This clip discusses how authorization roles work and their role in the security of the latest release of the F5 Networks Management Pack suite. It also touches on the creation and use of user roles within Operations Manager console and how to apply the authorization tasks to those roles. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with F5 Networks Management Pack suite, you're sure to benefit fro...
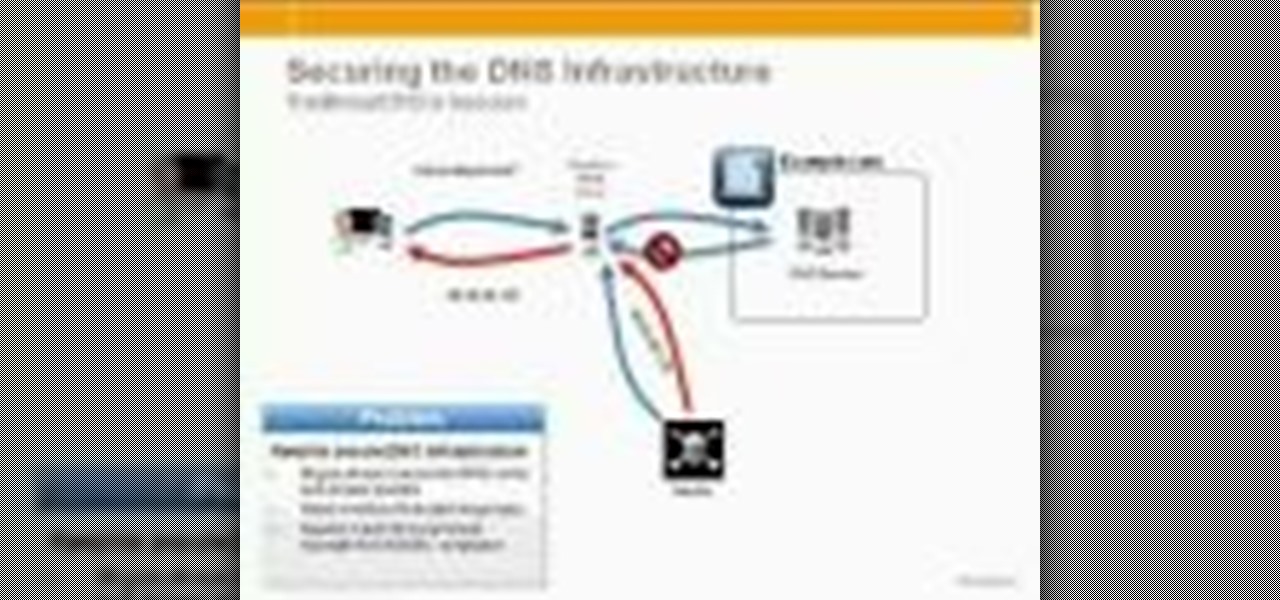
In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
