In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.
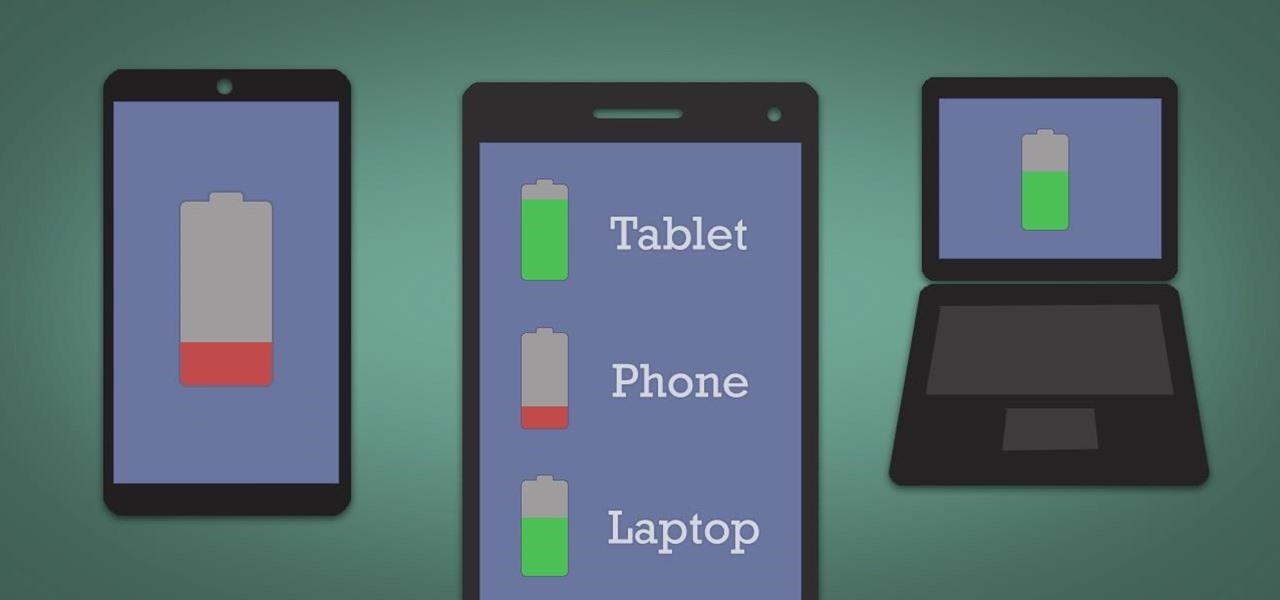
It's hard enough to keep tabs on the battery life of one device, let alone all of the different gadgets that a typical consumer owns in this day and age. Say your smartphone is running low on juice, so you switch to your tablet only to find out that it's almost dead as well. Better hope your laptop is fully charged, right?

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Whether it's using precious data or wasting battery power, switching between Wi-Fi and cellular service on your Android device can be a hassle. If your Wi-Fi is off, you may not know about free hotspot networks in the area you're in, leading you to waste network data (which more than likely is not unlimited). If your Wi-Fi is on all of the time, this leads to quicker battery depletion. There are already a few Android apps, like Auto WiFi Toggler, that combat this problem, but they just period...
Pokemon's Darkrai is one of the most coveted levels of the game. With this tutorial, learn how to find Darkrai in a few easy steps, as well as secure a Membership Pass and a Mystery Gift in Pokemon Platinum. So grab your Nintendo DS and follow along!

