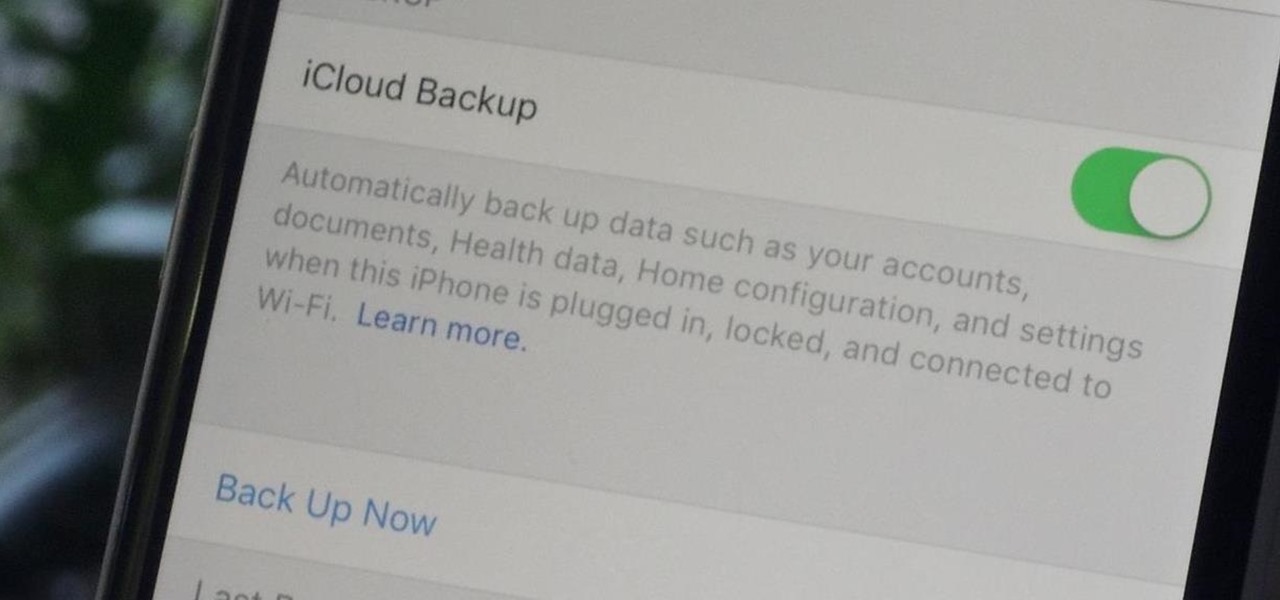
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

If you're looking for ways to get all James Bond on someone, you may want to check out this video. In it you'll see how to turn your iPhone into a spy camera, letting you take photos or videos at set intervals, or, whenever the mic detects any sound. It's pretty cool and not hard to do! Requirements: 1. iPhone 2. iPad 3. Wi-Fi (bluetooth works aswell but not as good) 4. a place to put iPhone 5. spare time! So remember, the name is phone. iPhone.
Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop iTunes on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

See how to build a weatherproof compact high gain WiFi antenna for under fifteen dollars! This homemade WiFi antenna should be enough for most applications, since it's three times more powerful than a standard antenna.

