Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

Sometimes it's hard to remember that lasagna, pizza, cannoli, and other dishes are actually Italian in origin; they're so much a part of the American culinary landscape at this point. Wherever they come from, Americans of all kinds love to eat 'em. This guy was released from a North Korean prison, and after two years, the first thing he wanted to eat was fast-food pizza.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Pumpkin carving and decorating is a favorite October pastime. After you've carved an amazing design or face into a pumpkin or two, you want to show it off through your window or set it out on your porch for the neighbors to see.

The origins of vodka are shrouded in mystery, with both Russia and Poland laying claim to its invention. Some say Genovese merchants brought vodka (then known as aqua vitae, or the water of life) in the late fourteenth century to Russia. For many years, vodka wasn't just an alcoholic beverage: it was also consumed as medicine.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

There are quite a few flaws with Apple's mobile products, and one that drives me crazy is their reliance upon iTunes for all your music syncing needs. If you want a song on your iPhone, you pretty much have to use iTunes to get it on there. Either that or buy it directly from the iTunes app on your device.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Double Charge" move.

Thanks to the PlayStation 3 and Xbox 360, video games are constantly evolving to higher degrees of sophistication, with complex graphics, lifelike resemblances and storylines that create exciting experiences that relieve the tediousness of our everyday lives.

AdSense. It's a beautiful thing, isn't it? Google AdSense is something every website owner or blogger should use… it's what every blog needs… if you plan on making any money and surviving. So, how much traffic do you need to actually start making money via AdSense? This video will try and answer that question for you. You must have targeted traffic to drive your blog.

Kongregate is a site that allows users to upload games. Users must go to the site to download the hack. On the site, select Kongregate. Then select the first topic and click on KBH 2.0.14. Once downloaded, you can extract the files onto your desktop. Open up the file and follow the video on how to use it. It also comes with the auto rater. This video will benefit those viewers who play games on the Kongrgate website and would like to earn badges.

Moonwalk on Club Penguin! In order to moonwalk like Michael Jackson with your penguin, you need to have Penguin Storm 10. So make sure you download it first before you start penguin dancing.

Get tons of coins for Club Penguin. Don't be the only one not cheating your way to the top. It's easy to do and you get tons of coins!

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to hack Club Penguin: money cheat (09/29/09). Download Penguin Storm 8.

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to get a member puffle on Club Penguin when you're a non-member (09/28/09).

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to cheat Club Penguin: padlock pin hack (09/25/09).

Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Devil's Spin Reverse 12 23 34" move.

Apple has a new way to tidy up your favorite bookmarks in Safari, making them easier to access than ever before. This new feature saves space, allowing you to quickly see more of your favorites at the same time.

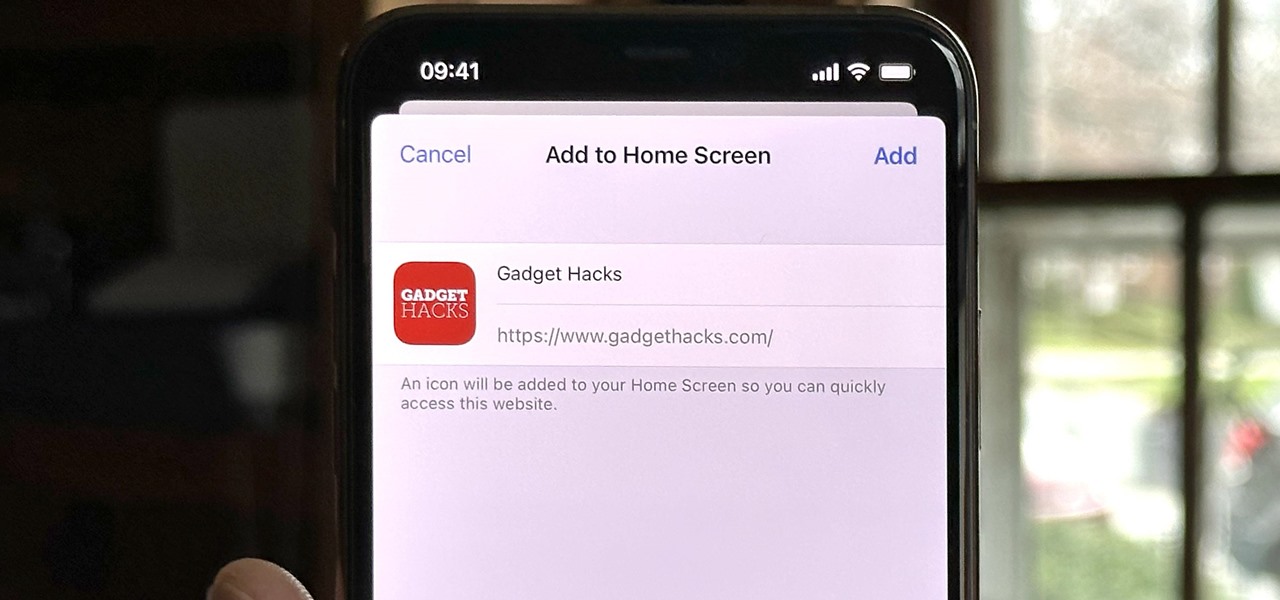
Safari isn't the only web browser on your iPhone or iPad that will let you add icons to your Home Screen for progressive web apps and website bookmarks. Apple gave developers the key to its "Add to Home Screen" feature, and your favorite iOS or iPadOS web browser may already support it.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.

To the end user, mobile apps are sometimes expensive. To the developers, those costs are justified for all the hard work put into making the apps. Sometimes app creators will meet in the middle by putting their apps on sale or giving them away for a limited time to gain more traction in the App Store.

Wordle has been popping up all over in the app stores, but none of them are the real Wordle. The popular word game app has amassed two million users since its launch in November 2021 but has no plans to hit the iOS App Store or Play Store any time soon — but you can still install the official Wordle app on the Home screen of your iPhone or Android phone.