Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.
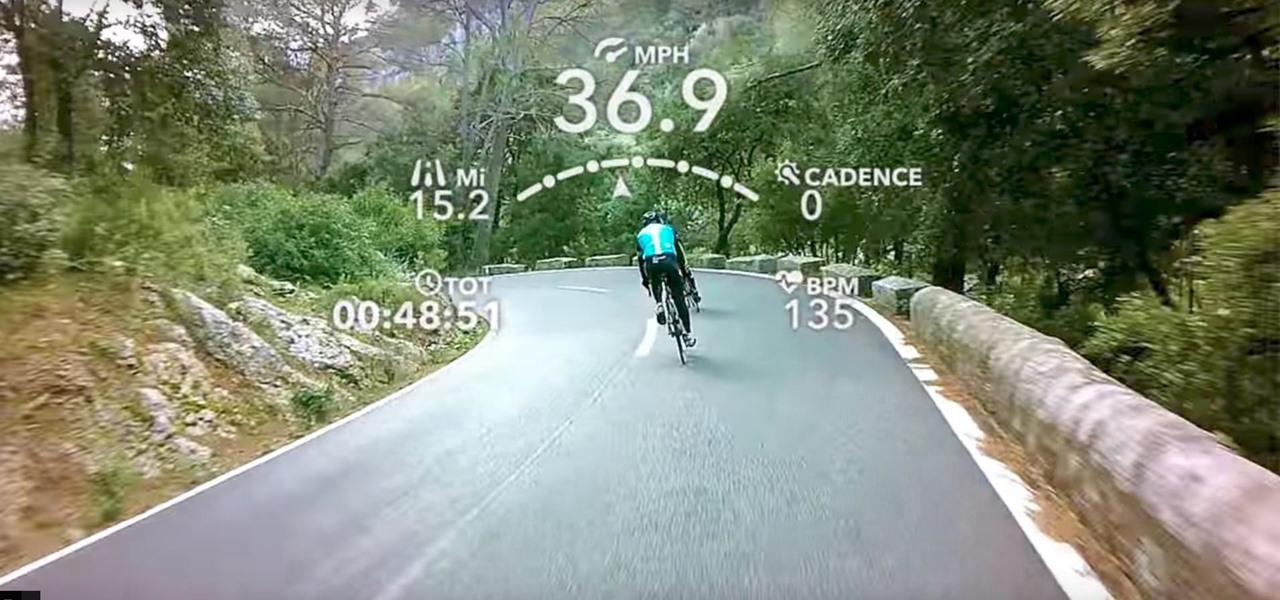
Cyclists of the world, new AR glasses are here to improve your rides. Possessing 2 GB RAM, a quad-core CPU, GPS, 16 to 32 GB of storage, an accelerometer, camera, gyroscope, magnetometer, barometer, Bluetooth, speaker, WiFi, and a mic, these aren't your regular UV-blocking sunglasses. Called the Everysight Raptor AR glasses, these shades project all of the information a cyclist could need to optimize their rides.
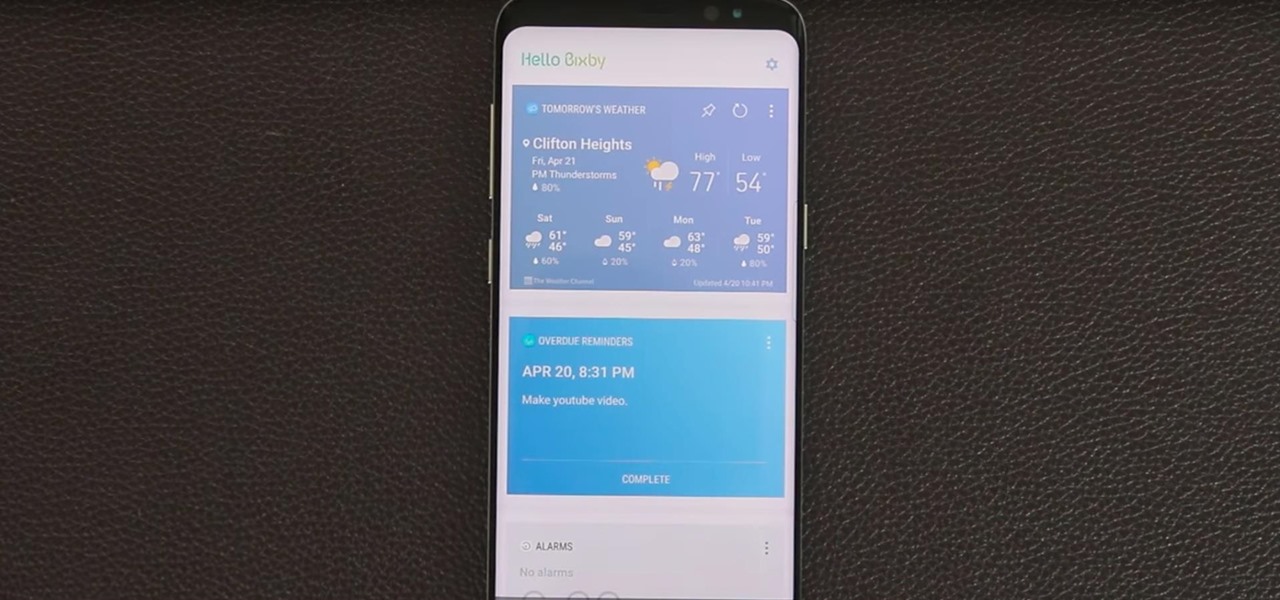
Bixby — Samsung's voice-activated digital assistant — has been delayed again because the software still can't recognize English. Although Samsung claims Bixby can execute 15,000 tasks, it appears it's inability to master English is a major obstacle that's preventing its full release in the United States.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

