A poker face is sharp, beautiful, and intimidating, giving your target a peak at the cow without giving away the milk. Bring out your inner card-dealing bovine by watching this professional makeup tutorial by makeup artist Reiva Cruze.

Need to color correct your photos and you're not sure how? In this video, the basics of RGB and CMYK colors are discussed as well as how to use them to color correct everything from everyday snapshots to portrait photographs. By using the eyedropper and the info palette to read the colors in the photos, you can then color correct. Based on the CMYK read out of the color sample targets, you can then adjust the color channels using a curves adjustment to achieve the kind of colors you'd like. A...

First, you have to lay down your net and bundle up the rope in one hand like an extension cord all the way up to the net. Hold the net in the same hand, and grasp the rim of the net with the other hand. When you want to throw the net, grab the net midway with the rim in the other hand, and throw it towards your target with some spin, so the net lands flat on the water. If the net landed properly, it should sink slowly to the bottom, trapping some fish underneath it. To retract the net, simply...

In this video tutorial, viewers learn how to perform a sumo squat. It is the same as a regular squat, except the legs are extended more wider. The bar should be setup a little bit below your shoulder level. Go into a split stance when picking up the bar. Keep your core muscles tight and keep the bar stabilized. Spread the legs wide, pass the shoulder width. This exercise target the leg muscles and helps strengthen them. Inhale when going up and exhale when going down. This video will benefit ...

In this video tutorial, viewers learn how to perform the Siva count sleight card trick. This sleight card trick is very similar to the Elmsley, except it is a reversal. It reveals the cards instead of facing them down. This sleight uses 5 cards, but only reveal 4 of them. It hides the target card. The card that you want to hide needs to be in he middle (3rd card). When going through each card, users have to double drop the card and not allow the spectator to see the hidden card. This video wi...

A lot of the available shooting benches on the market today are well-made, but it's really hard to find one that you're completely comfortable with. That's why it's best to make your own custom shooting bench, made especially for you, how you want it.

The runaway chainsaw family of glitches for Gears of War 2 enable the player to chainsaw a target to death instantly, without having to wait through the tedious process of watching their victim being sawed in half vertically. This video will teach you how to use the glitch in multiplayer, whether hosting or not. Like most of the game's glitches, this isn't all that useful in the game, but if you've finished all the other content, it's time to turn to the glitches!

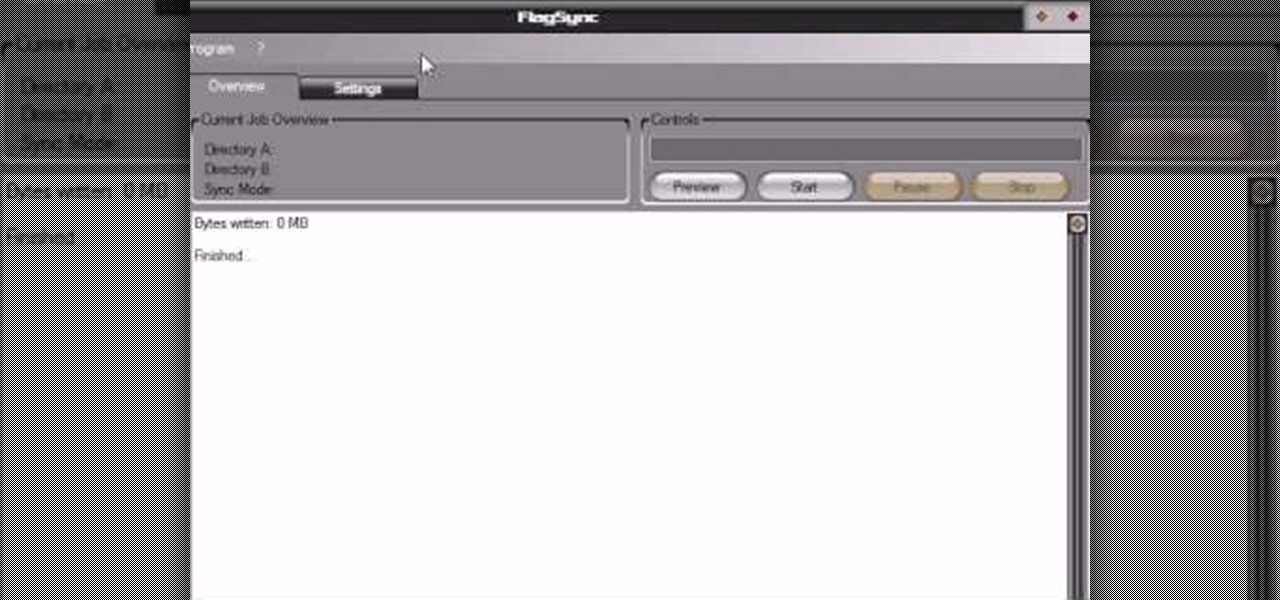
Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Get ready for the boss fight of your lifetime in the Xbox 360 game Darksiders. In the boss fight in Twilight Cathedral, spar against Tiamat. When you reach the bat queen Tiamat she will take offf into the air immediately. Quickly dash to the Inert Bomb Growth around the edge of the arena closest to the flying and then throw it at Tiamat. Now you need to use your Crossblade and target a flaming urn then the bomb you stuck onto Tiamat to light the bomb on fire. Once you detonate the bomb on her...