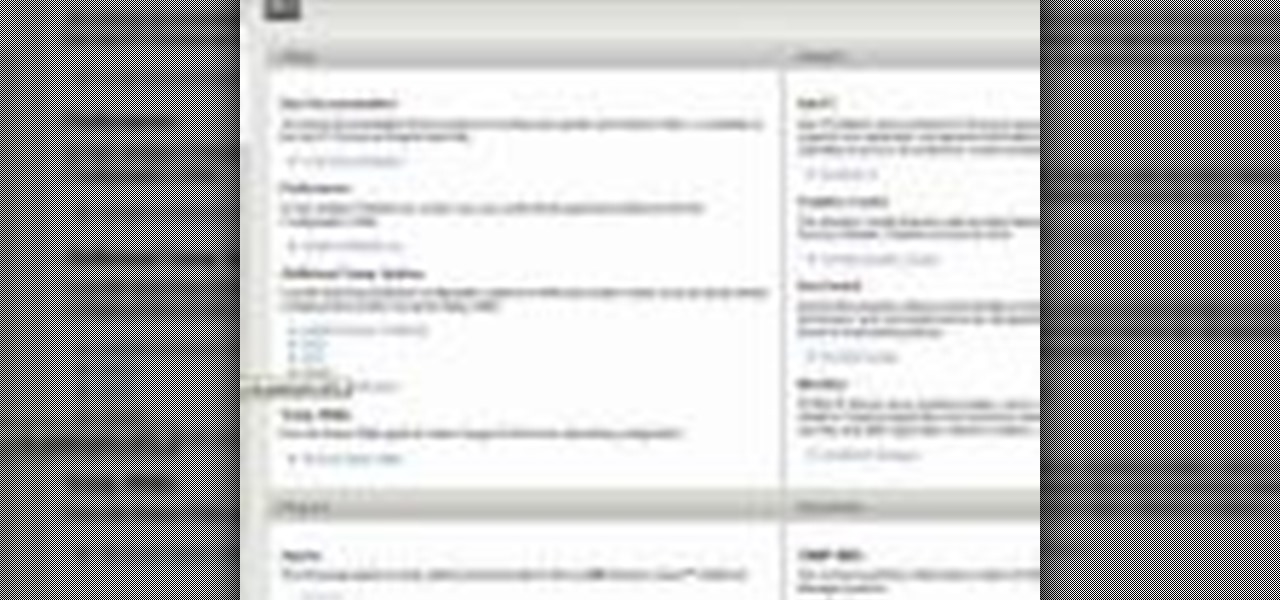
See how to use the PCI compliance reporting functionality within BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
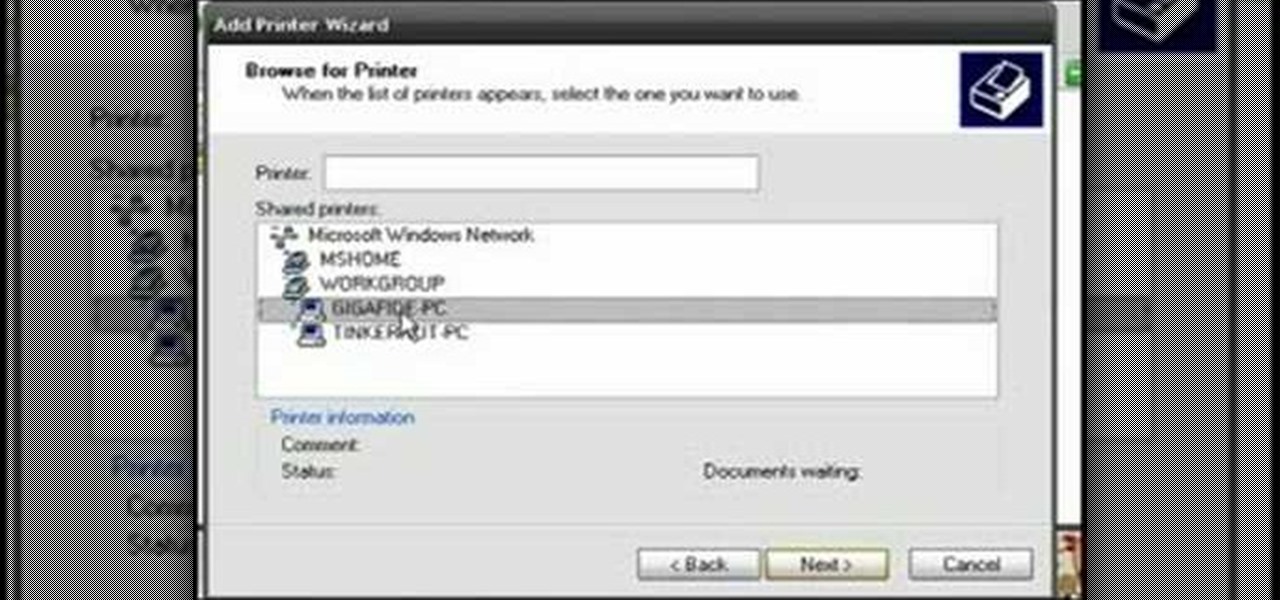
Odds are you have more computers on your network than printers. This video lays out the steps for sharing a printer over a network. This tutorial assumes that the printer is installed on another computer and not connected directly to the network. Take a look!

