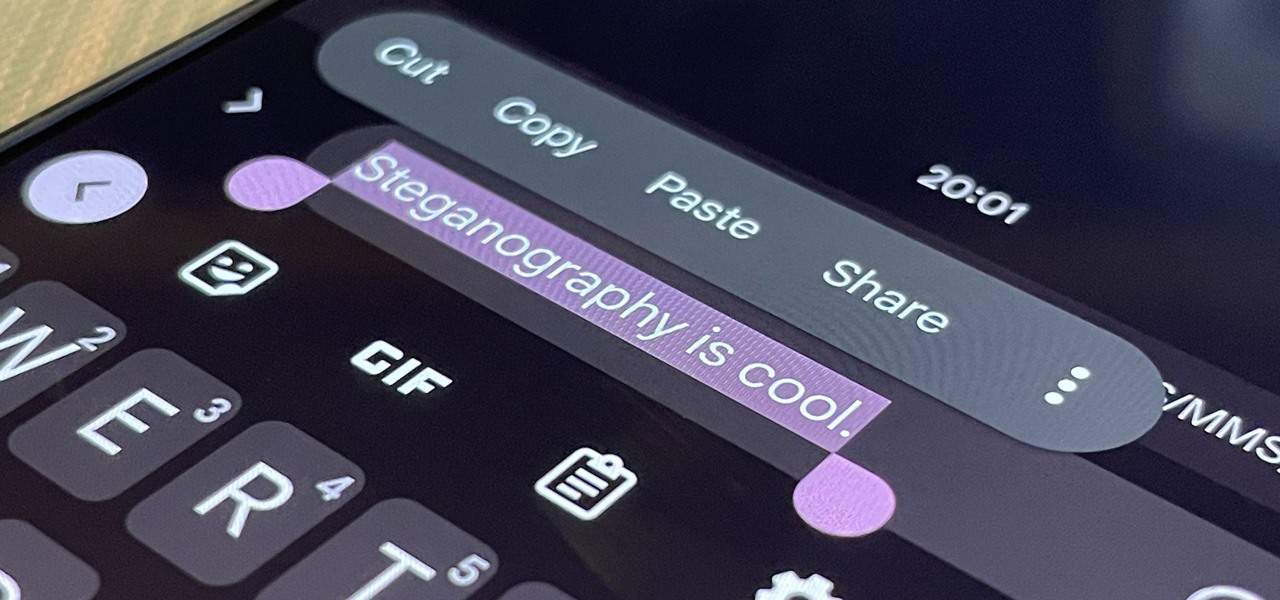
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

When temperatures drop and hit new lows during the cold, winter months, it's hard not to crank the heat up. That means increased energy bills each month, no matter if you rely on gas, electric, or another fuel for heating.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

