
How To: Deal with seasonal affective disorder or S.A.D.
Don't put up with another winter of discontent. There are simple things you can do to lift yourself out of the doldrums.


Don't put up with another winter of discontent. There are simple things you can do to lift yourself out of the doldrums.

Is your girlfriend or boyfriend always right? No matter what you say, they will always be right? Well, in this tutorial learn how you can win in an argument fair and square with a few simple techniques.

Whether you're hanging out at the beach, laying by the pool, or walking around in sandals, having nail fungus is not the most attractive thing to flaunt.

Keep your paintbrushes looking like new with these cleaning tips. You Will Need
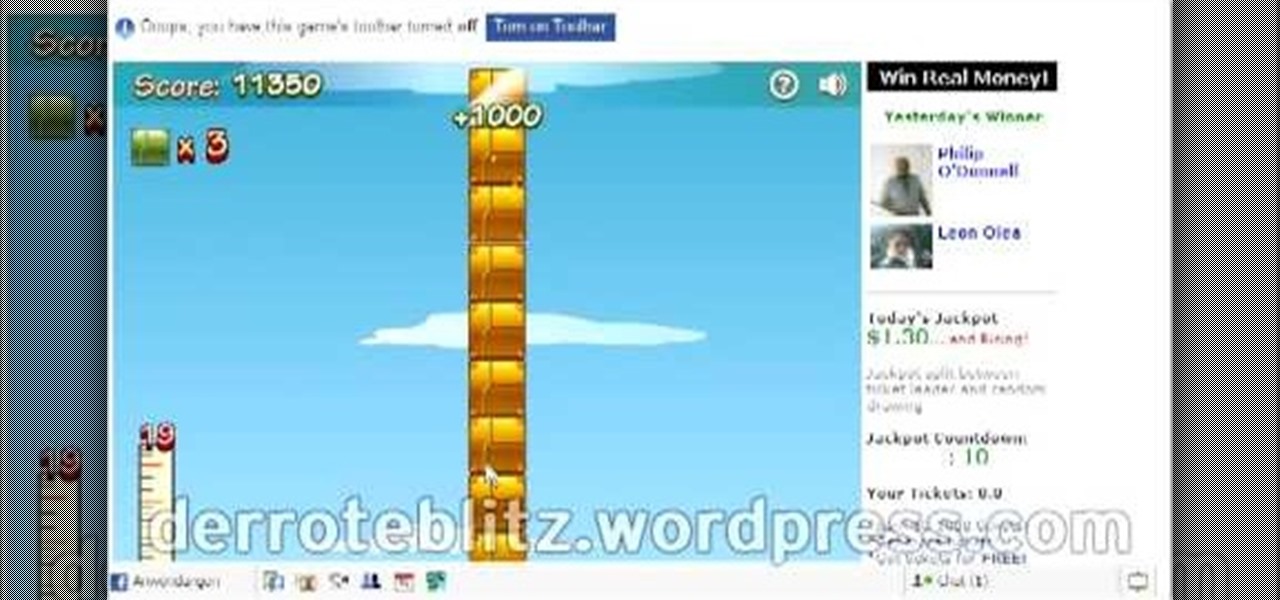
Tower Blocks is a Facebook game that allows you to test your speed at building the tallest tower ever! Watch this video tutorial to learn how to cheat Tower Blocks on Facebook (08/05/09).

From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

Board up a window for protection against strong storms and hurricanes. Learn how to board up a window.

Do you sometimes wish you were an only child? Yeah, so does your irritating little brother or sister.

