To do basic crunches the lady is lying on her back with her knees bent and feet on floor about a foot apart. Fingers are spread under her neck and head. She raises her chest and shoulders looking up and back down to the floor slowly, 14 times. Now, the left feet crosses over the right knee which is still down on the floor and shoulder to the opposite knee with a small range of motion 14 times. She reverses doing the same thing with opposite leg and opposite shoulder. Now, arms are extended un...

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Crochet a cool house-tent for your little homeless friends. This instructional video will walk you through a super simple pet project. Whether you're out to craft dwellings for a dog, cat, pig, or free-range snake, this tutorial demonstrates how to build and combine all the necessary components, including the frames, walls, and personalized decorations. The results are quite cozy.

Learn how to do a standing barbell curl drop set while leaning against a wall. Presented by Real Jock Gay Fitness Health & Life.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Like humans, cats can suffer infections caused by ticks, and too often, the disease is fatal. Learn about tickborne diseases that affect cats and what you can do to protect Fluffy from an untimely demise.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Mens jeans come in a ridiculously broad range of styles and sizes, from form-fitting to huge and baggy. Different body types look better in different types of jeans, and this video will teach you how to determine what types of jeans are best for you body type.

Watch this how to video and discover why induction cooktops are the hottest trend in the kitchen. These Home & Garden tips will help you decide on an induction stove that is right for you kitchen.

The Paslode Framing Gun is operated by a gas cartridge and battery so an air compressor is not needed. The tool also has a large range of nails available for different job requirements from 50mm To 75mm. Watch this video tutorial for a demonstration on how to use a Paslode impulse framing nail gun.

Do it yourself: extend your WIFI signal. This is a quick and easy way to get more range for pennies.

In this lesson we will learn how to solve probability problems involving a spinner. A probability measures the likelihood of a certain event. It always ranges between 0 and 1. The following formula can be used to find the probability of a particular event:

Learn how to perform this lateral crossover skip drill in order to maintain a full range of motion.

Everyone loves Scrabble, but not everyone knows how to play the game properly. Yes, there is a set up rules that come with each game, but who actually wants to read them? Isn't it better to learn from a more visual approach? This video will teach you the basics of gameplay.

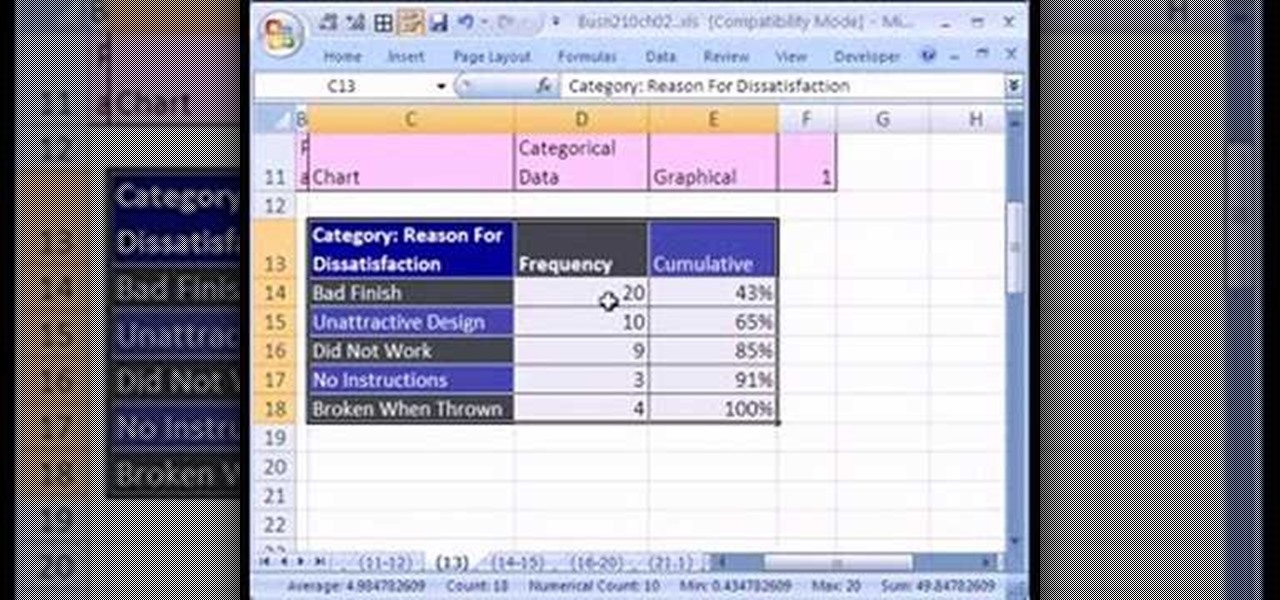
If you want to create a Pareto Chart for categorical data in MS Excel you should first have your data input into Excel already. From your data, you should highlight the cells that you want to count the frequency for and in the frequency box you should type in =COUNTIF and highlight the data you want the frequency for and put in F4 and then press , click on cell to the left and click enter. Now this will work all the way down. If you have not sorted it, you can right click and then click sort....

This photoshop tutorial demonstrated by Howard from tutcast.com, teaches you how to do amazing glow effects for your work and projects. Everything you need to know from the background you choose to use to editing out the leftovers. You can use any image that you choose to. Start out with the pen tool located on the toolbar on the most left of the screen. Create the initial layer for the glow by clicking now on the new layer icon located on the bottom right. Next, define brush by pressing the ...

You're a committed environmentalist but you love your candles. What are you to do? Did you know that you can recycle your candles? There's bound to be stuff left over. Just watch this video and learn!

Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his face to your knee. If the opponent is standing in front of you and there is not enough room to throw a fully extended kick, grab him and try a knee.

Is your waffle iron collecting dust? Plug it back in and use it like never before by whipping up a batch of brownies.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.