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

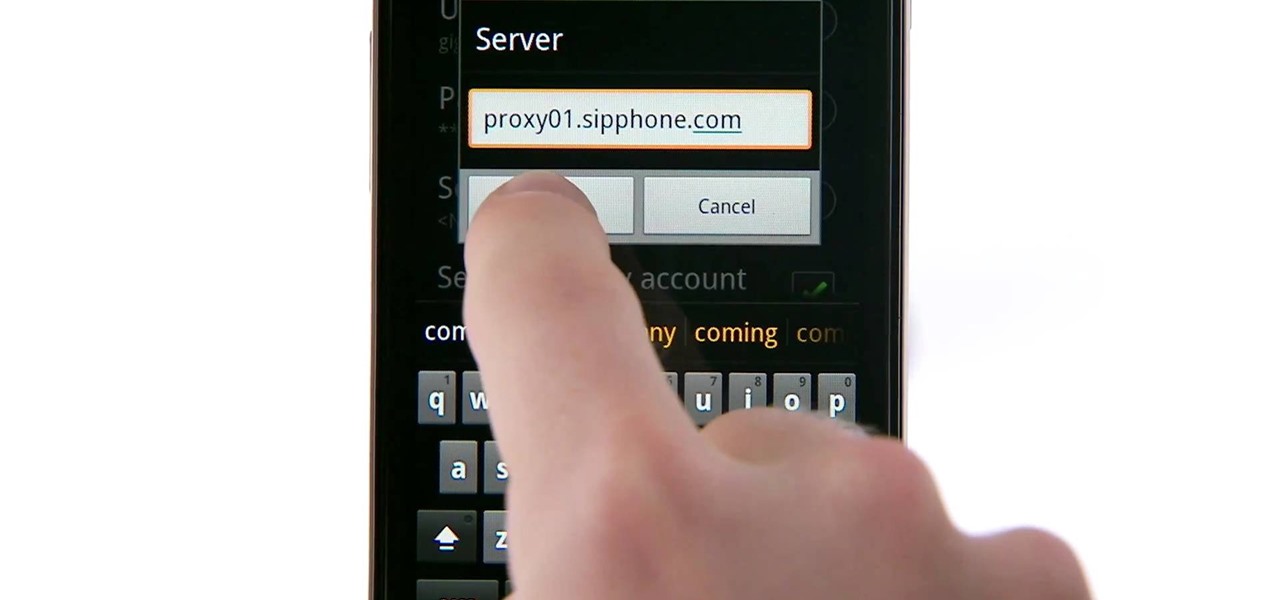
If you've got Android 2.3 Gingerbread running on your Google Nexus S smartphone, try out this cool feature. Set up a SIP (Session Initiation Protocol) account, and you'll be able to make Internet calls over Wi-Fi. You'll be able to talk to anyone with VoIP.

Tethering lets you share your Desire HD's 3G Internet connection with a second, Wi-Fi enabled device. Learn how to use it with this quick, official guide from HTC.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

In this tutorial, we learn how to set up a Wi-Fi network with a Linksys router. First, go to your cable modem and remove the yellow Ethernet cable. After this, plug the Ethernet cable into the very first port of the router and plug the other end into your computer. After this, connect any other electronics you have with cables, then plug the router into the wall to give it power. Next, turn the power to the modem and router back on. When finished, you should see a new Wi-Fi network appear in ...

This tutorial gives a start to finish explanation of how to make an Internet Wi-Fi router with Windows Vista. With real time computer screen video and narrative, it is easy to follow along at home.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

In this video tutorial, viewers learn how to disable their Wi-Fi SSID broadcast on a Linksys's router. Begin by opening your web browser and type in this address: Press Enter to access the page. Then type in your user name and password. Click OK. Now click on the Wireless tab and check Disable under "Wireless SSID Broadcast". Finish by clicking on Save Changes. This video will benefit hose viewers who use a Linksys's router, and would like to learn how disable their broa...

How to disable Wi-Fi SSID broadcast on an Apple AirPort in seven simple steps. Open your AirPort Admin Utility application. Find your network's name and double-click it or press the Configure button on the bottom right of the screen. Enter your password and click OK. The Configure "Apple AirPort Express" Base Station should open. Click on AirPort tab. Select the "Create a closed network" check box. Click OK on the dialogue box. Click the Update button on the lower right part of your screen. D...

