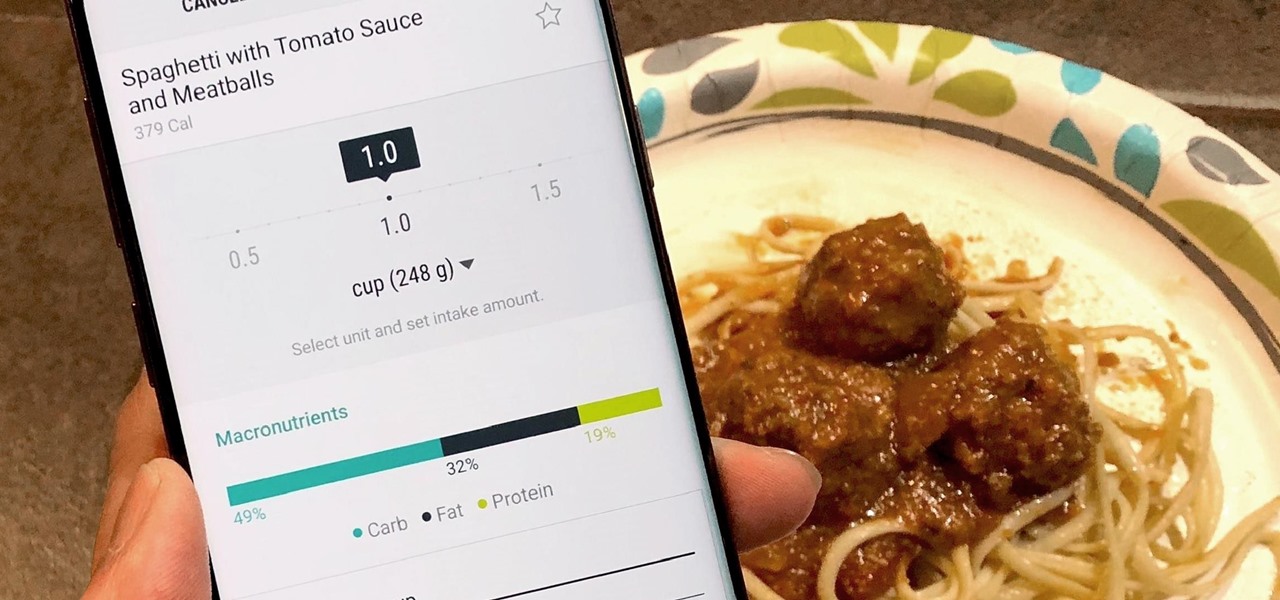
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

The holidays are here, which means a slew of new smartphones are set to be gifted to loved ones in the spirit of giving. Of course, a great case to compliment and protect that precious flagship is a must, regardless of whether it's a OnePlus 6T, iPhone XS, or Galaxy Note 9. And while quality cases usually come with a hefty price tag, there are plenty of Black Friday deals to keep you from going broke.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

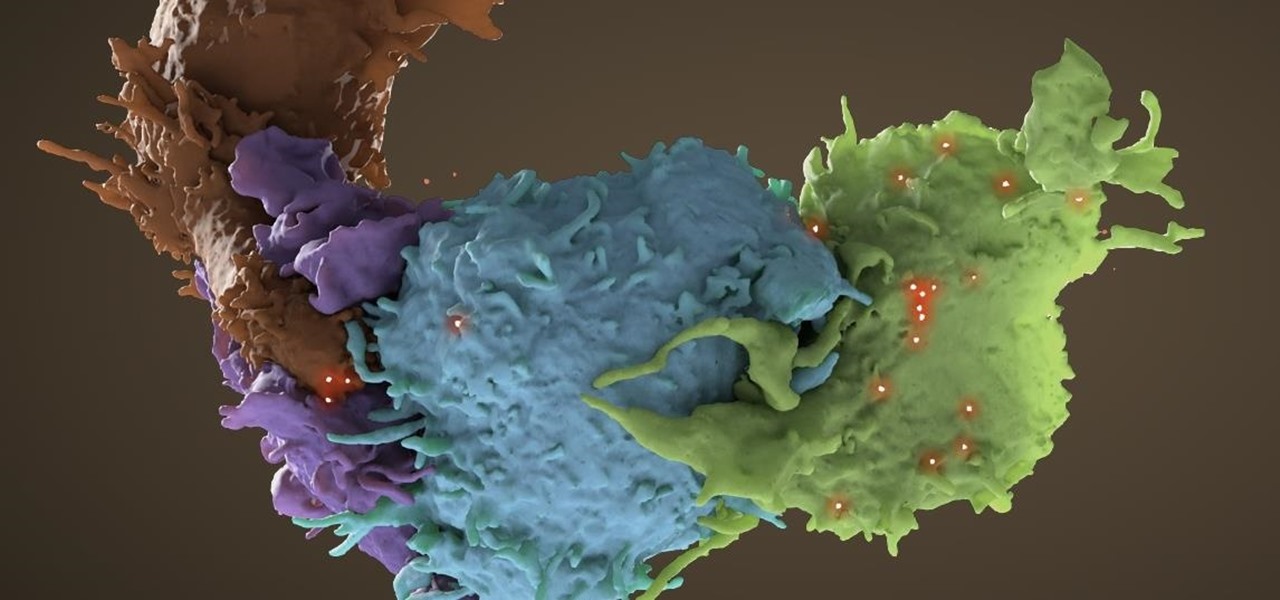
A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.