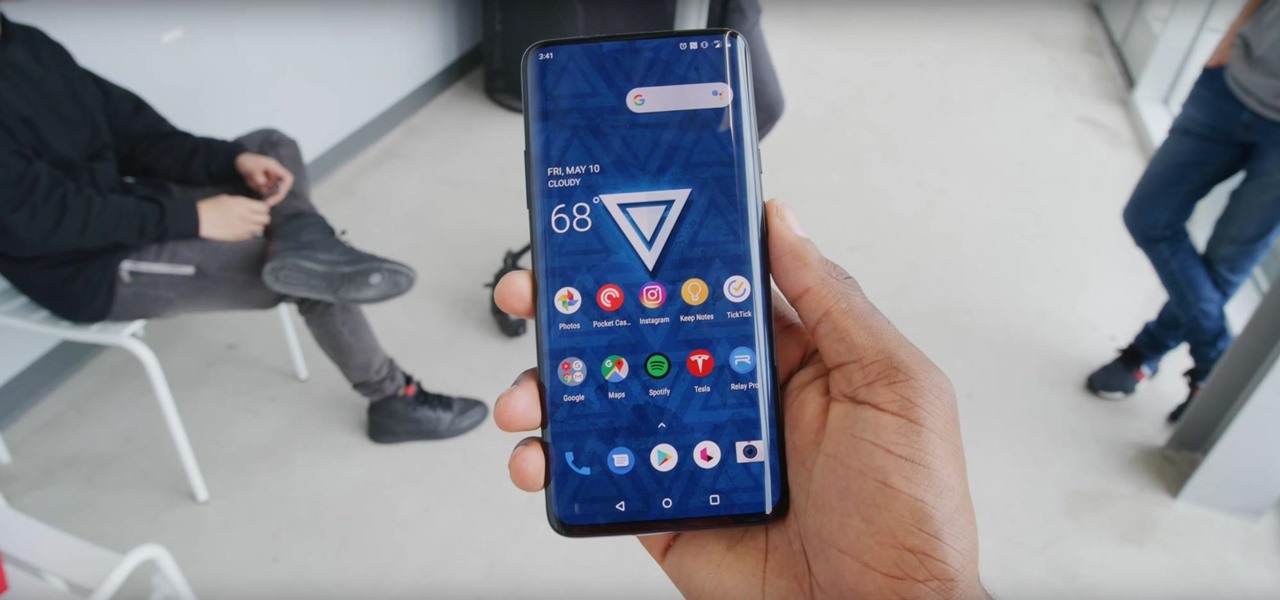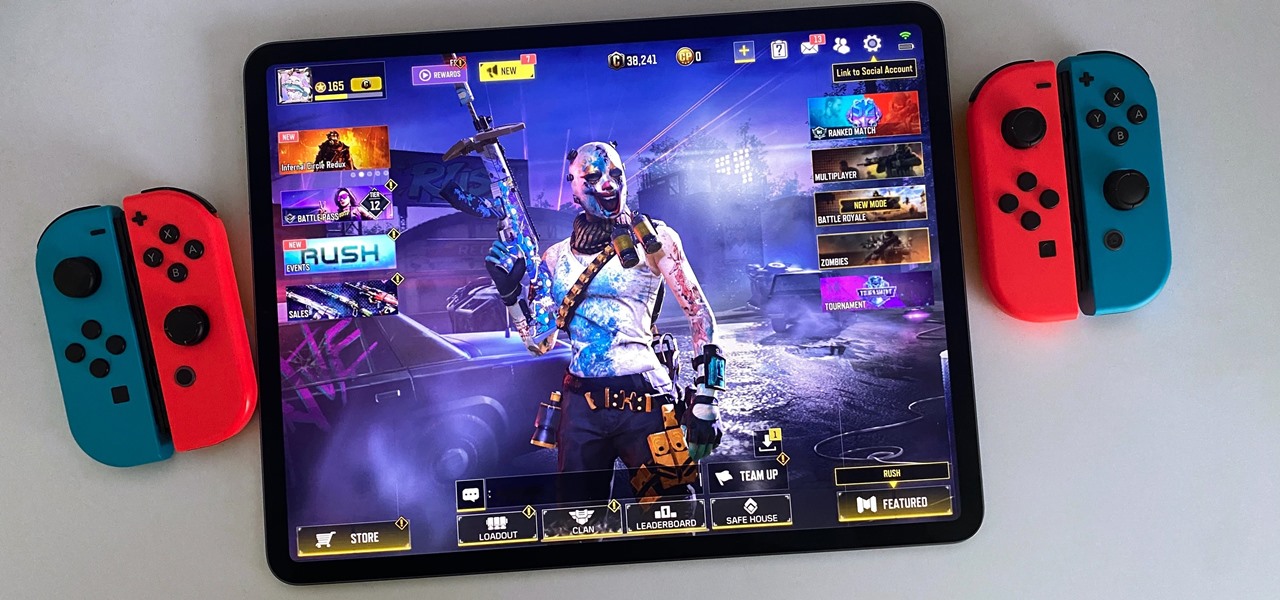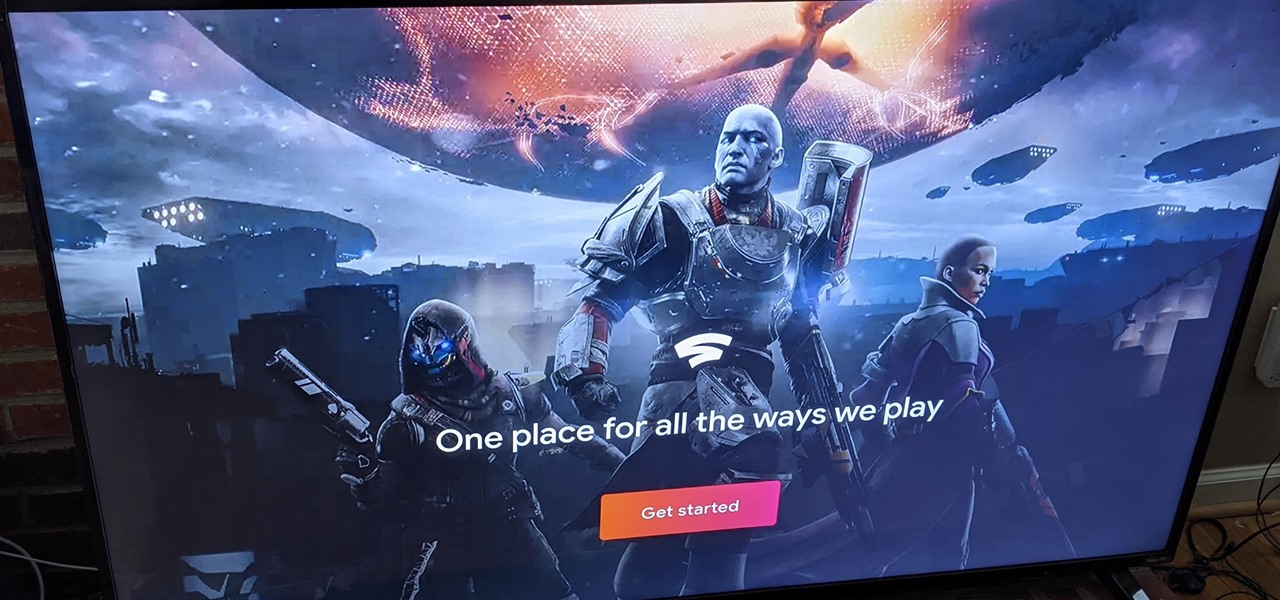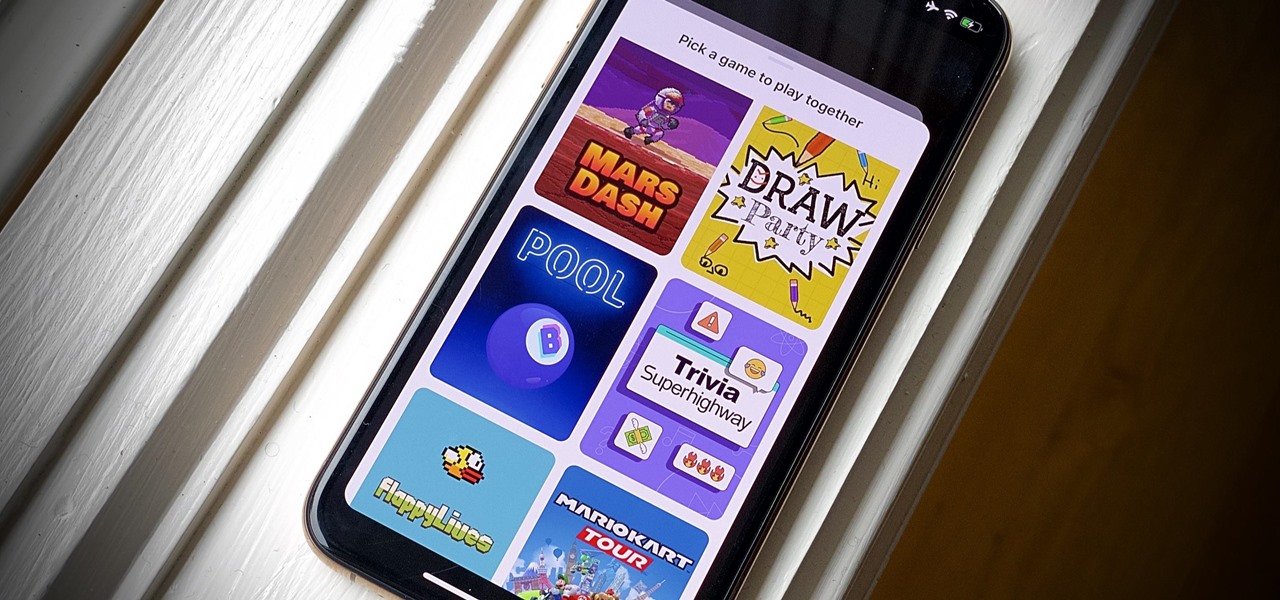
Even for those of us who enjoy spending time alone at home, at a certain point, it just gets boring. We all need social interaction, but with stay-at-home orders, that can be hard to come