In honor of hurricane season, bartender Anthony Caporale gives you a tutorial on how to make a Hurricane. Originating in New Orleans, this drink is always served in a hurricane glass (reminiscent of hurricane lamps), and always sure to add some life to the party.

Chicken tikka masala is a delicious curry dish, originating in India but now being cooked and served worldwine. You don't have to be a master of Indian cooking to make this dish - it's easy to make this spicy, flavorful dish at home. You don't even need chicken - tikka masala can also be made with lamb, beef or fish.

This video demonstrates how to write the letter P in calligraphy copperplate. The technique that is illustrated in this video show you the proper way draw the letter P effectively and beautifully. The video first shows you how to draw the capitalized letter P. The first step is to create a slightly S-curved stroke downward from the top margin to the bottom-middle margin--thickness in the middle. You end the line with a curled tail. To complete the letter you then have to draw a looping, curle...

Originating in Harlem in the 1920s, a rent party is a fun way to stave off eviction. You will need a place to party, food and drink, musical entertainment, paying guests, party flyers, a hat to collect donations, and lots of beer. Fact: The going rate for a Harlem rent party admission was usually 25 cents, plus extra for the homemade concessions sold in the kitchen or hallway.

Bob Fenwick shows us how to determine where a gutter leak is originating and what may be causing the problem, as well as how to correct it.

The roots of the sitar extend back 2000 years, with the modern sitar originating in the Middle Ages. Learn to play the sitar from an authentically trained player in this free sitar video lesson.

This fish taco recipe from Jason Hill is a Mexican favorite, originating in Baja, Mexico, and popularized with Rubio's Fish Taco recipe in Mission Bay, San Diego. This video shows you how to make grilled fish tacos along with Jason's fish taco white sauce. Serve alongside a cold Corona beer. Ole! The ingredients are mahi mahi or any whitefish, lemon herb marinade, cabbage, tomato, white sauce, and corn tortillas. Learn how to prepare this fish taco recipe by watching this video cooking tutorial.

Dragons are very popular storybook characters, especially with the release of "How to Train your Dragon" in movie theatres. Check out this tutorial and learn how to draw your very own fire-breathing buddy!

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Theming is one of the many facets of Android that gives it a leg up on its iOS competition. With the right home launcher and icon theme, you can completely change the look and feel of your device in just a few minutes.

When on-screen buttons were introduced alongside Android 4.0, it didn't take long before Google added a gesture to these virtual navigation keys. Since then, an upward swipe originating from the home button has always been a shortcut to Google Now on Nexus devices.

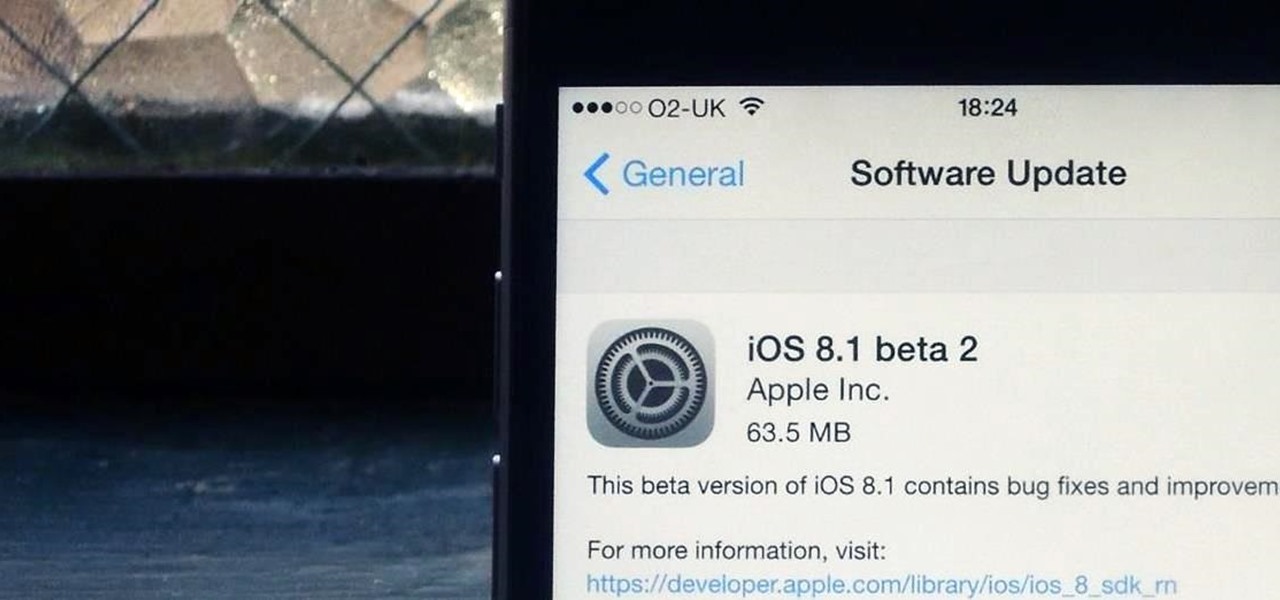
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