No wireless router? There is a way to network your computers by using your existing power-line. This CNET video will show you how to set up a power-line network - it's not as sexy as a wireless network, but it's easy and reliable!

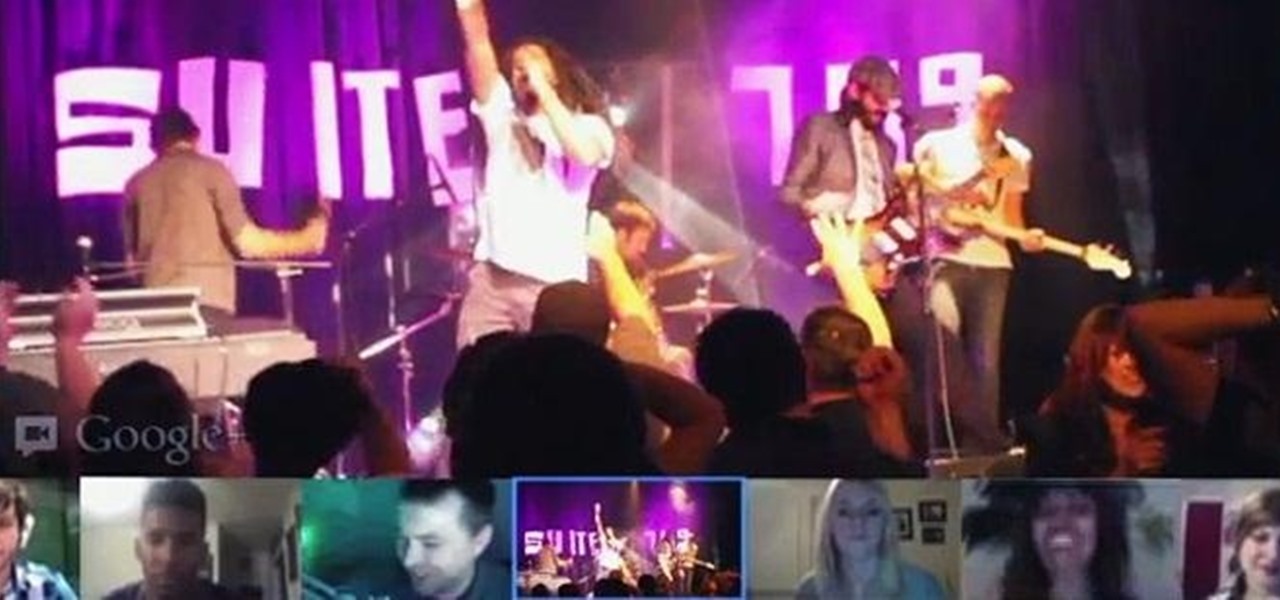
If you're a musician, Google wants you on Google+ Hangouts. In an effort to make it easier to stream your concerts, performances, and impromptu jam sessions, they've revealed their latest feature: Studio Mode. Enabling the new Studio Mode optimizes your Hangouts On Air for music, and the quality difference is massive.

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

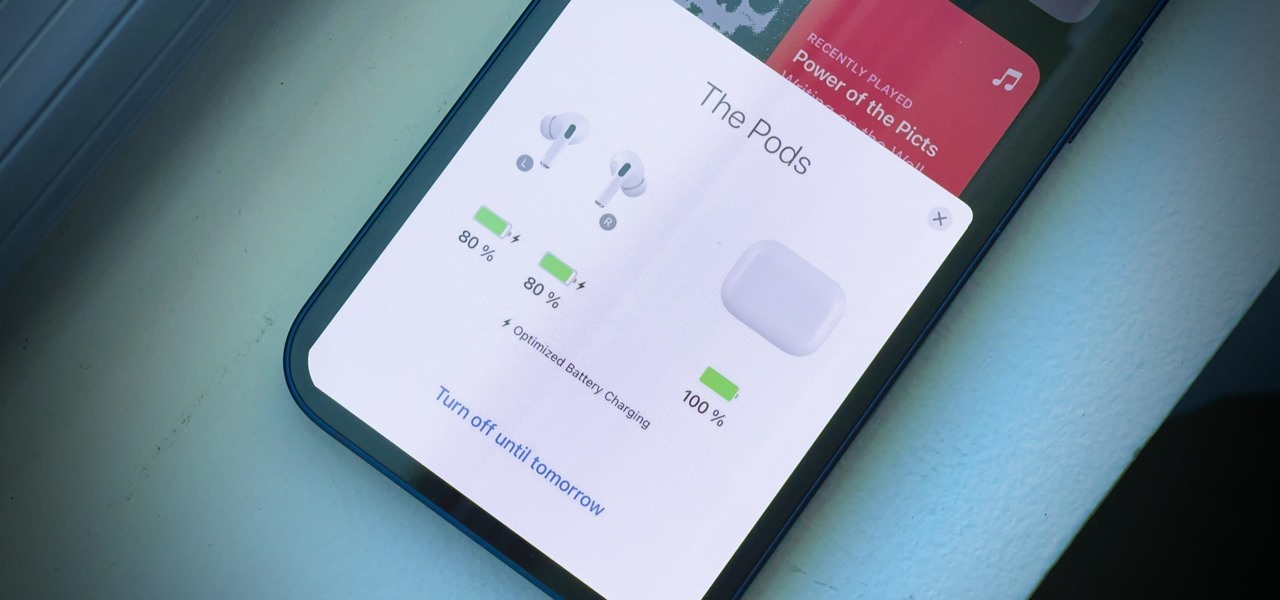
Your AirPods Pro can run up to 4.5 hours when 100% charged up. However, they're programmed to stop charging at 80%, and it won't kick back in until they think you'll need that extra 20%. That means they won't last as long in your ears before needing put back in the case. And you could end up with dead AirPods Pro if you're out, can't hit up a charger, and your case is out of juice.

