Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

Yo dawg, Snap heard you using Snapchat augmented reality Lenses in your messages, so it's putting its AR Lenses in other messaging apps.

Metadata might be a bigger concern than you might realize. In its continuous push to be a privacy-first company, Apple has released several new features with iOS 15 that allow you to adjust and permanently change the metadata stored within the photos and videos you take on your iPhone. But why would you want to do this?

The majority of us have been shown, again and again, that we want our own business. Business software is making this a reality by automating and simplifying the complex parts of running any company.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

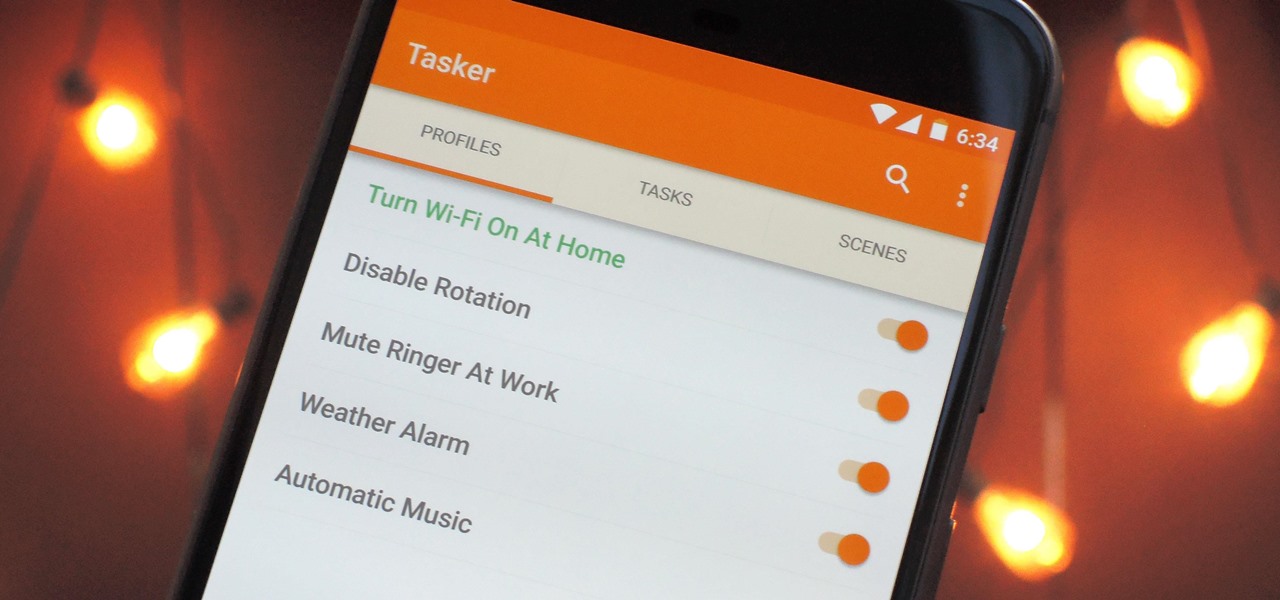
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

The close of the second quarter of 2021 brought about a flurry of merger and acquisition and financing activity in the augmented reality industry, headlined by the acquisition of Ubiquity6 and JigSpace's new multimillion-dollar funding round.

The economic impacts of the COVID-19 pandemic have been felt in practically every business sector. Now, as we look back at the top augmented reality investments of 2020, the AR industry has been no exception.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

YouTube is so famous it needs no introduction, but its mischievous clone, YouTube++, sure does. The latter's been tweaked to include hacks not found in the regular version, including background playback, ad blocking, and the ability to download videos directly onto your iPhone, iPad, or iPod touch.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
Welcome back Hackers\Newbies!