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

Caged Fighter: Make your way across town and you'll find an injured soldier on the rooftops that gives you some new information on finding Bartolomeo, who should in turn help you with Silvio. You get a large green area added to your map, but note that it's overlapped by a restricted area. Expect trouble.

Knowledge Is Power: But can power be knowledge, too? Pay a visit to Leonardo and he'll cook up a new weapon for you based on a mystery codex. After the cut scene, move out to the yellow map marker and you'll get some directions on how to use your new pistol. Lock onto the three dummies across the river and shoot 'em. Holding down the fire button builds up your accuracy, making it possible to hit the distant targets. When all three targets are shot, return to Leonardo to complete the mission. ...

Infrequent Flier: Fly through this episodic mission and take control. As you take flight, immediately pause the game and check out your map. You can see the locations of all of the fires in the city, as well as the target to the far, far southeast. If you make a simple beeline for the target, the Palazzo Ducale, you won't get the updrafts you need to maintain your height and infiltrate the fortress. Instead, you need follow the trail of fires that lead you east and then north before finally t...

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Aerobics are targeted by total physical fitness: strength, flexibility and cardiovascular fitness. Aerobics can be taken in classes and are usually done with music. To practice aerobics you should follow an instructor, stay in motion, use arms to lower or raise intensity, and strengthen heart rate. With this how to video soon you will be able to practice aerobics.

Have you tried working out with a swiss ball? A swiss ball and outer thigh lifts are an essential part of toning your legs and strength training. This fitness how-to video demonstrates how to target the outside of your thighs with outside thigh lifts. Learn about muscle training and exercises in this video workout.

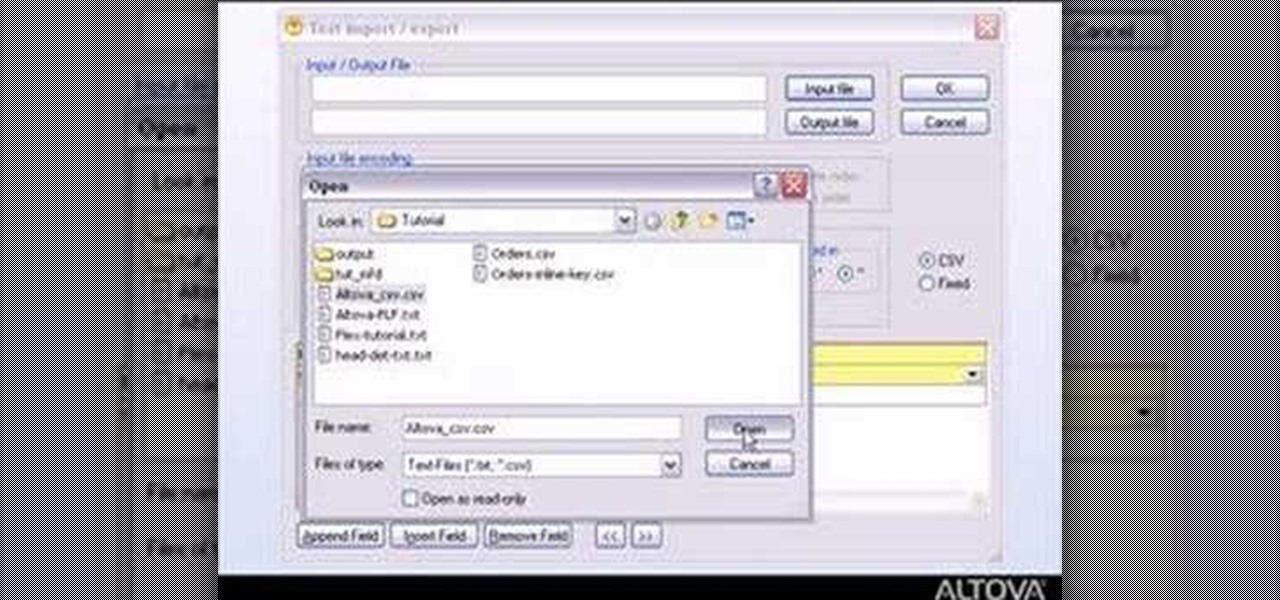
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

This three part how to video shows you a butt workout that will help you tone and tighten your glutes with three of the best butt sculpting exercises to target your butt, hips and thighs. Do these exercises and you will be able to get in great shape.

This tutorial demonstrates a weight training workout for your triceps. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your triceps and the rest of your arms.

This tutorial demonstrates a weight training workout that develops your deltoids. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your shoulders.

This tutorial demonstrates a weight training workout for the chest. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your pecs.

This tutorial demonstrates a weight training workout for your biceps. The how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your biceps.

Learn to play the board game "Plunder" with tips from this how-to video. To play Plunder, you need six players at the most. It is targeted mostly toward adults but even kids as young as eight like to plunder.

This is my updated video of eyeshadows brushes that I use when I do my eye makeup. I tried to be as detailed as possible.

The oblique muscles targeted by this bend-and-twist exercise will help you pick up everything from envious stares to spare change on the sidewalk.

In this tutorial, Bert will show you quickly how to use a bunch of different layers to create a ray gun shooting and exploding it's target. It will help if you already have some Photoshop knowledge for this one.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.