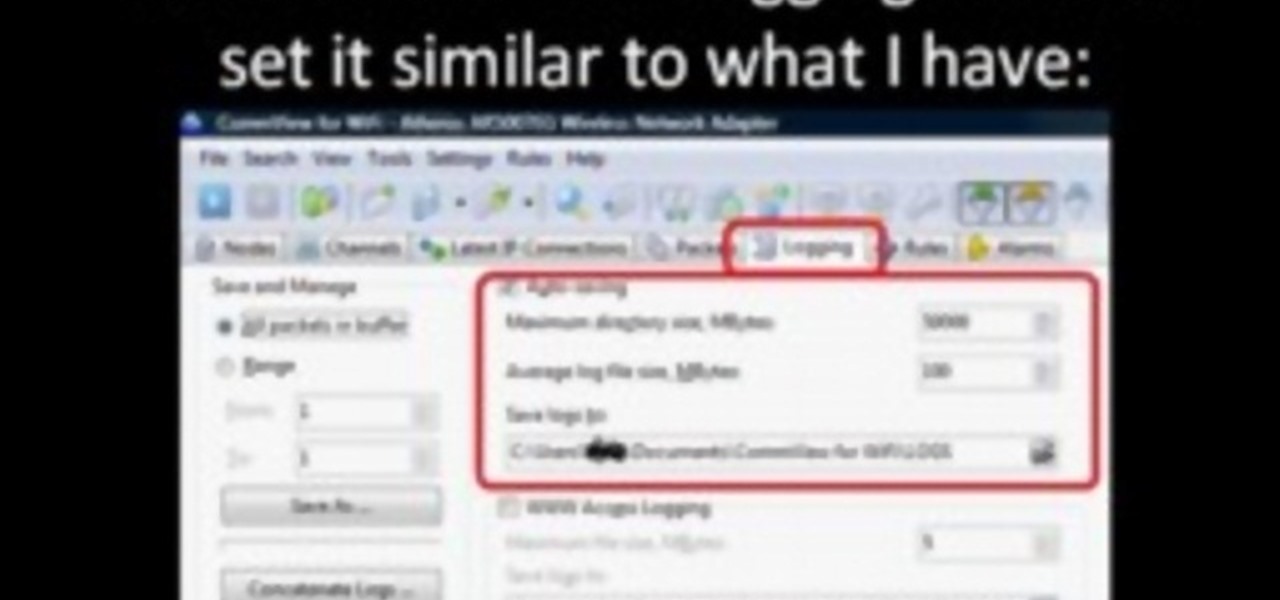
Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Thanks to their partnership with Tidal, over 30 million Sprint customers can access Hi-Fi audio on the go. And the Jay-Z-owned music service isn't limited to just Sprint customers — for $19.99/month, anyone can listen to lossless audio from their favorite artists. But streaming uncompressed audio files uses a lot more data than standard quality, so how do you use Tidal without hitting your data cap?

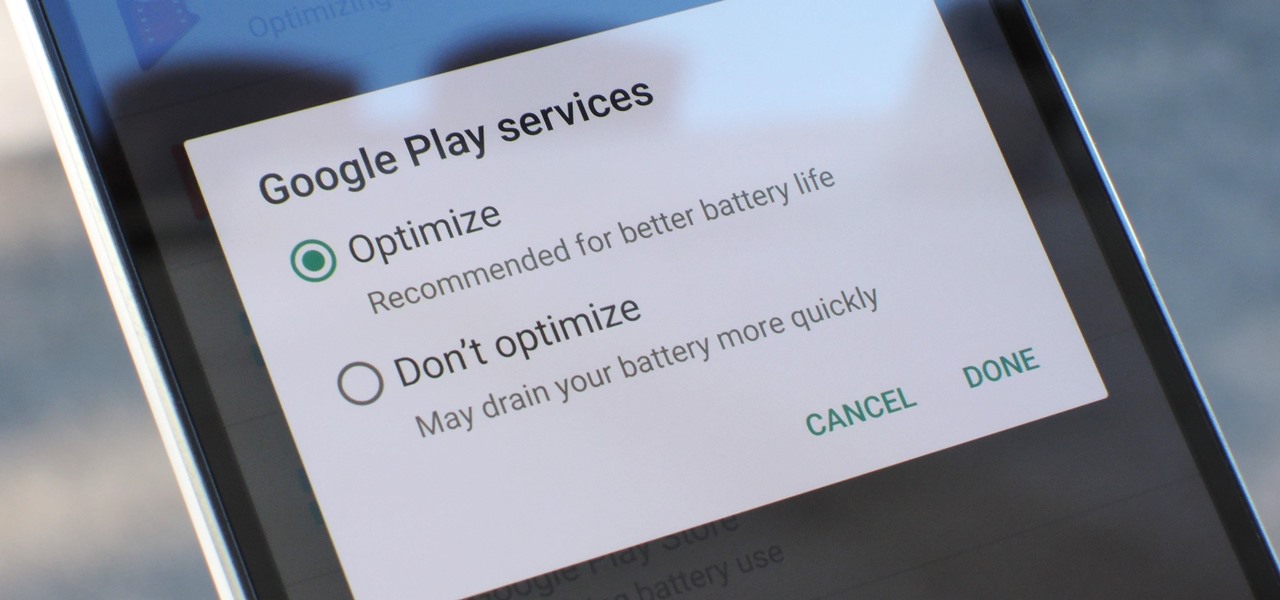
Google Play Services has been near the top of every Android user's list of battery-sucking apps for years now. It's a core system app, so you'd expect some battery drain, but for many folks, it runs rampant.

