
How To: Use a Marantz digital audio recorder
Check out this video tutorial to show you how to use a Marantz digital audio recorder. This video was made by the equipment room at CUNY Journalism School in New York.


Check out this video tutorial to show you how to use a Marantz digital audio recorder. This video was made by the equipment room at CUNY Journalism School in New York.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. Generally, the DataPager control is used with the ListView control. The ListView control is data driven. First create a ListView control and provide it some data. Next drop ...
In this video tutorial, Chris Pels will show how information can be passed from one page to another using a query string. First, see how to construct a query string including variable names and values from information on a data entry form. Next, see how to access the query string information when the page is posted including how multiple query string variables are handled. As part of the server side processing of query string information, see how to implement validation for existence of query...

Watch this how to video and learn how to make organic peppermint tea. This video will help you pick the perfect plants to prepare this delicious and soothing drink.

Check out this video to see how to draw a head by building it out of random organic shapes.

This video shows us how to use the following functions in Excel: average, count, counta, min, max, and sum. First, start off by create a set of numbers to work with. After that, click on an empty cell that you want to use for the functions. To do an average, click on the functions button on the top right corner of the menu bar, you'll see a list of all the functions that are available. Select average, and then highlight all the numbers that you want to find the average of. Repeat the exact sa...
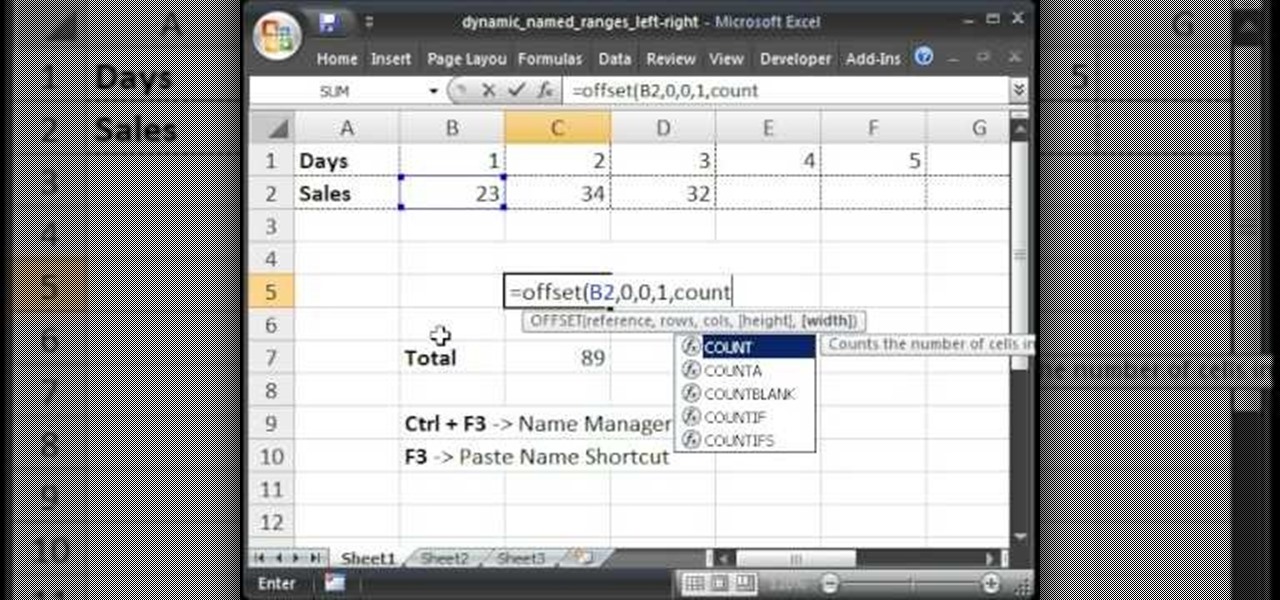
Teach Excel describes how to create a dynamically updating named range that goes from left to right using Excel. First, you define the named range by highlighting the cells containing numbers in a certain row. In the name box to the left of the formula bar, type the name of the data. In this example, the numbers correspond to sales, so type "sales." To check if the named range works, click on an empty cell and enter =sum(sales). That should return the sum of the highlighted cells. However, as...

