
Don't Be a Script-Kiddie part2: Building an Auto-Exploiter Bash Script
Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.


Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.
Welcome back Hackers\Newbies!

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Welcome back, my hacker novitiates!
UPS understands how important small business cash flow management is to increase profitability. UPS Billing Center allows companies to download their bills, allocate costs and pay online, so they can bill customers faster and get paid faster.
Video: . Learn how to play "Everybody talks" by Neon Trees. The tutorial is made by PianoCrumbs and available online at:

With all the excitement over the Mars rover landing this weekend, you might also want to know that Google has gotten their cameras into the Kennedy Space Center for their largest collection of Street View imagery to date. In total, the explorable facility totals 6,000 panoramic views. The views include the space shuttle launch pad, the towering Vehicle Assembly Building, and a up-close and personal view of a space shuttle's main engine.
If you've completed chapter 3 of Disgaea 4: A Promise Unforgotten, you can access the map maker and start to create your own maps for multiplayer. This guide teaches you how to use the map maker in Disgaea 4 to create unique maps for use against your online opponents!

If you're interested in joining or creating a fantasy football league, take a look at this guide on how to use leagues in ESPN Fantasy Football and learn the differences between the leagues. You can choose to play in a public or private league, depending on if you want to limit your fantasy league to your friends and family or if you want to play against other team owners you meet online.
Make sure that your Google+ profile only reflects the information that you want it to. Control your online presence and privacy in Google's social network by following the suggestions of this video. Learn how to edit your Google plus profile.
One of the coolest features of Infamous 2 for the PlayStation 3 is the ability to create your own missions. Set your preferred objectives and obstacles when designing missions, then play through them. You can also edit other people's missions online.
If you want to get your Facebook chat history, here's a way to do it, even if your friends aren't currently online. This video walks you through the steps to recover chat that you previously had, even with friends who are currently offline. Click here for more details.

If you're with AT&T and need to change wireless-user information, you can do it easily through the business mobility online customer portal, AT&T Premier. Whether you're needing to change email addresses, phone numbers or physical addresses, this is the place and way to do it.

Now that you've got a BlackBerry smartphone you'll want to get online and start emailing the world about it. You can use an exisiting email account and this simple how to by AT&T shows you the necessary steps to do it with OS 5.0.

Watermarks are essential for branding your online creations, but you may not always want a static image. If you're looking to create a rotating text or graphic logo, this tutorial is for you. Using 3D Studio Max, learn how to put your brand in motion!

Start playing one of the most popular browser based science fiction games DarkOrbit! This tutorial gets you started, showing you how to create an account and choose your faction (Mars, Venus or Earth). Then the basic system is demonstrated, so you can start exploring space!

In this video tutorial, we learn how to use Plotbot, a web application for writing and collaborating on screenplays. For all the details, including a complete demonstration and detailed, step-by-step instructions, and to get started using Plotbot yourself, watch this home-computing how-to from the folks at popSiren.
In this clip, you'll learn how to log into a Blackboard course and upload files, edit and manage files. Whether you're new to Blackboard's popular content management system or CMS or are a seasoned web instructor just looking to better acquaint yourself with the features and functions of versions 9 and 9.1, you're sure to be well served by this free video software lesson.