Learn how to play "Heal Over" by KT Tunstall on guitar, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Learn how to update your iPhone firmware from 1.1.1 to 1.1.4 using ZiPhone 2.5c with this video tutorial. To get started updating your own Apple iPhone, follow these steps:

Check out this home repair tutorial video that demonstrates how to fix and diagnose your appliance. These videos are for information purposes only. A qualified and proficient engineer should be employed to replace any faulty parts on your domestic appliance.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.
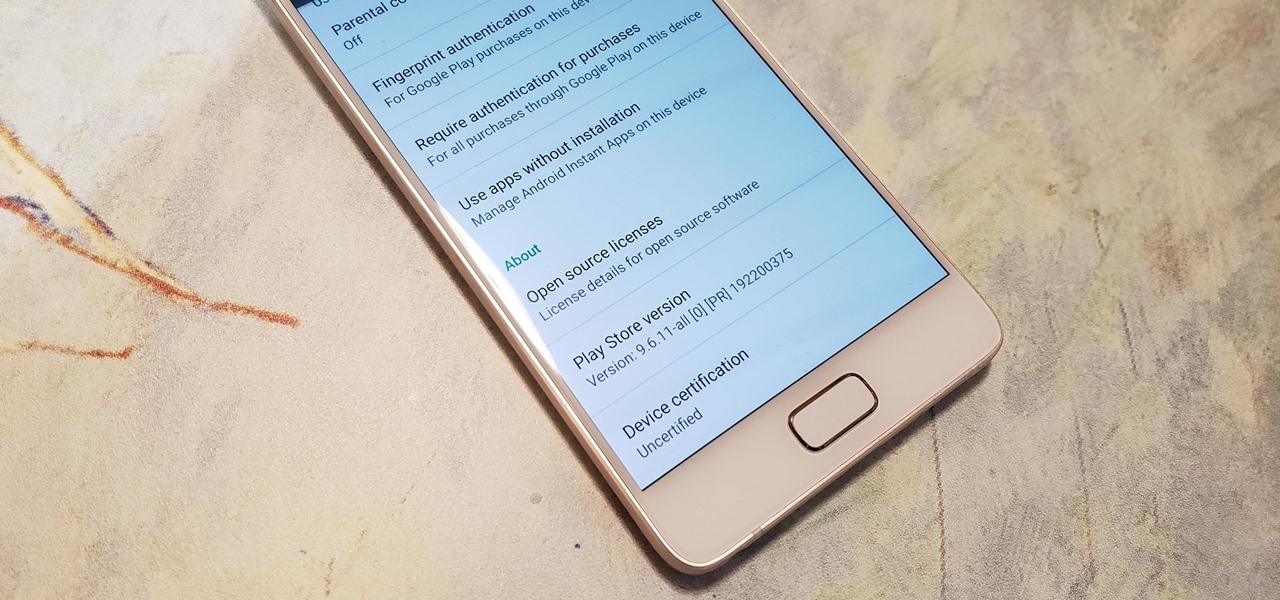
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.
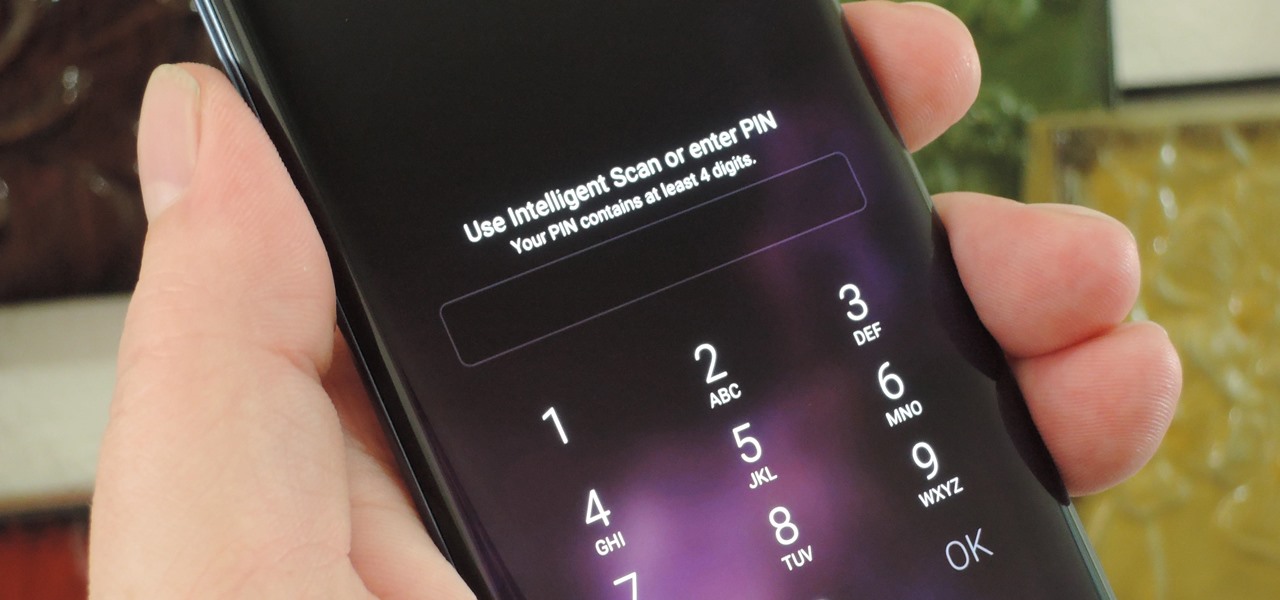
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

