A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

Some types of bacterial infections are notoriously tough to treat — and it's not all due to antibiotic resistance. The bacteria themselves are rugged and hard to penetrate with drugs.
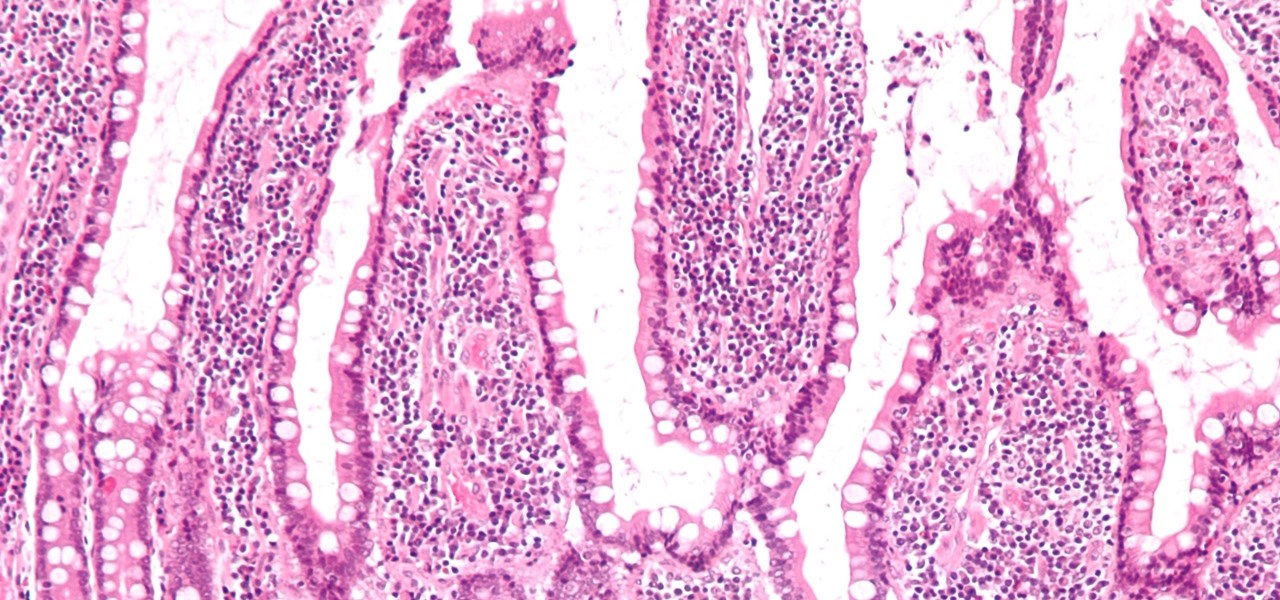
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

Do you know what your smartphone is made of? I've had smartphones for years, but if you asked me that question I'd probably respond with "Wi-Fi." For uninformed consumers like myself, it may shock you to know just how much goes into creating a smartphone.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

Yes, bubonic plague—the Black Death that killed millions in the Middle Ages— is still out there. It even infects and kills people in the United States. Without treatment, half the people infected die, but the Food and Drug Administration approved ciprofloxacin in 2015 to treat plague, and it has just successfully been used to stop the infection in five people.