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.
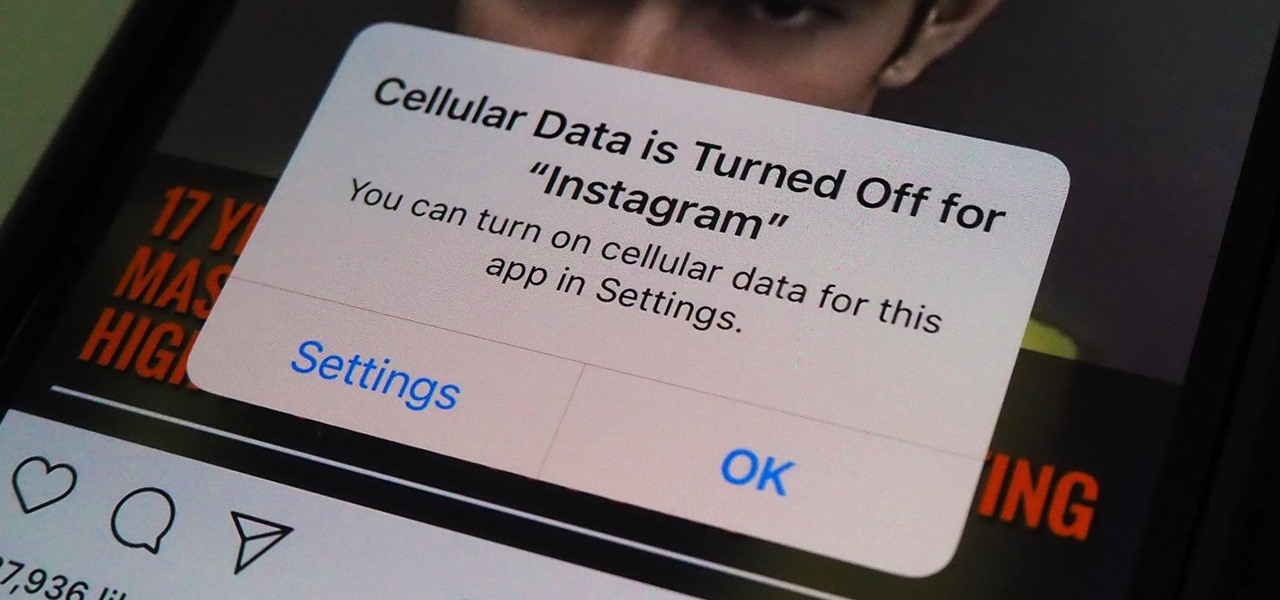
If you're on a cellular plan with a low data allotment, being thrifty with your data can help you avoid a higher bill. But even if you have an affordable unlimited plan from wireless carriers such as T-Mobile or Verizon, going over a certain amount of data may throttle your connection, leaving you with slow web speeds. One way to prevent hitting these thresholds is to keep certain apps in check.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

Data analytics is one of the hottest fields around. With so much data at our fingertips, top companies are seeking experts to put all of this information to real-world use.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.
