Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

While VR promises to take gamers to another world, AR has the potential to bring the game elements into your own neighborhood or home.

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Respiratory Syncytial Virus (RSV) is the most commonly occurring lower respiratory tract viral infection in young children and usually isn't serious, but in premature infants and babies under six months old, the infection can be severe, and even fatal.

Obstetric tetanus in an unvaccinated Amish woman after a home birth has emphasized the need for preventative healthcare.

There are rules that cooking in general always follows: cakes should be fluffy. Steaks should be heavily seasoned, and nowhere near a bottle of steak sauce. Every stock should start with aromatics (onions, carrots, & celery). And, until very recently, meringues should always be made with egg whites.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

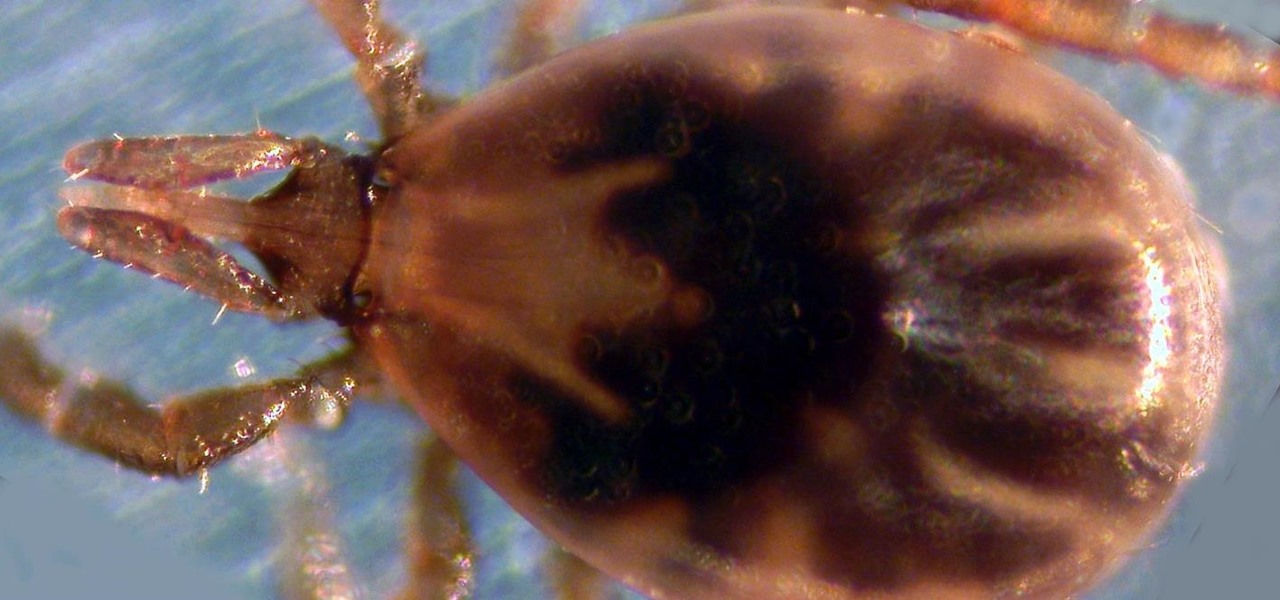
Primarily caused by the bacteria Borrelia burgdorferi, Lyme disease is the most common tickborne disease in the US. By all predictions, 2017 is expected to be a banner tick year in several regions. If you have children, it is important to know what to expect.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

With a predicated increase in the number of Lyme disease cases in the coming spring season, new research endorses the use of bait boxes to control ticks on the rodents that serve as their hosts.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

Thanks to the COVID-19 virus, the whole country is staying home. That means no dining out, no going to bars, no live music, and, sadly, no movie theaters. While you might think that means you'll have to wait to see movies like "The Invisible Man," "Emma," and "The Hunt," think again. Because of the pandemic, you'll be able to watch these movies on your phone earlier than ever.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

Growing populations and higher temperatures put pressure on world food supplies. Naturally occurring soil bacteria may save crops in drought-stressed areas, put more land into crop production, and produce more food.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

By looking for the mechanism that allows influenza A to invade lung cells, scientists also discovered a treatment that might block the virus from taking hold there.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.