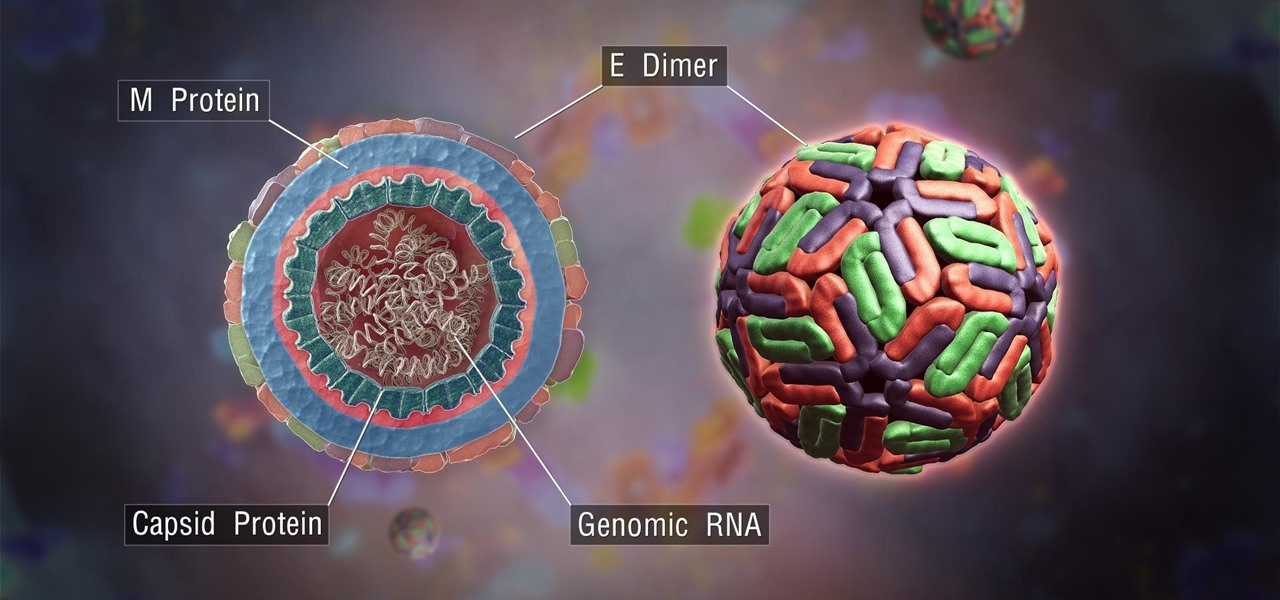
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Now is the time to act if you've been in the market for some must-have Android apps but felt like the price was a little out of your range. The Google Play Store is running a sale so you can pick up some high-quality paid apps—including the popular Nova Launcher Prime and Poweramp Music Player, among many others—for just $0.99 each. While there are quite a few solid apps here you should try—and with a two-hour refund window, why not try them all—here are our favorites you should seriously con...

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

You'll have to forgive me if I sound a little overexcited about this, but in my opinion, Google's "Now on Tap" is one of the most innovative™ smartphone features that I've seen in years. Sure, Microsoft heard about the feature being in the works and rushed out a similar Android app so they could say they were first, but that solution pales in comparison to this one.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

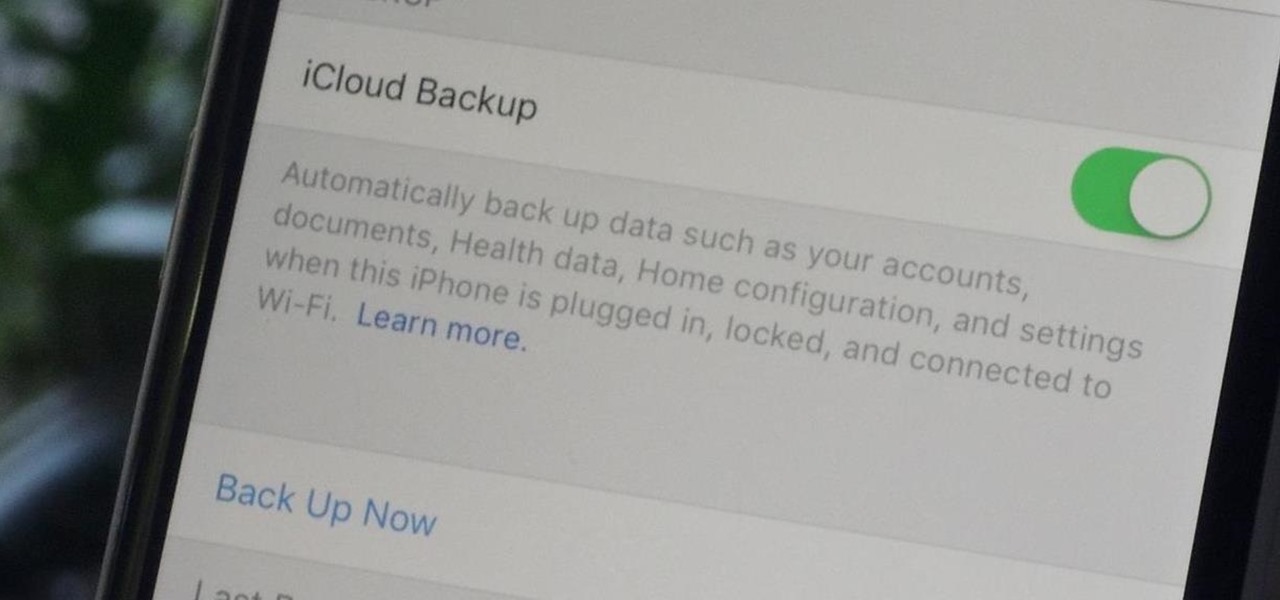
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

There comes a time in relationships when two people decide to move in together, and when this happens, you learn two things:

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Included in Spotify's new darker, slimmed down redesign is a much needed My Music section, which consolidates all of your starred music, local files, and playlists into a personal collection of songs, albums, and artists, similar to how iTunes organizes your music. This makes me wonder...