by. If you're feeling the itch to hang out with friends and have a good time, you should know there are plenty of free multiplayer games for iPhone and Android that will let you do just that — remotely.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.
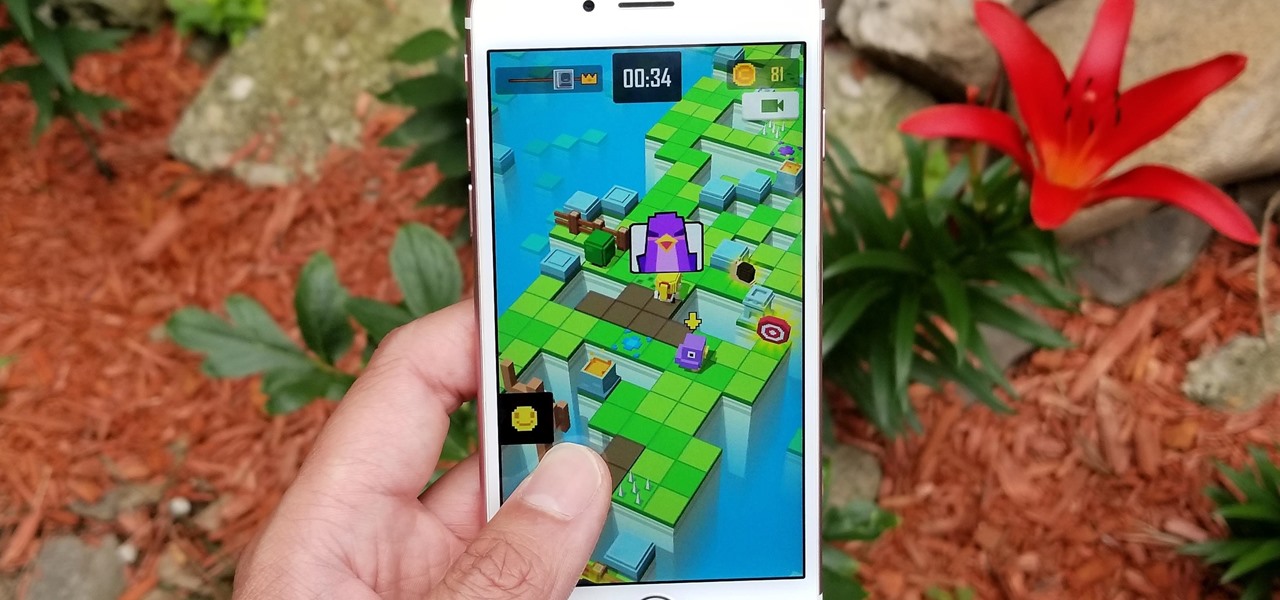
Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

