OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

Stock is a crucial ingredient for so many recipes: soups, gravies, and risottos depend on stock; quinoa and rice are both more flavorful when cooked with it, too. So, chances are that broth is a staple on your weekly shopping list.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a lost or broken phone, so it's definitely important to have this unique identifier handy.

Pop-Tarts are a pretty iconic breakfast food. And while I'm more of a bacon, eggs, and toast person myself... sometimes a sweet, gooey, artificially-flavored treat is just what you need in the morning. Yet, despite the fact that I do enjoy Pop-Tarts, I've always found them a little bit bland. Therefore I decided to make them better—by cooking with them.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

As we go about our daily grind, our smartphones and tablets take a silent beating. Dirt, dust, oil, and grime that our hands have picked up immediately gets transferred over to our shiny pocket-sized computers every time we check the time or look for new notifications, and over the course of months, this can have a very noticeable adverse effect.

Any other person can make plain pancakes... but only the most awesome of cooks can make stuffed pancakes. Luckily, this isn't a tough technique—in fact, it's so easy that you'll find yourself getting bored of the run-of-the-mill pancakes and dreaming of all the things you can stuff pancakes with, instead.

Bubble, bubble, toil, and trouble... it's time for another Halloween-themed food hack. This time, we'll be tackling the pumpkin cooler—an idea that has been done to death on DIY blogs around the internet. And there's no point in reposting something that everyone else has done, so I decided to change things up a little bit.

A classic French omelet is supposed to be completely cooked through with no brown edges. This is a delicate balance to strike, though. I always find that the moment I flip an omelet, it completely falls apart—unless it's so well-done it's rubbery, of course.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Few things are as frustrating as grabbing food from the fridge just to discover that your leftovers have gone bad. When it comes to cheese, you may have taken every last precaution to keep it as fresh as possible—sealed plastic containers, saran wrap, parchment paper—but to no avail.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

If there's a better way to impress your friends than with cocktails, I don't know what it is. Some nice glasses, quality spirits, and a recipe that doesn't involve pre-made margarita mix, and you'll automatically look suave. However, the most overlooked cocktail accoutrement (and the coolest, in both senses) is the ice.

If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

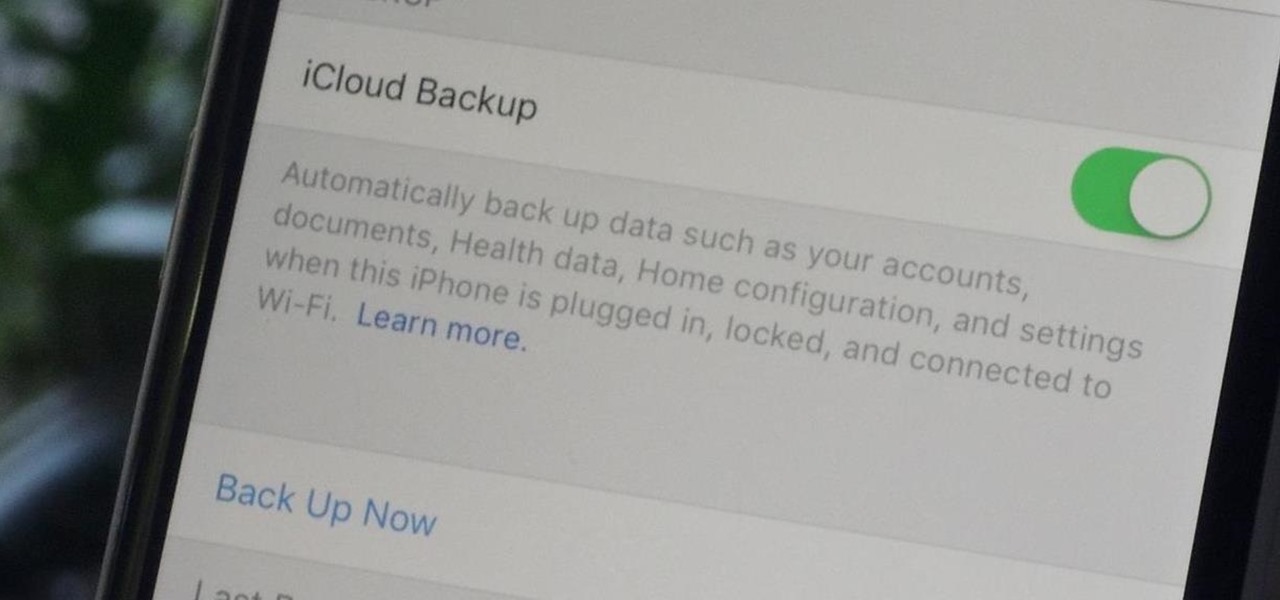
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

The grill isn't just a place for burgers, dogs, and corn anymore. Fresh fruit has made its way into barbecue territory, with results so good, you'll think twice about settling for fruit salad. While some fruits are common enough on the grill (like pineapple), these six are more off the beaten trail: peaches, watermelon, strawberries, mango, and pears.

Upgrading from velcro-only shoes to laced-up sneakers is an important step in life. Days are spent practicing the perfect bow-tying method, and people even argue as adults over tying with the bunny ear method versus the loop-and-wrap trick.

Welcome back, my rookie hackers!

A good chef's knife is a thing of beauty and, with proper care, a joy forever. It can totally change the way you cook and turn even the dullest prep work into a glee-filled task.

Other than salt, there's no ingredient that's as big a kitchen staple as olive oil. And just like salt, there are a million little known uses for it.

In my family, if a food could be made instead of bought, it was made. It wasn't until I went to college and started eating dorm food that I tasted the store-bought versions of many kitchen staples. I quickly learned that there is an enormous quality difference between homemade dressing and the kind that comes in a bottle at the supermarket.