All the Driverless news you need to know from the past 24 hours, bundled together in a tightly written package, about Uber, London delivery services, capital investments, and kangaroos.

There was big news today from Google, Apple, Volvo, and Nvidia regarding their self-driving efforts.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Apple CEO Tim Cook's June 5 announcement that the company is developing autonomous software should have some companies rattled. At least, Morgan Stanley thinks Tesla should be.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.

When just floating peacefully in the water with their brood mates, the Culex mosquito larvae in the image above does not look very frightening. But in their adult form, they are the prime vector for spreading West Nile virus — a sometimes mild, sometimes fatal disease.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

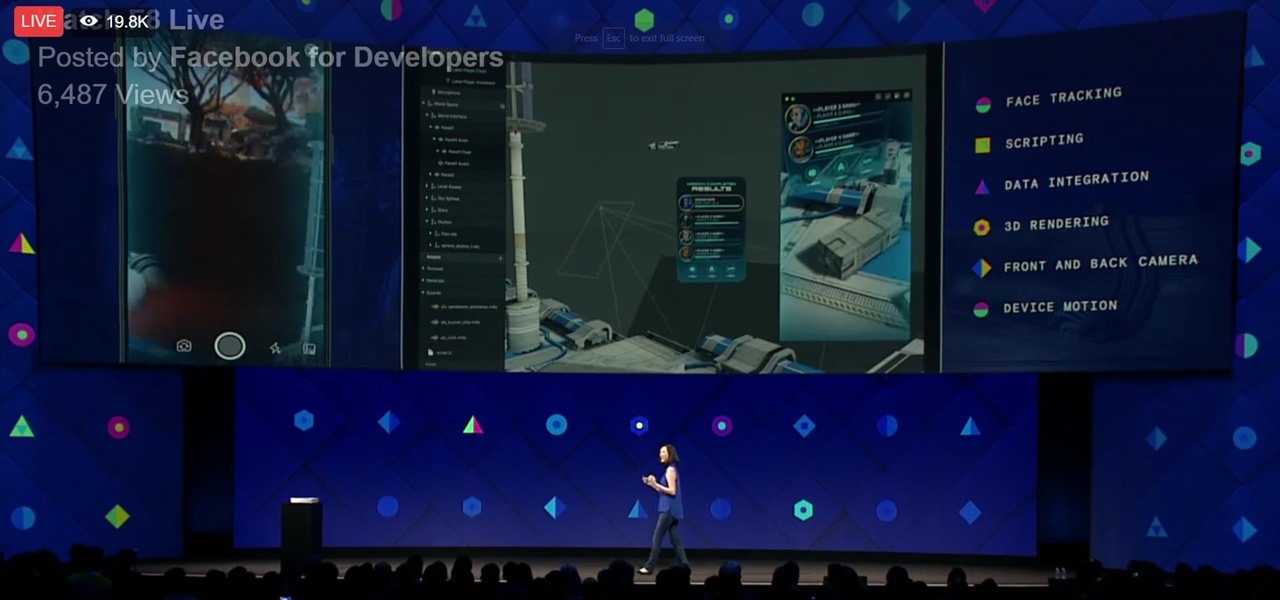
During his opening address on April 18 at F8, Facebook's developer conference, CEO Mark Zuckerberg launched the company's augmented reality platform centered on artificial intelligence-powered cameras.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

An advance in the race to stop birth defects caused by Zika-infected mothers has been made by a team of researchers from Rensselaer Polytechnic Institute in Troy, New York. They have identified the process Zika uses to gain entry into the placenta, and published their findings in the journal Biochemistry.