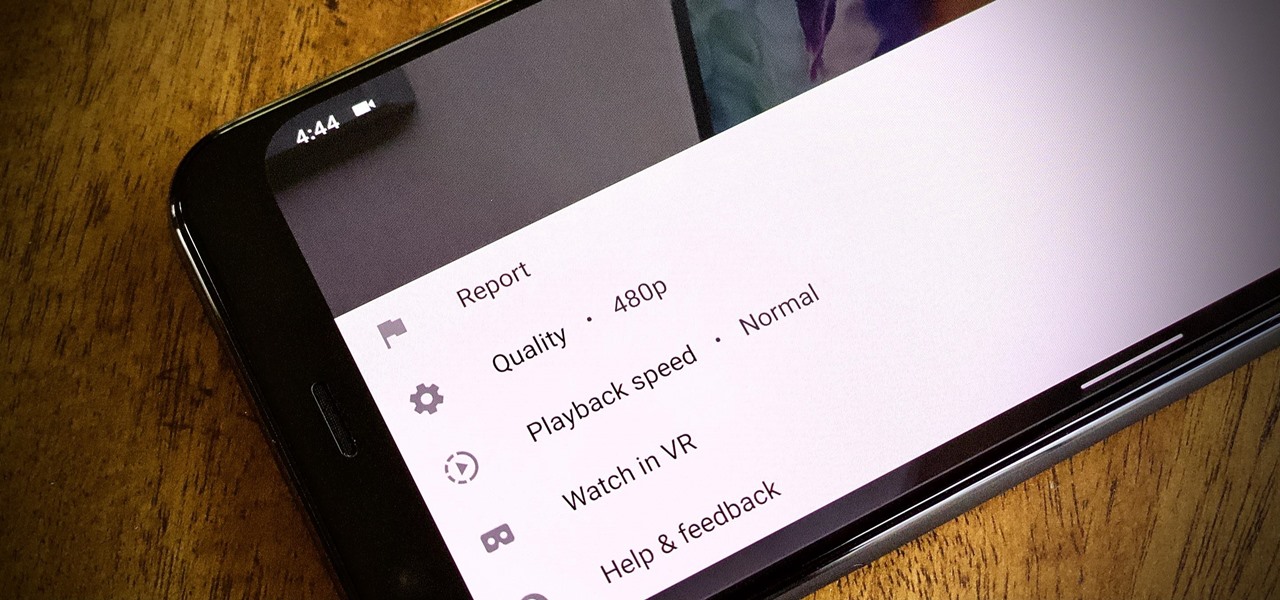
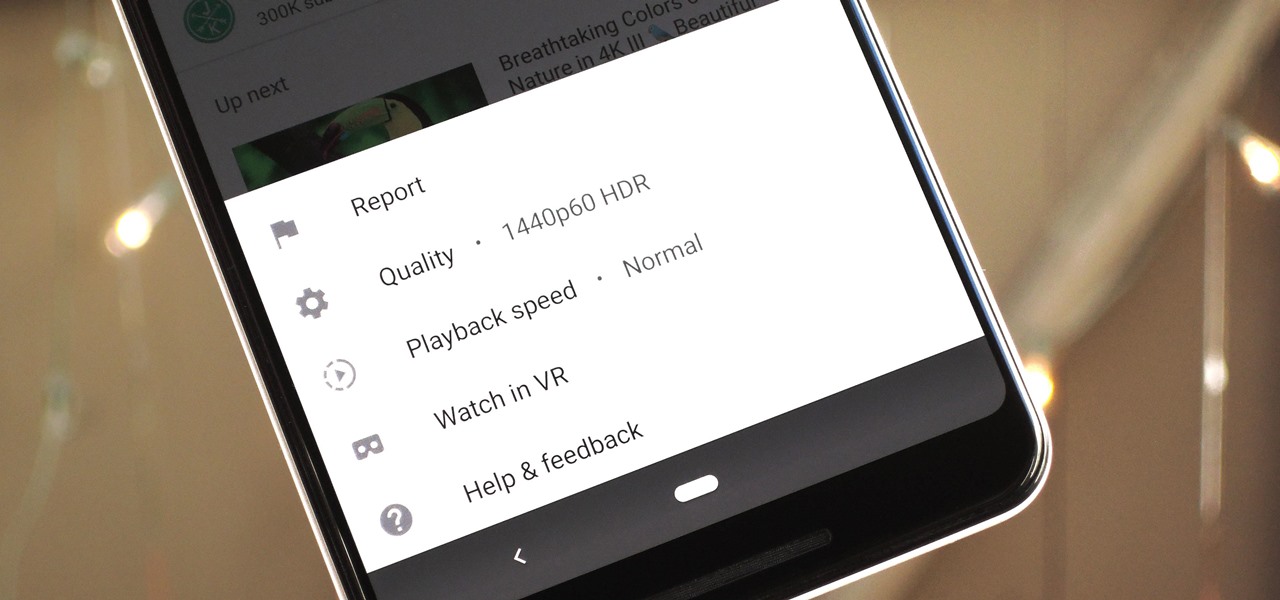
To reduce stress on internet bandwidth during the COVID-19 pandemic that the novel coronavirus is causing, Google decided to set YouTube's default video quality to 480p. That said, even when you could stream at HD quality without adjusting anything, you still couldn't switch the default to whatever you liked. We have a few methods on hand to help you change that.

The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.

Check out this helpful video to learn how to install Skype mobile video chat on your HTC Thunderbolt. First, download the file here then follow all of the instructions to get your Android smartphone running Skype video chat on Wi-fi and 4G.

