How To: Capture and save a screenshot in Windows XP
Learn how to capture a screen shot of your desktop, an active window, a website, or anything else use Microsoft Windows XP and without installing additional software.


Learn how to capture a screen shot of your desktop, an active window, a website, or anything else use Microsoft Windows XP and without installing additional software.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Everyone needs a great website. Whether you want to launch the new business you've been dreaming about in 2021, increase your brand's web presence and bring it into the digital realm, or promote yourself and your portfolio, a fully optimized website is the way to do it — and the results can be life-changing.
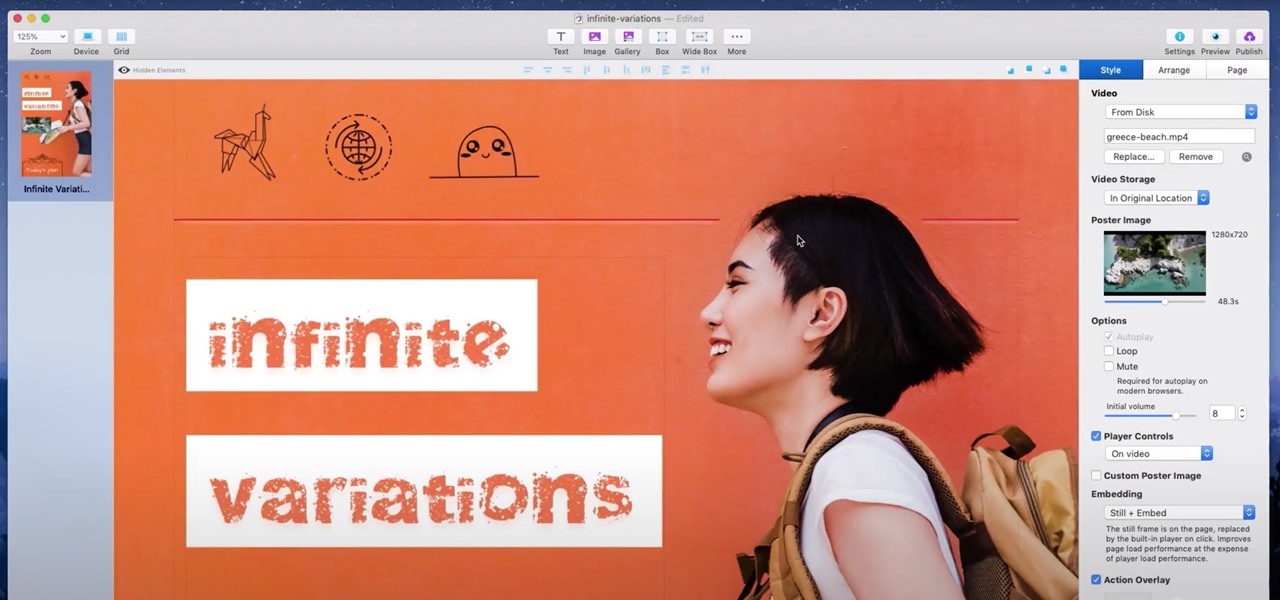
If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.
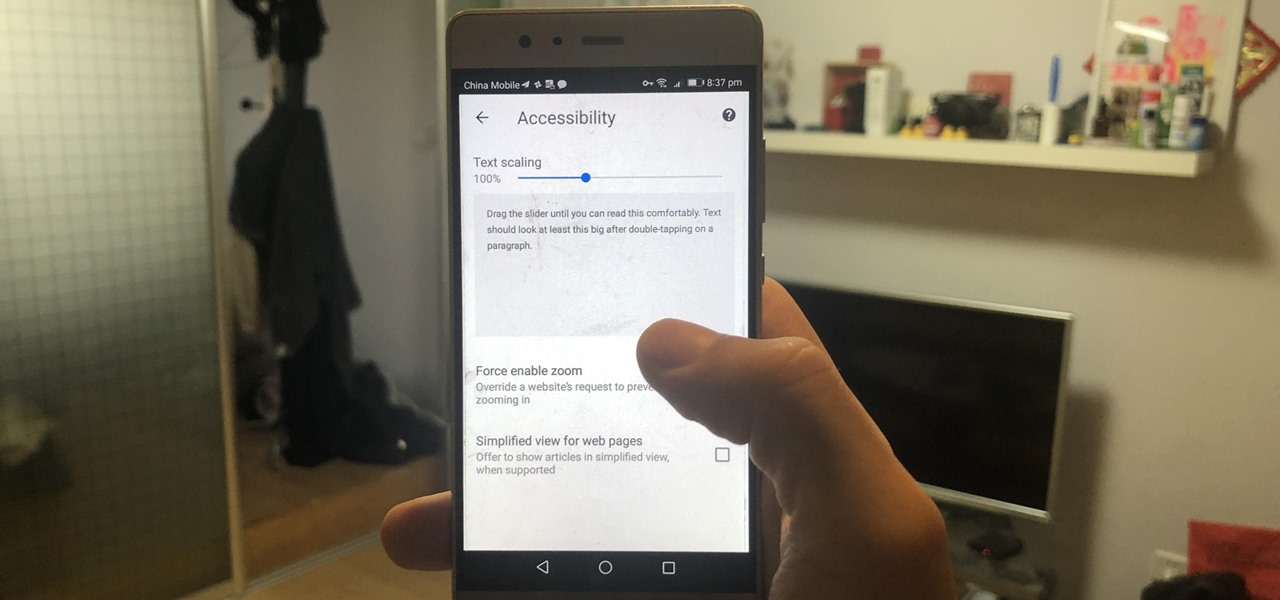
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google Chrome to be perfect for you.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.
One of the headlining features in Samsung's One UI update is a new dark mode that turns stock apps and system menus black. But something you may have missed is what this theme does to the Samsung Internet app and all the websites you visit.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

