The war between horror movie monsters has been going on for the better part of the last century. We're talking vampires, werewolves, ghosts, zombies and mutant flying creatures, each of which has had their fair share of the limelight in film. But it comes and goes. Once moviegoers get an overdose of a particular monster, they aren't scared anymore, meaning it's time to move onto the next. So, Dracula goes away kicking and screaming, just to be replaced by Frankenstein and then werewolves. But...

I've always wanted to get a bunch of people together to hit up various drive thru restaurants in reverse. I know it's not the most creative our outlandish thing, but I am sure it would turn a lot of heads and muster up plenty of good laughter!

We can make a paper fortune teller for fun by using the following instructions. First start the process with a square piece of paper approximately 8 inches on each side. Now, fold each corner of the paper into the center and flip it over and then fold each new corner now created into the center. Then, mark each triangle (there will be 8 of them) with a number. On the reverse side of each triangle, write a fortune for every number. Next, fold the numbered side in half and stick both thumbs and...

A field hockey defense must control the opposing team's offense. Communication and positioning are paramount when building an effective field hockey defense. Learn how to play field hockey defense in this video tutorial.

This video tutorial teaches you how to drive a manual transmission automobile. So, if you were ever curious about driving a stick shift vehicle, go no further, learn it right here. First things first, press the clutch. Then learn the gears of the car or truck. Put the car in reverse and put the handbrake down. Let go of the clutch while gradually pressing the gas pedal. That's it. Well, this is actually the first steps to driving a manual transmission auto.

The basic idea of the figure 8 is to manipulate the glowsticks in a way that creates a trail of light resembling the number "8." One glowstick is drawing the outline of an "8" while the other glowstick follows in its path. One way of doing this is using your arms. This video demonstrates how to draw an 8 using mainly arm movements (as opposed to wrist movements.)

Yoga posturing sequences are a succession of postures intended to flow together, one following the next. This is most commonly referred to as vinyasa or a personal yoga flow. Use these relaxing poses to release tension and stress from the entire body. Remember, the key to yoga is gentle, deep breathing and a clear mind.

For an object to balance, you have to have the center of gravity directly above the base. Well, reverse that to see that you can also balance an object by having the center of gravity directly below its base.

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners: The One Leg Circle. Pilates exercises focus on breathing, alignments of the spine & build strong torso muscles.

If you're just starting out learning to drive, get the lowdown on some of the basic car controls with this video tutorial.

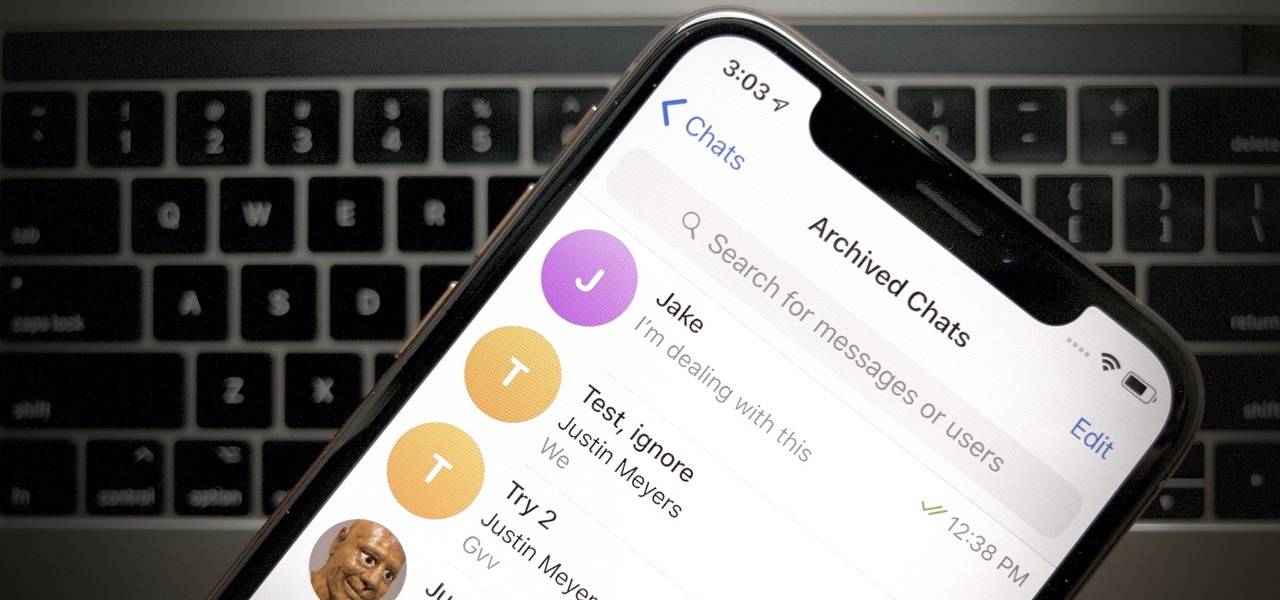
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