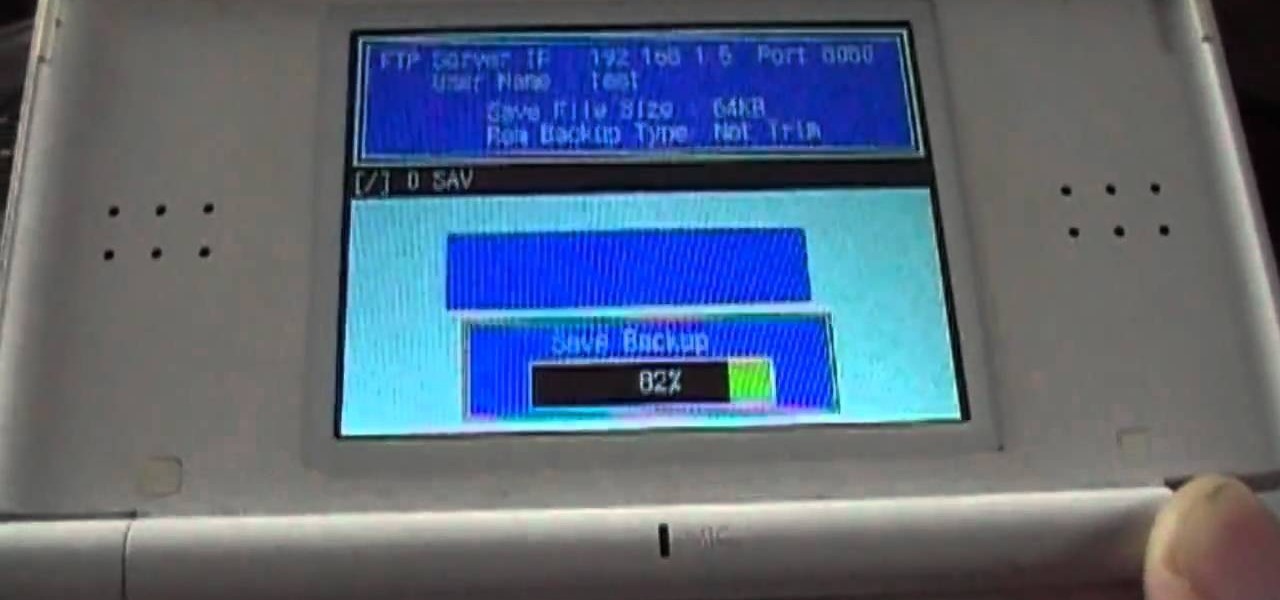
If you'd like to capture footage from your Nintendo DS, either to share online or make walkthroughs or playthroughs with commentaries, download all of the necessary files from Lifehacker, then watch this video for step-by-step instructions on how to get capturing. For recording gameplay this way, you'll need a DS or DS Lite, microSD card, NDS flash cartridge, Wi-Fi connection, SD card reader and a computer (along with all of those files you need to download).

In this clip, you'll learn how to use an Apple iPad as a wireless monitor for a still camera. In order to replicate this hack yourself, you'll need an iPad, Eye-Fi Pro X2 SD card, My Wi and Shutter Snitch. For detailed, step-by-step instructions, and to get started sending pictures directly from your digital camera to your iPad, watch this video guide.