The creative possibilities are part of what makes Apple's ARKit so exciting. We've seen new camera effects, painting, and new ways to tell stories through ARKit. Now, the app developer studio "Orb" has created an app to let you create scenes with 3D objects of your choosing.

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

As one of the most frequently used Android browsers, making Chrome work faster and more efficiently is something we can surely all appreciate. And just like its computer-based counterpart, there are experimental flags for the mobile app that can speed browsing up significantly.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.
If you want to embed a video on your website and customize the player so it doesn't look like crap, you've come to the right place:
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website.
This HTML Web Design tutorial will explain how to add a Heading tag for your website. The heading tag is very important because it helps search engines to determine what the main topic is on a particular web page within your website. The HTML codes for heading tags range from h1 to h6 with h1 being the most important or in other words the main heading HTML web design tag. Make sure to give the h1 tag the most importance in terms of titles on your web page for headings. Another rule I recommen...
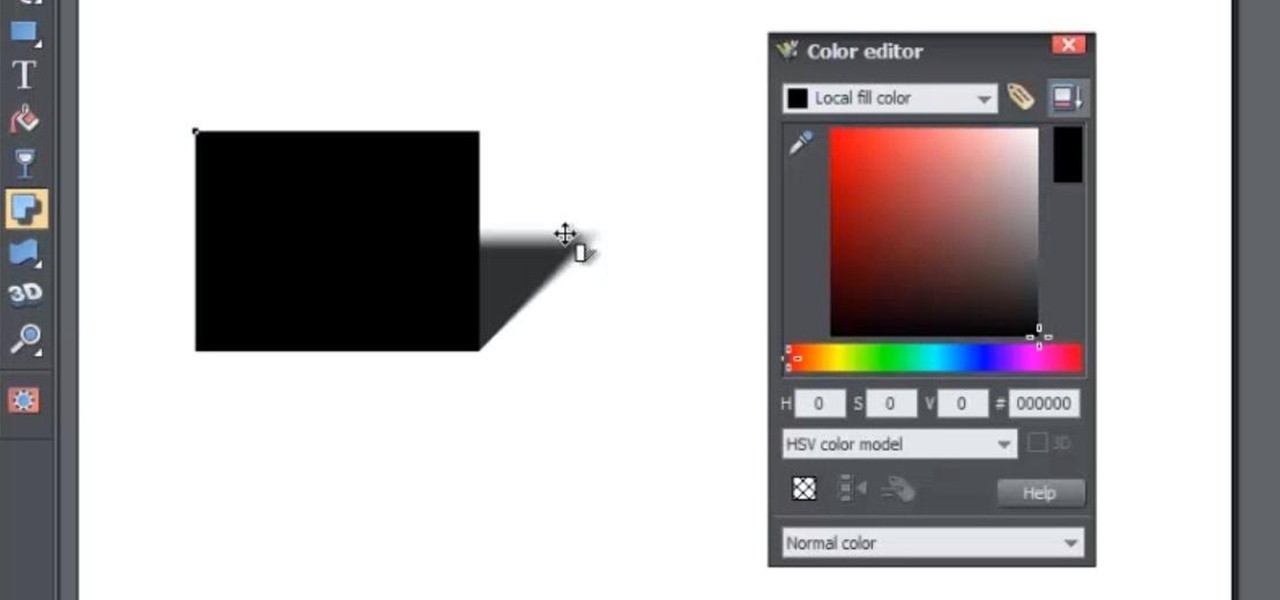
In this web design tutorial, you will learn to use the Xara Shadow Tool. Use the Xara Web Designer shadow tool to add shadow types such as: floor, wall and glow.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.
As an avid Steam user, I'm faced daily with high prices for all of the games I want to download and play. It's gotten to the point where I don't even bother going on Steam altogether because I might end up spending a bunch of money I don't have.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