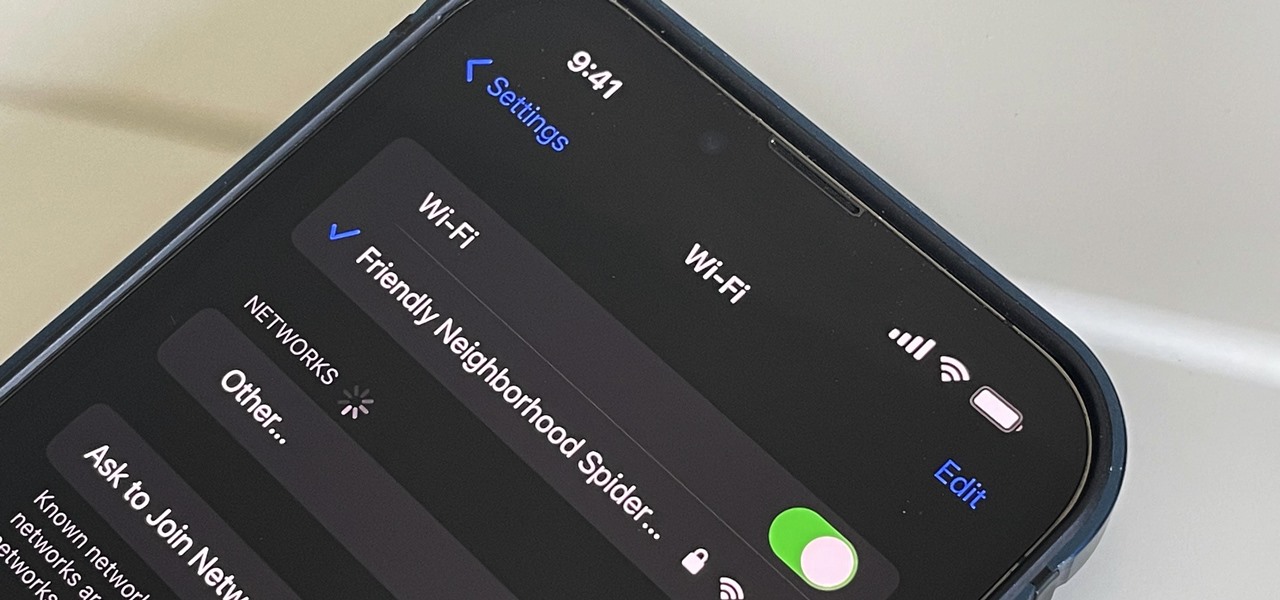
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

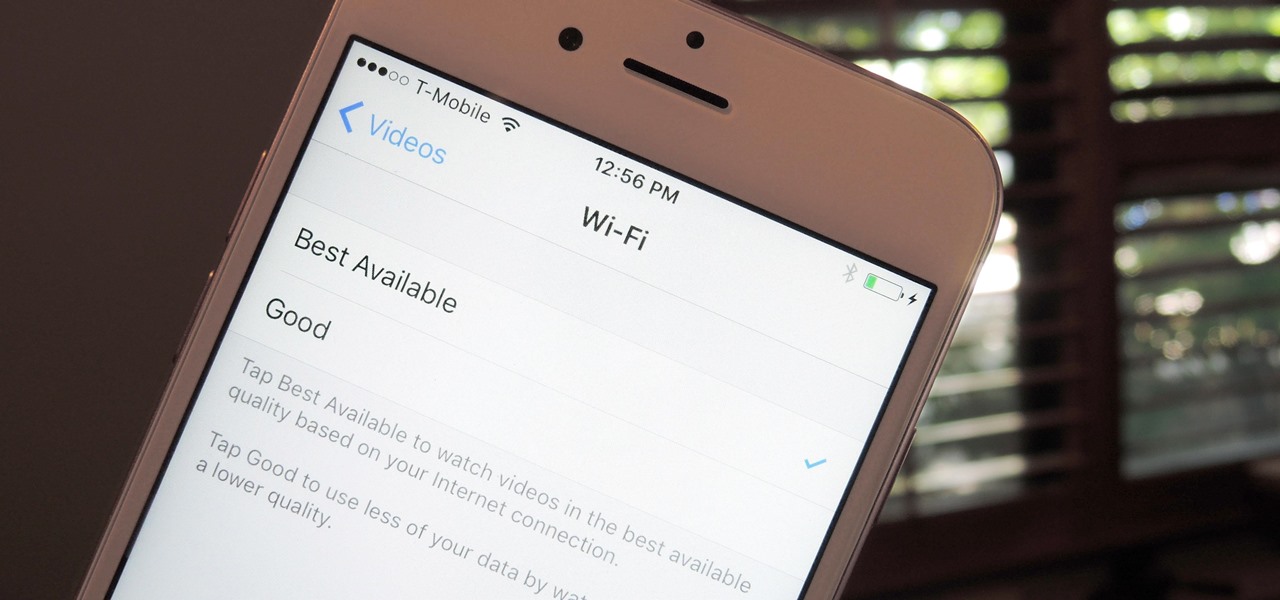
If you're watching videos over Wi-Fi on your iPad, iPhone, or iPod touch, iOS 10 lets you adjust the quality for when you want to save data or need help watching a movie or TV show on a poor connection.