In this installment of the online prank video institution Do Unto Others, you will learn a wide variety of great ways to mess with people in a variety of situations. Some of these situations include at a job interview, at the gym, when meeting a new roommate, and when using a public restroom. All are sure to add a little spark and concern to your fellows' day.
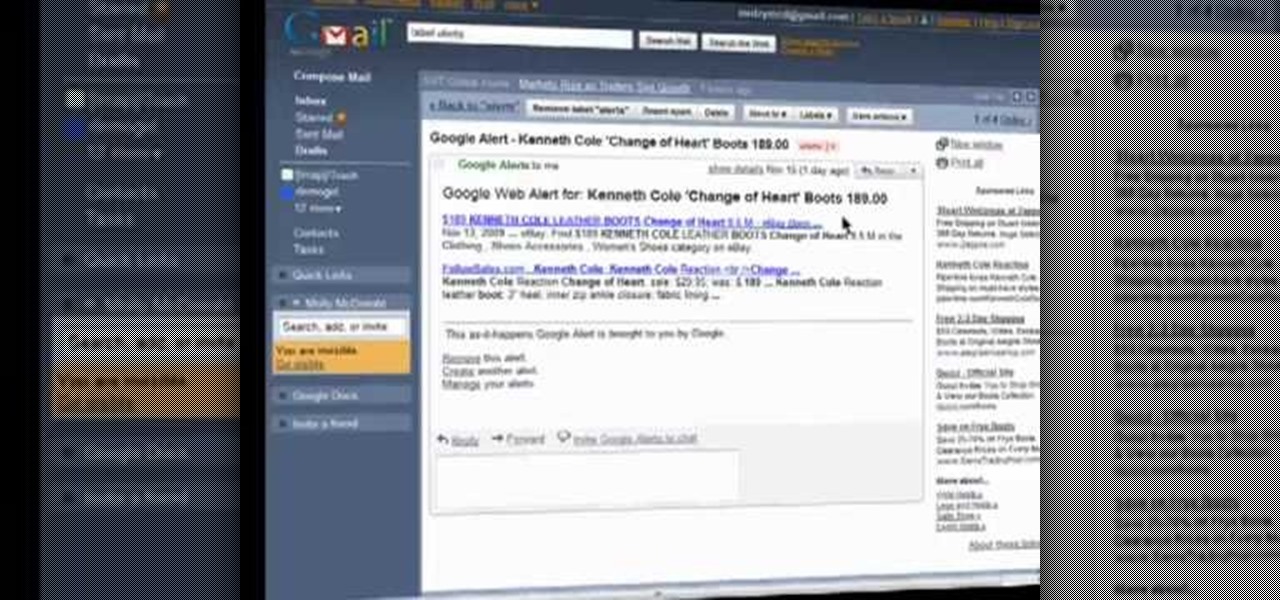
Looking for an easy way to track price changes? Look no further. In this clip, you'll learn how to use Google Alerts in tandem with Google's Product Search comparative shopping tool to monitor price changes and find the best value. Fore detailed, step-by-step instructions, and to get started using this online shopping trick yourself, take a look.
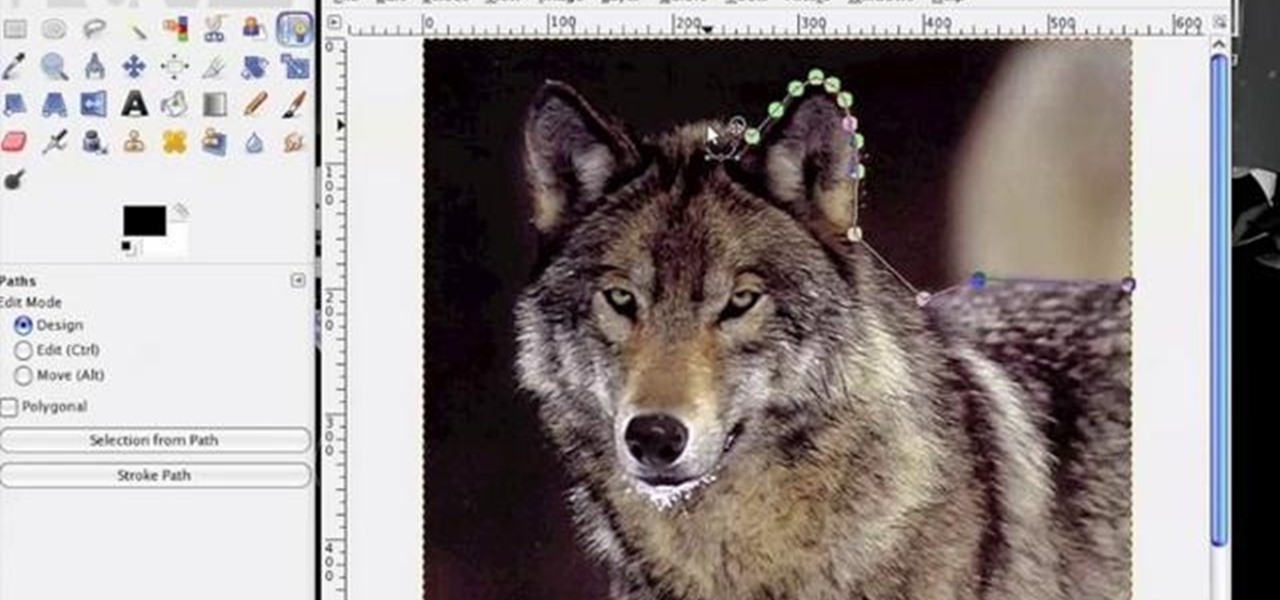
In this clip, learn how to use the Path tool in GIMP and edit your photos quicker and easier. This video will demonstrate exactly how to use this effective tool. GIMP is available for free online for both Mac's and PC's and is basically a freeware version of Photoshop. Enjoy!
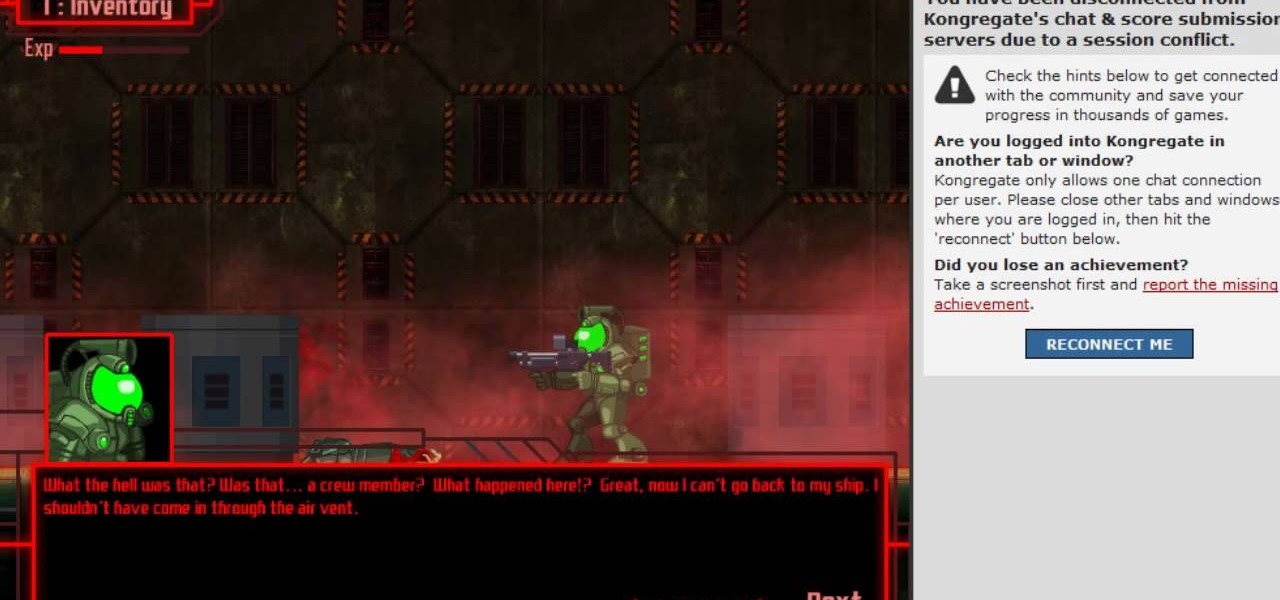
