In this Pets & Animals video tutorial you will learn how to train your dog to perform the "cop-cop" trick. In this trick the dog learns to put its feet on your feet. Step 1 – teach the dog to target a book or a mat with their feet by offering them some treat. You can do this either by appreciating or clicking when both the feet touch the book. The next step is getting the dog to target the book with their feet while they are between your legs. You have to continually reinforce the dog to ma...

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

The SOFLAM is a gadget that you can use in Battlefield 3. It is a team based gadget that you deploy and use to laser target. It is different than a mortar and can be a little hard to use. This guide will show you how to get the most out of a SOFLAM so that you can tear up the other team.

This Giant Bomb walkthrough will take you through the Iron Golem boss fight in Dark Souls. The Iron Golem is the last boss in Sen's Fortress and has a long reach. You will need to target the back of its legs in order to defeat it.

Just because you need to assemble an outfit for work doesn't mean it has to look all boring and aging. As long as you stay mostly covered up and don't pull out your neon-colored cheetah print stockings, you'll do just fine accessorizing and dressing fashionably.

Pretty Little Liars is the newest part of the increasingly puzzling lineup of shows on ABC Family that seem to be creating a new demographic to target as they go along. The girls on it are very pretty, and this video will show you how to create a makeup look inspired by the show's star Alison DiLaurentis.

THis video from accredited 3D art instructor Andrew Klein covers how to create symmetrical and asymmetrical blendshapes using the 3D sculpting program Zbrush. This is a fairly complex process, utilizing transpose masking features, move brush, smart resym, and morph target tools to accomplish its goal of creating a really cool animated 3D mask.

In this video tutorial, viewers learn how to properly shoot and sight in a compound bow. It is recommended that users use a release. Your body should be perpendicular to the target. Hold the bow vertically, and hold it with a relaxed and secure grip. When you are ready to begin shooting, learn a technique that will help you relax and steady the bow. When you draw the bow string back, you should be looking through the peephole on the bow string and where the target and pins come into view. Thi...

In this video, Tom Leese, Director of Instruction at Angel Park Golf Club, gives pointers for your pre-shot routine in golf. Important in the transition from the practice range to real games, your pre-shot routine helps you get situated and ready to play real competitive golf. Tom explains, first, how to set your lines, taking a straight and purposeful line down course where you want your ball to go, and remaining fixed on it, as you approach your tee. Then, when positioned at your ball, he t...

In this Photoshop CS3 tutorial you will learn how to use the knockout feature. This advanced masking technique allows you to move a targeted layer around, revealing the layer underneath. This video will show you how to reveal a creepy skeleton under a monster werewolf right in Photoshop. This classic technique lives again! Learn the subtle qualities of the Deep, and Shallow, Knockout feature in Photoshop.

Hip flexors are important muscles to target when weight training to build functional strength in the legs. Learn how to do hip flexor exercises in this strength training video. Take action: knees to chest exercise targets core, hold weight between feet, raise knees as high as you can, start in push up position and bring alternate knees to elbows, and work for quick reps and endurance. Tom Clifford, the instructor in this how-to video, has a degree in physical education, fitness and health fro...

Katherine and Kimberly Corp show you how to do a ten-minute (1o min) pilates arm workout using stretch bands. This workout targets every major muscle group in the arms and helps maintain alignment and ab strength.

In this video tutorial you are told how to use the Wagon Wheel Cue Ball Control training method. This is called Wagon Wheel because each target ball is aligned to RESEMBEL the spokes of a wagon wheel. Set your cue ball and your object ball in the same position each time. The objective is getting the cue ball to one balls width of the target ball. Using THE FOLLOWING cue ball, direction and speed. By using a piece of chalk the instructor helps line up the balls. By using either a quarter stick...

Component 1. Frame And Posture. The benefits of dance shoes never outweigh the benefits of proper spin technique. Your body should be straight lower abs and stomach should be tight. Your arms are in proper position. If you lift your hand it should be in 90 degree angle.

