Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

Learn how to choose the rabbit that's best for children. There’s probably not a kid out there who wouldn’t love a pet bunny, but rabbits and children can be a tough combination. To make the match a happy one, follow these steps.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Here is a quick and easy tutorial on making miniature trees. Watch this instructional model making video to get started with the traditional method using Woodland Scenics and learn some alternatives using found materials like wire and scouring pads. They look great and are perfect for dioramas, doll houses, and model railroads.

Peerguardian2: Block the RIAA and Malicious IPs +Mac/Win. Doesn't block http traffic though, and it's not very accurate and won't make a difference.

UUNICEF Youth Adviser Joel takes lessons in Patois (the Jamaican language) from a young man. The language lesson includes how to say "hello, how are you?" "that girl is good-looking" and "see you later".

Learn how to watch flash videos from websites other than YouTube on your iPhone. Using a free download from videohamster.com

n this video you will see how to use content versioning for your site with Drupal.

Set to some background music this video shows you how to make a stork. Instructions also available in Spanish on website.

This video will show you how to use the Windows command prompt and ip-address.com to find the location of any website. This is a PC based trick and will not work with a MAC OS.

Rum is no ordinary liquor. If you have a yearning for some rum, you need to know the basics of rum culture, like what rum is (and isn't), what kind of rums are available, and how is rum made. Once you know this information, you'll be a rum master. Rum is available in a wide variety of weights, ages, and blends. If you aspire to become a connoisseur of fine rums, start with the basics.

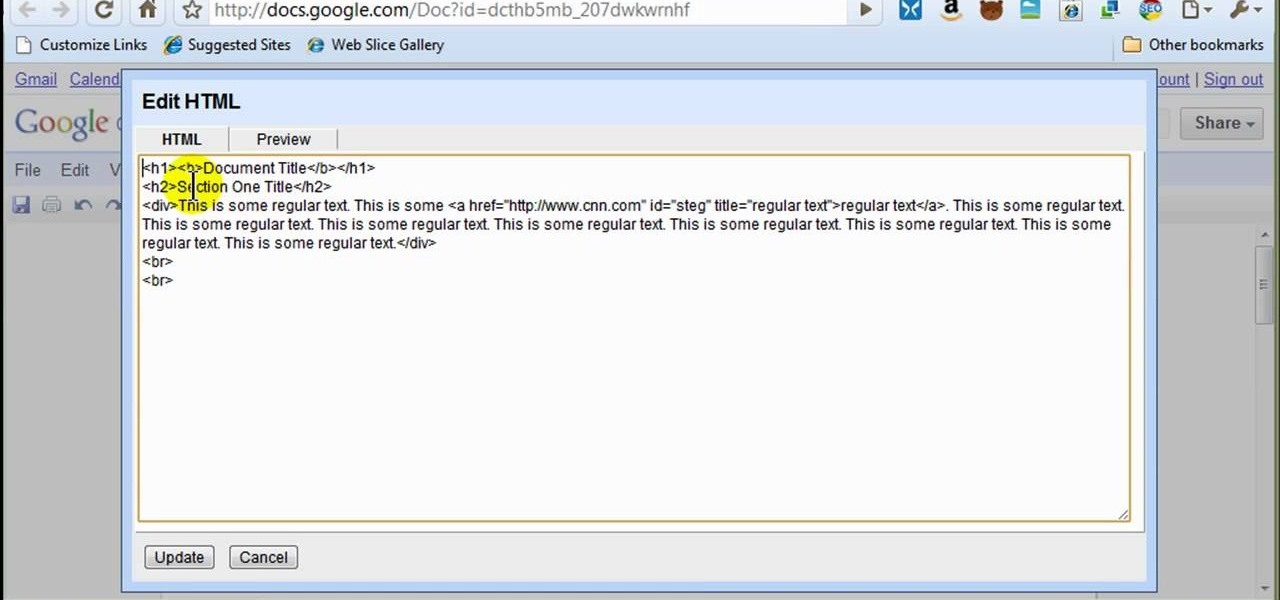
In this how to video, you will learn how to style documents with the Google Docs CSS editor. First, create a new document in Google Docs. First, click on the drop down menu for style. Type in a title in the document. Select heading 2 in the menu and type in the section title. Next, take off the style and type in the body for the content. Select some of the body text and click the hyperlink button. Type in the address and click okay. Now you can click this text to go to a website. Go to file a...

