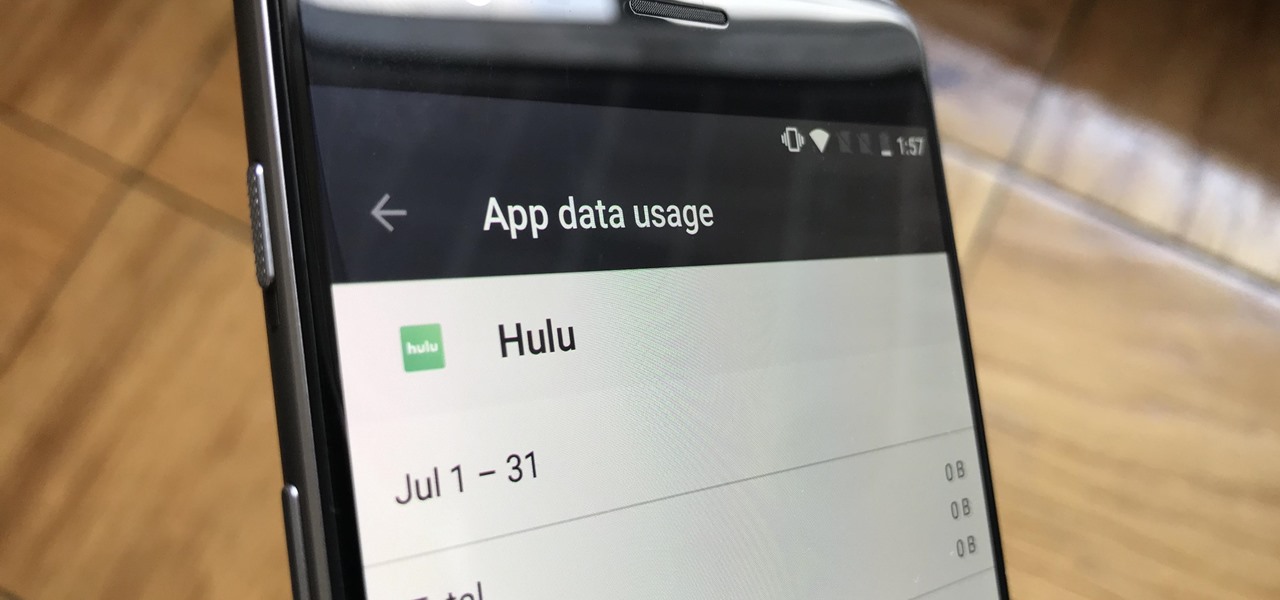
Thanks to their partnership with Tidal, over 30 million Sprint customers can access Hi-Fi audio on the go. And the Jay-Z-owned music service isn't limited to just Sprint customers — for $19.99/month, anyone can listen to lossless audio from their favorite artists. But streaming uncompressed audio files uses a lot more data than standard quality, so how do you use Tidal without hitting your data cap?
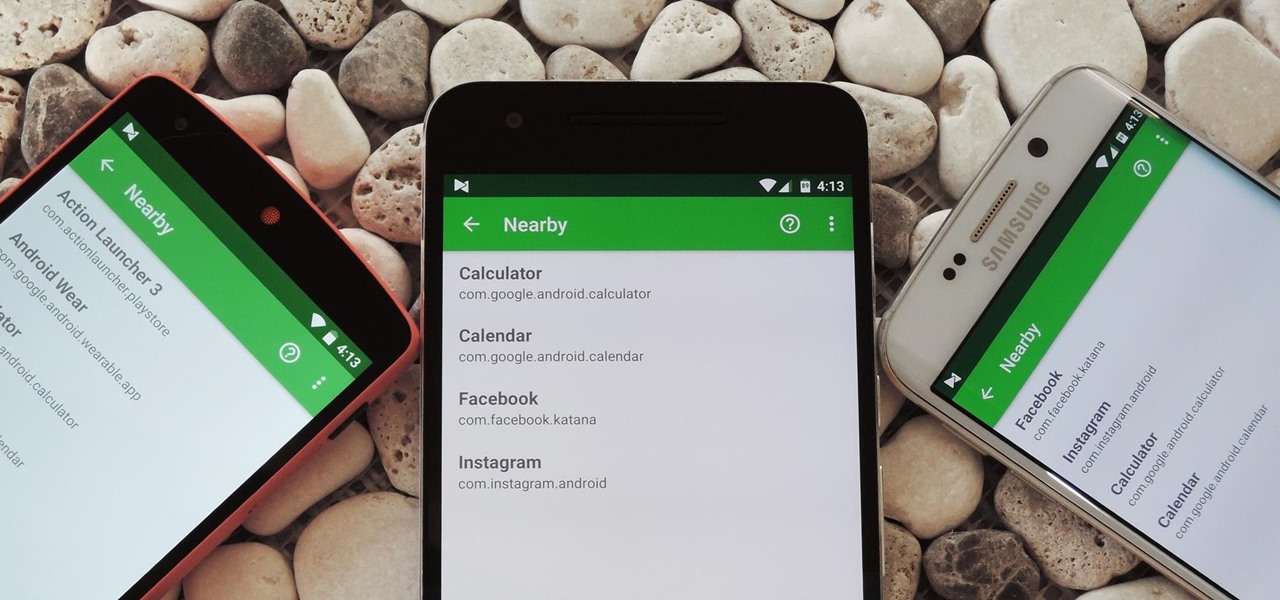
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.
