
How To: Stop pipes from freezing by applying insulator and caulk
About a quarter of a million homes sustain damage from broken pipes every winter. Here's how to avoid a similar fate. Watch this video to learn how to prevent pipes from freezing.


About a quarter of a million homes sustain damage from broken pipes every winter. Here's how to avoid a similar fate. Watch this video to learn how to prevent pipes from freezing.

Learn how to wash leafy greens. Is a bath for your leafy greens really necessary? Well, yes, especially if they're organically grown.

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Learn how to clean up after Christmas and pack away Christmas decorations in this free home organization video series.

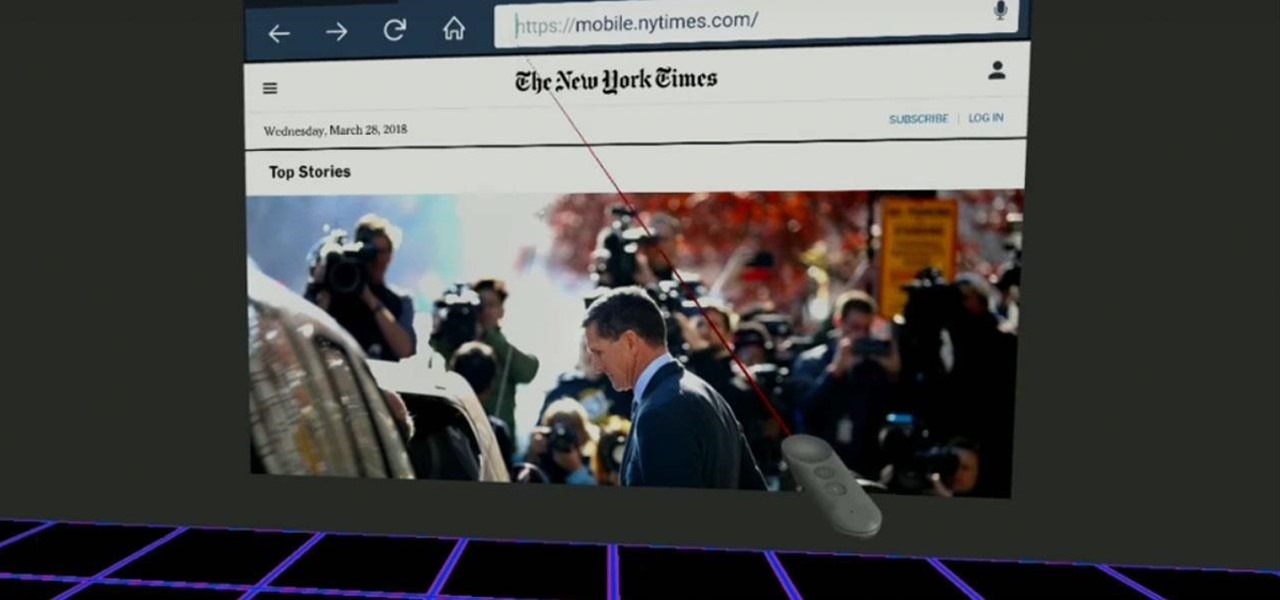
After establishing itself as a leader among media companies in augmented reality in journalism over the course of 2018, The New York Times pulled back from the technology this year.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.
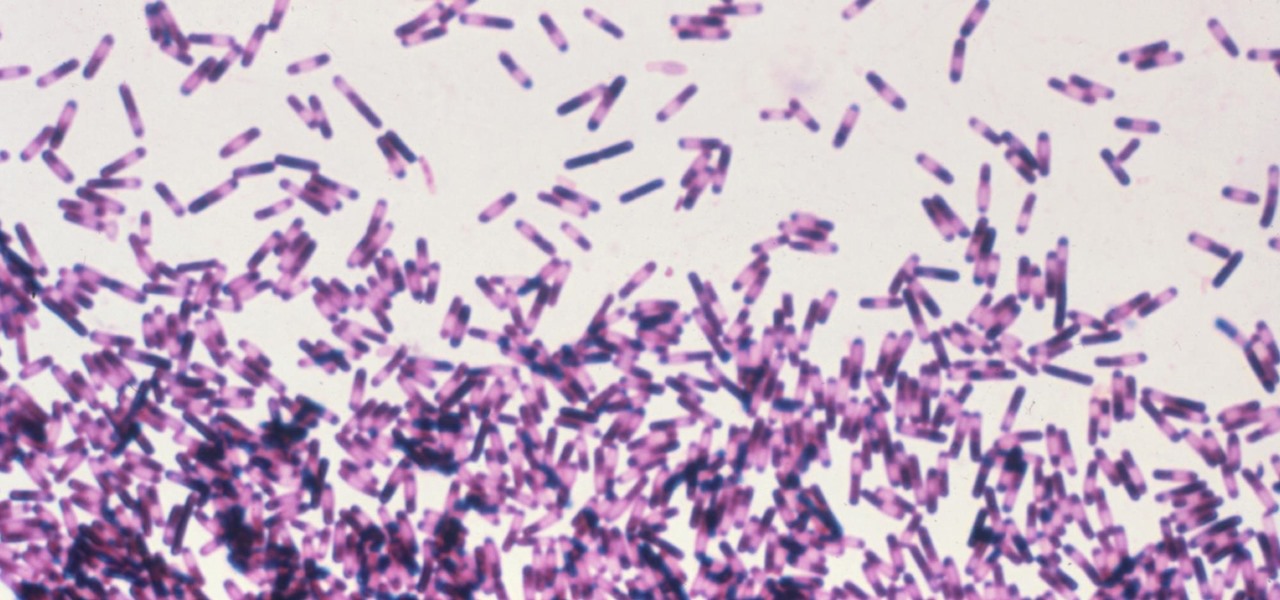
Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Aerobics are a super fun way to get rid of some calories and lose weight. If you really enjoy your classes, maybe you should consider taking up a healthy career as an instructor! This video will give you the steps you need to make your new job happen!