Google's Chromecast streaming device is a marvel of functionality and form. Even with powerful features such as screen mirroring and collaborative party playlists, it's the device's idle screen that first catches the eyes of most folks.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Owners of Google Pixel devices now have a plethora of imaginary friends to play with thanks to the Playground augmented reality app.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

I'm a sucker for sushi, both in its traditional forms and its modern fusion creations. When the infamous sushi burritos surfaced, I'm not ashamed to admit that I waited in a ridiculously long line for what is essentially an uncut sushi roll. (As for whether it was worth it or not, well... that's another story.)

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

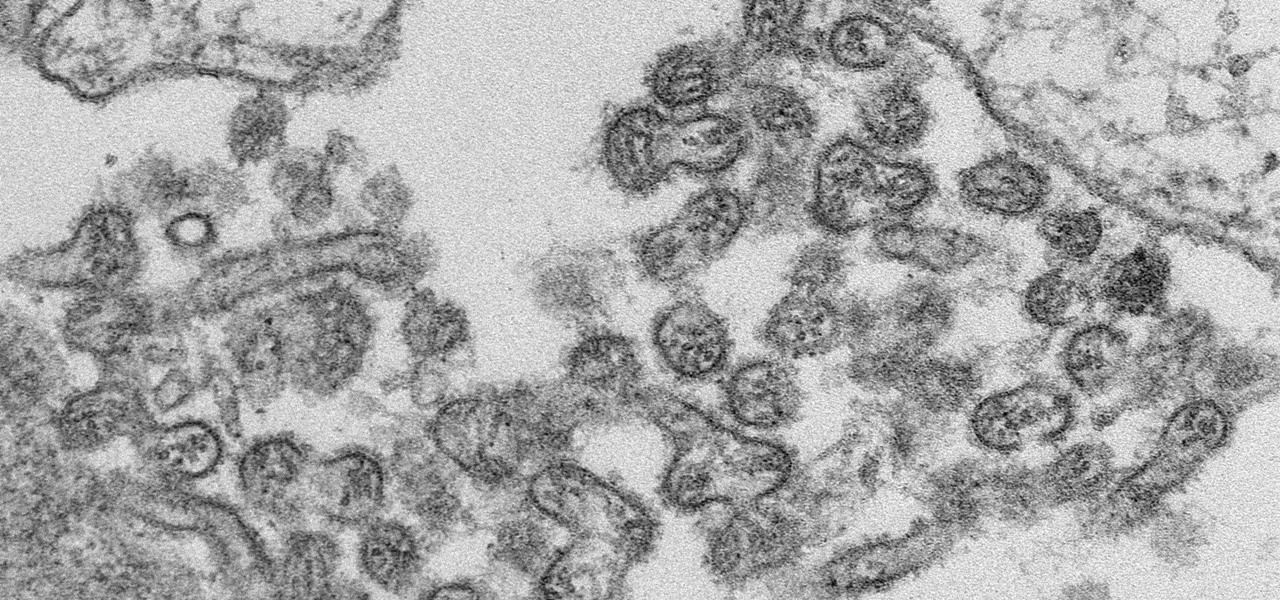
A new case of the still-mysterious Bourbon virus was confirmed in Missouri, likely originating within the state, local authorities said in a June 30 press release.