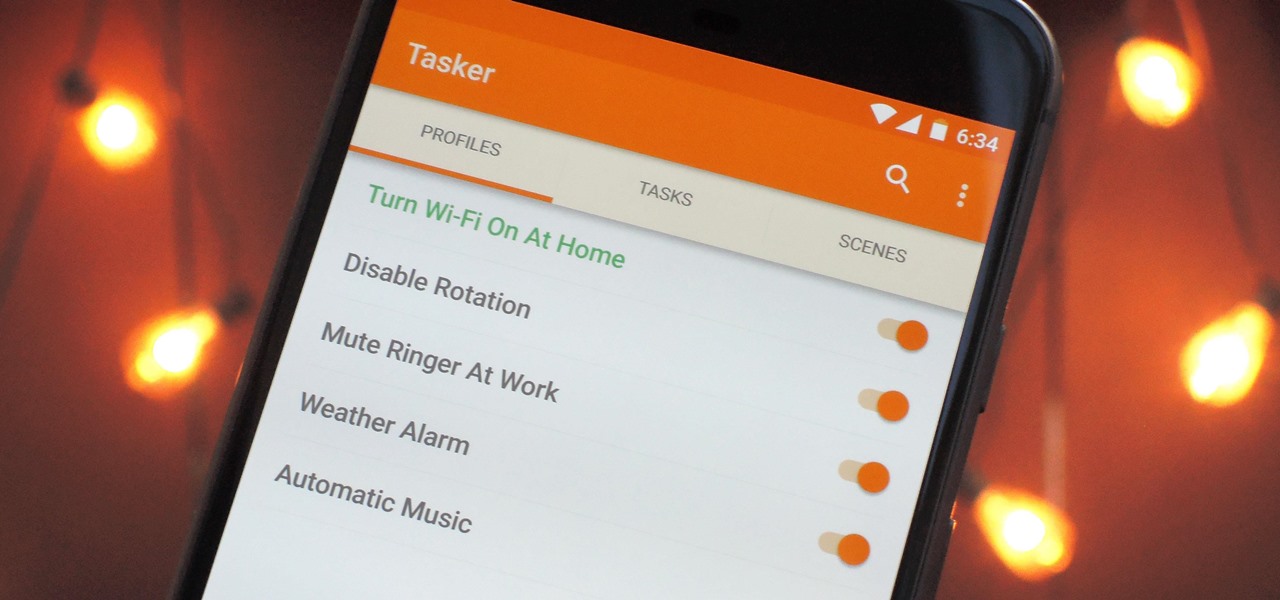
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.
The scrolling, synopsis-giving titles of the sci-fi epic Star Wars might be the most famous set of titles in the history of cinema. All most people need to see is deep space and yellow letters to immediately think of Star Wars. This video will teach you how to make similar titles for your own films using Adobe Premiere Pro. This is MUCH easier than what the Star Wars staff did to make the original titles, so fire up your computer and make your own!

