With iOS 12, Apple is offering users more options than ever to create, store, and manage their saved passwords. Not only can iOS 12 make you new passwords via the AutoFill feature, you can quickly and efficiently access your entire iCloud Keychain using Siri. Why go hunting for the passwords yourself when you can ask your iOS assistant to find them for you?

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.
While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Ah, the sand between your feet, the sun on your skin, and the debt you're accumulating. However strong my sense of wanderlust may be, I still can't justify dropping thousands of dollars on a vacation. Fortunately, a new site — Wander — promises to help you book vacations that match your budget.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

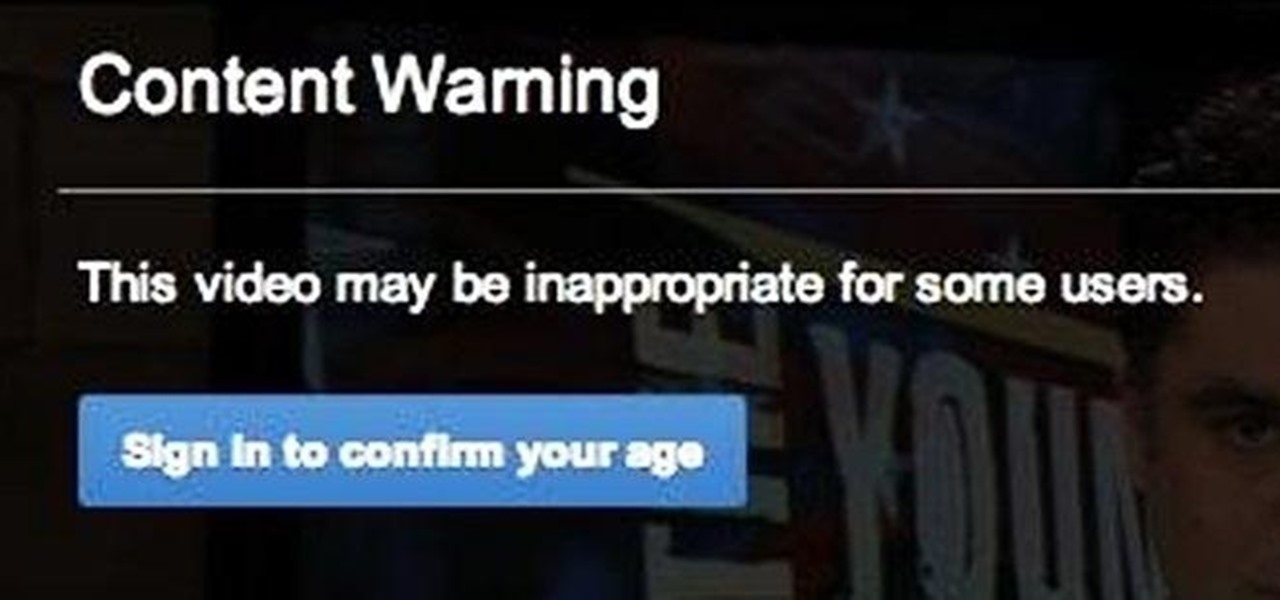
YouTube is the first place I go to watch funny videos online—me and about a billion other people. But one thing that always annoys me is having to sign in time after time to view age-restricted videos.

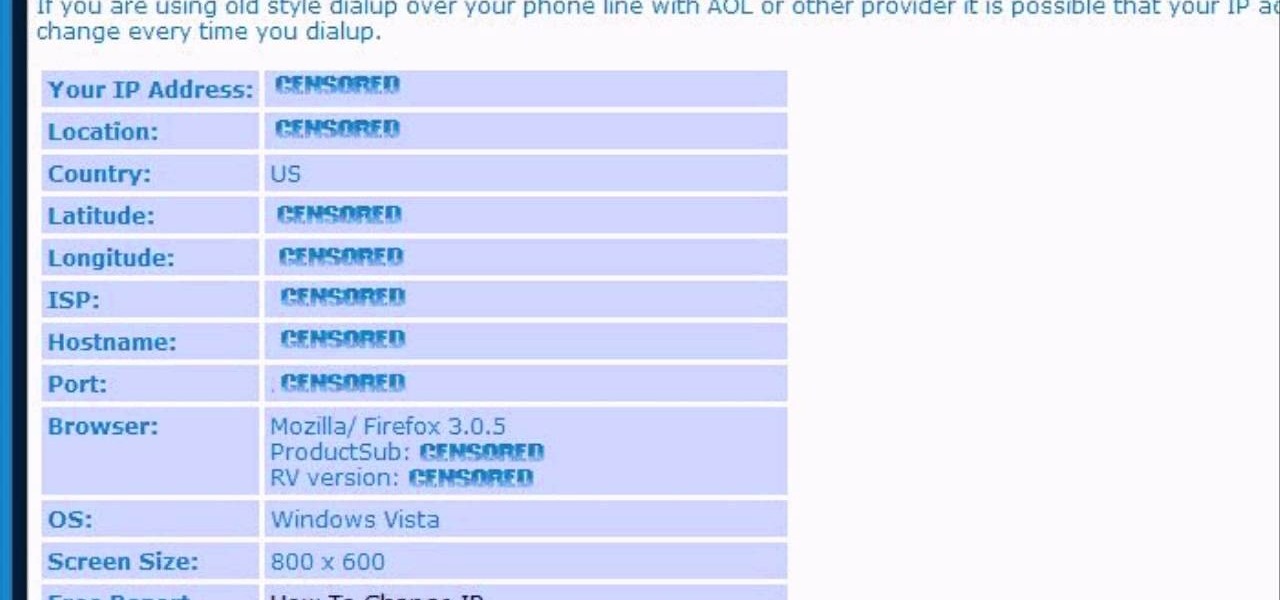
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. Once you have this information, make sure you don't share it with anyone else. If someone gets this information, they will be able to hack into your computer and ruin it. They could also access sensitive information and s...