Video: . Optimize your Marketing with a Mobile Website

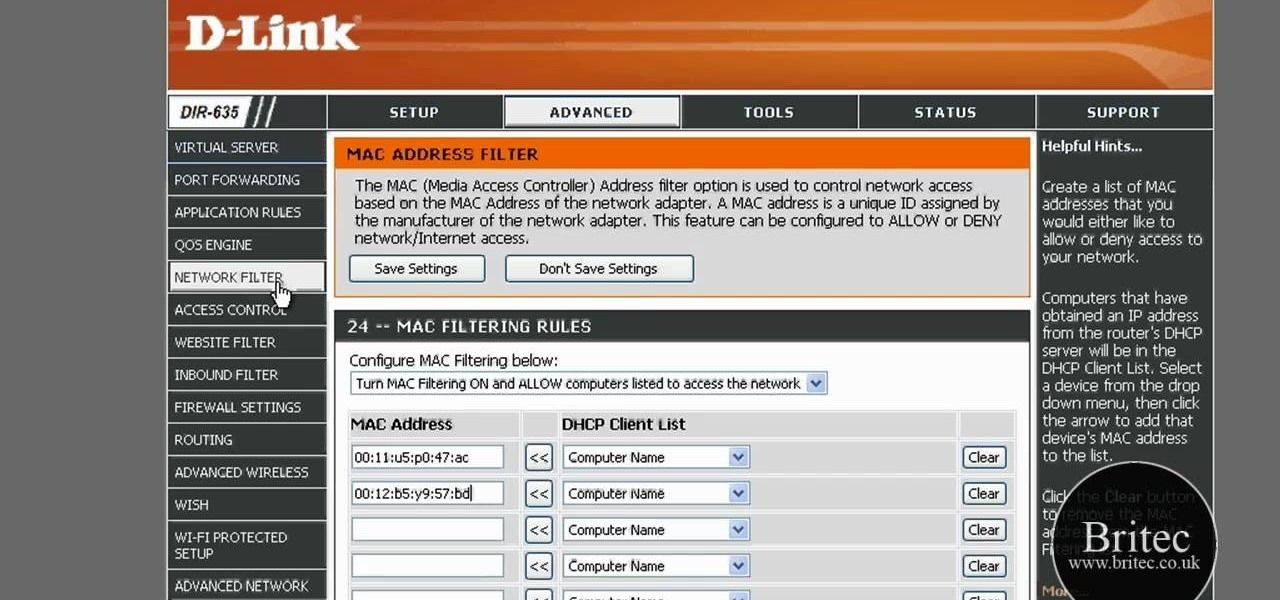
The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.