Stuttering is a communication disorder affecting over 3 million Americans. Stuttering can make school and other social interactions difficult. Although there are no instant cures, these tips will help your progression toward speech fluency.

It's easy to find yourself drowning in a pile of papers and nick-nacks if you're not armed with a good organization system. By taking the time to set up a system where everything is condensed and has a place you'll find it much easier to keep it that way.

You have a purebred, make it official. With a few simple forms your purebred dog can be a member of the American Kennel Club and carry on the traditions of and gain access to this exclusive organization. Your dog can have an official pedigree.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.
Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

One of the most highly-cited drawbacks to the HoloLens is its limited field of view (FOV), but now it appears that Microsoft has solved that problem.
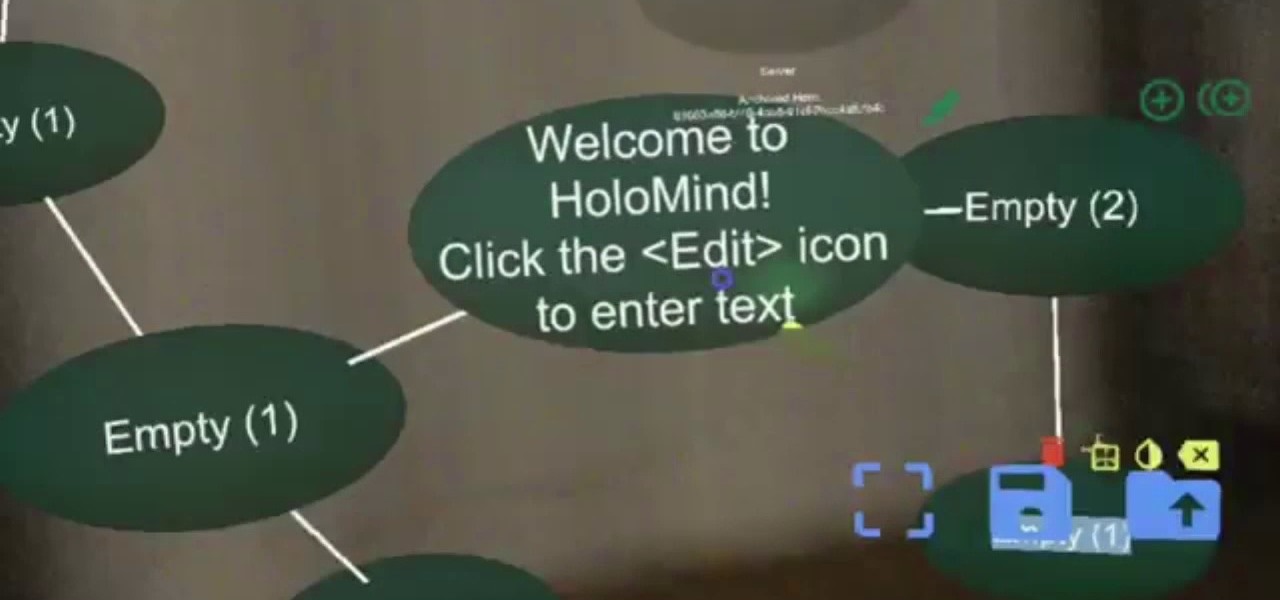
In the world we live in now — a world of complete data overload — new ways to sort through that data moves well past "nice-to-have" and firmly into the needs category. Mind mapping has been one tool that allowed someone to break down large problems into like components and help visualize the problems in different ways. Now thanks to Data Experts gmbh's Windows Store release Holo-Mind, we can do that in 3D on the HoloLens.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