In this video, we learn how to unblock a Facebook firewall at school. First, you will need to try to go to the website you want to go. If you try this and you can't reach the site, go to the top of the bar where you typed the website in at. Once here, you will find where it says "http". Type in an "s" after the "http" so you end with "https" then type in the website that you want to visit. After this, you should be able to go to the website you want to go to without any trouble, just make sur...

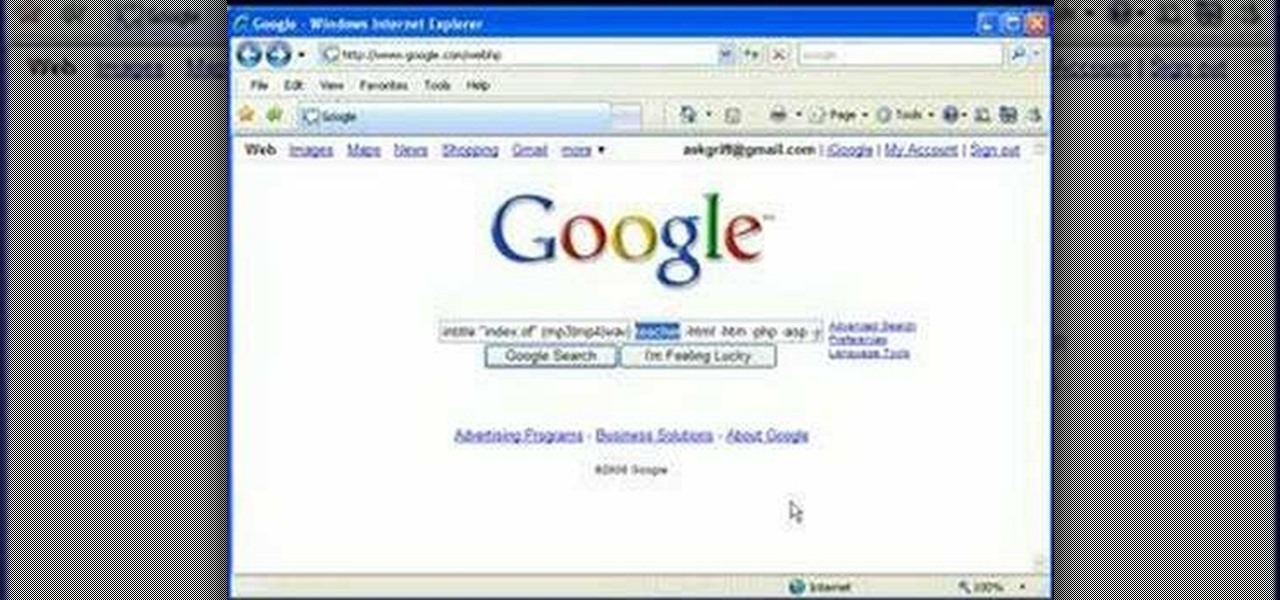
In this video, we learn how to find music and movies easier using "insite" in Google. If you are looking for media and can't find it through iTunes or an official site, you can find it on Google. First, go to Google, then type in "intitle:"index.of"(mpg(avi)wmv) (word you're searching for) -html -htm -php -jsp -asp". After you search this, you will see "index of" pages where you can do searched of what you are looking for. Once you click on the links that are available, you will be able to do...

In this tutorial, we learn how to get started out on Twitter. First, you will need to go to the main website and sign up by entering in your personal information. After you do this, you will be asked to enter in your other e-mail addresses to see if your other friends are on Twitter as well. After this, you can change your settings to change the icon that shows up on the site. Next, you will be able to start to follow people and enter in what you want your tweet to say. Go through the differe...

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.

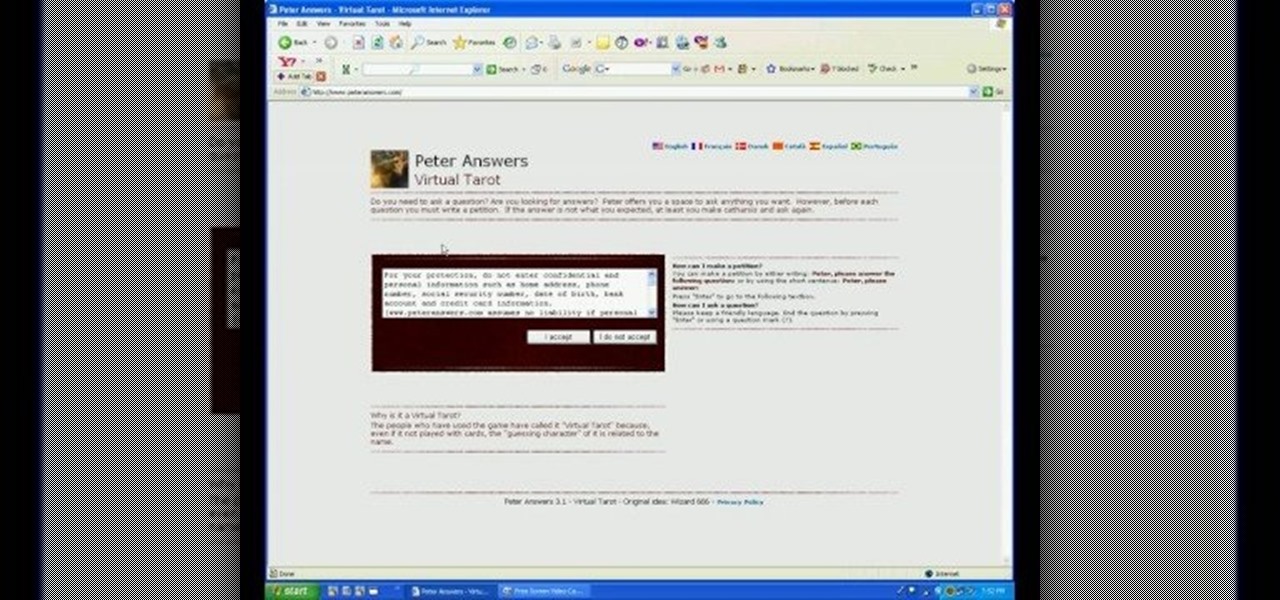
Peter Answers is a fun website online that you can use to play pranks on your friends. This site is easy to access, free and requires no downloads.