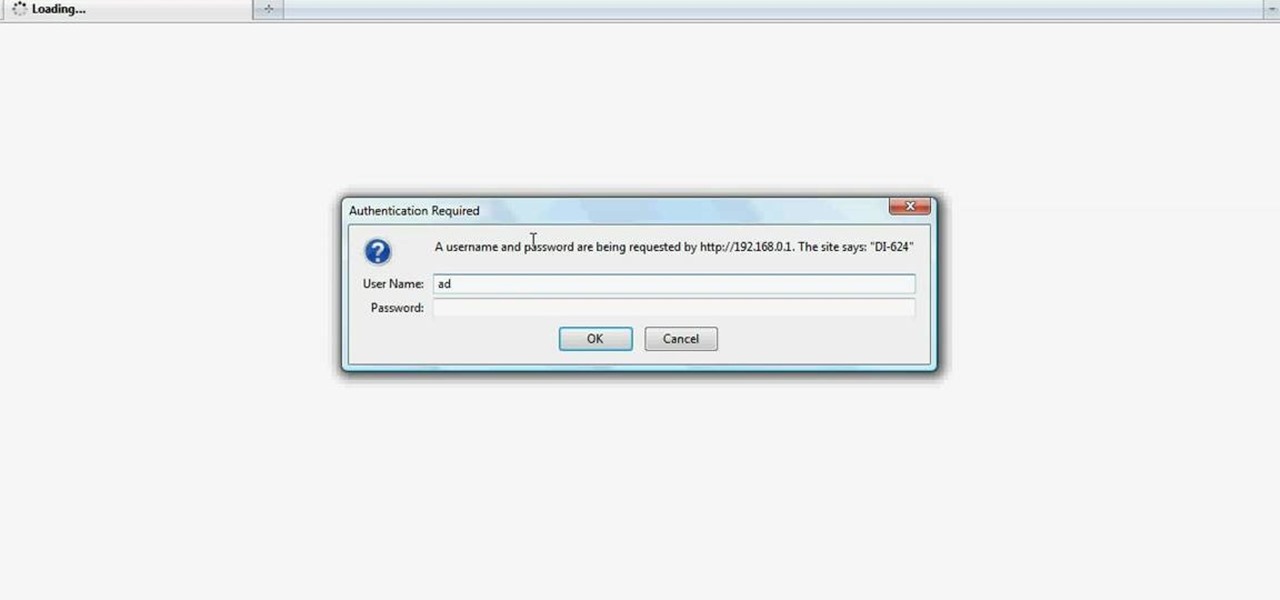
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

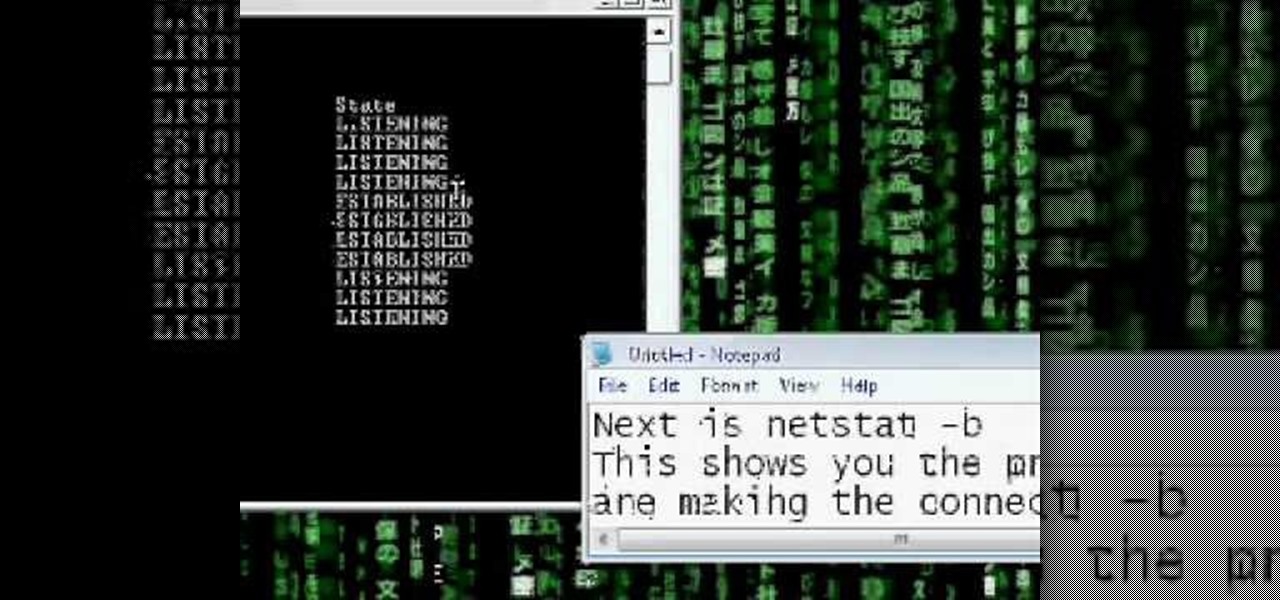
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

Samsung has made curved displays a signature element of their flagship phones, but the Edge Screen, as it's called, has proven to be a magnet for accidental touches. Fortunately, Samsung has developed a little known app to help prevent this problem.