A sensory poem is a poem that uses all five senses to describe something. These are common poems for grade school children. They are not difficult to do and only need to choose something to describe and follow the rules.

This is how my version of an origami Christmas tree turned out based on the instructions I posted awhile back. Cory also made a version from white glossy paper, which looks great. I opted for the green and brown look, but it wasn't easy.

Electronics seem to fail on you at the worst moments, don't they? Luckily, if your iPod freezes, there is a quick and easy fix. Check out this video and learn how to reboot your iPod on the spot and solve many issues.

She thinks just because you're related that your closet is her closet; and if she ever gives your things back, they're never washed. If it's time to stop your sister from being a closet bandit, check out this video. This tutorial is full of tips for gettinf rid of that pesky sibling and keeping your clothes all to yourself.

The name of your business will leave an impression on people as this is probably the first information they will receive. Make sure to express yourself and give the impression you intend by choosing the best name for your business.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

The COVID-19 pandemic has created a frenzy for news and information that is nearly unprecedented in the smartphone era, with a major side effect of misinformation. Now, major tech companies are making it easier to ask for advice about novel coronavirus from their respective digital assistants. Results may vary, but Apple and Google are the most useful at the moment.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

Everyone seems to be talking about Elon Musk's new futuristic Tesla Cybertruck, the vehicle that either looks like a cool moon rover or an outlandish video game replica, depending on your tastes.
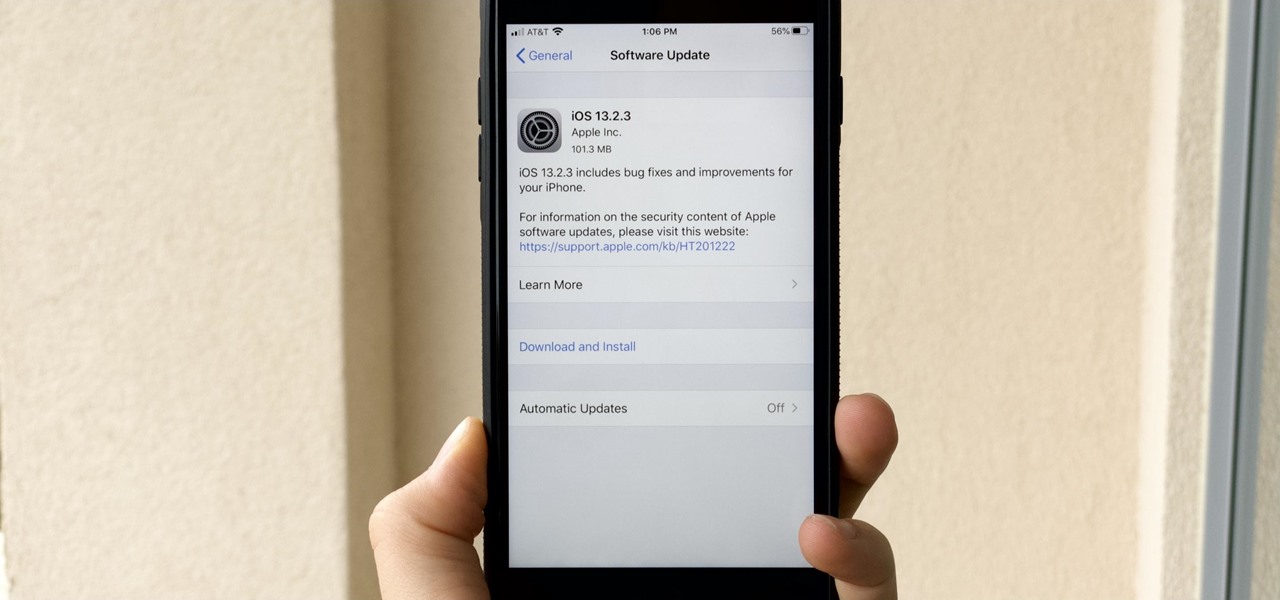
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.
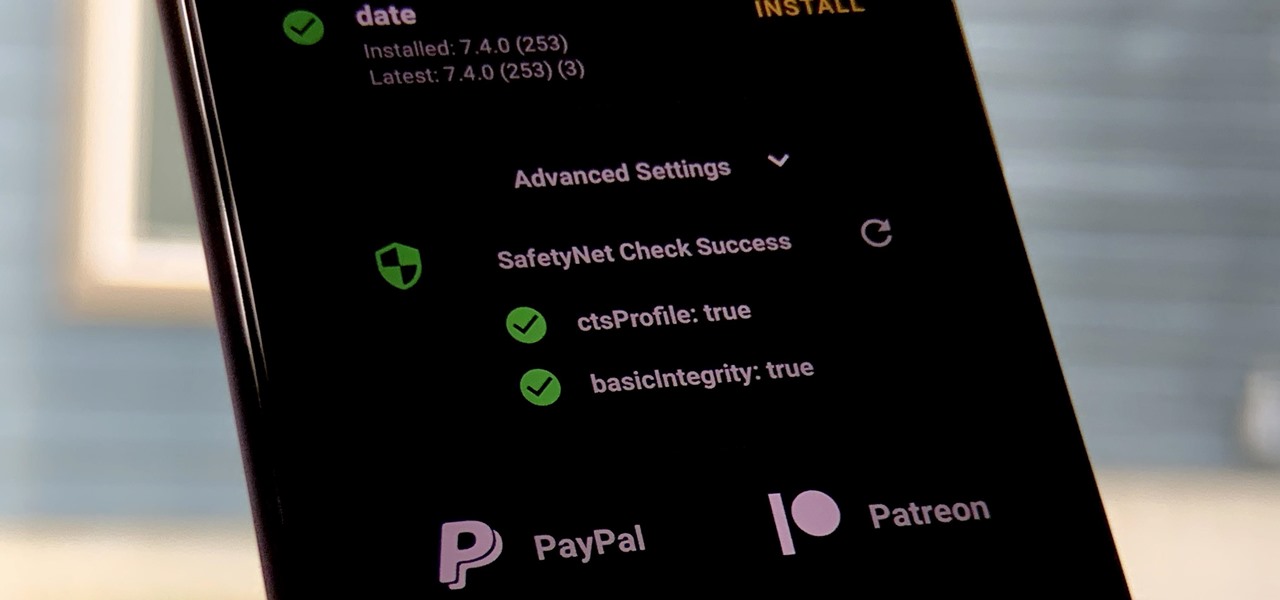
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.