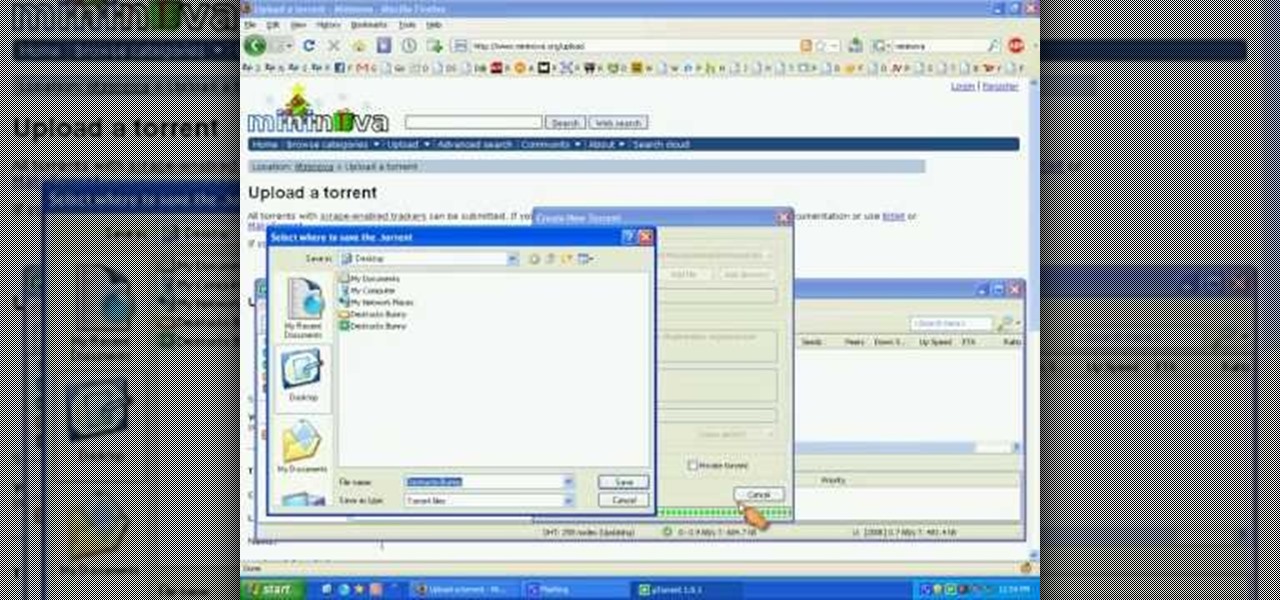
In this how to video, you will learn how create a torrent using uTorrent. First, download the program uTorrent. Next, find a tracker on a website such as Mininova. Open up uTorrent and go to file and create new torrent. Next, select the folder in which the files you want to upload are located. Paste the tracker in the form shown. From here, press create and save us. Choose a name and then close. Now your tracker will be created. Next, upload to the site by going to the website and uploading t...

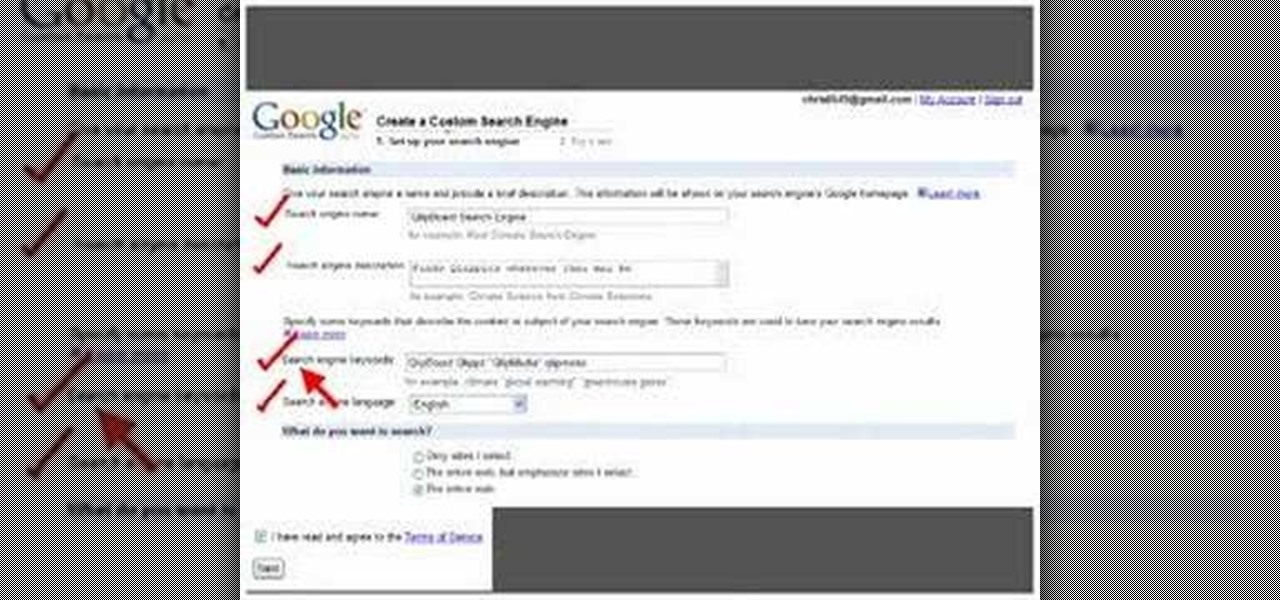
This video shows how to make a Google Custom Search Engine. A Custom Search Engine safely searches only the sites you want, and gives you relevant results. To set it up go to the Google home page and sign in. If you don’t have a Google account, you can easily set one up by following the directions. Sign in, then enter in your browser “www.google.com.coop/cse”.