Google announced several new devices (as well as updates to existing devices) that will take advantage of the company's augmented and virtual reality platforms.

The Note 7 debacle taught Samsung an important lesson on cramming oversized batteries into their handsets, and they've applied it diligently to their Galaxy S8 and S8+. You might even say the company has gone a little too far in trying to achieve a balance between battery size and battery life, as it not only not only sets screen resolutions to 1080p by default and warns users about maxing out display brightness, but it also keeps close tabs on individual apps' battery usage.

Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

Usain Bolt ran 100 meters in 9.58 seconds, an insane record-breaking time that might not ever get beat. As fast as that is, wouldn't it feel like a travesty if your Samsung Galaxy S3 took that long to open up Wikipedia?

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

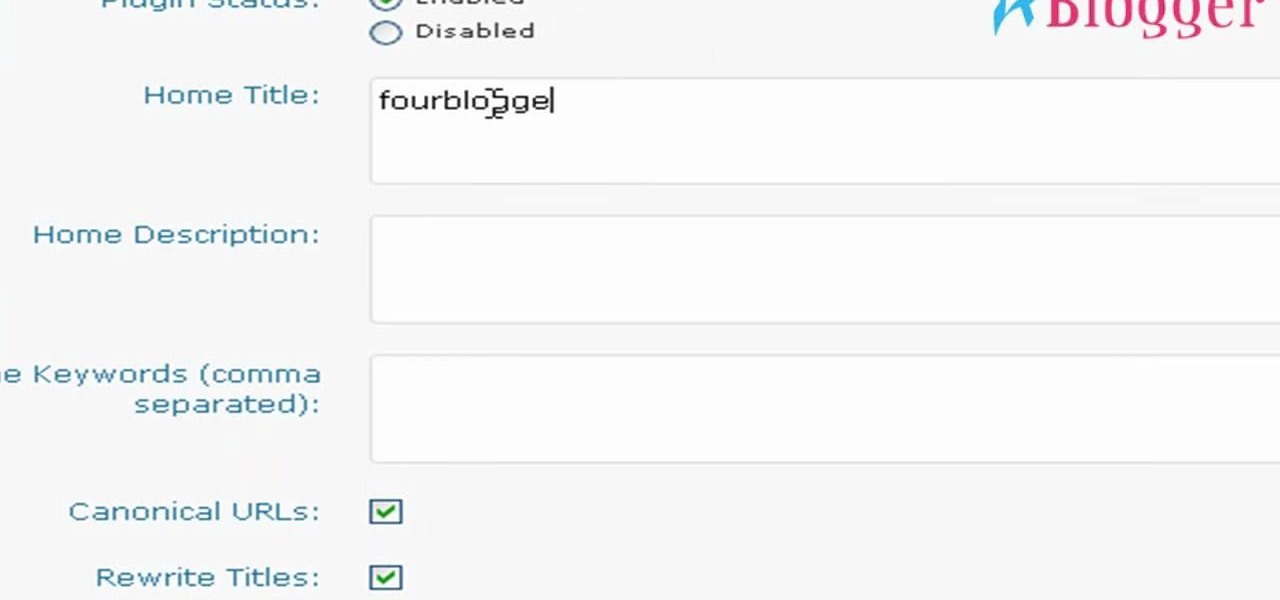
If you're looking for a good SEO theme for your WordPress blog, look no further. This video will talk about the WordPress cms users who are searching for these good search engine optimized themes. You may use any WordPress theme, but with the help of all in one SEO plugin, you can make any free theme as search engine optimized. This plugin tutorial explains how to fill the All-in-One SEo plugin settings page effectively to optimize your blog title, post title, page title, category title, home...

