Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

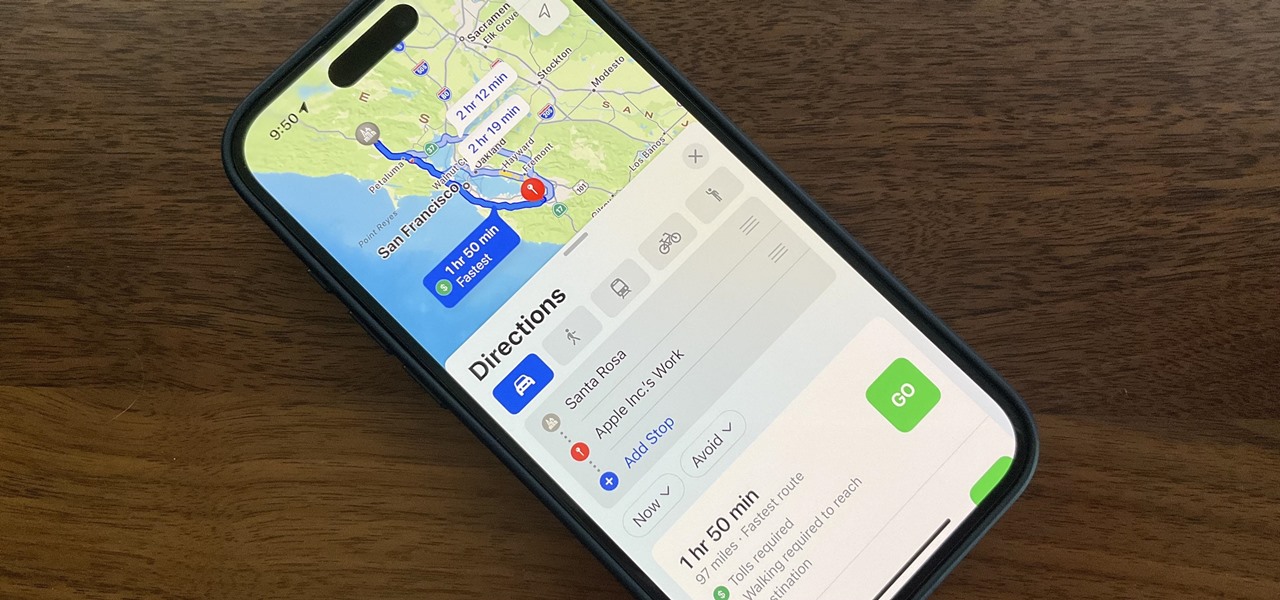
While Apple Maps didn't receive as huge of an update on iOS 17 as other apps such as Safari, Camera, Photos, Notes, Weather, and Messages, there are still some very important new features and changes you need to know about.

Apple just released the public GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes three hours after Apple released the 13.6 GM for developers, and the same day as the release of iOS 14 public beta 2.

Apple just released the GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes nine days after Apple released the third developer and public betas for 13.6, and the same day as the release of iOS 14 public beta 2.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

While the iPhone world's attention might be fixated on Apple's upcoming iOS 14 and all of its new features, it's still in beta. What's not in beta anymore? Apple's latest iOS 13 update — iOS 13.6 — which dropped on July 15.

Many lazy cooks skip rinsing off their grains before they cook 'em, but that's a big mistake for a few reasons. Some grains have coatings on them that need to be rinsed off to cook properly and taste good.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Apple's iOS 18.2, iPadOS 18.2, and macOS Sequoia 15.2 updates are here, packed with enhancements that take device intelligence to the next level. New Apple Intelligence features lead the release, offering smarter tools for creativity, productivity, and everyday tasks. However, there are also new features for all iPhone, iPad, and Mac models — not just those supporting Apple Intelligence.

How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see information about them on the internet, MySpace, Facebook or other site or track the email. The site gives instructions on how to track the email via outlook, outlook express and other mail programs and the video shows ...

In this 5 part tutorial video, you will learn how to dance the Soukous. Soukous is a vernacular dance which is one of many roots of swing dance. Originating in the Democratic Republic of Congo, this form of dance has been modernized, much like today's swing is a descendant of the cakewalk and Texas Tommy.

The two-step is a step found in many folk dances, and in various other dances. The Washington Post Two Step is a 19th Century name originating in the USA. It is similar to the traditional two-step dance but slowed down and a bit jumpier. This video is only a demonstration, and unfortunately it does not give step by step instructions.

A butcher block table (or counter) is a solid, wooden table. Originating in butcher shops (hence the name), this has become a popular household item. Butcher block tables and counters are durable and attractive looking. The downside of butcher block is that the wood is so porous it can stain easily. Butcher block can be sanded and refinished to get rid of stains, but that drastic step isn't always necessary.