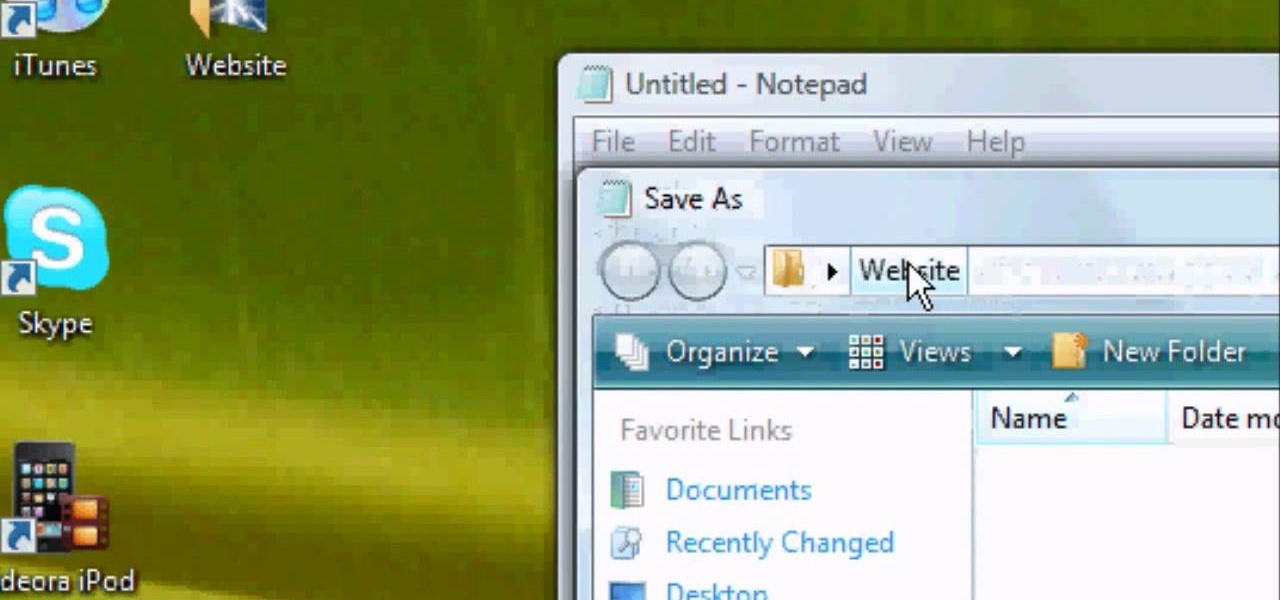
First of all you have to open the 'notepad'. Now you have to type in "<html>" in first line. Write "<head> in second line. Write "<title>this website contains text wrapped around images</title>". In the fourth line you have to type '<body bgcolor="#999999">'. This shall add a light orange color. Now find out the name of the image. Here the name of the file is 'image.png'. Then in the next line you have to type in "<img src="image.png">this text should hopefully wrap around the outside of the ...

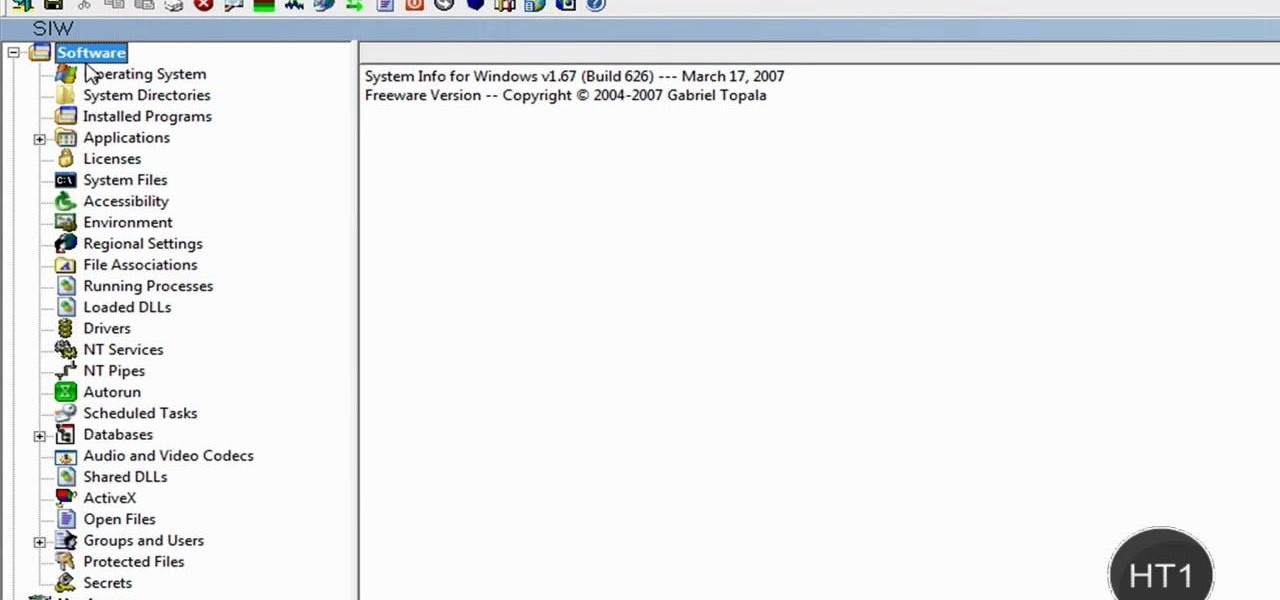
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