If you've ever made graphs and charts, you know it can be a struggle to represent a large amount of data. It's something that just doesn't work very well on a flat surface. In virtual and mixed reality, however, the data can exist all around you.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen when you can get a better grasp of everything by just checking out the Notification Center instead.
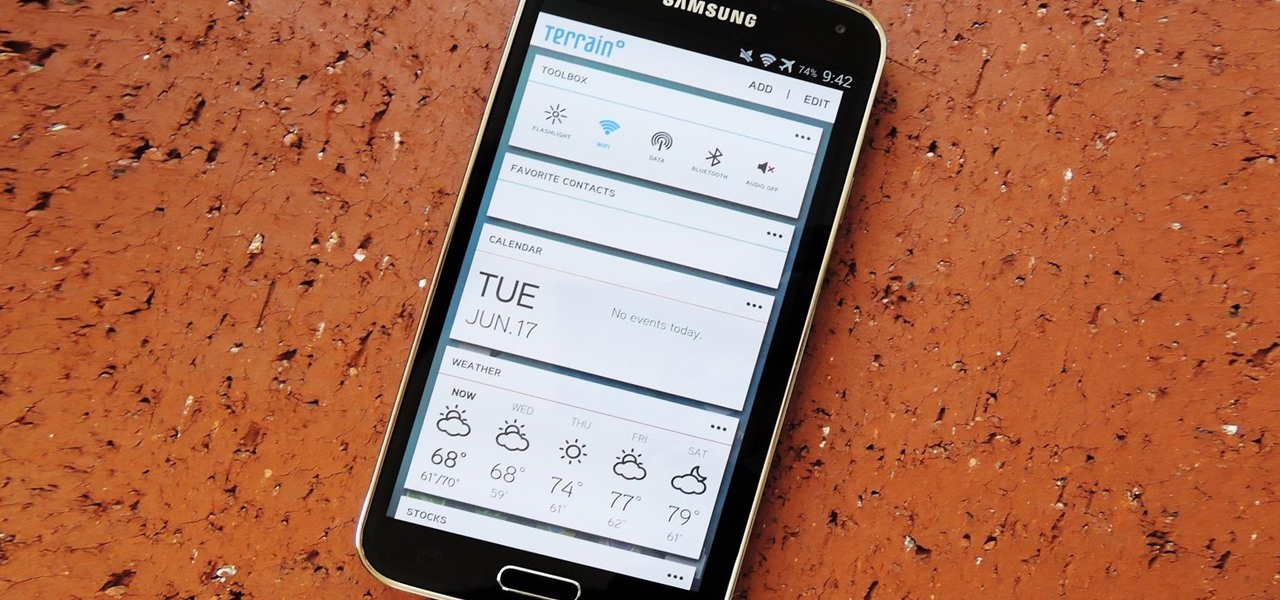
With the release of the M8, HTC decided to begin publishing some of its exclusive apps to the Google Play Store. While most of these apps aren't available for download unless you own an HTC device, this practice made it possible for the Taiwanese smartphone manufacturer to issue updates to its users independently of carrier-modified firmware upgrades.