Apple is in the process of developing its own graphics processors for future iPhones, according to recent reports.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

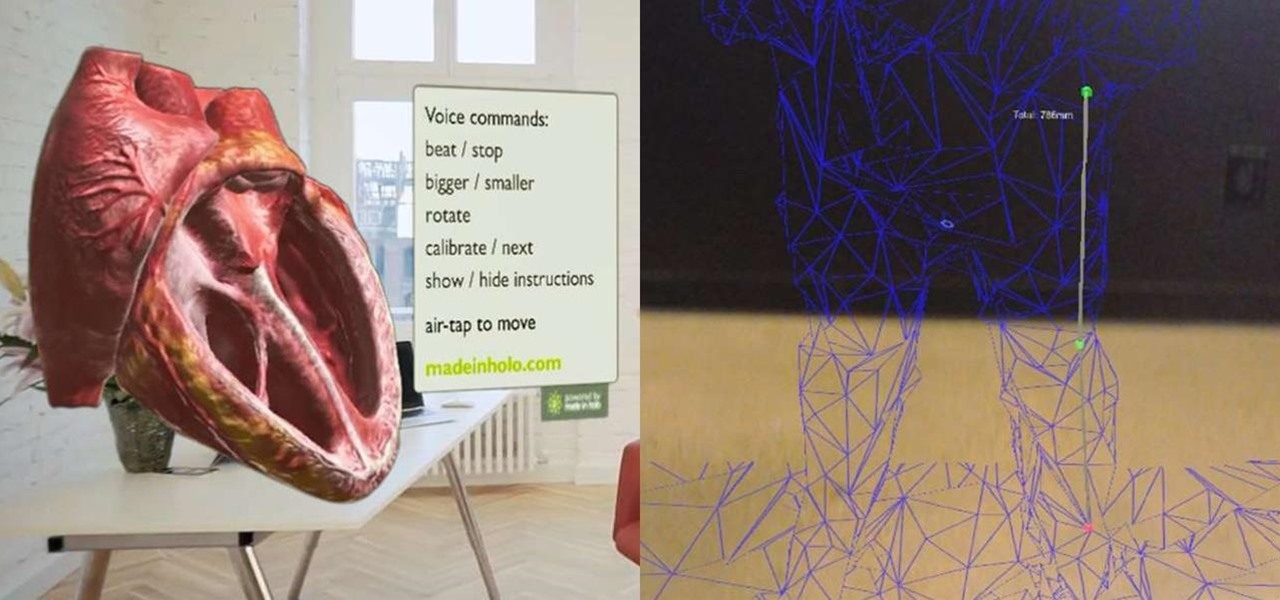
While all of my previous Have You Seen This? posts have all focused on individual HoloLens apps in the Windows Store, this time I'll be sharing a couple at once. These holographic applications are really simple in scope, so there is not a lot to say about them, yet they are interesting enough for me to want to share them with you.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Watch out Samsung (and you too, Pebble, Sony and the still unrealized Apple), your hold on the smartwatch market is about to get a lot less firm. Announced today, Google has released Android Wear, their platform for developing smartwatches, along with a preview of the Moto 360 smartwatch from Motorola.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

I know that after seeing 8 Mile for the first time, you and your friends tried a few freestyles yourself. Nothing to be embarrassed about. As one person dropped the beat, you started your stuttering flow, and everyone else nodded their head. And for a second you probably thought you sounded pretty good, until the beat maker started coughing and threw you off.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

Rust protection doesn't have to cost a fortune. With a little zinc and some electricity, you can protect your precious metals from rust by galvanization. When you galvanize something, you're giving it a protective coating, and in this case, it's a zinc coating.

November 11th isn't just Veterans Day— it's Origami Day in Japan, where they celebrate the traditional art of paper folding. November 11th is also the last day of World Origami Days, a 2-1/2 week celebration held internationally.

Acne develops when pores become blocked with dead skin cells and oil. They usually disappear over time but sometimes they leave a scar. When those blemishes form white blood cells rush to the surface to help heal the area. But occasionally a scar forms. Popping and picking can send bacteria further into the skin and increase the blemish and it greatly increases the likelihood that a scar will appear. Nodules and cysts are more severe blemishes and have an increased likelihood of leaving scars...