If anybody knows how to pick a lock, it's Schuyler Towne.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Apple erroneously released iOS 14.1 for iPhone as a stable OTA update on Tuesday, Oct. 13, just after the special event where it announced the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max. It's not surprising given Apple's track record lately.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

We're still awaiting the arrival of consumer-grade AR smartglasses from the likes of Apple and Facebook. But that doesn't mean there aren't AR products out there to try this holiday season.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq.

You probably know of Apple's Text Replacement feature for iOS, iPadOS, and macOS, but you're probably not using it as much as you should. With it, you can create your own keyboard triggers for almost anything you can think of, whether it's an email address or an entire email. There are endless reasons to create custom text replacements — and we'll show you why.

Gaming just got easier, thanks to Apple. A secret feature on your iPhone or iPad makes it so much easier to beat that level or opponent you can't seem to defeat, and it can even help you learn to play a new game faster.

If you're doing the same tasks on your Android phone repeatedly each day — like playing a specific playlist at the gym, viewing work documents, or watching your favorite music video — you can save some time by automating your routine, turning each task into a one-tap gesture on your home screen.

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.

Apple gave its Photos app some serious muscle in a new update, and it's time to start flexing. Photos has so much power now that it may finally be time to ditch all your iPhone's other photo and video editing apps. You won't even need any third-party apps to remove backgrounds or lock private content from prying eyes because it's all included in the latest Photos upgrade.

The emergence of Facebook's collaboration with Ray-Ban to launch Stories smartglasses has finally put an exclamation point on a new category of smartglasses: the pre-augmented reality wearable segment.

When life hands you lemons, make lemonade. At Magic Leap, the lemons are the COVID-19 pandemic, and the lemonade is a new solution for virtual meetings born out of social distancing.

At launch, Chromecast with Google TV is fairly limited in the number of compatible apps. Many of the usual suspects are there, but there are some interesting omissions, like Google Stadia (though support is coming). However, at its core, the device runs on Android 10, which means you can sideload apps, including those that don't officially support Chromecast with Google TV.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Many lazy cooks skip rinsing off their grains before they cook 'em, but that's a big mistake for a few reasons. Some grains have coatings on them that need to be rinsed off to cook properly and taste good.