Many Android users woke up on January 10 to discover that their phone's performance took a nosedive overnight. Battery life is draining fast, overall performance has been sluggish, and devices seem to be overheating for no apparent reason. Not to worry, this isn't happening because of something you did.

Several years ago, I moved to Brooklyn, New York, just outside a Spanish neighborhood. It was here that I was introduced to chayote. Fast-forward to present day: I live in Los Angeles and buy several chayote squash a week to cook with—yes, I said several. It's so versatile and healthy! For the uninitiated, chayote (chai-YOH-tee) is a light green squash shaped like a pear originating from central Mexico. Although it's considered a fruit, chayote is a member of the Cucurbitaceous (gourd) family...

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

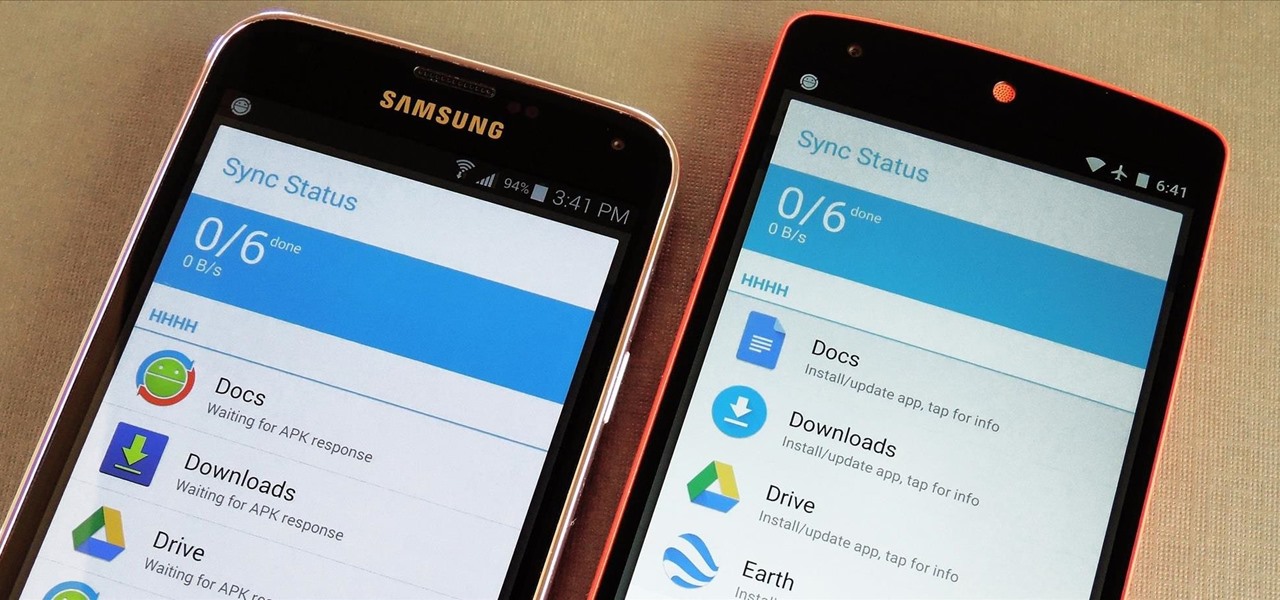
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

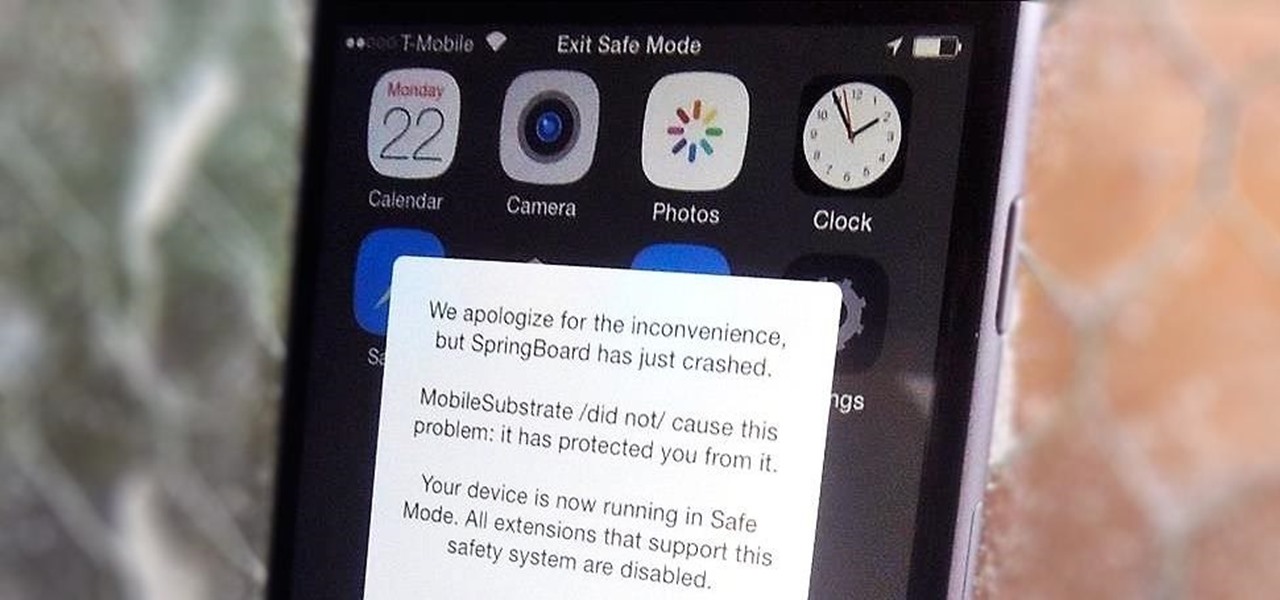
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

Toast notifications are a type of pop-up alert built into Android, letting us know when an app has performed a certain action. Whether it's Gmail saving a draft or Firefox opening a new tab, toasts are meant to be informational while not being totally intrusive.

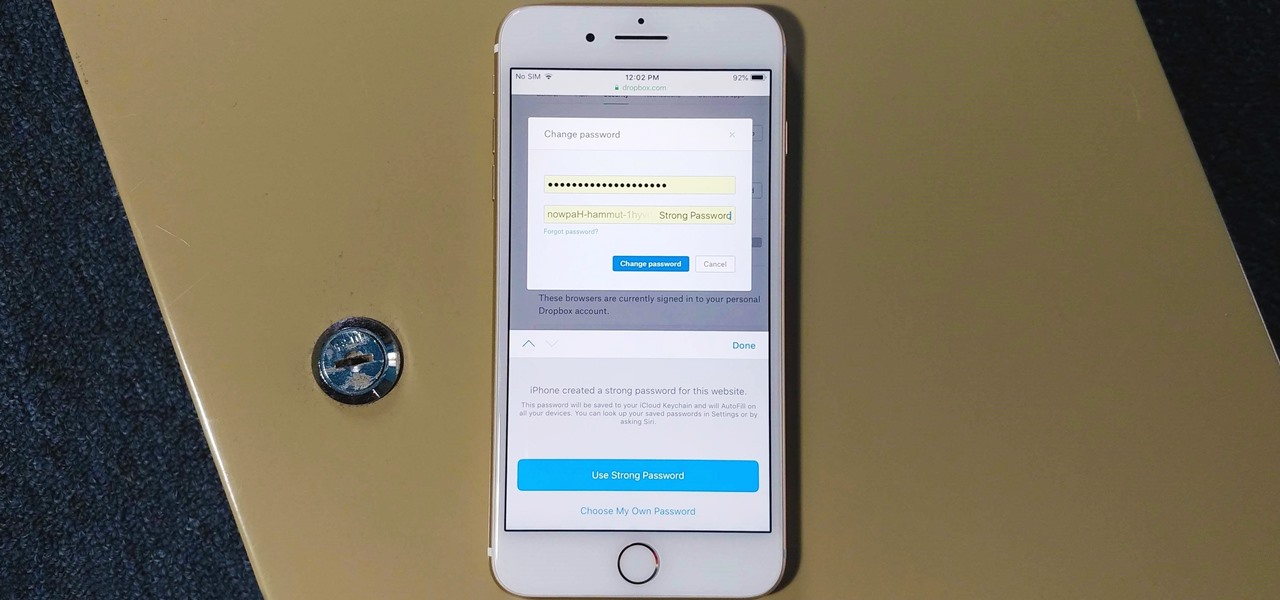
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

