Lemon peels have long been known for their ability to be home remedies for cleaning and medicinal needs. In the kitchen, they are equally as useful and can transform many common dishes and drinks into more memorable ones with just a hint of citrus. To give you some ideas, below are five ways that lemon peels can spruce up your recipes.

Whether you call them chickpeas, garbanzo beans, or Egyptian peas, these little morsels are one of my favorite snacks—when properly seasoned, that is. Being mild in flavor on their own, they're incredibly versatile and fun to experiment with. (They're also incredibly healthy.)

The buttery scent of crescent rolls bring me back to my childhood, but those tubes that open with such a satisfying pop are more than just retro reminders. Crescent rolls can morph and serve as the base for hundreds of creative and cool dishes.

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

Things smell, and whether or not those things smell good or not is up to you. For lingering food odors on your hands, try using stainless steel or coffee grounds to remove the stench. To de-stink smelly jars, use mustard and water. For cutting boards, use lemons and salt, and use cinnamon and sugar for your funky kitchen. In your fridge, combine baking soda and a sponge, or even just orange peels and salt.

Let's be honest, most of us buy the bottom-shelf vodka either because we're broke or because we're going to disguise the gag-inducing taste of it with juice or something fizzy. If you're cooking or baking with vodka (ice-cold vodka works wonders in pie crust), what's the point of buying Belvedere?

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

The movie theater business is hurting due to the pandemic, but that hurdle is actually the perfect set of circumstances for movie studios to lean hard into augmented reality marketing.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Get Out absolutely tore up the record books this year. And the wildest thing about it? It did so with the most ordinary looking characters and props ever (hence the shoestring $4.5 million budget). Which makes it a godsend for the time- and cash-strapped come Halloween. With Get Out, Jordan Peele is the first (and only) African-American writer-director with a $100-million film debut under his belt. The film is also the _all-time highest domestic grossing debut based on an original screenplay ...

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

With the weather warming up and the days getting longer, fruit salads are starting to appear at backyard BBQs, beach picnics, and pretty much everywhere else. Often these sweet side dishes are unremarkable, with each colorful bowl blending into the next. Luckily, there are easy ways to spice up your fruit salads so that everyone will still be talking about them next summer.

Hands down, chips and dip are the best entertainment foods to ever exist. This fact can be confirmed in an instant by any grocery shopper strolling down the chip isle on Super Bowl Sunday or New Year's Eve. However, you may want to hold off on buying those standard salsas or dips at the store—especially if you own a food processor.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

I always found that those safety lights for bicyclists on the market were never good enough when riding in the dark. That got me thinking about people who use wheelchairs and how unsafe the night could be when they want to go out. So here's what I came up with:

What if I told you that you could read minds? You'd most likely think I was crazy, and you'd be right. But what I really meant is that you could make people think that you could read minds, something that's not the least bit crazy.

Augmented reality technology is often likened to magic powers, so it is fitting that a new AR experience featuring the Harry Potter franchise uses the newest AR tricks from Facebook and its Spark AR platform.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

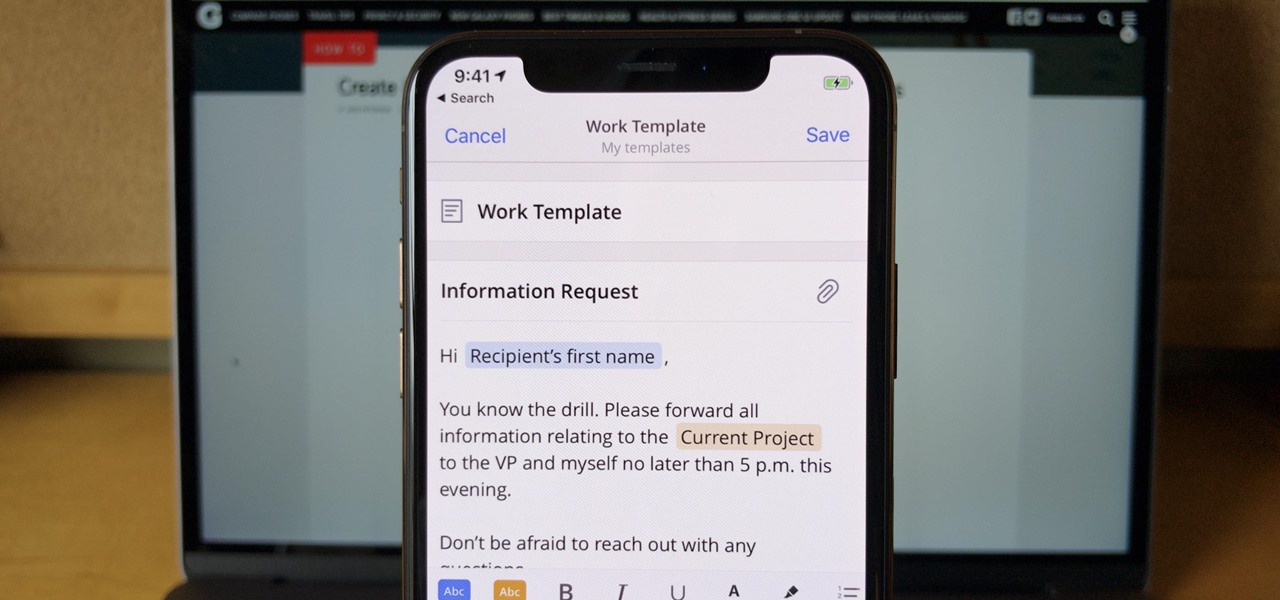
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

There's nothing in this life that we love more than making one ingredient or one food tool do multiple things. It saves money! It saves time! It makes us look smart at cocktail parties!

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

The cinematic photos feature in Google Photos can create impressive three-dimensional views of normally flat images, turning ordinary pictures into life-like representations of the moment captured. Google Photos would automatically pick images from your library to apply the effect to. Now, you can choose images on demand from your library — it's just not super obvious that you can.