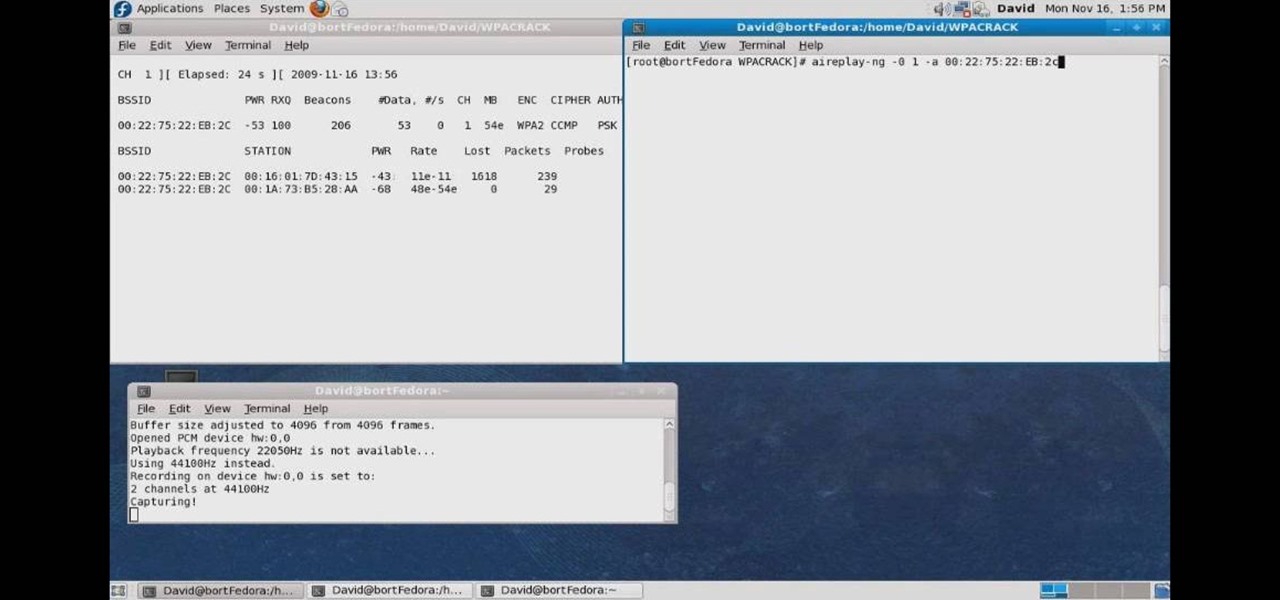
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

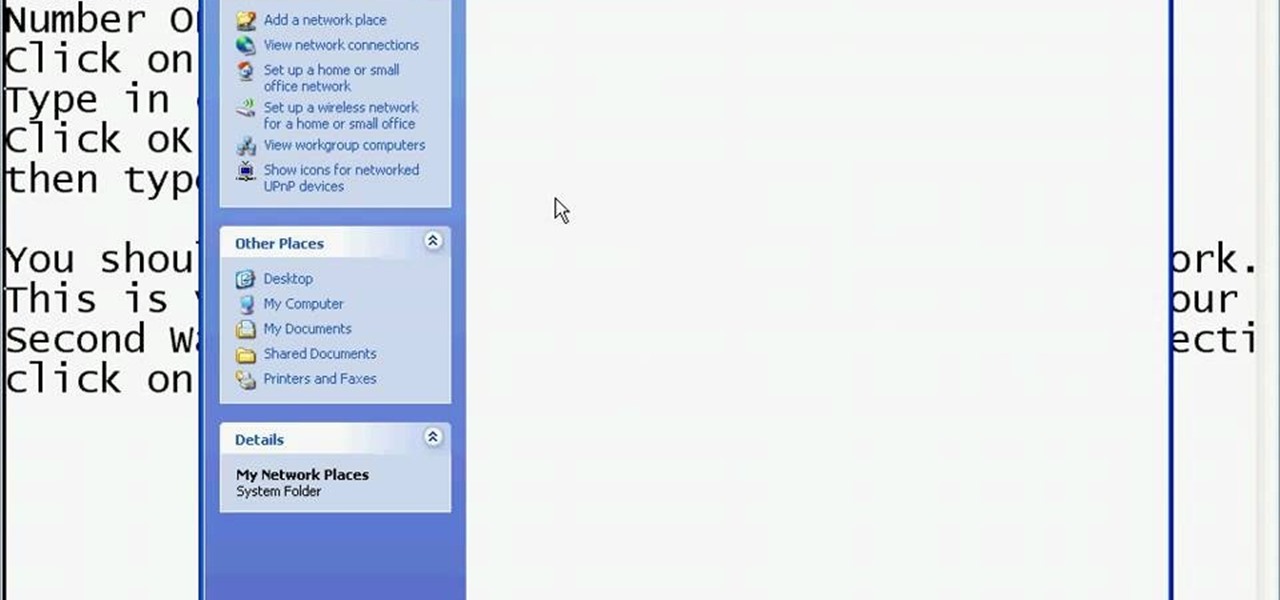
This video shows you the method to find if someone else is using your Internet connection. There are two methods for this. The first method involves opening the start menu and click on 'Run'. Type cmd in the text box which opens as a result of clicking on 'Run'. Type NET VIEW at the command prompt. This will show all people using your network. The second method involves going to Start menu. Go to Connect to and Show all connections. Click on My network places. Click on 'View workgroup compute...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.