This how-to video is for anybody looking to gain lean muscle right in the convenience of your own home with little to no equipment. The intensity and variety of these exercises makes for an effective muscle-building workout. Standard Pushup

In northern style kung fu, practice the rising block, reverse punch, shin kick, side kick and side punch combination to add power to a martial arts arsenal. Perform this unique attack combo with tips from a professional kung fu instructor in this free martial arts video. Perform a northern style Kung Fu combination - Part 1 of 20.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

You may not want to disable notifications for the Mail app entirely on your iPhone since you could miss essential emails when they come in. But you can at least silence conversation threads on an individual basis. Doing so won't mute all conversations from the same sender, only the thread you select. Plus, it works for group email threads where things can get chaotic.

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

If you use the mobile Slack app, whether for work, school, or play, you know that the background color in discussions for channels, threads, and direct messages is white and that most of the text is black. Unlike with the sidebar, there's no way to customize the colors that appear here, but you do have one other option: dark mode.

Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

The Galaxy S9's Super Slow-mo feature comes packed with tools that help you tweak your slow motion clips like a pro. Among these is the ability to convert your slow motion videos into GIFs with a user-friendly interface. As a result, it's incredibly easy to go from recording to GIF conversion and on to sharing in a few taps.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

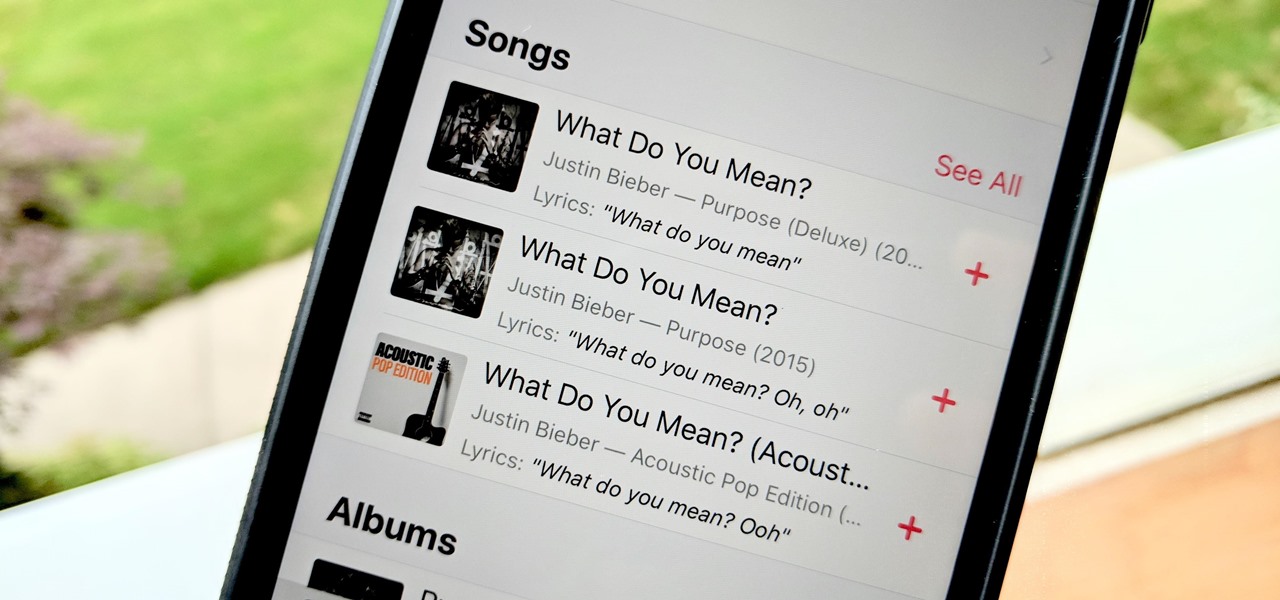
Has this ever happened to you: You're singing a song in your head and want to look it up on Apple Music but you just can't think of its name or even who recorded it? In iOS 12, if you can sing it, you can search for it, as the update lets you find songs in Apple Music by lyrics alone. It's like Shazam, only instead of identifying music by sound, it uses the lyrics in your head.

Ever since 2009, you could send a photo or video that you've already taken right from the Messages app on your iPhone. You would just tap on the camera icon next to the new message box, then choose either to take a new one or select one from your library. If you're running iOS 12, that's no longer the case, but that doesn't mean the capability is gone entirely.