This will illustrate us how to use the reverse auction site Dubli. Here are the following steps.Step 1: First of all enter the link and log onto the official website of DubliStep 2: Now you will find various options on the homepage of Dubli.Step 3: go and click the option of auction option.Step 4: The various product that are for auction will be displayed.Step 5: Search for the product that you want to auction for and enter the amount that you pay for the product and press the go button.Step ...

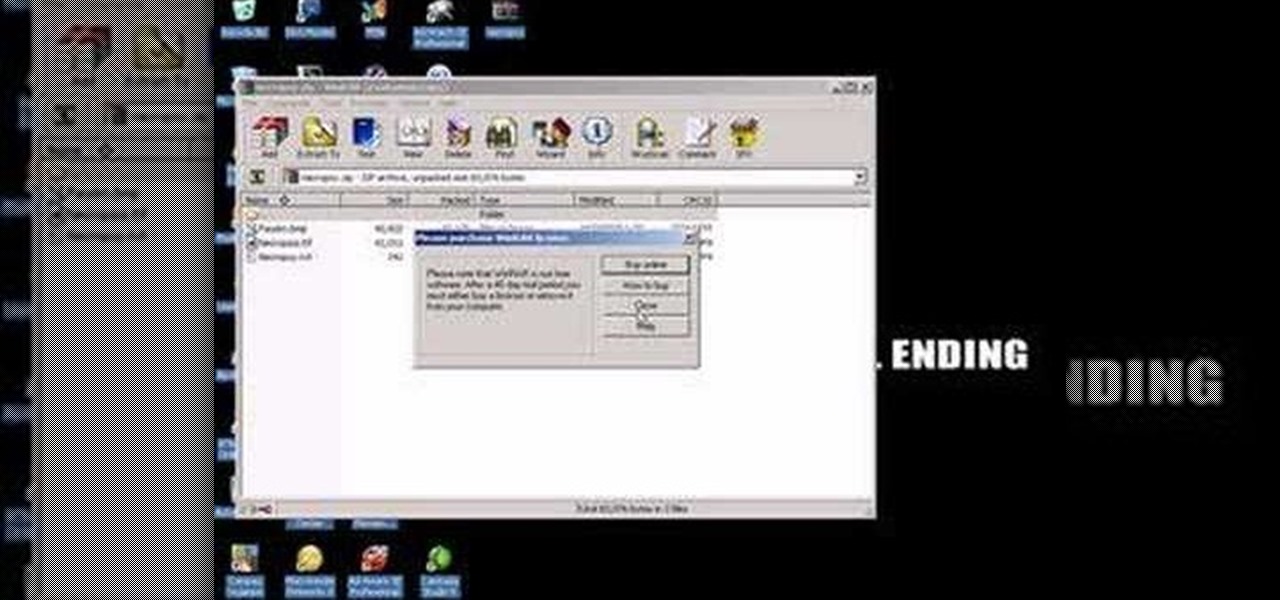
This video is about how to install custom fonts on XP. The first thing to do is to open your browser and type "fonts" in the search bar. Several sites will appear and just simply click on any of the websites. Once you have found the site that suits you best, just start looking for fonts that you may like. And if you already have found a font, just simply press download then save it in your computer. Once you have saved it, other files need to be extracted so just simply extract it. After extr...