You see it in the movies all the time. A character on the phone doesn't like what the other person is saying or telling them to do, or they just don't want to talk to them anymore, so they fake bad reception and cut the call off. In real life, it's pretty easy to tell when someone is doing it, and there are better ways to end a call abruptly so that it looks like you didn't hang up on them.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

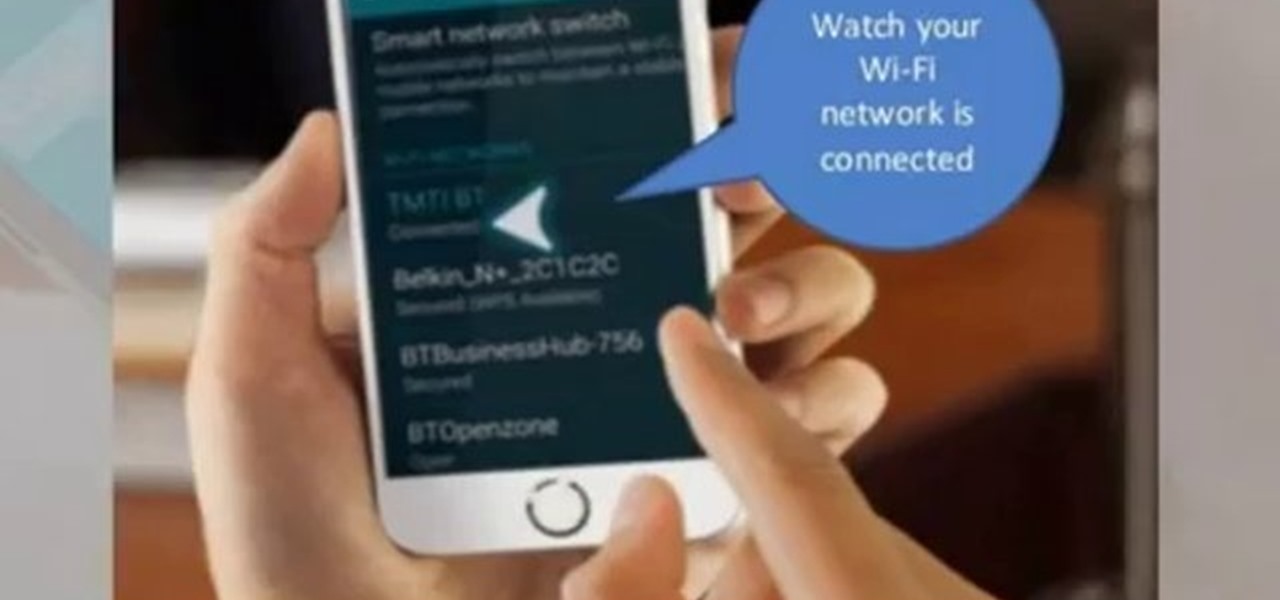
This video will show you how to set up a connection with wifi network in your Samsung Galaxy S5. So please watch the video and follow all the steps carefully. Employ the technique in your Samsung Galaxy S5 phone and enjoy a wifi environment.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

The advantages of rooting are vast. From free wi-fi tethering, being on the latest and greatest software, theming all aspects of the OS, to ditching Touchwiz for a pure Google experience and much much more.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

In this tutorial, we learn how to allow only your computer to access your Wi-Fi while using Apple Airport. First, select the Apple Airport Express item on the base station chooser. Double click this and press Configure, then enter your password in the new window that pops up. Now, a new window will open, and you will need to click to "Access Control" tab on the top of the window. Next, click "add" and then select "Mac address" and enter in your MAC address and description. Once finished, clic...