Online shopping is way more convenient than brick-and-mortar stores in a number of ways, not the least of which are the discounts. But with so many online stores and sites like Amazon which feature thousands of retailers, how can you know you're getting the best deal?

This 3D software modeling tutorial series shows you step by step how to create a suitable model for Google Earth within SketchUp. The series will start by showing you how to export data from Google Earth to use for reference, how to build and optimize the modle, texture it in Photoshop or Picasa and export and load it to Google Earth.
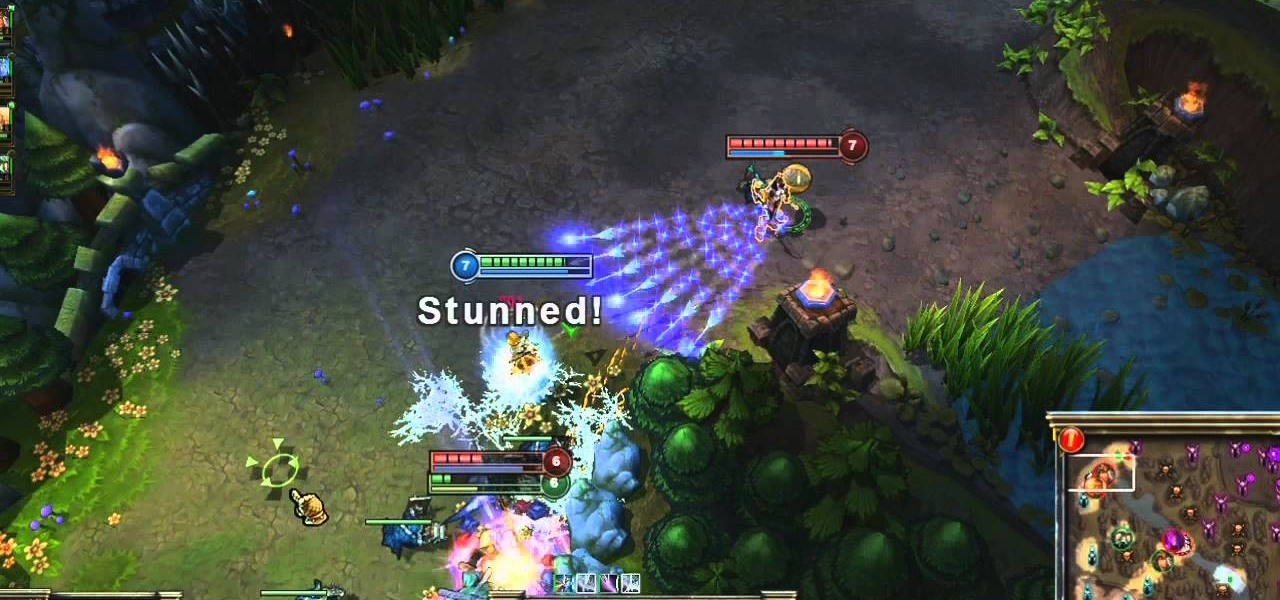
Orianna is a unique champion that focuses her abilities on the use of a ball she carries with her. The ball allows you to pull off some pretty cool tricks, including slowing your opponents in an AOE around it and harassing with it during the laning phase.

