Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.

Halloween is only a few short weeks away, and most people are scrambling to get their costumes together before the big night. The secret to a great getup is all in the details, and including your pet in the fun can be exactly what you need to take your costume to the next level.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

For the majority of my math classes in middle and high school, a graphing calculator was a must. While the calculators were very useful to have, they were quite steep in the price column. After losing the TI-83 graphing calculator my parents bought me in high school, I had to save up my own money to buy the next one.

The Pro Bowl has definitely had its ups and downs. It's probably the most glorified exhibition game on earth. I mean, even the NFL Commissioner, Roger Goodell, wanted to cancel it this year.

Online shopping is way more convenient than brick-and-mortar stores in a number of ways, not the least of which are the discounts. But with so many online stores and sites like Amazon which feature thousands of retailers, how can you know you're getting the best deal?

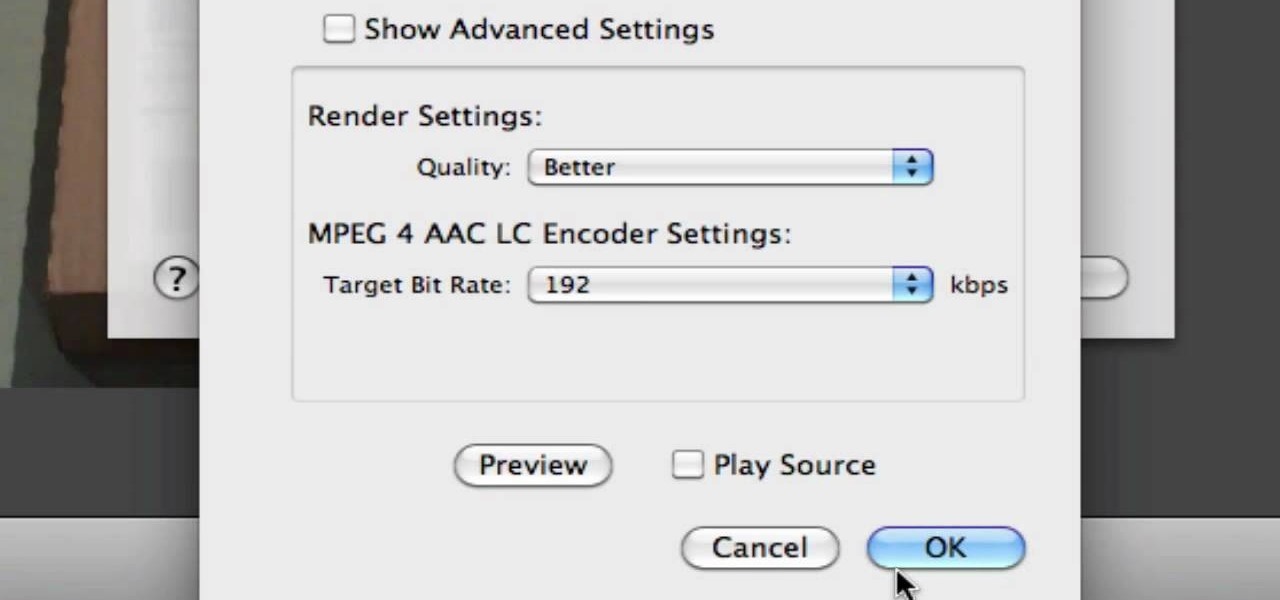
In this video from AppleGenius0921 we learn how to export videos using Screenflow in HD. Launch Screenflow, make sure you're editing is complete and go to File, then Export. A window will come up asking the name you want to save it as and where you want to save it. Make a good title that is relevant to your video. Now click customize. Then click settings. Now go to compression type and double click H.264. Set the quality on Best. Click OK and use no filter. Now go to size and click 1280x720 H...

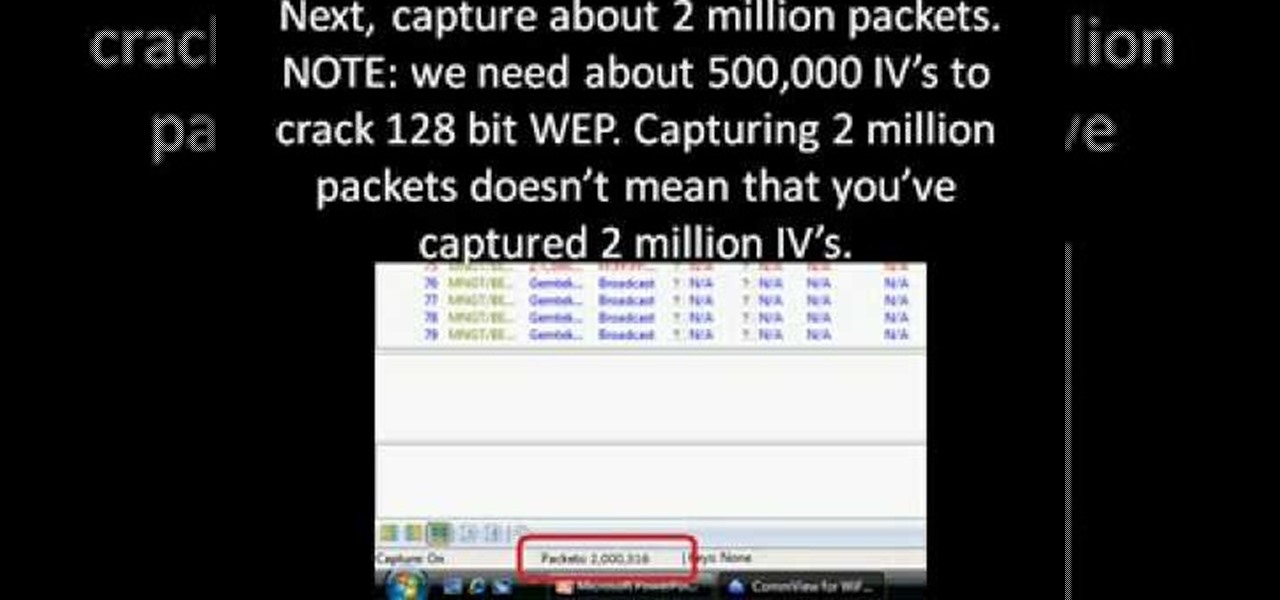
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