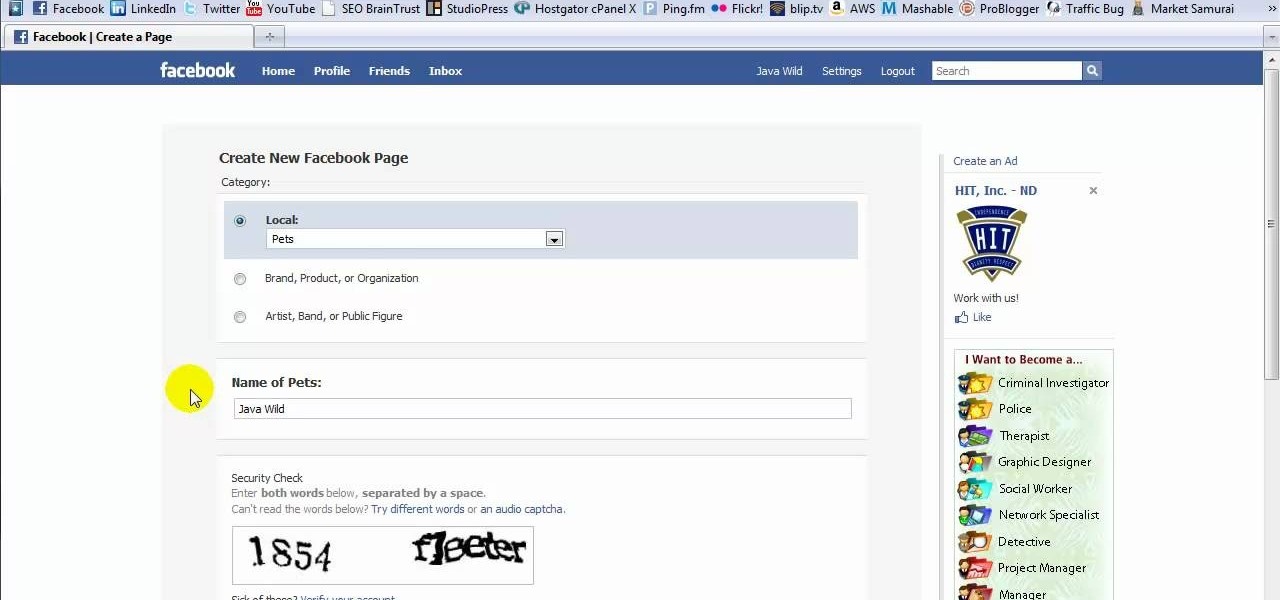
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

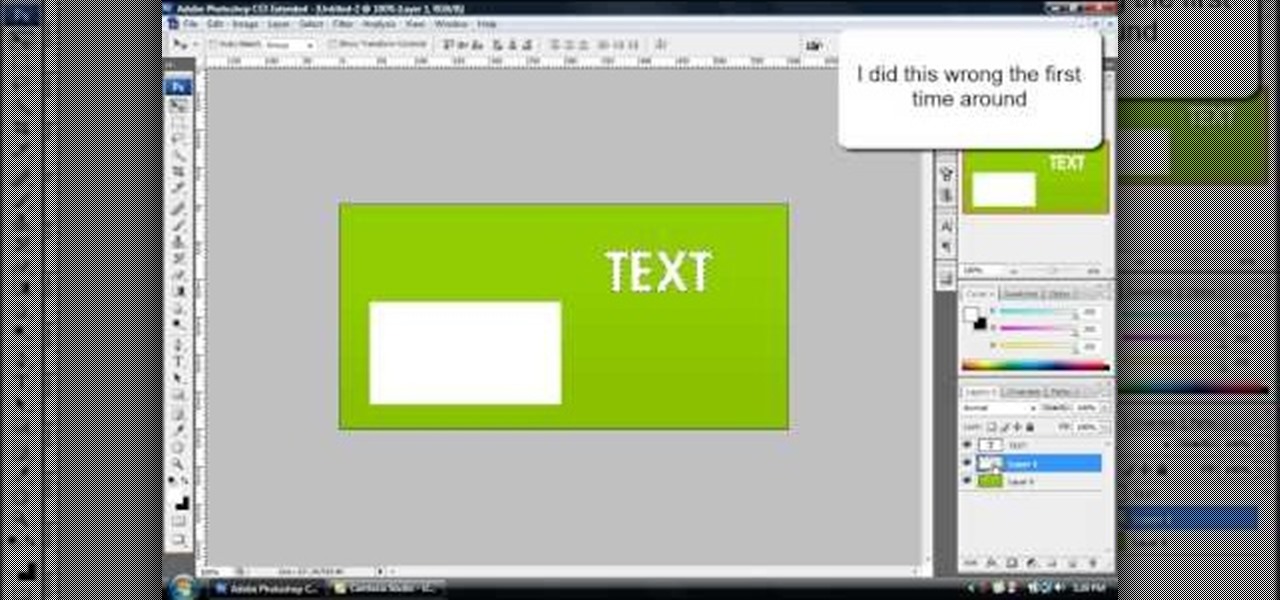
Melvin from QZPStudios takes you on a quick tutorial in which he creates an embedded text effect in Photoshop. This could be a useful trick for website designers who want to create banners containing text which have a shadow effect.