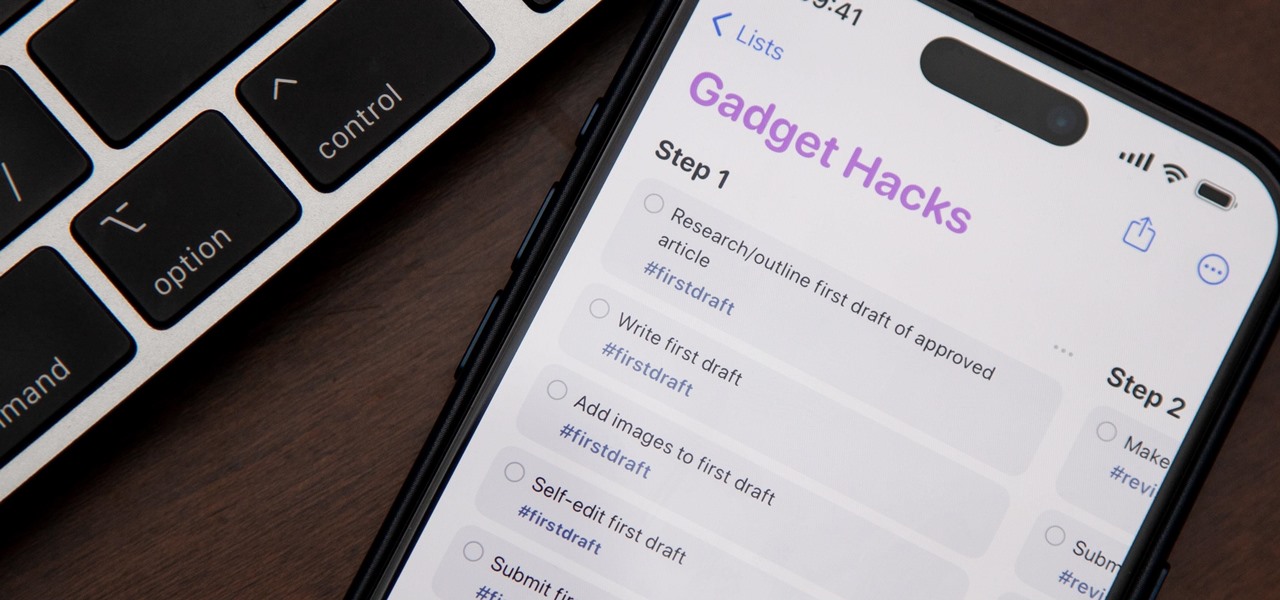
If you're still using a third-party task manager on your iPhone, you might want to check out Apple's updated Reminders app. With each new update, Reminders gets more powerful yet remains one of the simplest task managers to use, and iOS 17's new to-do list features reinforce that statement.

Apple's Reminders app on your iPhone or iPad now comes equipped with a new way to organize your tasks: sections. With sections, you can better sort through reminders in your lists by placing tasks into likeminded buckets or even in kanban-style columns for more efficient workflows.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

The Metaverse, or AR cloud, has been a sci-fi dream for decades, but only recently have companies begun to actually develop the technology to build it. With its latest funding round, Epic Games is suddenly a front-runner in this pursuit.

You can't beat Samsung's hardware, but their software still isn't for everyone. That's the thing, though — software can be replaced. So if you're more a fan of Google's vision for Android, but you can't get enough of Samsung's beautiful screens and build quality, you're just 11 steps away from getting the best of both worlds.

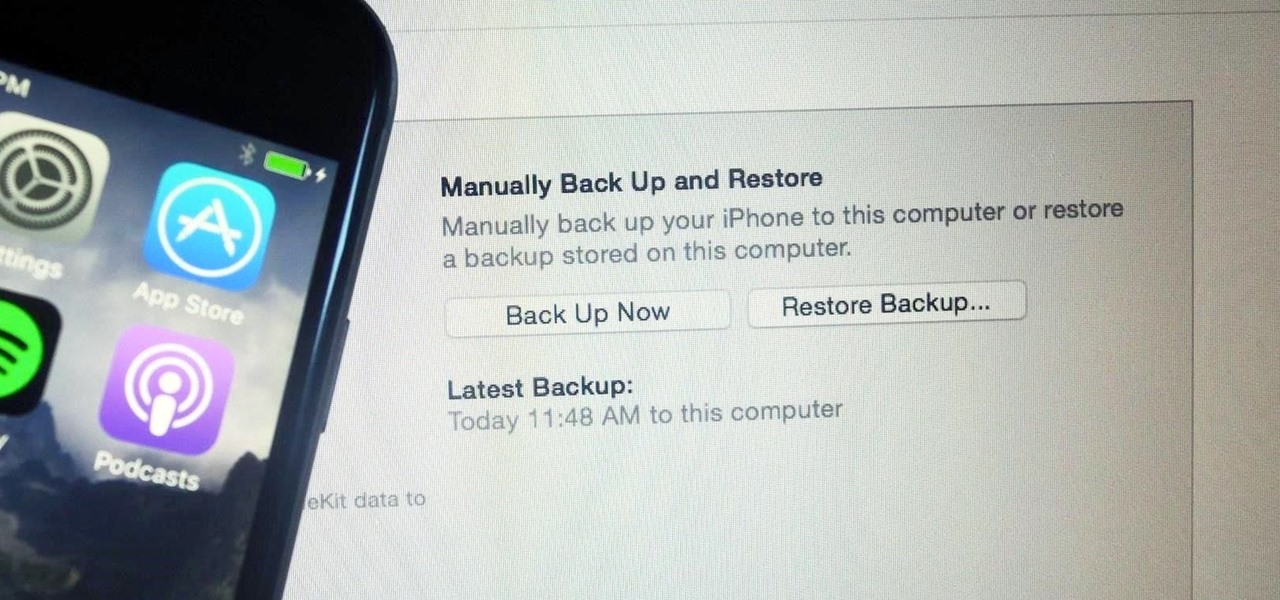
It's easy to back up and restore your iOS devices using iCloud, but there are a few downsides to encrypted iCloud backups. For one, Apple holds the key to decrypt all the data. Plus, you're limited to only 5 GB of data for free before you have to upgrade your storage to 50 GB, 200 GB, or 2 TB.

The smartphone market is stagnating. Without hordes of new users rolling in every year, the best way to boost profits nowadays is to poach customers from the competition. That's exactly what Apple appears to be doing with iOS 14.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.