When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

If you've ever made graphs and charts, you know it can be a struggle to represent a large amount of data. It's something that just doesn't work very well on a flat surface. In virtual and mixed reality, however, the data can exist all around you.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.
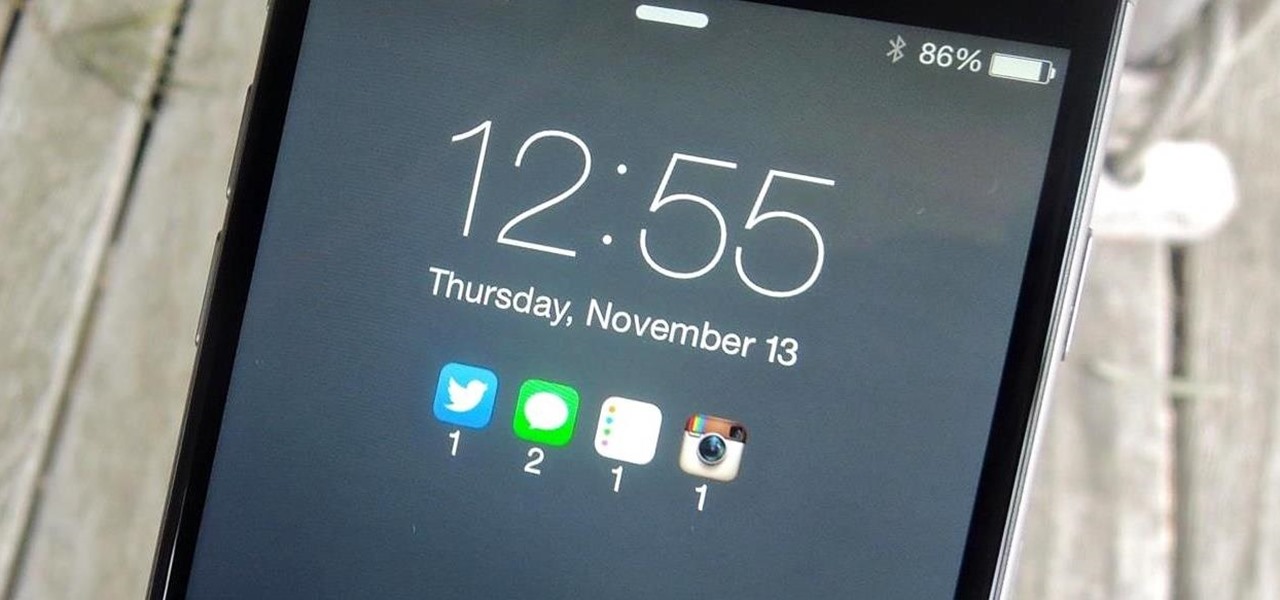
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen when you can get a better grasp of everything by just checking out the Notification Center instead.
With the release of the M8, HTC decided to begin publishing some of its exclusive apps to the Google Play Store. While most of these apps aren't available for download unless you own an HTC device, this practice made it possible for the Taiwanese smartphone manufacturer to issue updates to its users independently of carrier-modified firmware upgrades.

Sometimes I actually search Google Images for things other than GIFs and pictures of athletes' extremely hot wives. Google Images has helped me with school projects, work, and proving my friends wrong on numerous occasions. Unless you're strictly using it for the latter, you're going to have to be aware of copyrights.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...

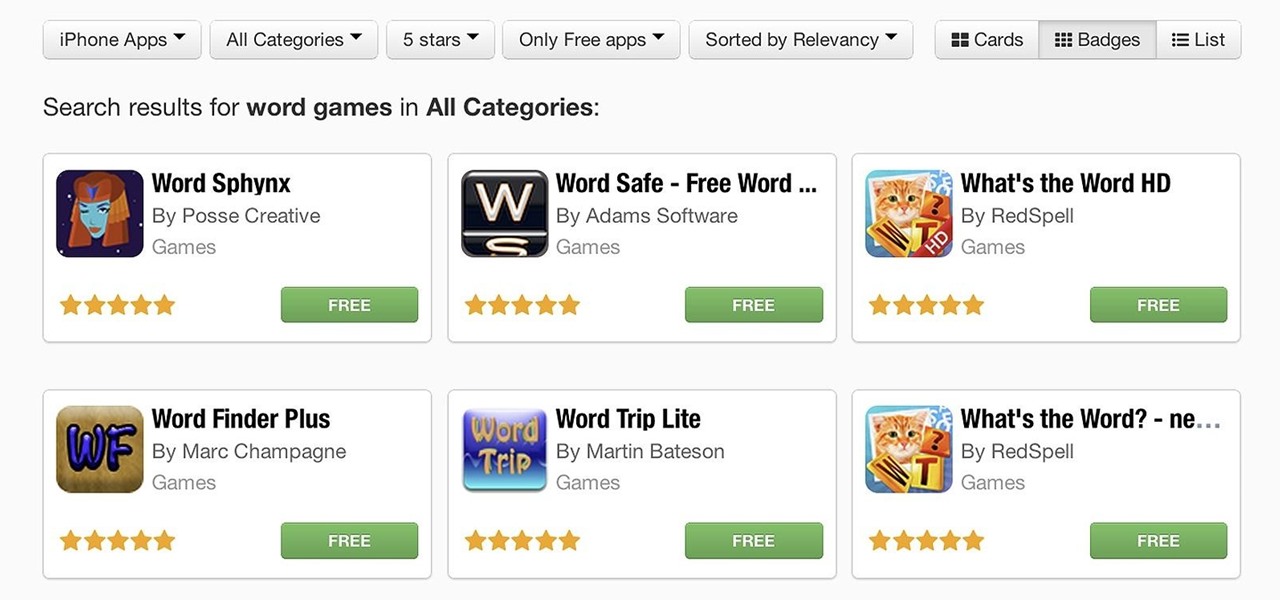
If you have an iOS device, chances are you've spent a decent amount of time in the App Store—without at least a few apps, smartphones are pretty boring. There's an app to do just about anything you could ask for, but the problem is finding them. Searching the App Store sucks.

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

Need to organize information in your PowerPoint presentation? Learn to make an organization and a cycle flowchart. This is a great tool to use in presentations in the classroom and the boardroom.

Most people have tons of gadgets laying around the house these days, and they all need to be charged. Let the Wood Whisperer take you through the process of building a gadget station for all your favorite electronics. From laptops to cell phones, this gadget station will hold them all. Be sure to watch the entire 12-part tutorial from beginning to end for the whole experience.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the UK and the Netherlands within the next two years.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

Selecting text on a touchscreen device has always been a major pain point. Those tiny little arrows that let you adjust the selection area are always too hard to actually adjust, making precision all but impossible. Then there's the issue of some apps not even allowing text selection in the first place, so the entire experience is basically a big mess.

You may have had to deal with this unfortunate scenario when you have a hankering for homemade ice cream: you find a great recipe, just the flavor you want to make, you start reading it... and you discover those ever-dreaded words "pour into your ice cream maker and process according to manufacturer directions." Oh no!

It seems like Microsoft has finally come to the realization that their Windows Phone mobile operating system is probably never going to compete in today's smartphone market. Why do I say that, you ask? Because they've recently started to embrace the more popular platforms by releasing some quality iOS and Android apps.

Smelly foods are what make my culinary world "go 'round," so to speak. I grew up with fish sauce, learned to cook with and love fermented beans and veggies, and am one of the biggest garlic advocates I know... other than my husband, who thankfully shares the same smelly food sensibilities. (Let's put it this way: anyone that can stomach stinky tofu can handle anything I could possibly cook up.)

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

Watch this video tutorial to learn how to book the best hotel room for your money. You've spent all year saving up for your dream vacation. The last thing you want is to end up in a hotel room that ruins the whole trip.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

Is your fridge getting out of control? Can't identify that raunchy smell that has invaded your ice box? Can't find your ketchup? The best way to alleviate these problems is by organization. Organizing and keeping your fridge tidy is the best way to go, but it could be hard in a roommate situation where one said roommate will never give a damn. Nonetheless… chill out! Use these helpful tips to get your refrigerator organized.

How much time have you wasted, wandering around your home trying to find one particular book? Without a good system of organization, finding the book you're looking for can become a hopeless task. Organize your book collection at home by following this tutorial.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

Augmented reality's status as a new storytelling medium has already led to the reinvention of filmmaking and journalism.