If you are going to travel outside the United States on a ski trip with Skitravel.com, you will need a passport. From Skitravel's website you can click the "get a passport" link. The link will take you to the US Department of State's passport form (the DS11 passport form). On the Department of State's form, you have two choices, a passport book or a passport card. The passport book is good for ten years and you can travel anywhere in the world with it. The second choice is the passport card. ...

Testing products for a living is a bit more complicated than it sounds. You Will Need

Hook-billed birds are the ones in the parrot family—from petite parakeets to massive macaws. Here’s some stuff you should know if there’s going to be a hookbill in the house.

Why waste your vacation dollars on pricey hotel rooms when there are cheaper – and sometimes free – alternatives? Watch this video to learn how to find cheap (or free) places to crash on vacation.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

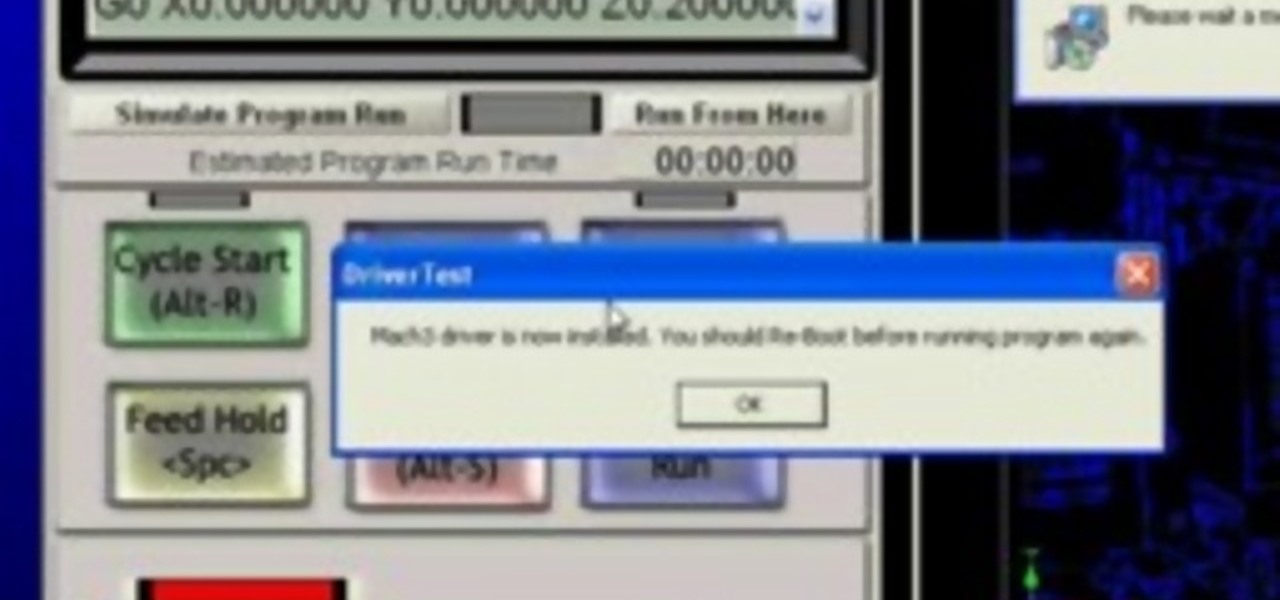
A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Learn how to use a site: http://www.copyscape.com to check if people are stealing content from your website.

You can learn how to drive traffic to your website using links. The most important thing is to get people to your website. You can not spend hours and hours writing emails to people who steal your articles.