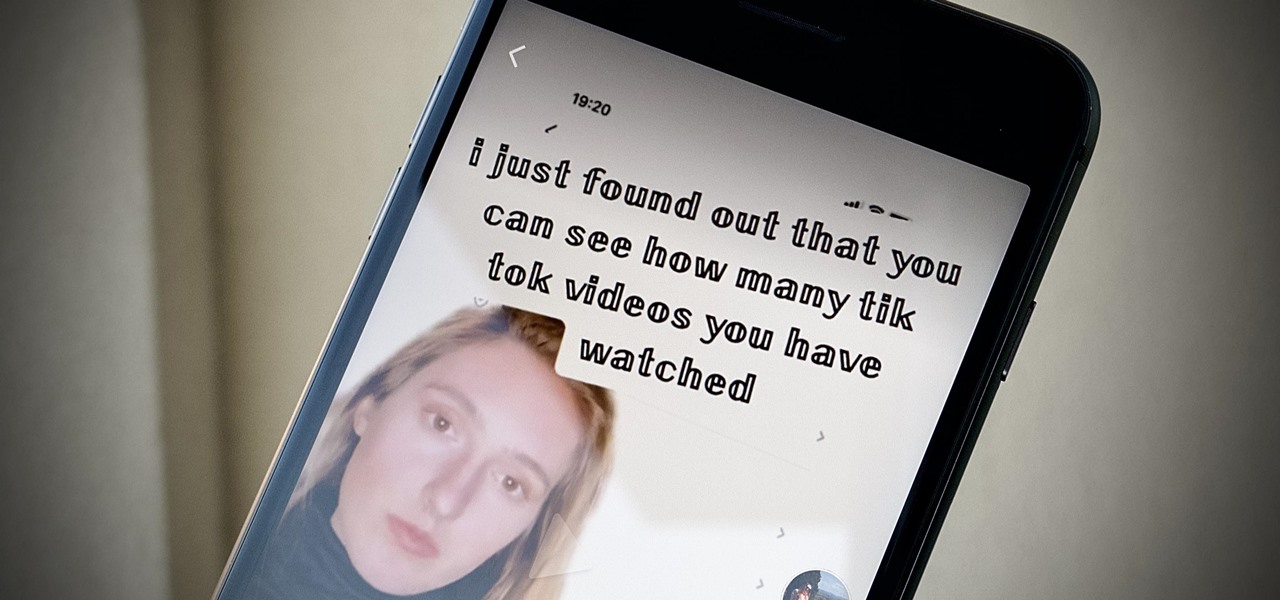
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Your Google history is mostly a binary choice — either you enable it fully, taking advantage of all its features while letting Google record your activity, or you disable it, staying incognito but also missing out on some fun stuff. But now, Google will let you auto-delete your history, allowing you to utilize all the perks that come with recording your history while maintaining some level of privacy.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.
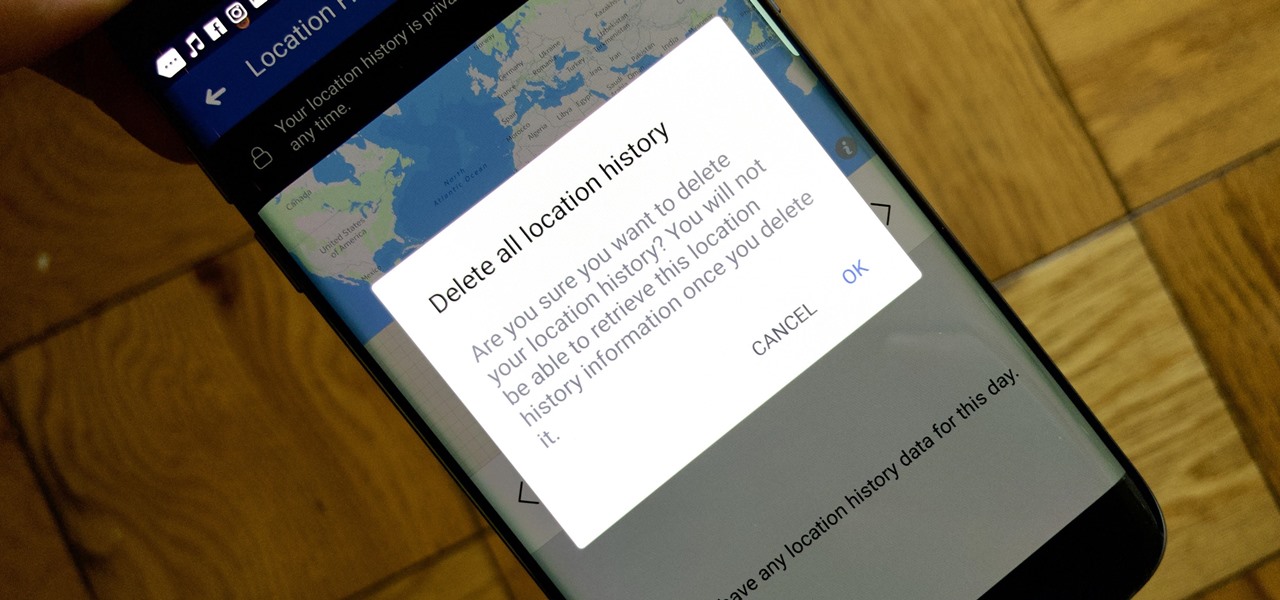
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.