I know people who hate mayonnaise. I know people who detest ketchup. But I know almost no one that hates mustard, and that's because mustard has a complexity and depth that bland mayo and ketchup do not. Mustard runs the gamut from smooth and subtle to sharp and spicy, especially when you know how to make your own.

You no longer have to resort to a third-party email client on your iPhone to schedule messages to send whenever you want. Apple built the scheduling functionality into its Mail app, and it works with any email service you use in Mail, whether that's iCloud, Gmail, Yahoo, Outlook, or another service.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

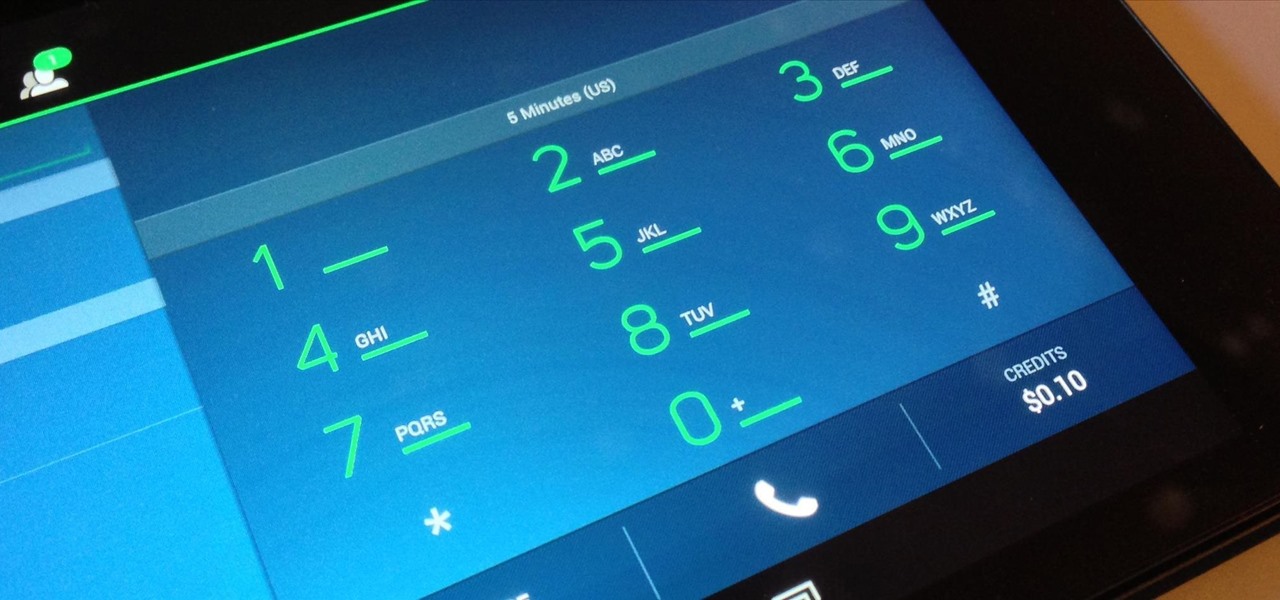
Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

Standard notifications on Android are pretty intuitive, but the little popup toast messages that appear at the bottom of the screen can be a bit elusive. They come and they go, and that's about it. You can't long-press them to change their settings or even tell which app displayed them in the first place.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.