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

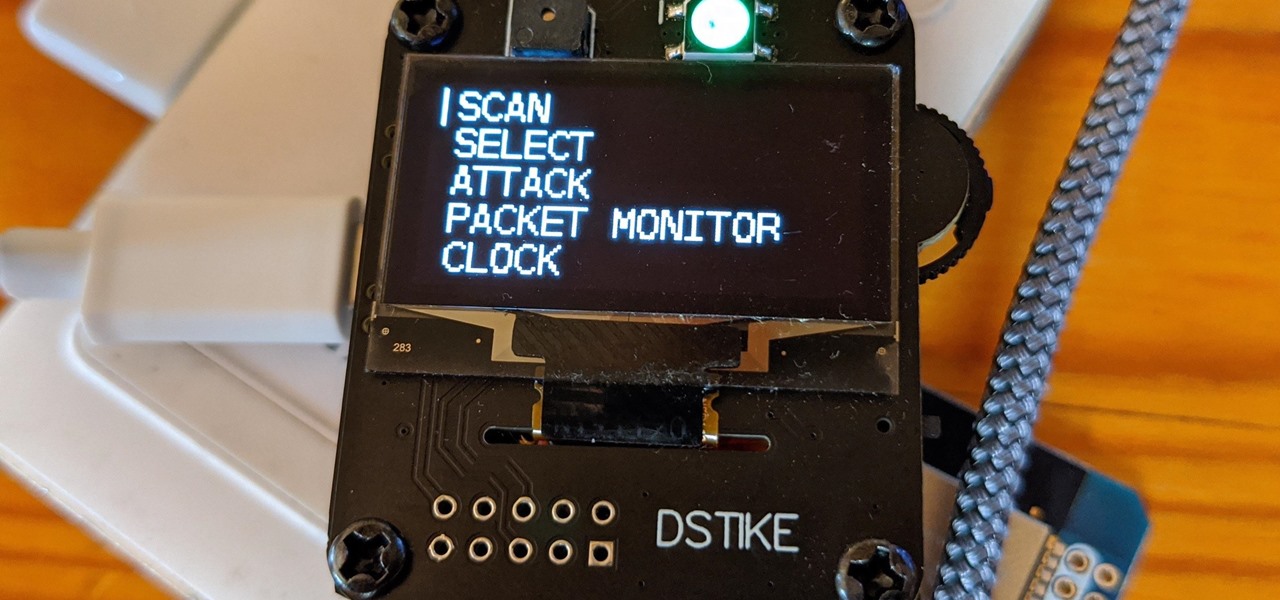
When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Vampire voltage may sound like the next Sci-Fi channel original movie, but it's not. It's something that lives in your very home and can be affecting your energy bill even as you read this. Basically vampire voltage is an appliance that is using electricty although it's not being used. Computers, microwaves, blu-ray disk players, etc are examples of vampires.

The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.

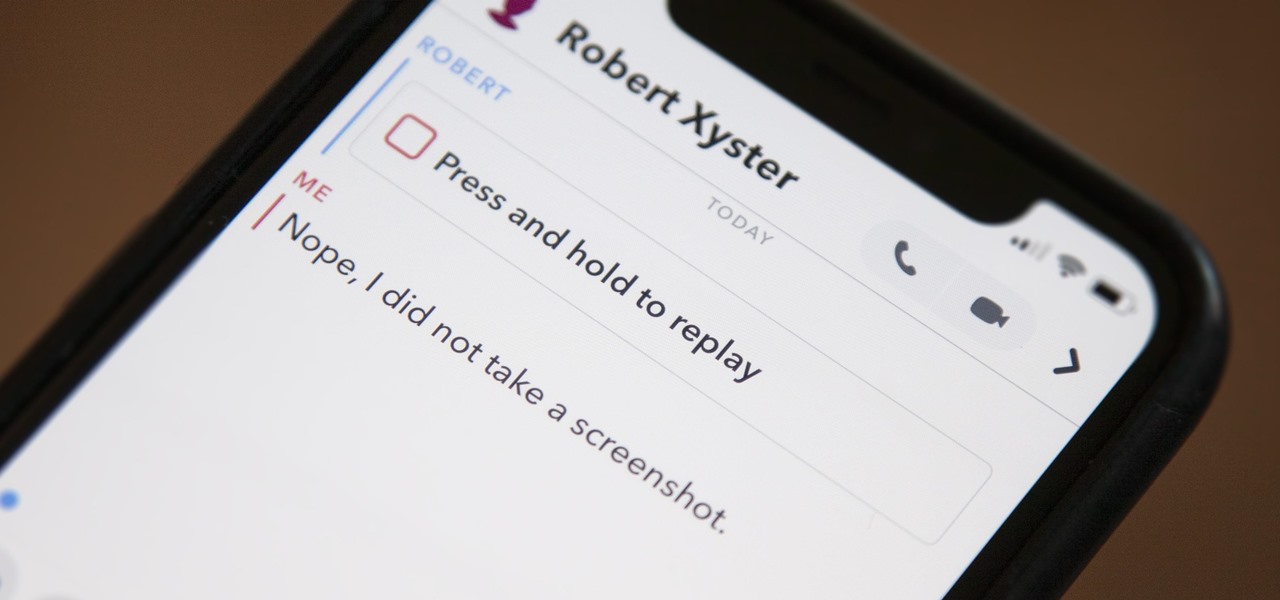
Snapchat doesn't prevent you from taking screenshots of snaps received, but the other user will get an alert either as a prominent push notification or a subtle note in the app. Snapchat has improved its screenshot detection abilities over the years, so it's much harder to circumvent its technology for truly undetected screenshots — but not impossible.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Now that iOS 11 is official, everyone can enjoy all of the great new features available, but there are certainly a few bad seeds in there that you'll probably find annoying. Luckily, a lot of these disagreeable quirks can be changed for the better.

It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.

A groundbreaking new Android feature called seamless updates was announced at Google I/O 2016. No longer would we have to wait for updates to download and install — instead, they'd be applied silently in the background, and the new Android version would be waiting on us the next time we restarted our phones.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

Oops... did you forget to connect to a Wi-Fi network before streaming HBO GO on your iPhone? While those episodes of The Wire may have been absolutely life-changing, your three-digit cellular bill is definitely going to hit you a little harder.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

You've managed to get your Motorola Droid X rooted, so now what? What's one of the first things you could install on your Droid X? What's the most valuable items you need on your cell phone? Everybody knows the answer… wireless tether, a way to suck the internet from your Droid X to your laptop or home computer. Well, this video tutorial will show you how to get the free Wi-Fi tether mobile hotspot app, called Wireless Tether, on your Droid X from Verizon Wireless. You don't have to pay tons ...

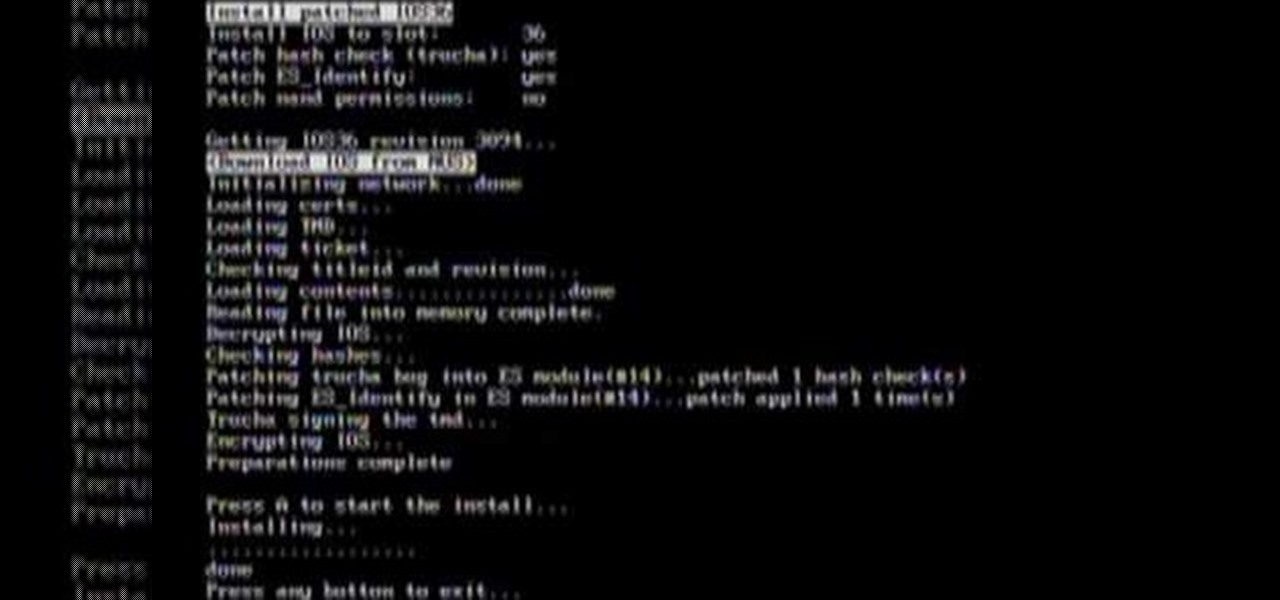
Trucha Bug Restorer is a powerful piece of homebrew software that you can use on your Wii to make sure that it is formatted properly in order to play burned games and use other hacks. This video will show you how to use it to set up an installation of cIOS on your Wii, which is the program that allows you to play burned backup copies of games.

Since it's introduction, iPhone has become the standard for design and ease of use, redefining what's possible on a mobile phone. And now with iPhone 3G, this revolutionary device gets even better, offering even more advanced capabilities. iPhone 3G works with fast 3G cellular and wi-fi networks around the world to keep you connected wherever you go. With its integrated GPS technology iPhone 3G makes it even easier to find where you are and where you're going. iPhone 2.0 software includes sup...

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Video chatting has become an important factor in the overall smartphone experience. Even just a few years ago, 37% of teens were making video calls on a regular basis, and that number has surely grown. 85% of households with infants have used video chat apps to call relatives in other cities, and it's been shown that toddlers can create bonds and learn from visual cues in video calls.

Whether you just got a brand new laptop or you've had an old notebook for several years, it's in your best interest to maximize your laptop battery life so you get the most out of your computer.

Julian Oliver created the Transparency Grenade in January 2012 for the Studio Weise7 exhibition at Labor 8. It's a transparent device with a "payload" built from an ARM Chip, an Arduino Nano, a mic, and a strong Wi-Fi antenna. It taps into wireless networks and logs emails, webpages, images, and voice to a publicly available online map showing its "detonation" location. Apparently, development for an Android version (sans the pretty plastic shell) is under way thanks to interested donors. See...

The iPhone and iPod touch are nearly identical devices, especially now that Apple has added a front-facing camera to the iPod touch. All that's missing is the phone part. With the help of Lifehacker and apps like Skype and Line2, you can save some money by turning your iPod Touch into an iPhone, without the need to jailbreak.