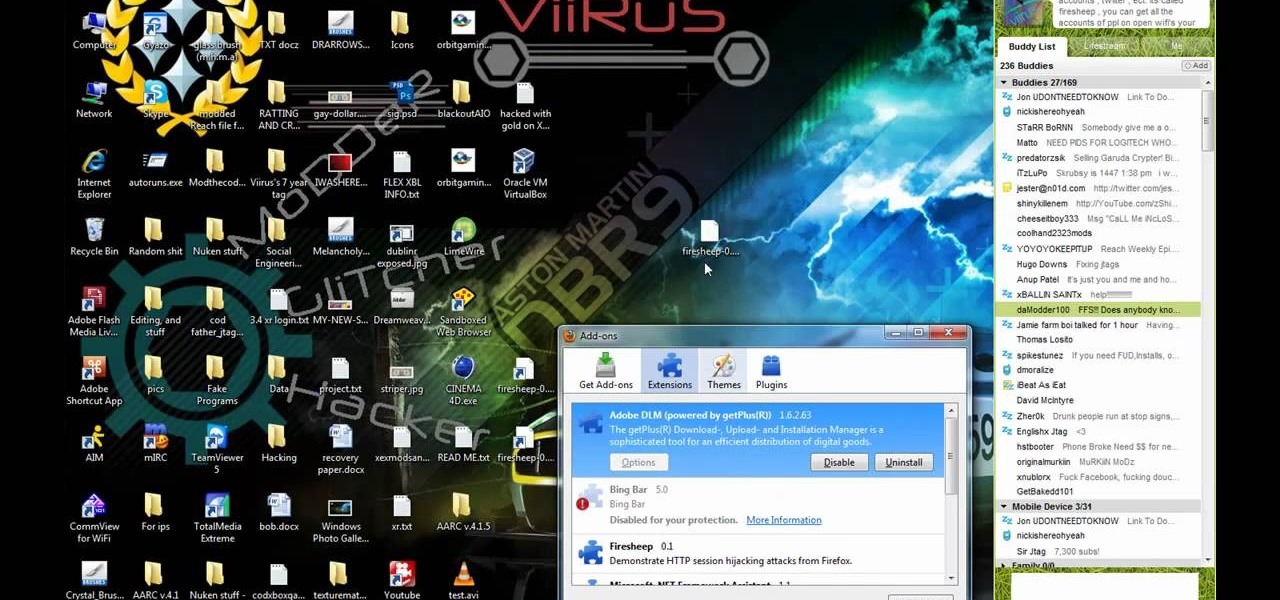
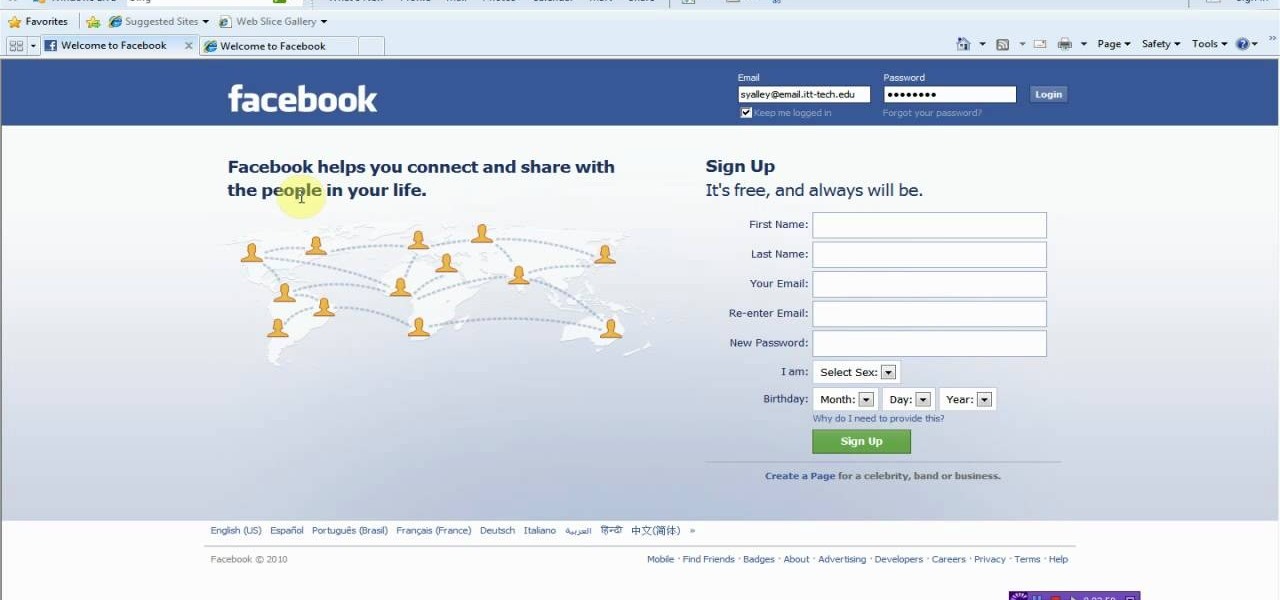
Ever wanted to hack your friends' Facebook accounts? With the Firesheep Mozilla Firefox browser add-on, it's easier than ever. Before you can use Firesheep to sniff account cookies, however, you'll need to download and install it. This clip will teach you everything you'll need to know.

Firesheep! It's a good reason to be cautious when using public Wi-Fi. But is it reason to stay off of open networks altogether? Certainly not! There are, in fact, a few simple steps you can take that will make you invulnerable to the malicious Firesheep Firefox addon. Learn how to protect yourself against Firesheep with this video guide.

If you're feeling extra adventurous with your new Android-based Samsung Galaxy S phone, aka Vibrantor Captivate, watch this video tutorial to learn how to root it in a few quick steps. Rooting your Android phone may give you a few benefits over a regular version, such as easy wi-fi tethering, better keyboard and even multi-touch browsing.

No Wi-Fi? No problem. All you need is a Bluetooth-enabled phone and laptop to surf the Web from anywhere.

This is a video tutorial on how to set up a very simple foil parabola to increase your wireless signal at your home.

Kitchen utensils and computers, that's right! This video will show you how to increase your computer's wireless connection using a strainer!

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you can get it right now.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.