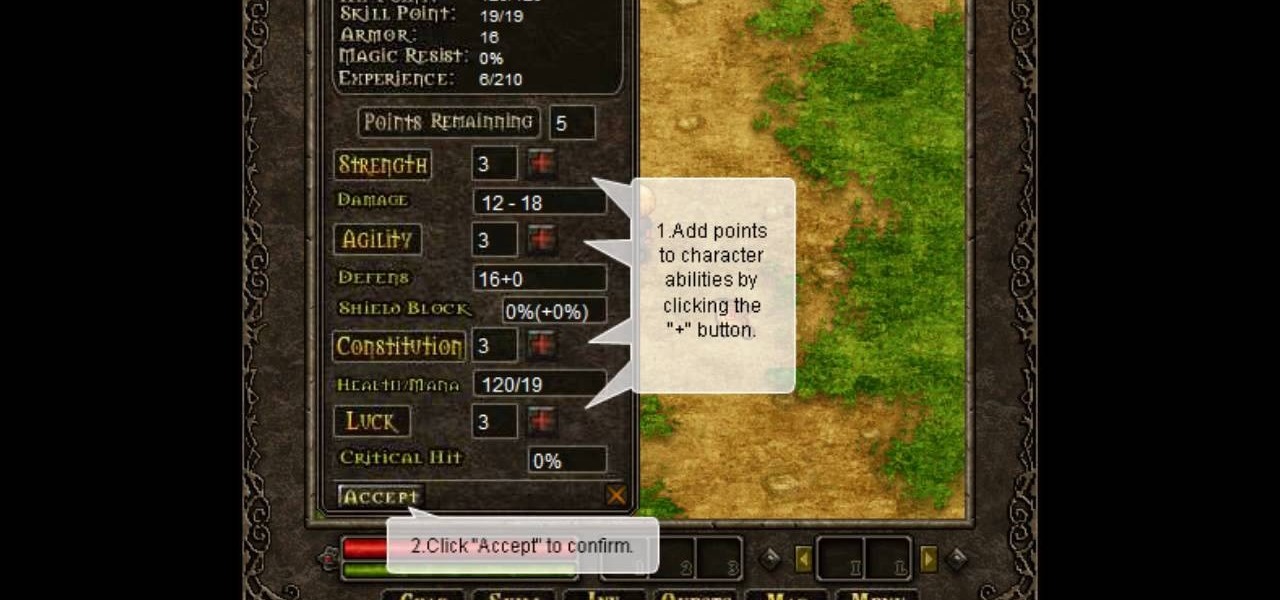
Want more gold? How about more skill points? You may need them in the game Acruz. But how do you get more, more, more? Well, with Cheat Engine, you can get more gold and skill points, with no real hassle.

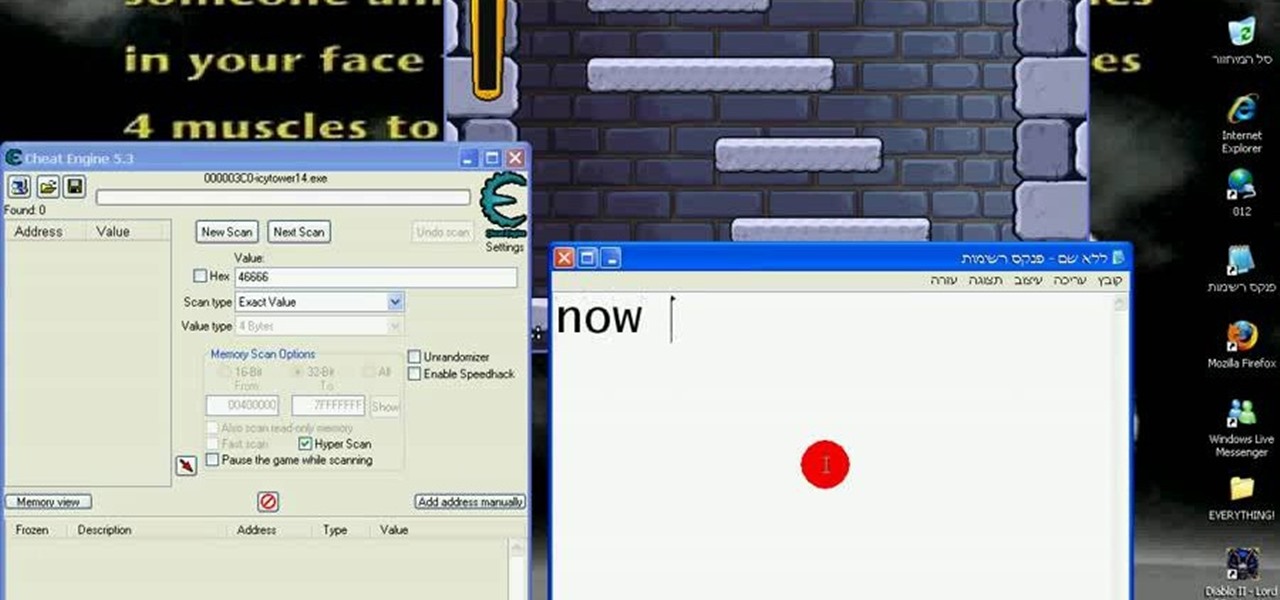
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily.