When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Despite the abundance of sci-fi titles in the iOS App Store, very few of these mobile games ever have the staying power keep us glued for more than a few hours. Enter Space Pioneer, an awesome space exploration game that soft-launched in Canada ahead of a worldwide debut. With a little spoofing, you can experience the game yourself right now.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

The LG V30 has solid battery life. With its QHD P-OLED screen and 4 GB RAM, it's able to maintain all-day performance with average use. Heavier users might find that its 3,300 mAh battery isn't quite enough for a full day of work, though, but with a few software tweaks, you can squeeze out even more battery life.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Who would have thought that musical.ly would be the first social media app with a highly successful original show?

By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google Now, Voice Search, and Now on Tap rolled into one service, with an extra layer of personality added on top. The end result is one central location for all of your Google needs, be it web search, screen search, playing m...
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Repaired Original video on the LIFE LINE from 2007

Even with Apple's forthcoming iOS 5 updates to its default camera application, those upcoming features can't match what already exists in Global Delight's Camera Plus Pro. For $1.99, Camera Plus Pro provides users with over 100 tools for every part of the picture taking process, including video recording. It works with all versions of the iPhone, iPod touch, and iPad 2 with iOS 4.1 or the later update. Let's examine what it can do, and why you will want to replace Apple's default camera with ...

Over the past few years, I have downloaded several third-party web browsers for the iPhone, iPod touch and iPad, and the one I have found most advanced and feature rich is Atomic Web. While many mobile browsers have their unique features, Atomic Web could well be considered the professional browser for advanced web users. With each version of the app, the developer has included features that make navigating the browser more user friendly and useful for bookmarking, managing and saving website...

Here are the posters from the original 1974 "The Green Hornet"

Original picture appears on the ONION.
Original post by FrontierVillePost Click through to see pictures! Today we got an update for the 4th of July celebration of America’s Independence Day. Because this game is based in America around the Western Expansion movement, our pioneers deserve a chance to rest from their chores and celebrate!

The original international movie trailer for "Suspiria" The Movie Trailer for the Remastering of "Suspiria" The US movie trailer for "Suspiria"

Left 4 Dead 2 has a new add-on campaign, and it's called "The Sacrifice". This DLC for the Xbox 360 is a prequel to "The Passing", which features a meeting with three of the survivors from the original Left 4 Dead video game, where they learn that Bill, the fourth original survivor, sacrificed himself for his fellow comrades.

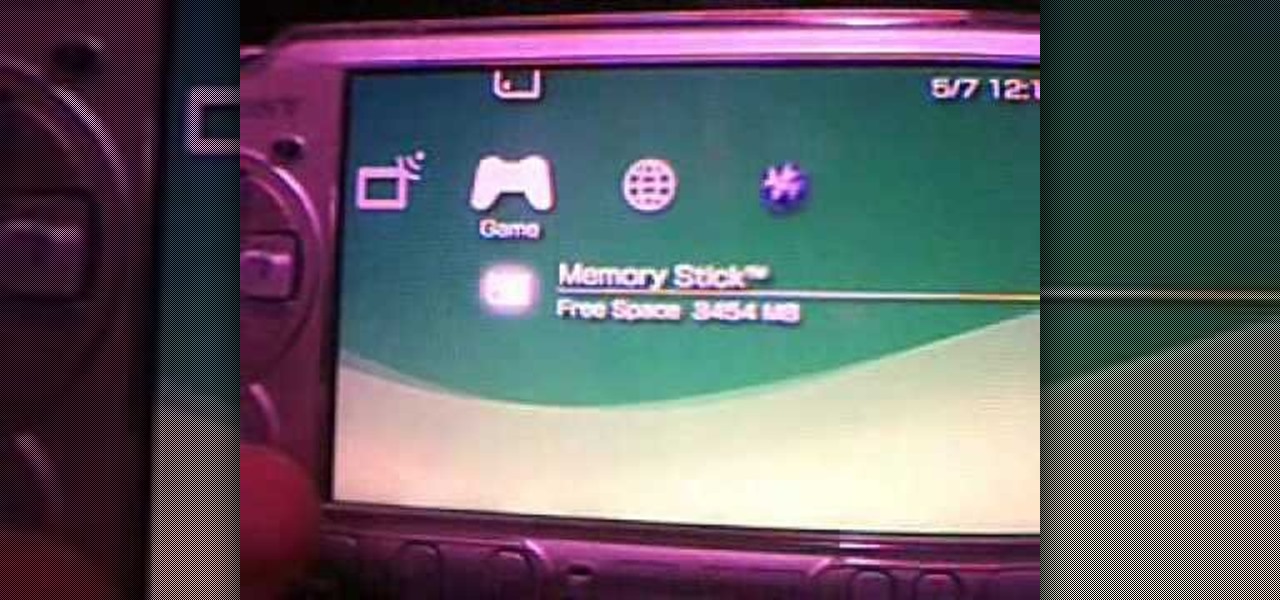
When Sony released the new versions of the PSP Slim and 3000 in 2009, it thought that it had solved the PSP's rampant hacking problem. They hadn't. This video will show you how to load the popular exploit / CFW installer ChickHEN R2 onto a slim or 3000 PSP, leaving it ready and waiting for whatever homebrew hacks and games you'd like to put on it.

In this how to video, you will learn how to layer videos in Final Cut Pro. First, open Final Cut Pro. Get your original clip and then put the clip that you want in the clip and drag it in over the top in the time line. Change it to image and wire frame. Grab the corner of the image and drag it down to the size you want. You can also move it around. Next, go to sequence and render it. Once that is done, change the selection back to image. Once you play the file, both clips will be playing. If ...

Maintaining a strong, healthy physique can be time consuming. If you're looking to stay in shape without committing a large chunk of time, this workout might the one for you. It only takes 15 minutes to build strong muscle and stay in shape!

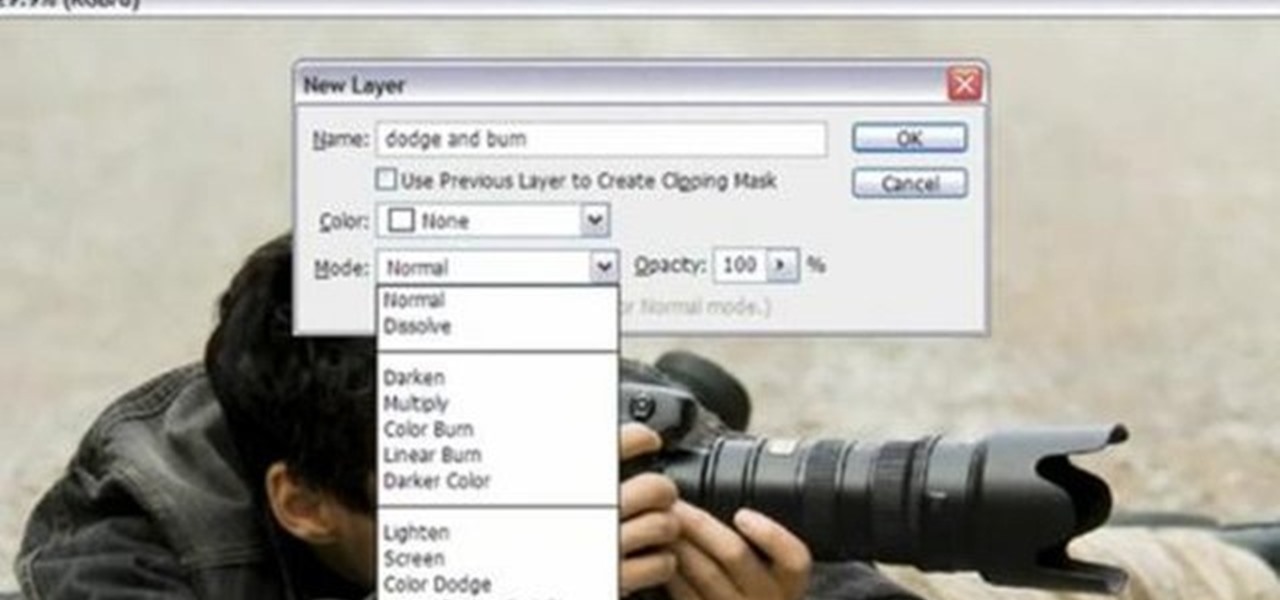
Yanik Chauvin demonstrates how to do Non Destructive Dodging (lighten) and burning (darken) of images using the tools in Photoshop. He shows the image of a man lying on earth with his camera. To start the work he wants to make a new layer which can be done in two ways either by clicking on the ‘layer’ button on top of menu or by pressing down the alt key and clicking on the new layer at button of the layer palette. It will bring up the dialogue box. He named it “dodge and burn” and from the l...

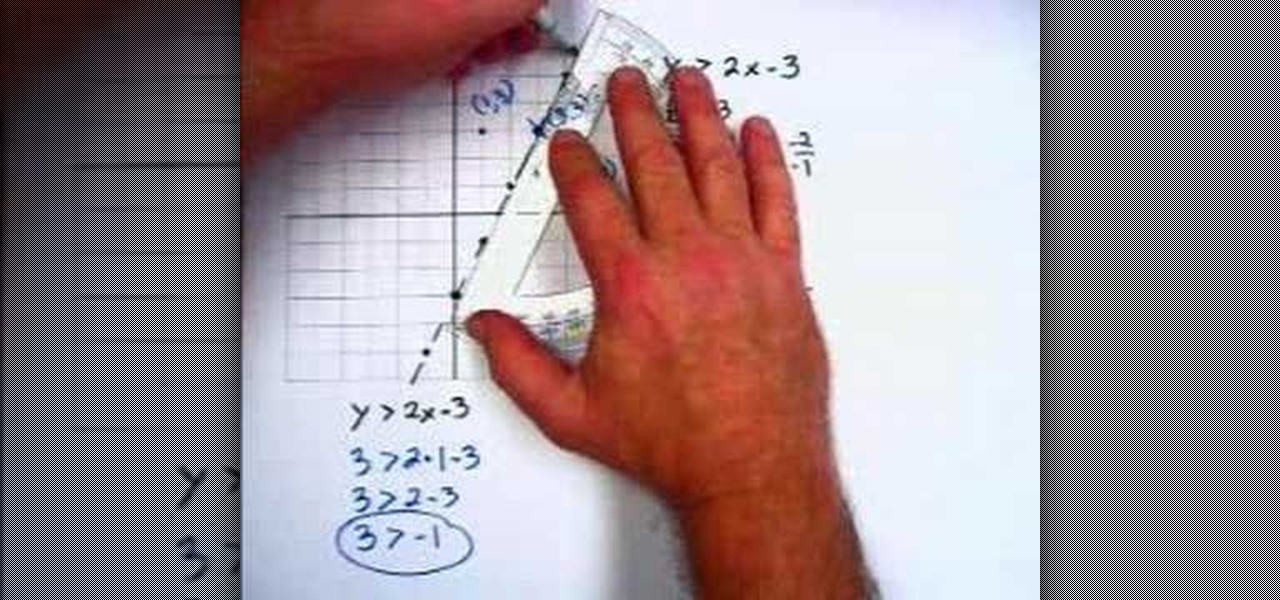
In this video the instructor shows how to graph linear inequalities. A linear in a equation is almost similar to a linear equation except for the sign in the equation. Now treat the in equation as a linear equation and graph the line. So substitute the lesser than or greater than symbol in the liner in equation with the equals to sign and graph the equation. Find the slope of the equation and identify the points that the line passes through. Now take a point on the either side of the pointed ...

Create a photo frame out of an origami paper or any art paper in minutes! 1) Lay the paper down on a flat surface. 2) Fold the paper in half with the shortest ends together. 3) Fold in half again so that you get quarters. 4) Unfold step#3 and with the first fold at the top, fold the top corners down along the center fold. 5) Unfold the corner flaps, open up the original fold and fold the corner flaps inside, now close the original flap. 6) Fold the lower edge up as far as it will go, do the s...

Did you know there's a difference between "semiformal" and "dressy casual"? Here are the finer points of proper dress.