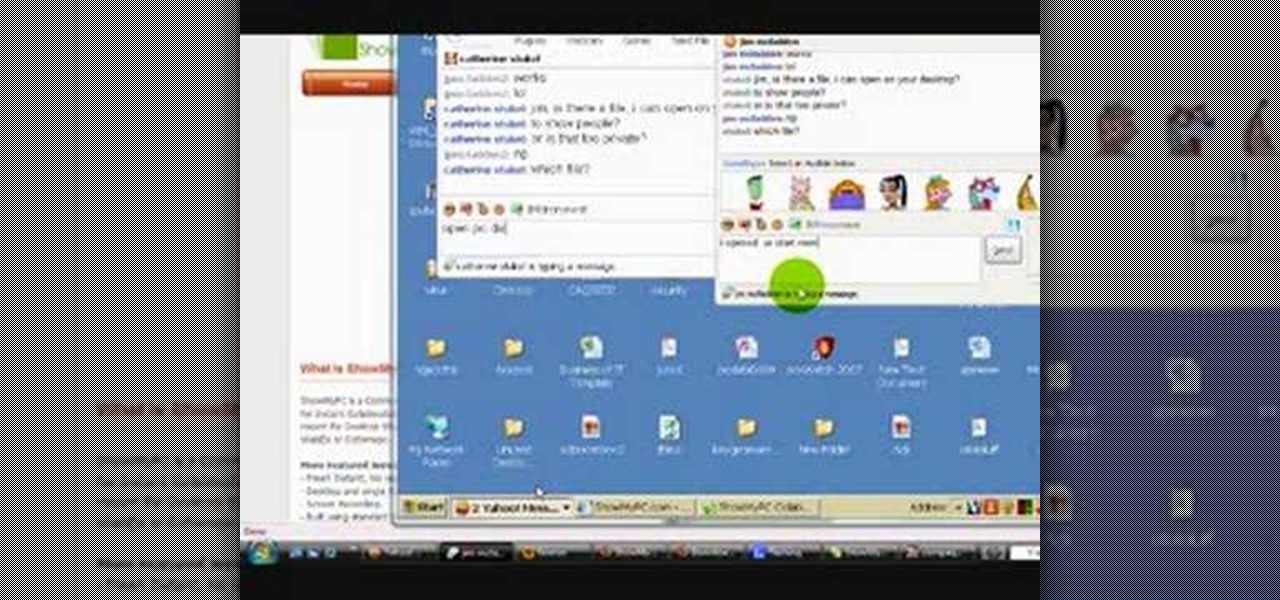
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

What's in a name? Quite a lot. Learn how to choose a good one that targets your desired demographic. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.

Party poppers are magnificent. They can be used for a plethora of pranks— basically, any prank where the victim / target has to open something. You can use party poppers on practically any household item, but this video covers the much used dental floss container. The exploding floss prank is easy to do yourself, and requires only the floss container, the party poppers, scissors, and a screwdriver. Once your prank target goes to use their floss, they'll have quite the grin.

In this video tutorial, viewers learn how to shoot a compound bow. It is deeply recommended that users who use a compound bow should have a release. Put your arrow on the string and push it in until you hear a click. Now hook the release into the D-loop. Your feet should be shoulder width apart and the tips of your feet should be on the target line. Now look at the target and pull back the bow. Your hand should be at the point of your jaw, arrow at the corner of your mouth and string on the t...

In this video tutorial, viewers learn how to avoid a bad finish to cure a golf push shot. Usually, when players make a swing for the ball, their arm separates from their body. This will take the club to the right of the target and as a result, pushes the shot. To correct this, connect your left arm to your left side as you make a swing. This will allow the club to stay with your turn and go down the target line. This video will benefit those viewers who enjoy playing golf and would like to le...

In this video tutorial, viewers learn how to burn fat with a cable workout. These exercises will require a cable machine. There are four exercises in this workout. These four exercises are: cable wood chop, reverse wood chop, one arm cable row and exercise ball cable crunches. When performing these exercises, do not use a heavy weight. These exercises mainly target the abdominal and core muscles. They also target biceps, obliques and back muscles. This video tutorial will benefit those viewer...

How to aim your shot in World Golf Tour in four easy steps. When aiming for a shot, simply click the target and drag it on your desired location. The Yardage Indicator will change as you move the target closer or further. If it turns red that means that you positioned it outside the maximum carry distance for that club. You can also consider changing your club. Hit the Space Bar or click on Zoom to give you the aerial view to get a closer look and adjust for a precise aim. Be sure to take the...

Kathy Kaehler, author, celebrity trainer, spokesperson and mother, gives us a rundown of the best exercises for fellow women and moms on how to target their belly fat and love handles, and specifically the best ways to tighten these areas. Kathy first does advise us that if you're going to be targeting like this the most important thing first will be cardio and general fitness. Then, she offers us first the side plank, where you place one elbow to the ground, lying on your side, and then elev...

The obliques exercise is a classical pilates exercise which targets the abdominal muscles to flatten the stomach and strengthen the core. Keeping the elbows wide helps keep the shoulders down and increases the rotation in the trunk, which helps shrink your waist. Be sure to stretch your legs fully each time and stop the knee at 90 degrees of hip flexion to encourage greater strengthening of the abdominal muscles. Watch this how to video and you will be strengthening your obliques with pilates...

In this video tutorial, Chris Pels will show how to deploy a web site using the Copy Web Site Tool in Visual Studio. First see how to connect to a remote web site and deploy an entire site to the target location. Next, learn how to synchronize an entire source and target web site. In addition, see how to copy and synchronize individual or groups of files including how the Copy Web Site tool provides status indicators of differences between files. As part of this process see how the tool provi...

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

If the name Leroy Jenkins elicits a reaction from you, then you are old enough to remember the iconic title World of Warcraft from its heydey (whether or not you actually played the massively multiplayer online role-playing game).

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.