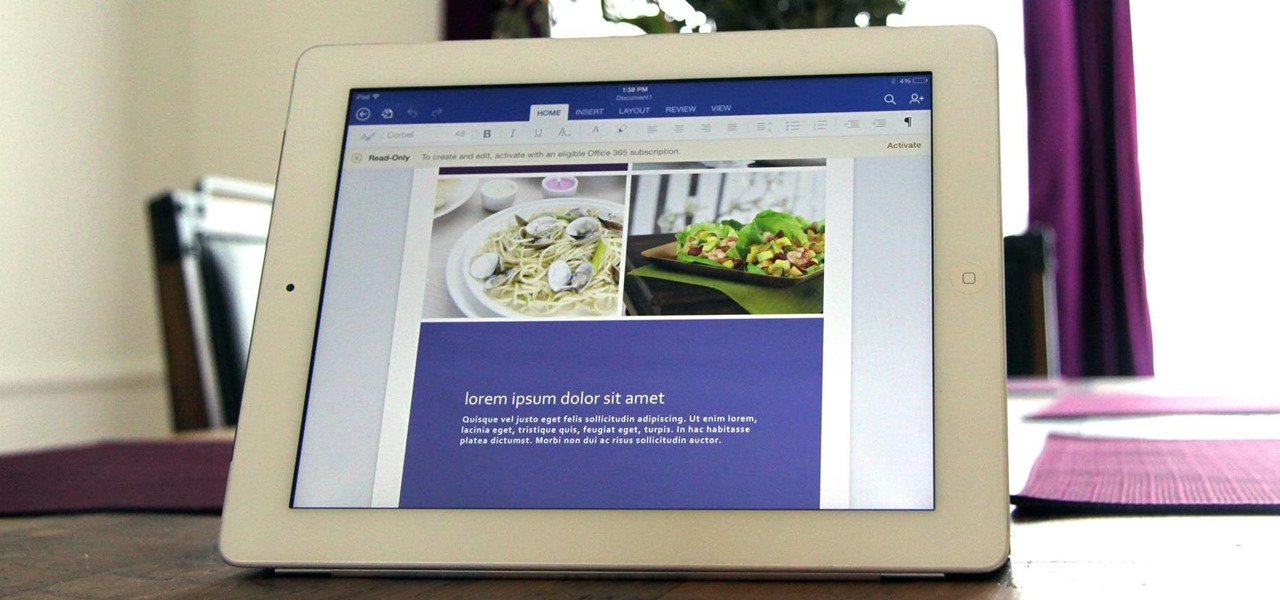
After much speculating, denying, and waiting, Microsoft has finally released their suite of Offices apps dedicated to the iPad. With increased competition and flocks of users going to apps like Quickoffice (which was recently acquired by Google) and Kingsoft Office, it was getting close to do-or-die time for Microsoft.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Now that there's a working jailbreak for every iOS 6.1 device, there are more and more people jailbreaking their iPhones (including me) for better customization. But for those of you who have no desire to jailbreak, you can still do some pretty cool tweaks.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

This may seem like an odd subject, because what do Steampunks and iPhones even have to do with each other? Actually, more than you might think!

A sensory poem is a poem that uses all five senses to describe something. These are common poems for grade school children. They are not difficult to do and only need to choose something to describe and follow the rules.

So now you've completed everything that the Dark Brotherhood quest-line in The Elder Scrolls V: Skyrim has to offer. But now what's left to do? Anything? Well sonny, there is something you could do! After you complete the quest-line, one of your goons will suggest to you that some upgrades are in order for the sanctuary. Doing so will add some really cool bonuses.

In this clip, you'll learn how to add or remove software on a Mac. With a little know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. (In most cases, it's just a matter of dragging and dropping!) For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

Vocal breaks are a serious problem for singers just starting out. For those of you new to singing, Kevin Richards offers some advice on how to avoid vocal breaks.