In this Business & Money video tutorial you will learn how to make a successful curriculum vitae or resume. This is the first step in getting your dream job. A well written CV captures the interest of the person who is reading it. Think yourself as a product and the CV is a piece of paper that is going to sell you. Don't be afraid to sell your skills and abilities. If you don't do it, nobody else is going to do it for you. First thing on top is to put your name; centered and bold. Then leave ...

Almost 125 million people worldwide suffer from what is known as psoriasis, the skin disease that's marked by red, itchy, and scaly patches that are hurtful, if not visually god-awful. There can be a little hope though for psoriasis sufferers. Though you can treat and control psoriasis, characterized by dry scaly patches of skin, the progress is often erratic and cyclical, so be patient and consistent in executing these steps.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

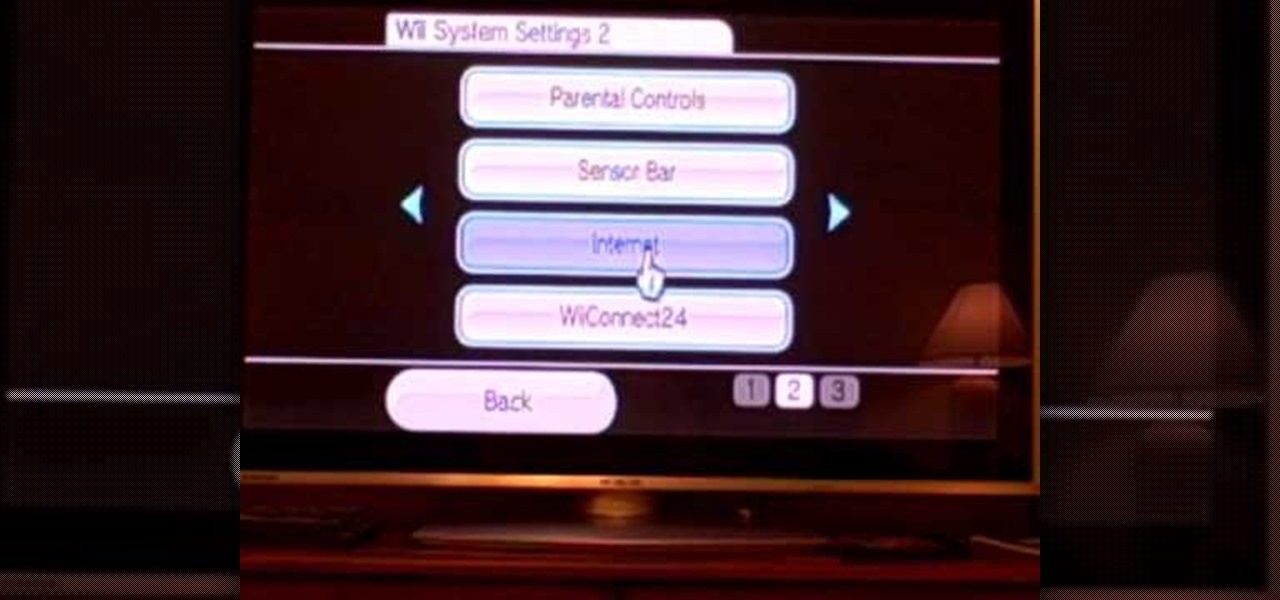
Did you know that your Nintendo Wii can go online? If you haven't been using the Internet with your Wii, you are missing out on some of the system's coolest features. With an Internet connection, your console can surf the web, watch movies from places like Netflix, or connect with other players to compete online. In this tutorial, learn exactly how to connect your Nintendo Wii to the Internet and start using your system the way it was meant to be used.

In this edition of ClubHouseGas, with host Casey Bass, basketball coach Chuck Melito shows us how to shoot free throws. He shows us how to work on both the mental and the physical approach to free throw shooting. A right-handed shooter should place his right foot at the center of the basket. A left-handed shooter should place his left foor at the center of the basket. Then it's important to get balanced, so you're not leaning to one side or another, or more weight on one foot than the other. ...