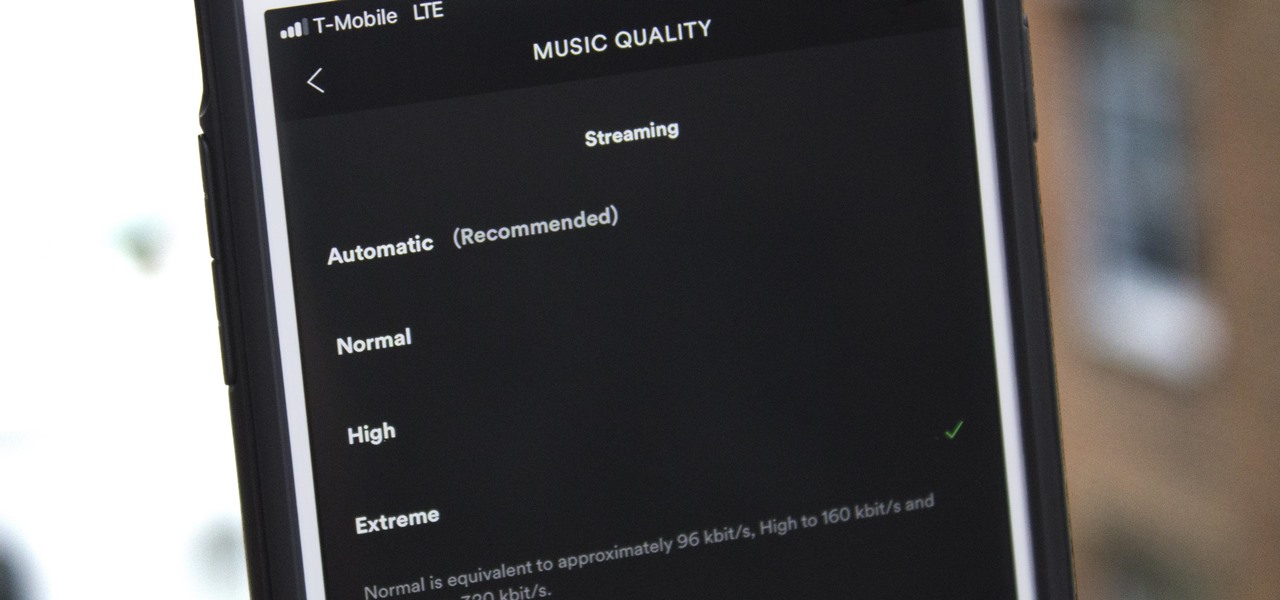
Spotify's massive song catalog can be streamed in decent quality on iPhone or Android without any tinkering. But if you're an audiophile, you've probably noticed that the sound quality can fluctuate from time to time.

How can something get more free than free? Well, in the case of Twitter, Virgin Mobile found a way with its newest promotion. If you have a 4G plan with Virgin Mobile, you can now access Twitter from your smartphone without it counting towards your monthly data allowance.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expandable status bars to suit their unique needs.
Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.