The League of Legends champion Kayle, or Judicator, received a rework a while back and now plays slightly differently because of that. Take a look at this champion spotlight guide by Riot Games on how to build Kayle as a hybrid support champion using the right runes and masteries. Be sure to take advantage of her ult so that you can save someone at the right time with invincibility!

Having cool photos as your desktop can make your computer a welcome sight, but having to find a fresh one every so often can get pretty stale fast. Thankfully, freeware utility Flickr Wallpaper Rotator for Windows PC's can import images for your desktop from Flickr automatically at intervals you set. You can even set it to use photos from a Flickr search or show favorites from a specific user.
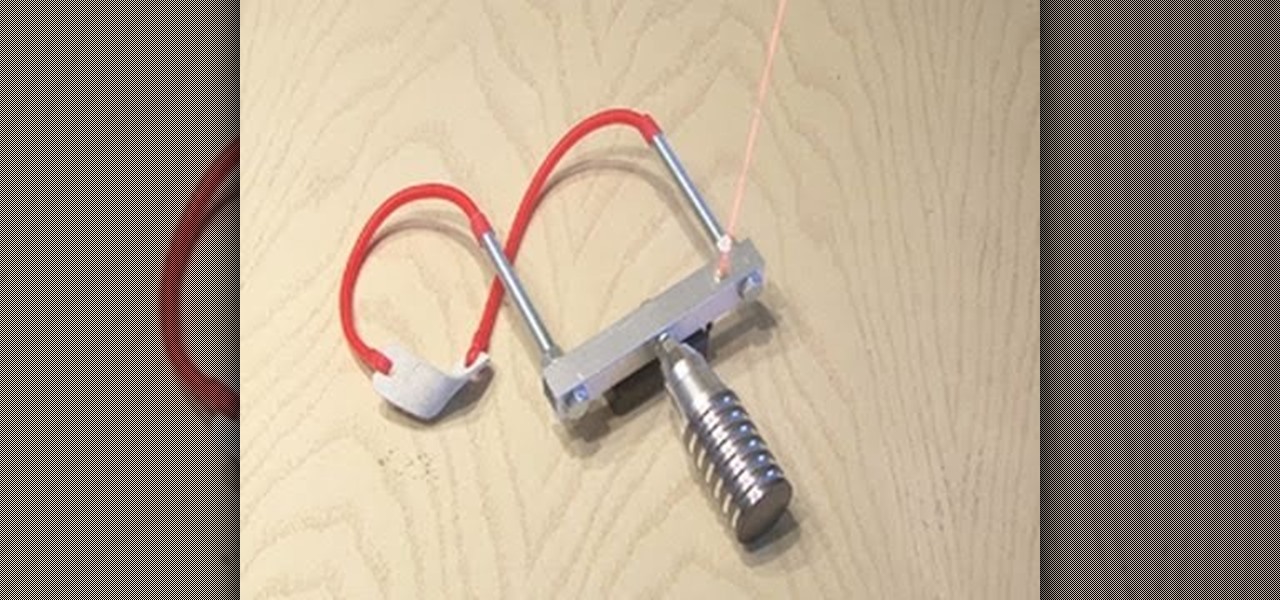
In today's day of mobile devices and improved technology, anything of yesterday can be considered retro— even a freakin' slingshot! Yes, that's right— forget fallen down tree branches. A rubber band and tree limb ain't going to cut it anymore. These days, kids need accuracy, and Kipkay has the knowhow.

FL Studio is one of the biggest names in digital music-making software, and Korg the biggest in physical gear. Unfortunately, FL Studio and the Korg nanoKontrol USB controller don't get along out of the box, and the transport buttons on the Korg won't work with FL Studio. That is, until you perform the steps in this video that will lead to a blessed union of software and hardware.