The Breach is one of the many popular online games available from Kongregate Games. Like any game, it can be rendered more enjoyable in the long-term by cheating at it. This video will show you how to use Cheat Engine 5.6 to hack the game and give yourself more experience points, making your character nearly indestructible. Don't let the zombies win, watch this video!
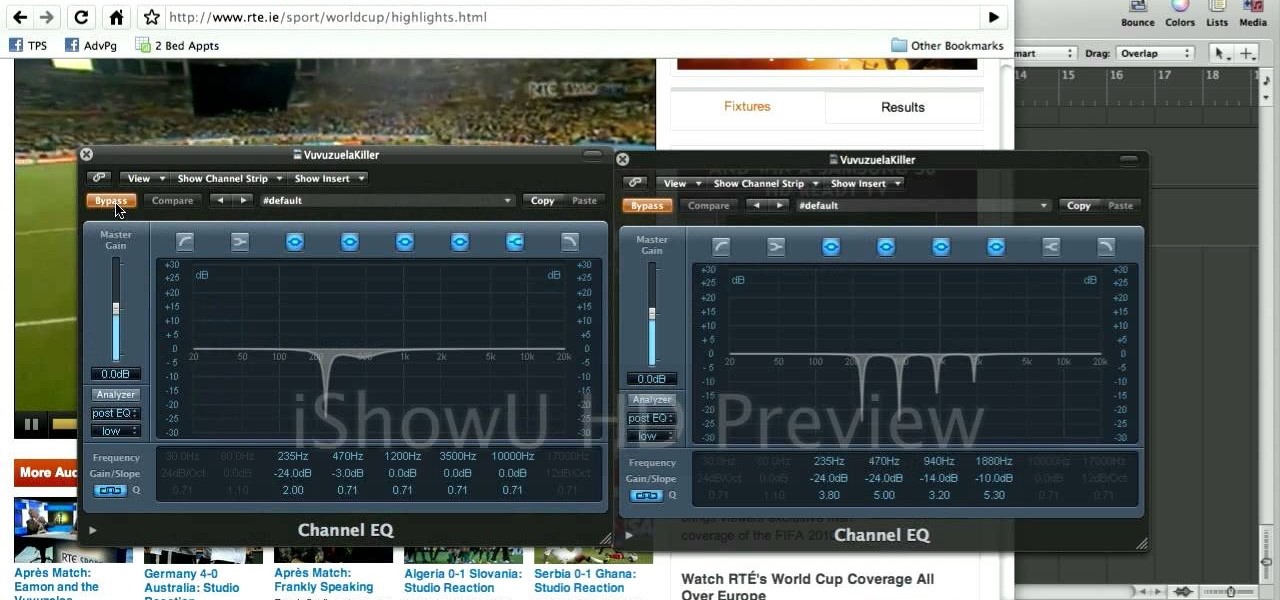
In this tutorial, learn how to use Logic Pro to alter the sound of the World Cup games so that you filter out the vuvuzela. The vuvuzela is a South African horn that is blown for 90 straight minutes and to those of us that are not from South Africa, sounds more like an annoying swarm of bees. Follow along with this quick tutorial and learn how to lessen the bumble bee sound if you are streaming your games online.
Pixel Basher is a new online game available from Armor Games. It has it's feet firmly planted in the Breakout! tradition, featuring a platform, bouncing balls, and blocks that need breaking. This video shows you how to use Cheat Engine 5.6 to hack the game, changing it's associated numerical values to make the game easier and more fun.
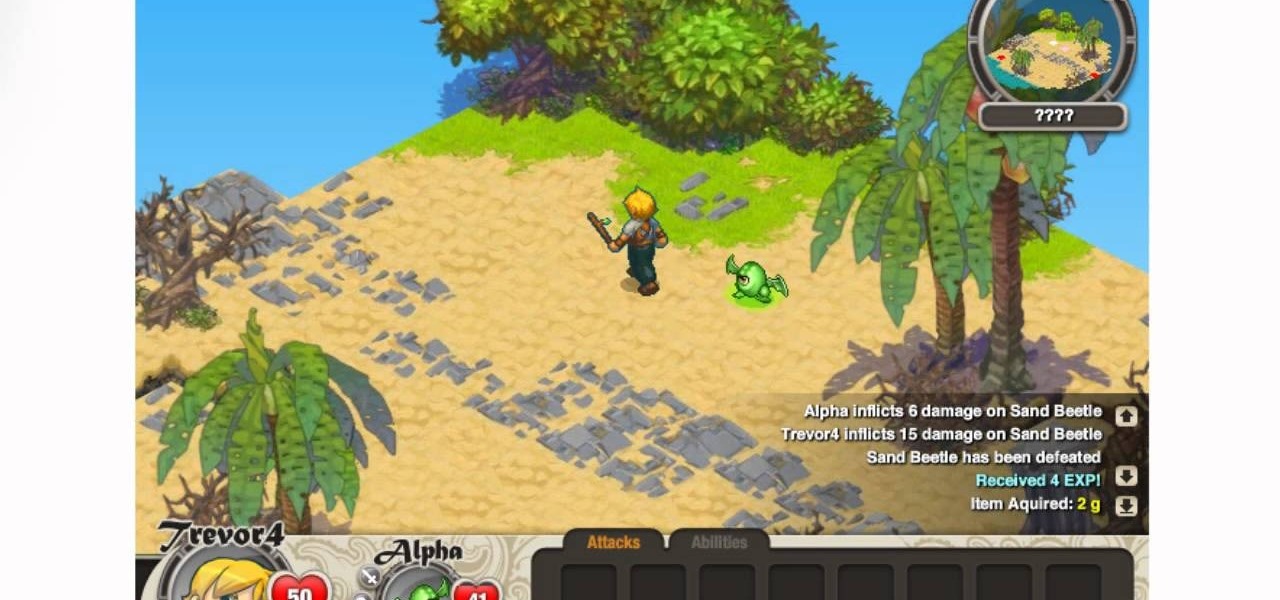
Castaway is one of the growing family of popular online games available from Armor Games and Kongregate Games. This video will teach you how to use the infamous cheat engine to hack the game, increasing your strength and other statistics using an 8x process. Never languish with a weak character again, cheat you way to the top!

Greeting cards are getting more and more expensive these days, costing as much as $15 for four if you're getting the top quality ones from online boutiques. Stop spending precious moolah you could be using to purchase presents for your friends and family by making your own Christmas cards.

With the spread of smartphones and free online games, the "Freemium" model of product distribution and monetization has become prevalent over the last several years. At it's essence, it is handing out software products for free and then allowing customers to pay for in-software services using microtransactions. This video features some businessmen who do business in iPhone apps discussing how they use "Freemium" systems in their apps to make the most money possible while providing great servi...

If you have a high-speed Internet connection, your cable subscription might be redundant. This consumer's guide from the folks at CNET TV presents an overview of the various options available to you — all of which will save you money over cable in the long run. For specifics, and to start seeing whether you too would benefit by dropping your cable television subscription, give this guide a look.