Ice pops are like summer on a stick, with all the sweetness and stickiness of July and August. Store-bought popsicles, although refreshing, are never as good as homemade. So it's time to up your popsicle game with some of these beautiful creations, including some boozy pops (poptails) for adults.

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

I've always had an affinity for pretty wine bottles. When I was younger, my parents and my siblings would give me their empty wine bottles so I could collect them, and I loved every single one.

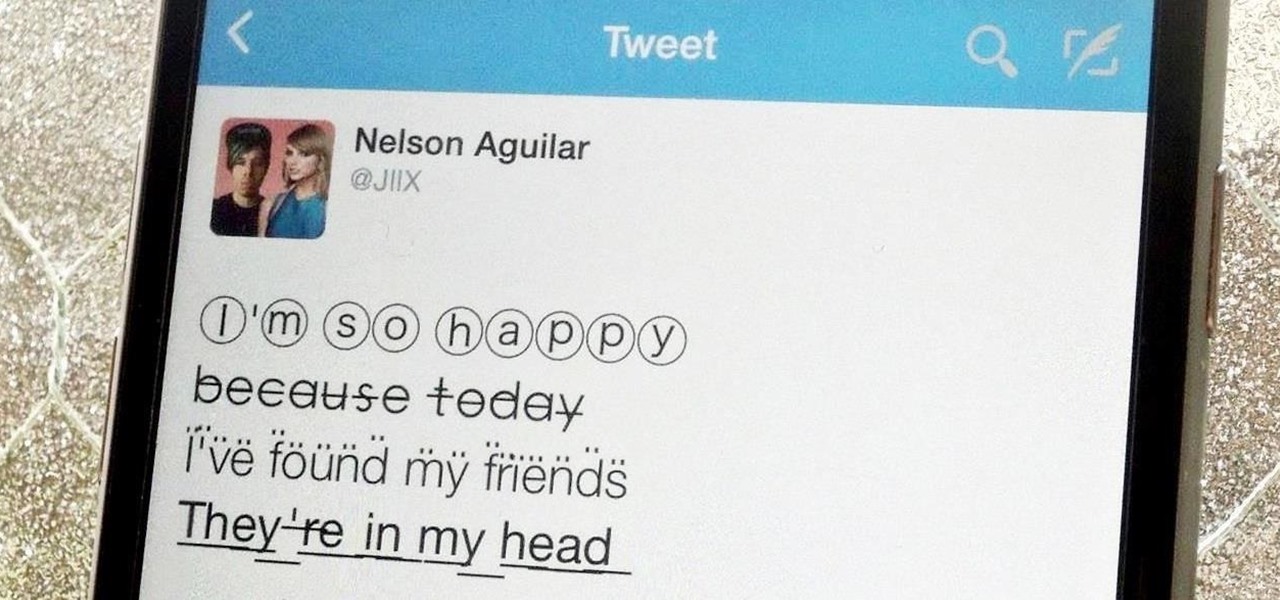
Aside from media, there's not a whole lot you can do in 140 characters to make your tweets stand out. You can use emojis, but they aren't exactly ground-breaking. However, now you can use Bedazzle, a Chrome extension from Gordon Zheng that'll allow you to add "rich text" to your tweets.

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

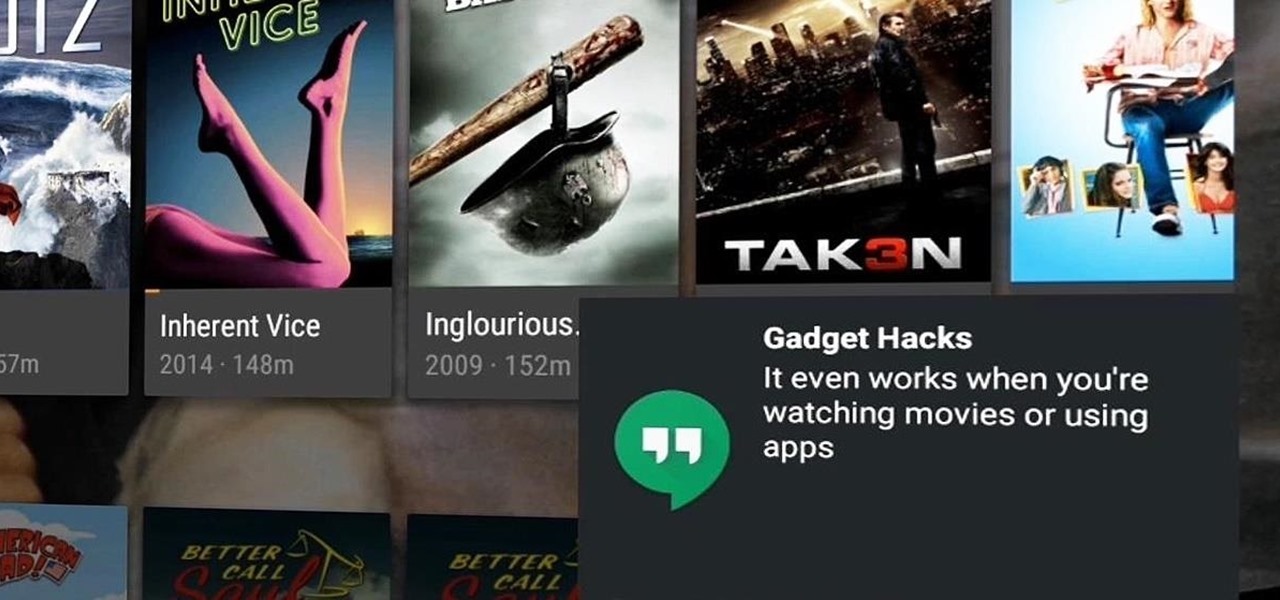
With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!