Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...
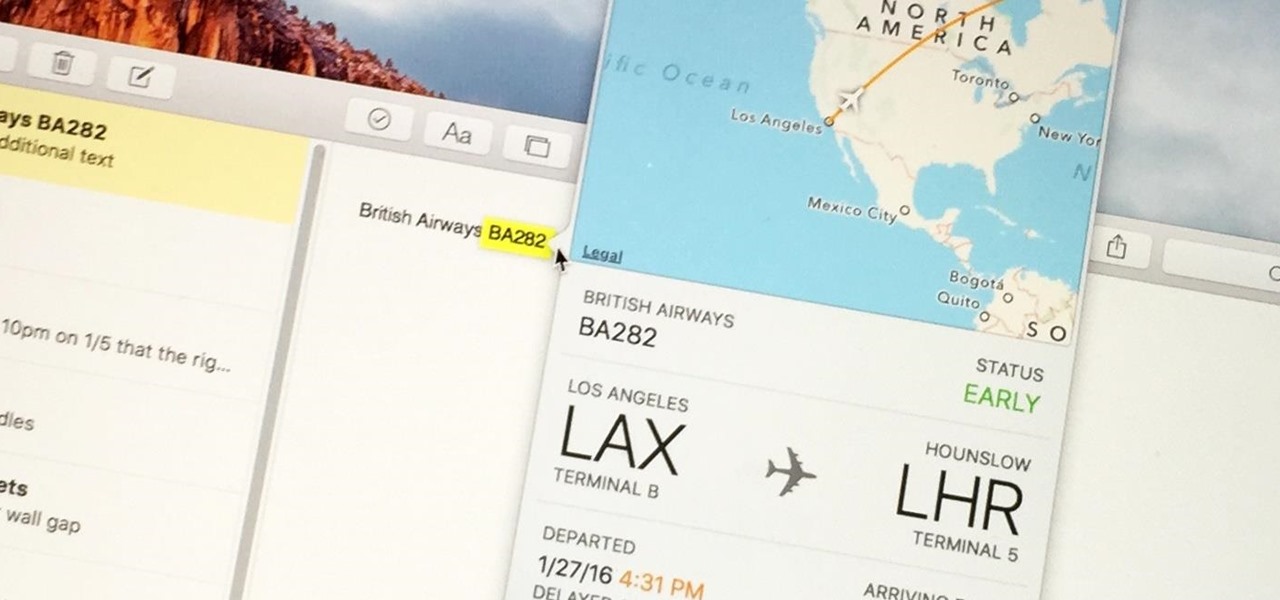
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.
Hello there Nullbytes, In my previous tutorial found here,

Hello there Nullbyte users! This will be my first article here.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

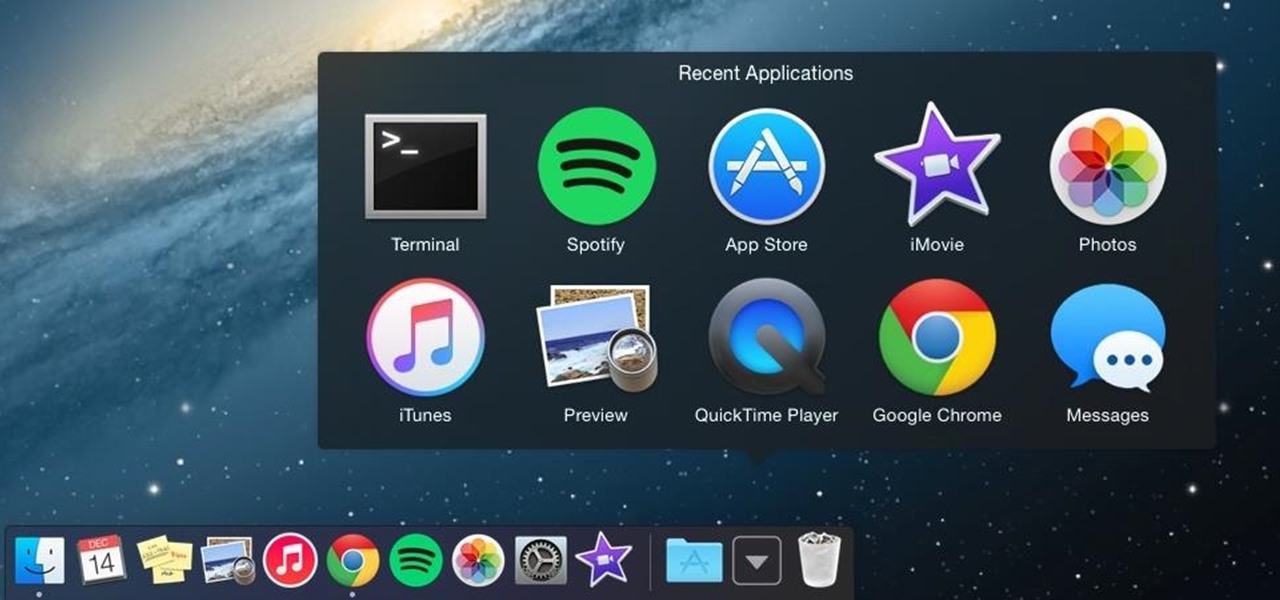
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Starting a few months back, you might have noticed that some text messages you received from certain friends or family members had blank or missing characters. This was because Apple included all of the new Unicode 8.0 emojis in an update to their iPhones, but Android devices didn't have some of these just yet, so they weren't capable of displaying them.