Sometimes I actually search Google Images for things other than GIFs and pictures of athletes' extremely hot wives. Google Images has helped me with school projects, work, and proving my friends wrong on numerous occasions. Unless you're strictly using it for the latter, you're going to have to be aware of copyrights.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...
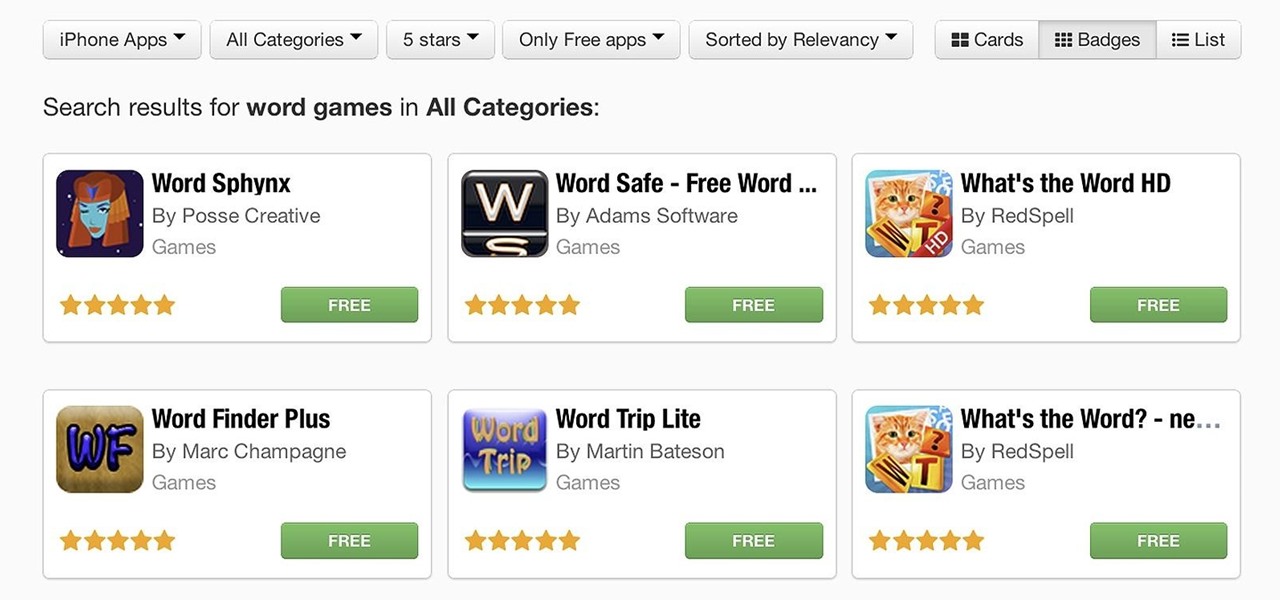
If you have an iOS device, chances are you've spent a decent amount of time in the App Store—without at least a few apps, smartphones are pretty boring. There's an app to do just about anything you could ask for, but the problem is finding them. Searching the App Store sucks.

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

Need to organize information in your PowerPoint presentation? Learn to make an organization and a cycle flowchart. This is a great tool to use in presentations in the classroom and the boardroom.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

Most people have tons of gadgets laying around the house these days, and they all need to be charged. Let the Wood Whisperer take you through the process of building a gadget station for all your favorite electronics. From laptops to cell phones, this gadget station will hold them all. Be sure to watch the entire 12-part tutorial from beginning to end for the whole experience.
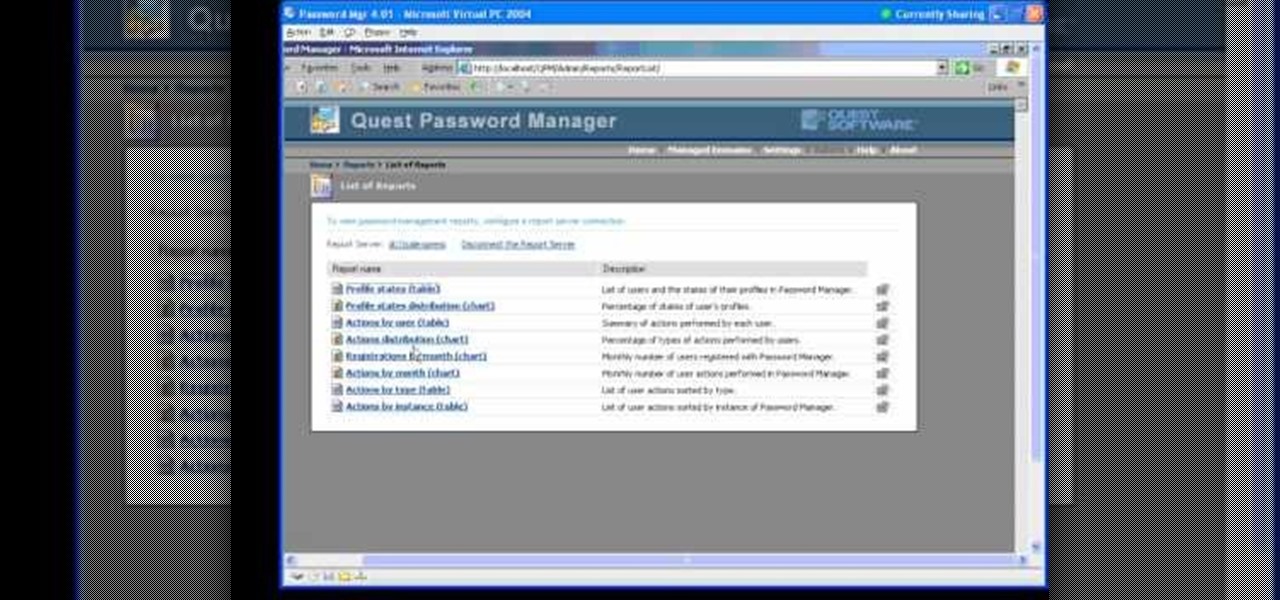
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.