John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

The video presents "How to start your own Clothing Line Business". The steps include getting the financing, designing the prototype outfit/s, producing the line of clothing, promotion and sales. A good way of financing for a small business such as this is to sell your idea to family, friends and even colleagues. Research and prepare the business plan for your clothing line and be passionate about it in your presentation to convince them to fund your business. The next step is to get the produ...

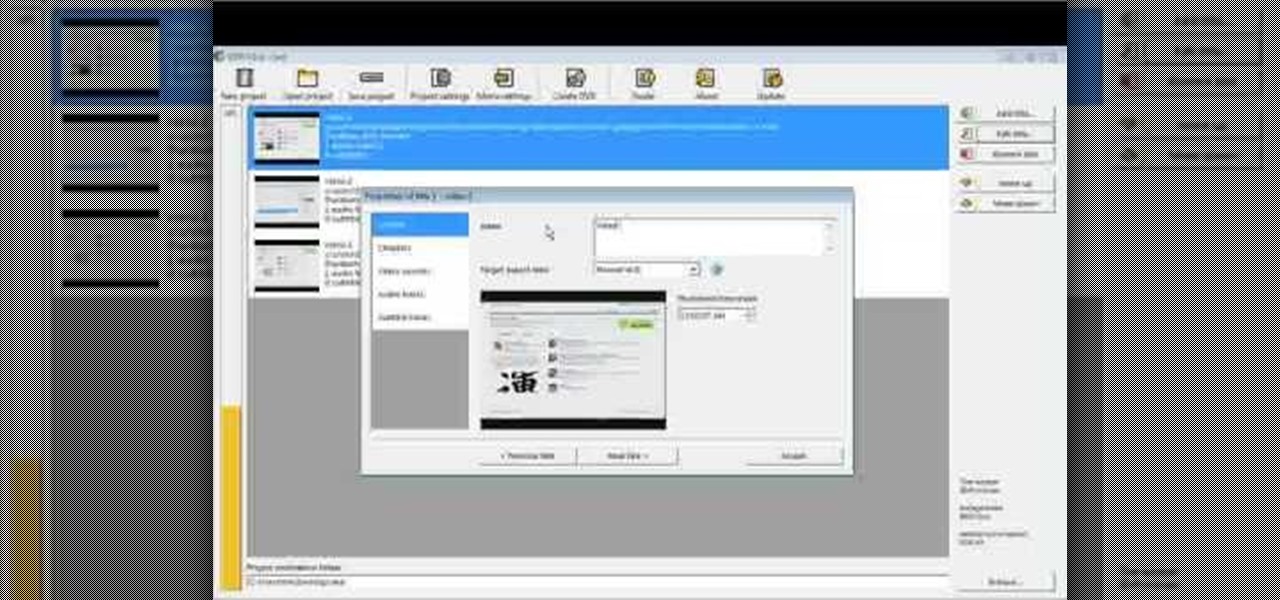
This video tutorial from Foreclosureresearch presents how to burn video files to a playable DVD using DVD Flick application.First you need to download and install free software called DVD Flick.You can find it at DVD Flick.Once it's installed, run the program. First thing to do is to set your Project Settings. Click Project Settings from top menu. From Project Settings window you can name the project, select Target size (size of your DVD), Encoder, Thread count, DVD format, bitrate, playback ...

Golf Link demonstrates how to identify whether your golf swing plane is correct. The swing plane is the path described by the golf head that controls the direction that the club head is traveling through when it impacts the ball. An on plane swing will have the club head directly traveling towards the target at the point of impact. That and a square face will make a straight shot. If the swing comes inside or below the plane, it will produce a hook shot or a push shot. A swing that comes outs...

You can manipulate the AF fine-tune on your Nikon DSLR in order to optimize the sharpness and resolution of your lenses. This is a great tool for achieving the highest picture quality possible.

You can organize your closet with simple drawers and shelves or racks that you purchase at a discount store such as Target. Outside of your closet you can have drawer space (use transparent drawers) by labeling your own drawers with large labels that you have written the contents of the drawer on and placed this at the front where it will be visible. The drawers can be divided into short sleeved sweater tops, long sleeved sweater tops, tanks, vests, short sleeved tees, long sleeved regular to...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

This is a Computers & Programming video tutorial where you will learn how to take screenshots on Mac OS 10. 5. Andrew Grant says there are several ways of doing this. The easiest way is to hold down the Command and Shift key and press 3. You will get a screenshot of the entire desktop. To take a screenshot of a selected area, hold down the Command and Shift key and press 4. The cursor now changes into a target. The figures next to it are the values of the pixels from the left hand top corner....

In golf the grip is the key essential feature and this video shows you the most common mistakes. It is intended for a right handed golfer - left handed players should note that the opposite applies. Let your hands fall to your sides and let your fingers fall to the grip. The video shows a weak, neutral and strong grip. The strong grip shows a V shape formed by the left thumb and forefinger pointed to the right shoulder. The palm of the right hand should face the target. You should let the fin...