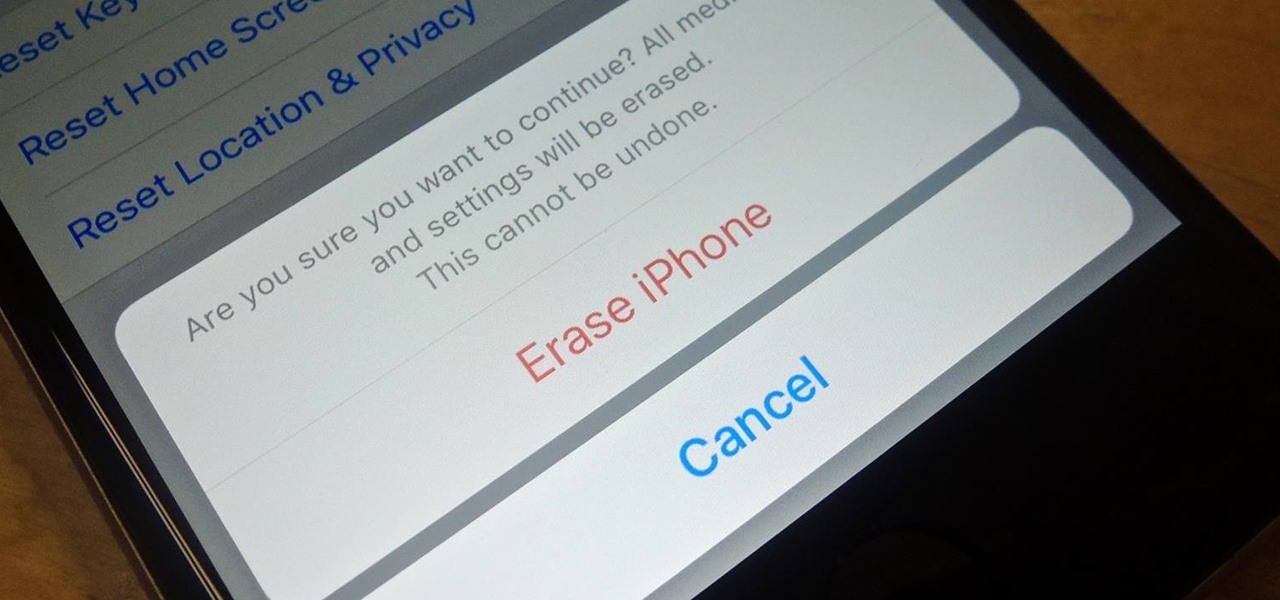
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Hello again, ***UPDATE: Adding links to the other Two articles****

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

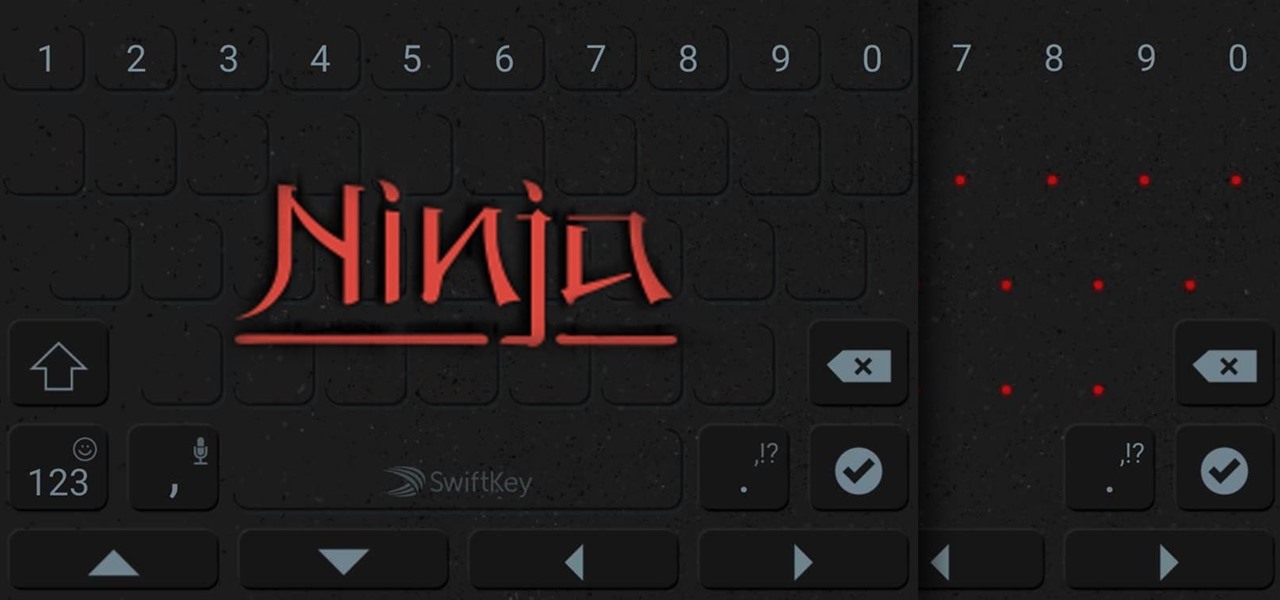
Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

Yes, there's already a way to jailbreak iOS 9 on your iPad, iPhone, or iPod touch, but given the fact that it's only been out for about a week means that not all developers have had a chance to make their tweaks fully compatible yet. That doesn't mean they won't work, but that they might not be as smooth as they should be.

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

If you want to watch a movie on Netflix with a friend, family member, or significant other, but can't meet up in the same living room, the next best thing is doing it remotely from the comfort of your own homes.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

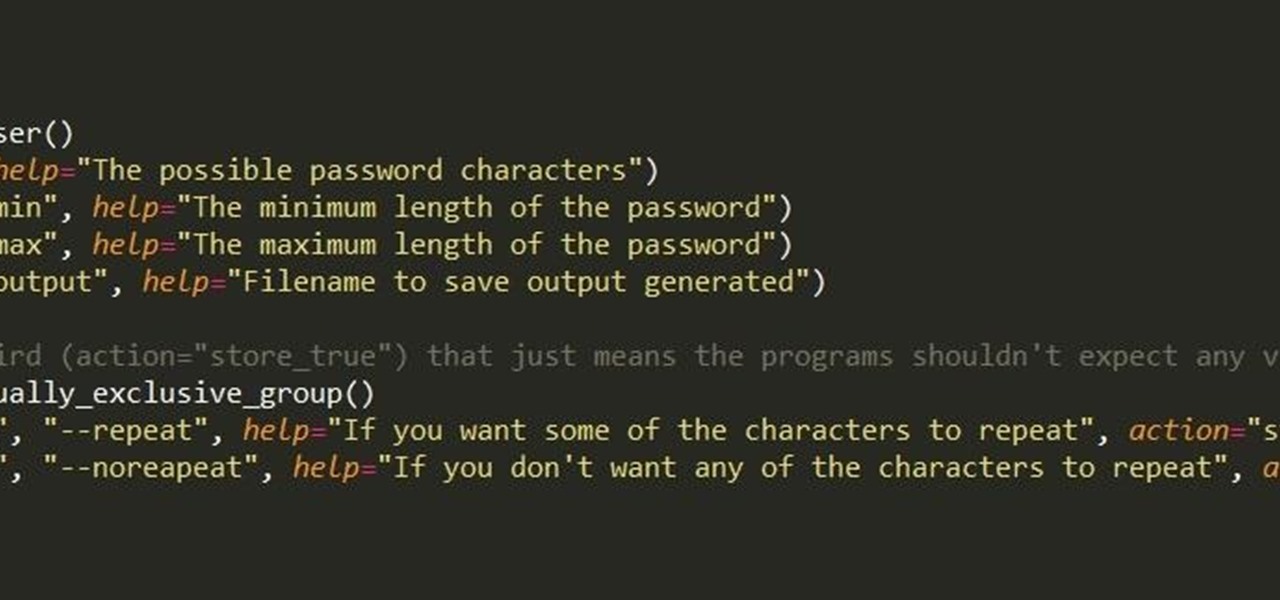
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Well, this is my first article so if it sucks tell me...lol!! Story Time

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

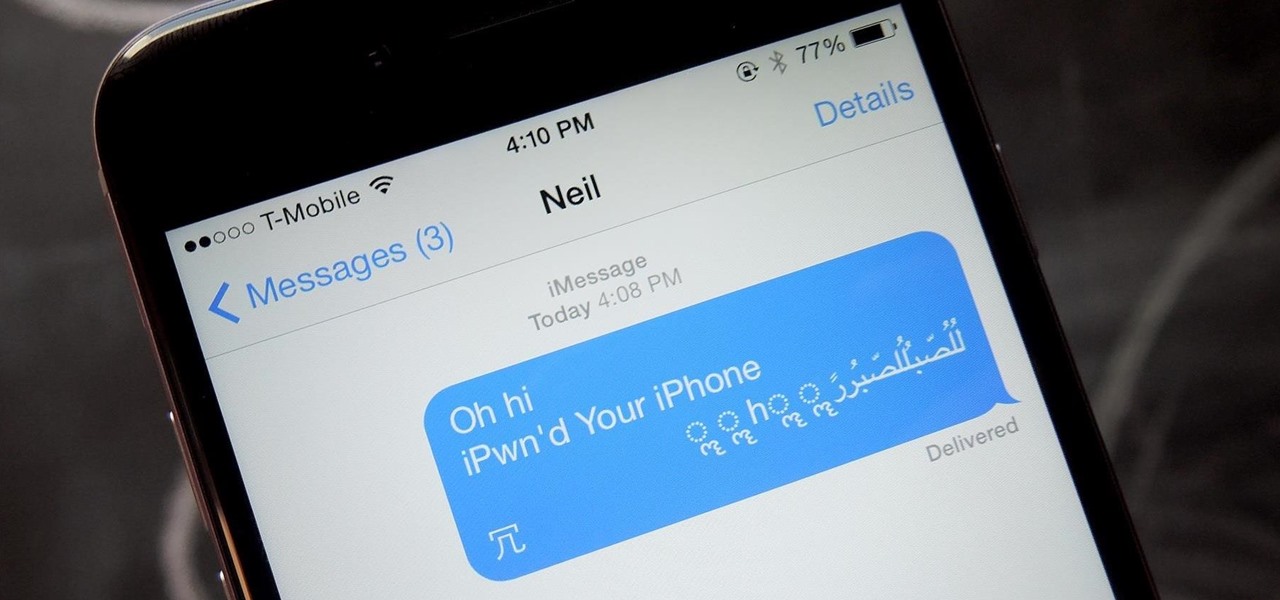
Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.

It's hard to not to like the look of iOS emojis. Sure, Samsung and other Android phones have emojis, but they're all kind of goofy-looking. And since iPhone emojis continue to be viewed as the standard, it comes as no surprise that you can actually get them on Android—and without root!

No one is perfect, and this goes double for software developers. All of the quality assurance testing in the world does nothing when you put a new OS in the hands of everyday users, since we all use our devices in different places and for different reasons. Recently, Cyanogen released their version of Android Lollipop, Cyanogen OS 12, and with it came a whole lot of great features, but some bugs also slipped in.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.