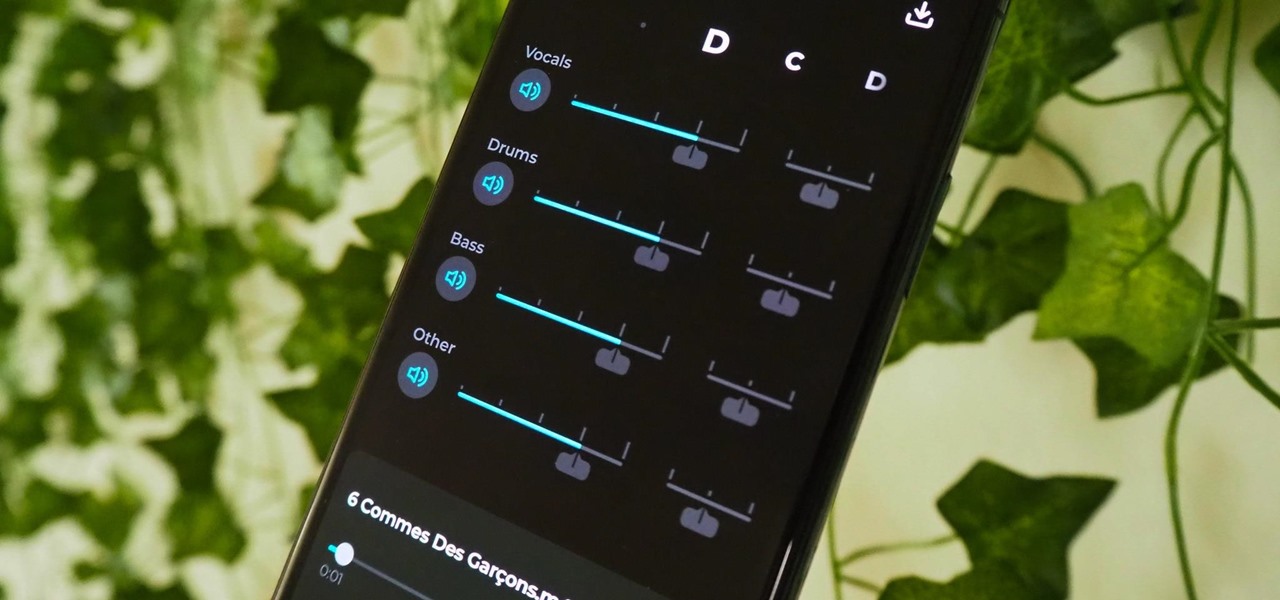
Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Your days as an ordinary Muggle are over — as long as you have an iPhone. With just a word or two, you can use your iPhone and newfound Muggle-born powers to cast spells or utilize charms just like Harry Potter and team. Only your "wand" is from Apple, not Ollivanders in Diagon Alley.

MIT Professor Arthur Mattuck gives a lecture on how to calculate with ordinary differential equations (ODEs). He also covers the geometrical view of y'=f(x,y), directional fields, and integral curves. Calculate ordinary differential equations.

Prank your friends by hacking some ordinary bubble gum to ooze fake blood when someone chews it. It can take 3-4 days for the "blood" to disappear. Use this as inspiration for one of your April Fools Day pranks! Make bloody prank bubblegum.

Street magic at its simplest. It is magic and there is a Santa. Spit, cigarette, and a thumb is all you need to learn how to make an ordinary cigarette vanish. Make a cigarette vanish.

Seriously, what can a lemon not do? Other than being your go-to fruit for making lemonade, this versatile citrus can do some household cleanup, deodorize bad smells, alleviate sunburns, and much, much more. Read on and you will never look at a lemon the same way again.

Rosie O'Donnell web show demonstrates an easy and quick way to make decoupage soap. Use dried flower or paper cutouts and glue to add a flare to ordinary soap. Make decoupage soap in Rosie O'Donnell's Crafty U show.

Hate the feeling of dirt beneath your fingernails after gardening? Rather than digging out the dirt afterwards, take a preventive measure by digging your fingernails into a bar of soap, which will keep them clean and wash out easily afterwards.

This is no ordinary tractor. Nor is it an ordinary Fiat. Not by a long shot. Japanese ironsmith Kogoro Kurata custom built this bulldozer from an old Fiat 500 body and caterpillar tracks, which can only reach a speed of 3 km/h. It may move at the pace of a snail, but I wouldn't mind using this beast to shovel my driveway (in style) this come winter.

The Curacao-blue color of this exciting cocktail gives it its high-energy name. If you are looking for something a little out of the ordinary, give it a try! Make an Electric Lemonade cocktail.

Do you want to turn an ordinary photo into a surrealistic image? You could simply do it by changing its color. In this video tutorial you will learn to use a Photoshop adjustment layer to modify the colors in a photograph. Use a Photoshop adjustment layer to modify colors.

Info Summary: Website: EducateTube.com | Host: Sipski

This is an in-depth tutorial page that teaches flute making theory and shows how to make several different (they have freakin' tables of information and dimensions) flutes from ordinary PVC pipe.

Looking for an out-of-the-ordinary destination for your next vacation? Check out these 20 top trips, hand-picked by National Geographic Traveler editors as the best of 2011. Where do you want to go this year?

It's amazing what you can do with an ordinary material like cardboard... or a truckload of discarded pizza boxes.

Learn how to make maple ice cream with this cooking video. This maple ice cream recipe is brought to you by Tammy Donroe on How2Heroes. Search How2Heroes on WonderHowTo for more cooking videos.