In this video tutorial, viewers learn how to disable SSID broadcast on a NETGEAR router. Begin by opening your browser and go to the site: Router Login. Then type in your user name and password. Click OK. In the sidebar under Setup, click on Wireless Settings. In Name (SSID), type in a new network name and click on Apply. In the sidebar under the Advanced, click on Wireless Settings. Type in your user name and password once again, and click OK. Under Wireless Router Settings, uncheck Enable S...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

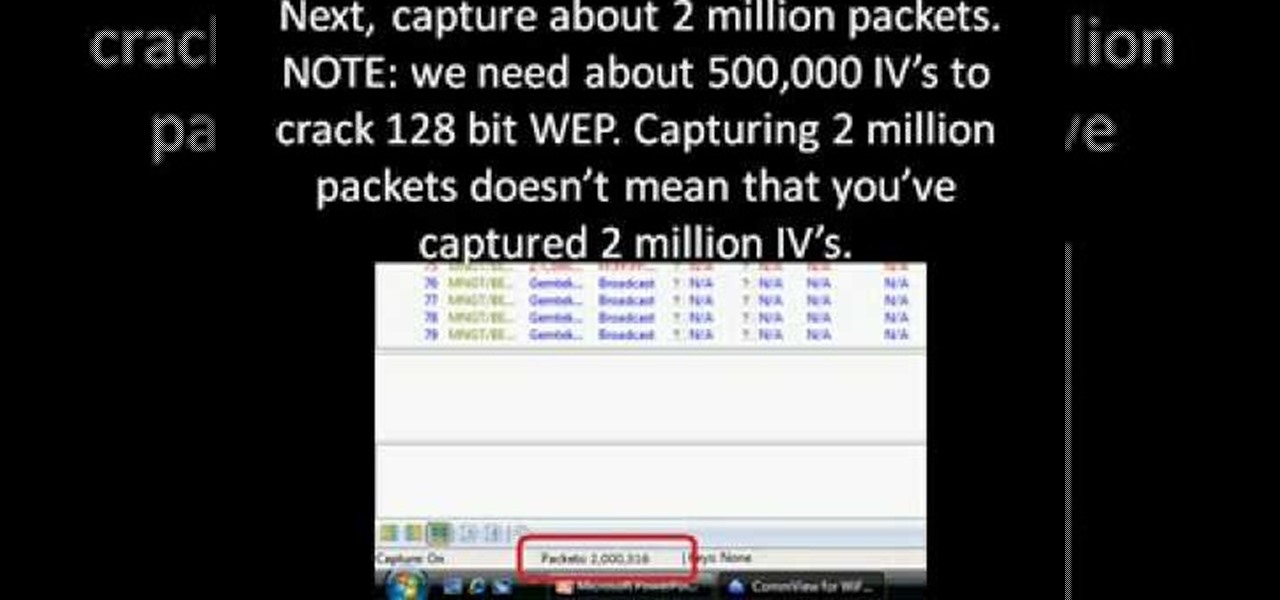
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...

All you need to remotely access your computer's iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide.

All you need to remotely access your AppleTV library is your iPhone. Learn how to control Apple TV with your iPhone with this Howcast guide.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy for this hack. If you follow the instructions in the video, you'll have a completely rooted Motorola Droid X cell phone. Try it out.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

Watching YouTube on your phone has never been a better experience than it is today — our smartphones have super-sharp displays that make watching the newest HD, QHD, and even 4K content look fantastic. But there are plenty of circumstances where we want to watch our content on a larger screen.

Chromecast comes to mind when "casting" video from a smartphone to a big screen television, but it's not the only way to "cast" streaming content. This is especially true for Netflix, where you can cast movies and TV shows to not only a Chromecast-enabled TV, but to smart TVs, video game consoles, and other streaming media players so that you have complete control right from your smartphone.