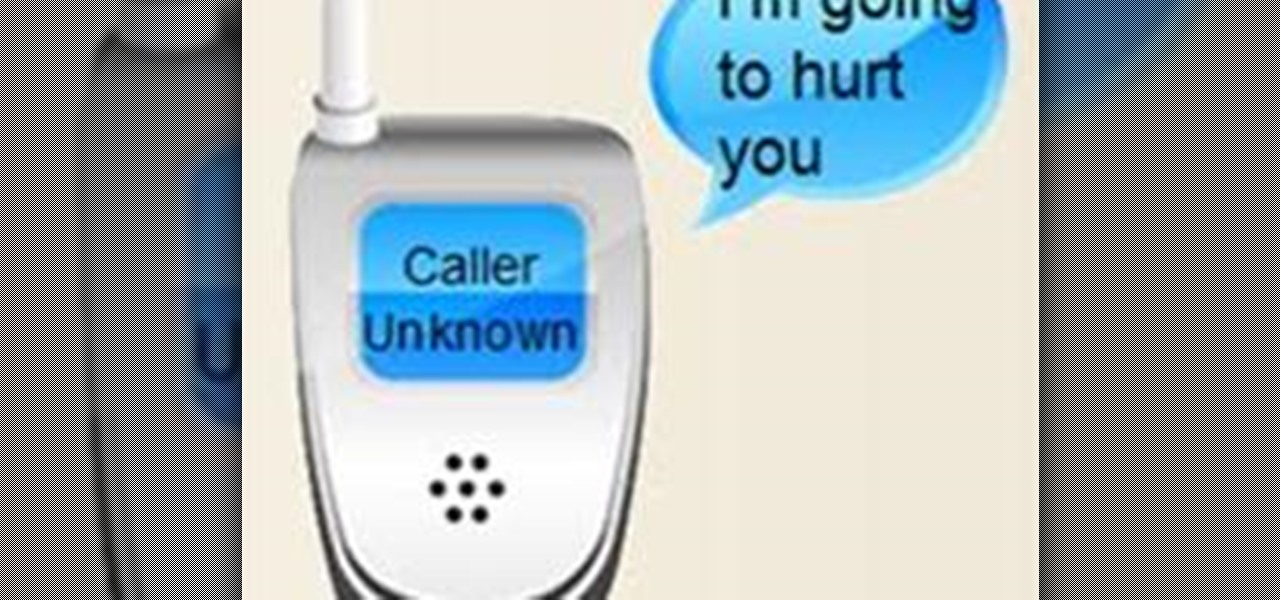
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

Downloading images from Google Images search can be a time consuming and DANGEROUS process. On more than one occasion, while trying to save the full size image and being forced to the originating website, I have accidentally come across malicious websites.

Originating from the middle east and India, threading is the ancient art of hair removal. With only some cotton thread, this video will show you how to create your own threading instrument. Create a threading instrument to remove hair.

Shinya Kimura is an artist. And his art is the motorcycle. Though a legend in Japan for some time now, the motorcycle engineer first came into the American public eye as a contestant on Biker Build-Off, a Discovery Channel channel show featuring custom bike builders. Kimura has been accredited with originating the popular, vintage style trend of customized bike building (think Pimp My Ride meets retro Harley Davidson).

In this tutorial, we learn how to find an IP address in Hotmail. First, open up your Hotmail in box and right click on the email you want the IP address of. Now, select "view source" and find where it says "received: from" or "X-Originating IP". This will give you the exact IP of where this email was sent from. You can use this for any email you receive and the best part is that it only takes a few simple clicks of the mouse and a few seconds out of your day! This can help you bump up securit...

One of the creepiest musical instruments ever is undoubtedly the theremin, a device originating from the early 20s that emits eerie sounds with a just a wave of the hand. If you've seen the original movie The Day the Earth Stood Still, you know what I mean—freakishly creepy. Playing the theremin can be off-putting for some, since it's a relatively pricy gizmo, but a new geek gadget called the EaTheremin aims to make all of us professional, dinnertime theremists.
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States

Snapseed is a highly regarded and award-winning photo-editing app for iOS devices. Originating out of image manipulation specialist Nik Software in San Diego, Snapseed is Apple’s iPad App of the Year and, after using it for the purposes of this review, I believe it points to the future of image editing.

On a Wednesday evening when friends are going to a movie or out to dinner, you’re at the dojo training.

I've been curious to watch one of these famed '3D' games for a while now. Last April at NAB, I attended several 3D panels and folks from ESPN suggested that one of the strongest experiences that would bring 3D into the home would be live sports. I've missed opportunities to watch the PGA Masters broacasts, and NCAA games, but being a hardcore Soccer (Futbol) fan, I've been most excited about this possibility. It did not disappoint, but not without some concessions. I will be as detailed as po...

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Originating from the middle east and India, threading is the ancient art of hair removal. With only some cotton thread, This video will show you how to remove leg hair by threading.. Thread leg hair.