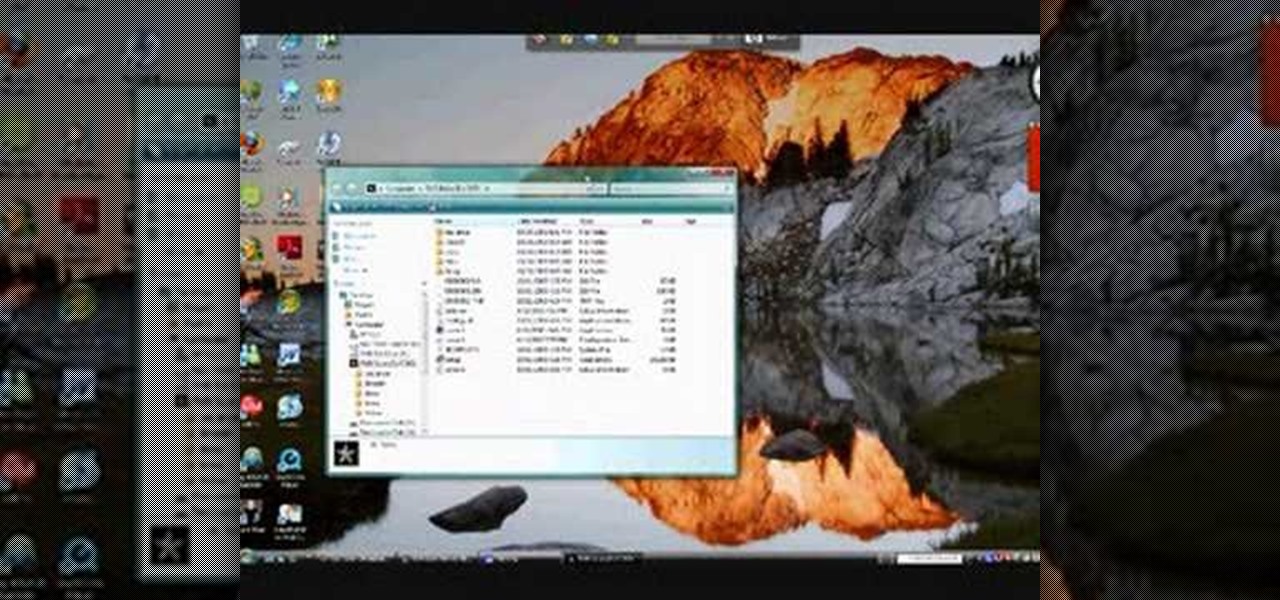
In this video you will learn how to download a torrent PC game, mount and the burn it. For this you will need a torrent program (to download torrents), daemon tools (to mount the images) and powerISO (to burn it). To get a torrent go on site mentioned in the video or on other torrent sites. After you downloaded the file, right click on daemon tools icon select virtual drive and mount your image. Enter in image from my computer, take the CD key from crack and write it on a CD case. To burn it ...

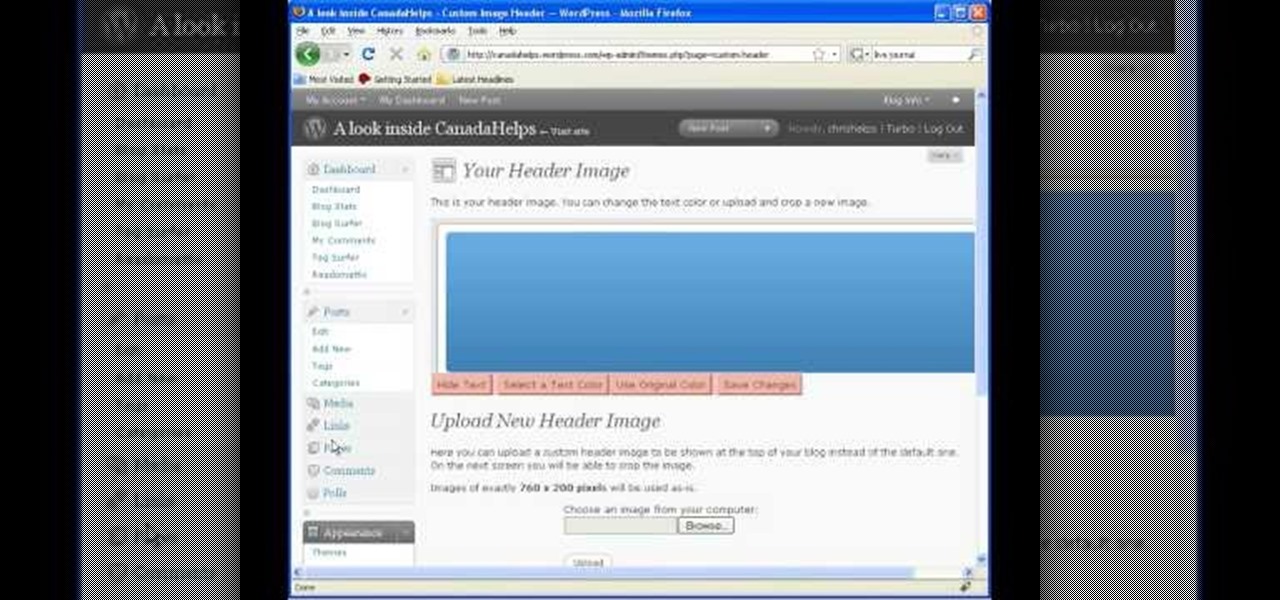
In this video tutorial, viewers learn how to start and set up a free blog. Viewers will learn how to setup a free blog for a charity, make a blog entry, edit and customize a blog and share a blog with their network. A blog is a online journal that provides the reader with regular posts on various topics. Three of the most popular blogging sites are: Blogger, Word Press and Live Journal. When creating a blog, keep the posts short and meaningful. Try to engage the reader. Update your blog regul...

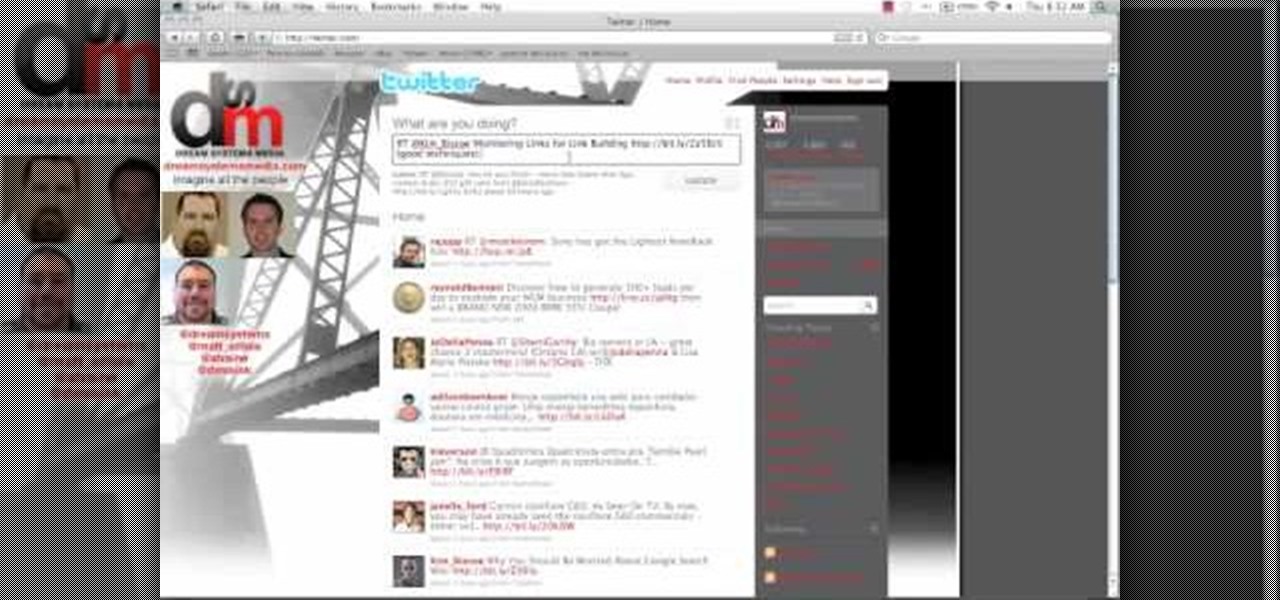
This video shows the method on how to Retweet web sites using Twitter. The website used on this video is Dream Systems Media. First, choose an interesting topic to tweet. Highlight and copy the entire tweet. Second, using either of the following codes: RT, rt, R/T or retweet, and the ‘@’ symbol; paste the tweet previously copied. Check if the tweet contains the name of the site and the URL. Third, place your comment inside the parenthesis following the tweet. Last, click the update button and...

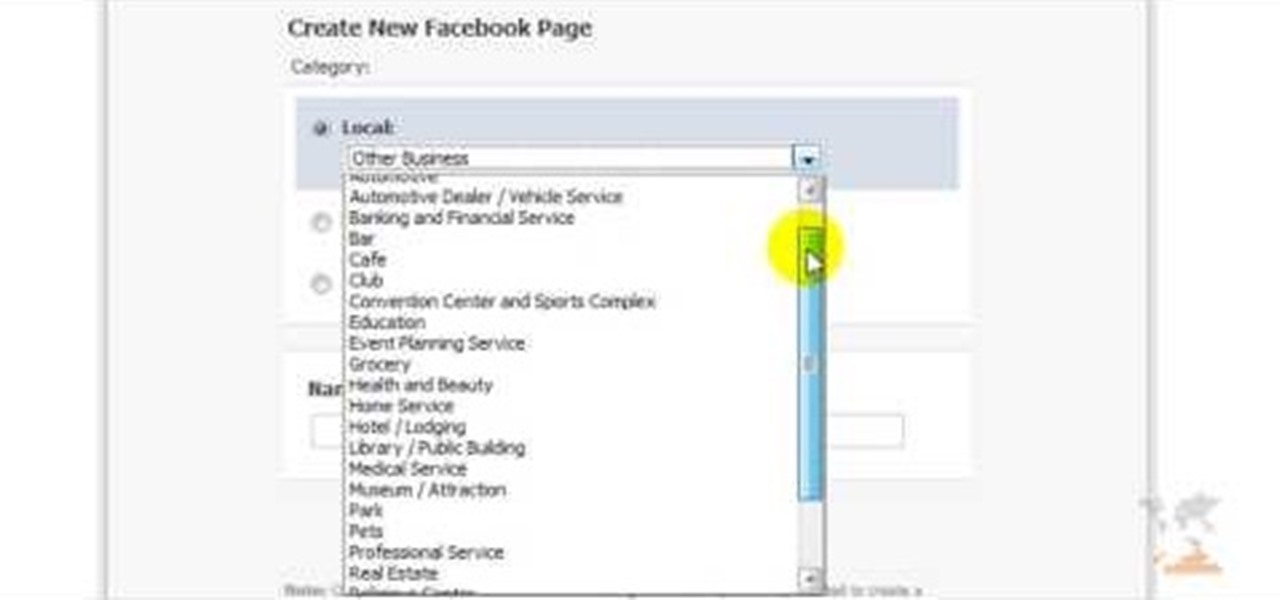
Facebook is one of the most popular Social Networking Sites around. Watch as this video shows you how to make your very own Facebook page so you will be included in one of the biggest things around! First, you want to sign up for an account. "Its free and anyone can join" is their slogan! Go to www.Facebook.com and get to signing up! After that simply login into the site using your user name and password. After that your profile is set up you must simply just personalize it. Fill our your inf...

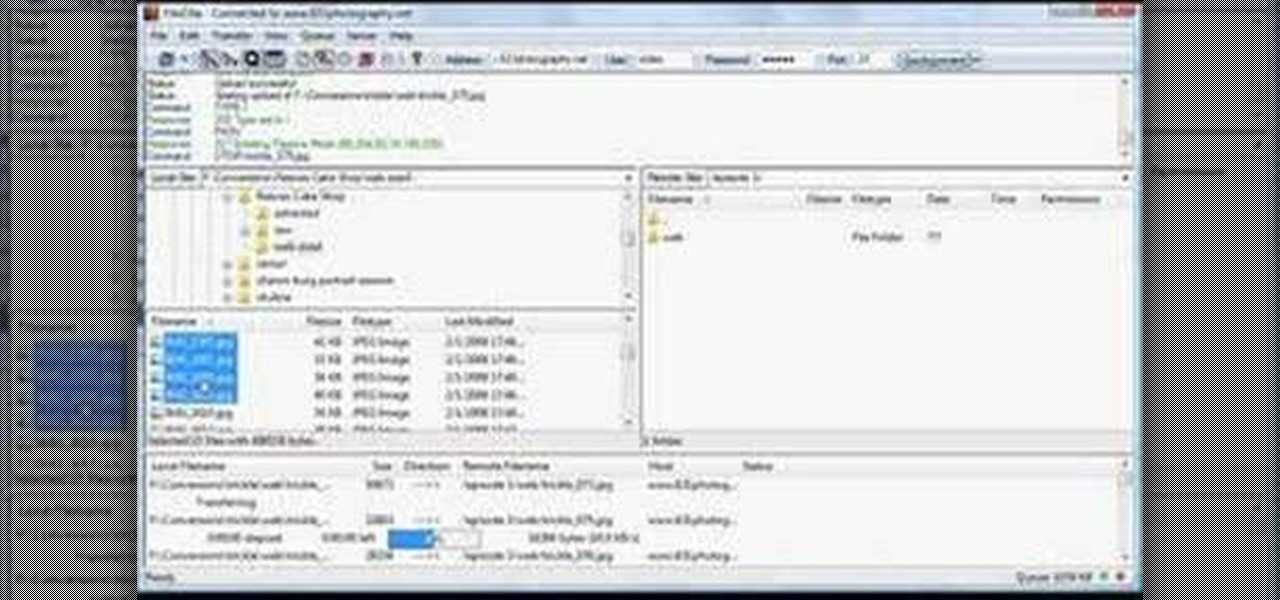
Shannon Smith shows how to upload files using Filezilla in this episode of No Mac, No Cheese. Filezilla is useful in assisting you with putting files onto a web site. Simply type in your web address, user name, and password. Then create a folder and name it appropriately. Adjust the properties by keeping all permissions enabled. Then, open up the file to find all of the folders on your hard drive. You can easily drag and drop a folder from your hard drive or double click to individually selec...

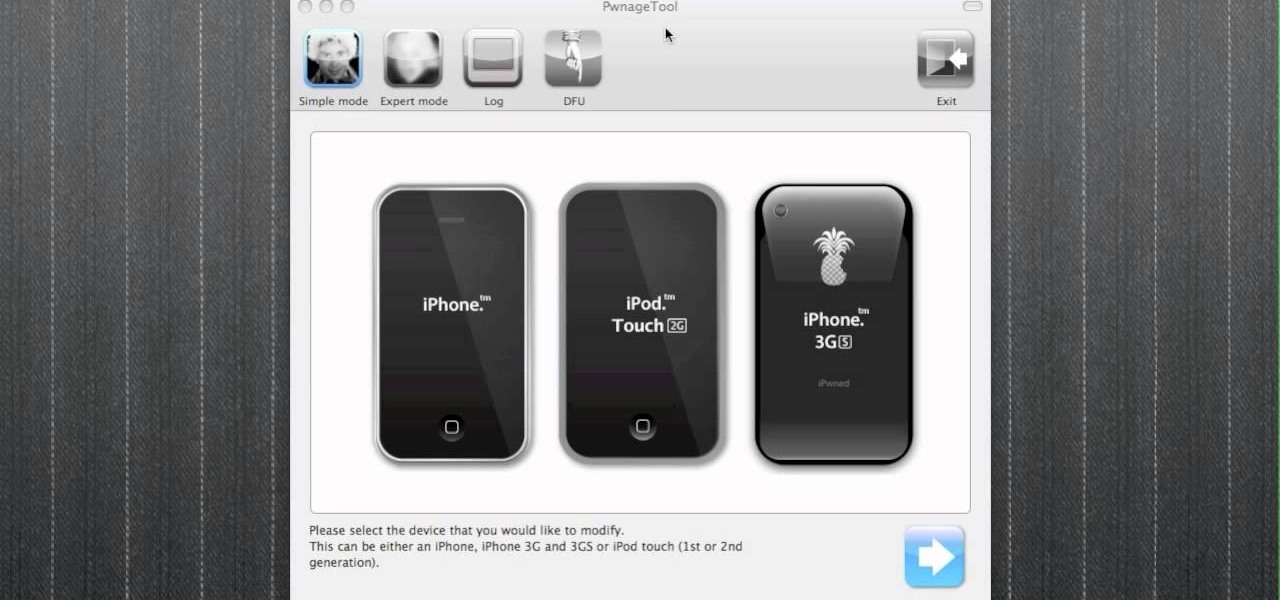
Are you a Windows user who wants to jailbreak your iPod Touch 2G 3.1.1? George from the iPhone Press shows you how in this video. The needed firmware is on the Megaupload site. There is a link provided that will take you to the site so you can download the firmware. Next, it tells how to put your device into DFU mode using Pwnage Tool. Then it explains how you connect your device to your computer, and get iTunes to open up. After iTunes opens, the video shows how to navigate in iTunes to get ...

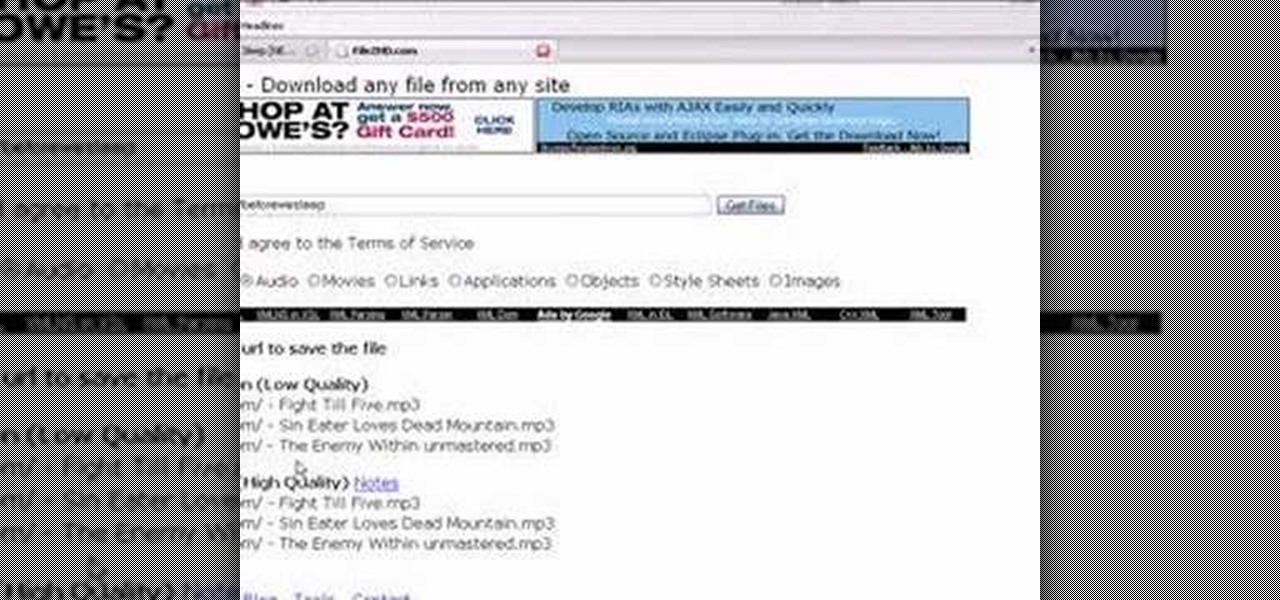
Want to download a music track that you heard on MySpace? this video shows you how to download music from MySpace using the site File2HD.com. First find the MySpace page that has the music track you want to download, copy the URL and then go to File2HD.com and download the music track as shown in the video make sure to accept the terms and conditions. File2HD.com can be used to download music or videos from other sites that stream content so watch this video and happy downloading.

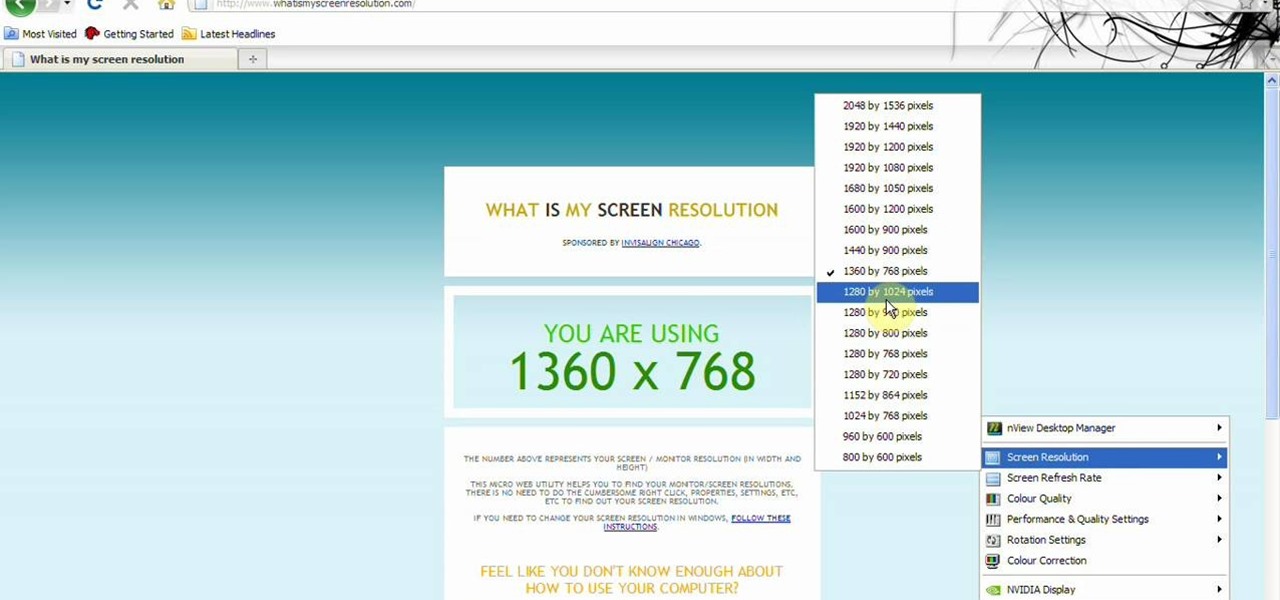
This video tells about the screen resolution of your monitor. In this video it is said that we can check our screen resolution by opening the site www.whatismyscreenresolution.com .While you get into that site our screen resolution will be displayed in the screen. But the screen resolution can be checked easily by clicking the right button of the mouse in the desktop and then selecting the properties button. In the small window that appears click on the settings tab. In that window we can see...