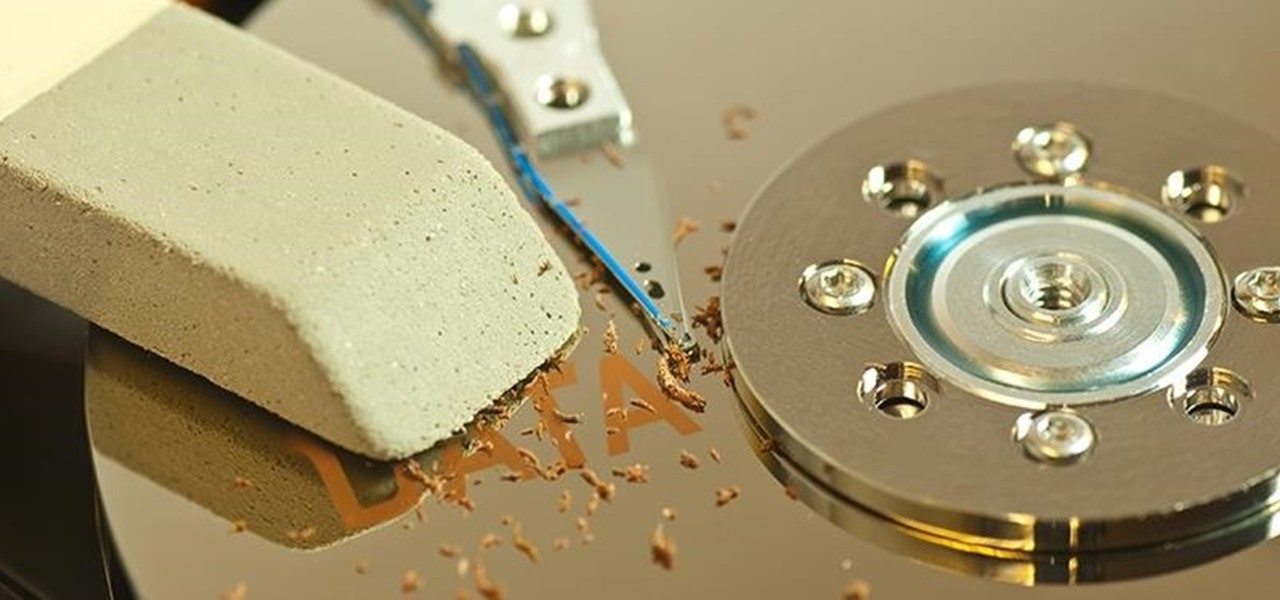
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.
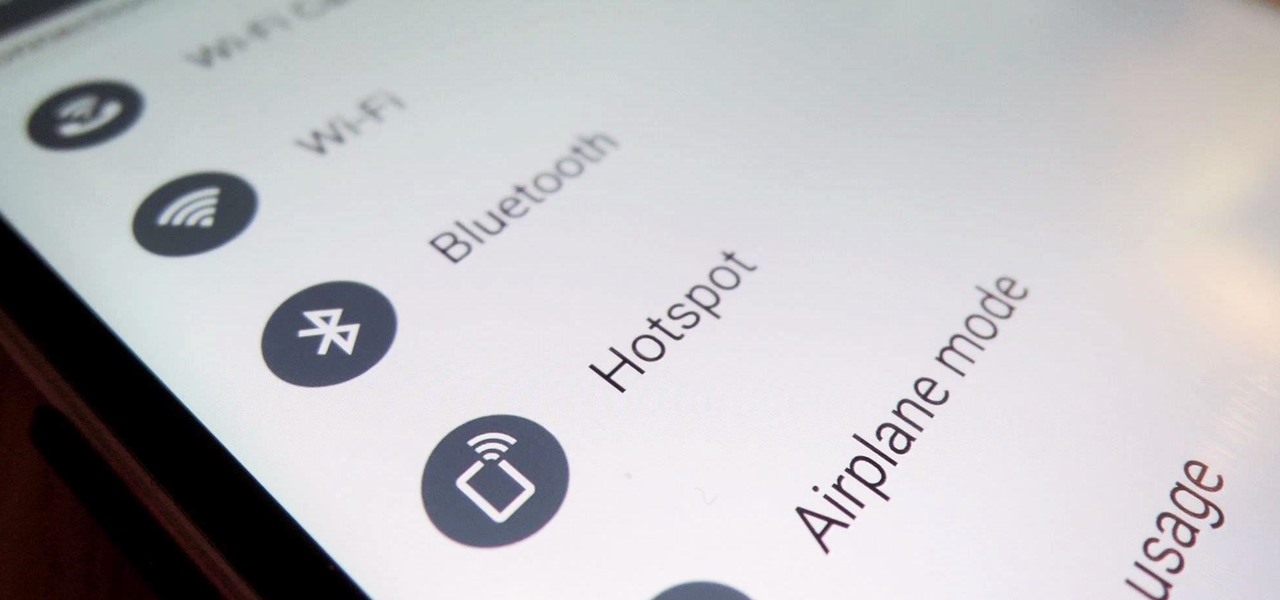
T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

Carriers really suck, don't they? We constantly have to monitor our data usage, even though many of us are on "unlimited" plans, which, in reality, will just be throttled to a slower 2G or 3G connection when we hit a certain download threshold.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.