Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Apple continues to suffer production delays caused by COVID-19 era factory closures, and the products taking the biggest hit are its customized 14-inch and 16-inch MacBook Pro configurations. Long story short, you'd be lucky to get one of those 2021 MacBook Pro models by the end of June 2022.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

The economic impacts of the COVID-19 pandemic have been felt in practically every business sector. Now, as we look back at the top augmented reality investments of 2020, the AR industry has been no exception.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Plantar warts are non-cancerous growths that can be found on the heel or ball of the foot, and in some cases, even on your fingers. They most often are very painful and are hard to get rid of. Most removing methods can be very painful and uncomfortable.

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

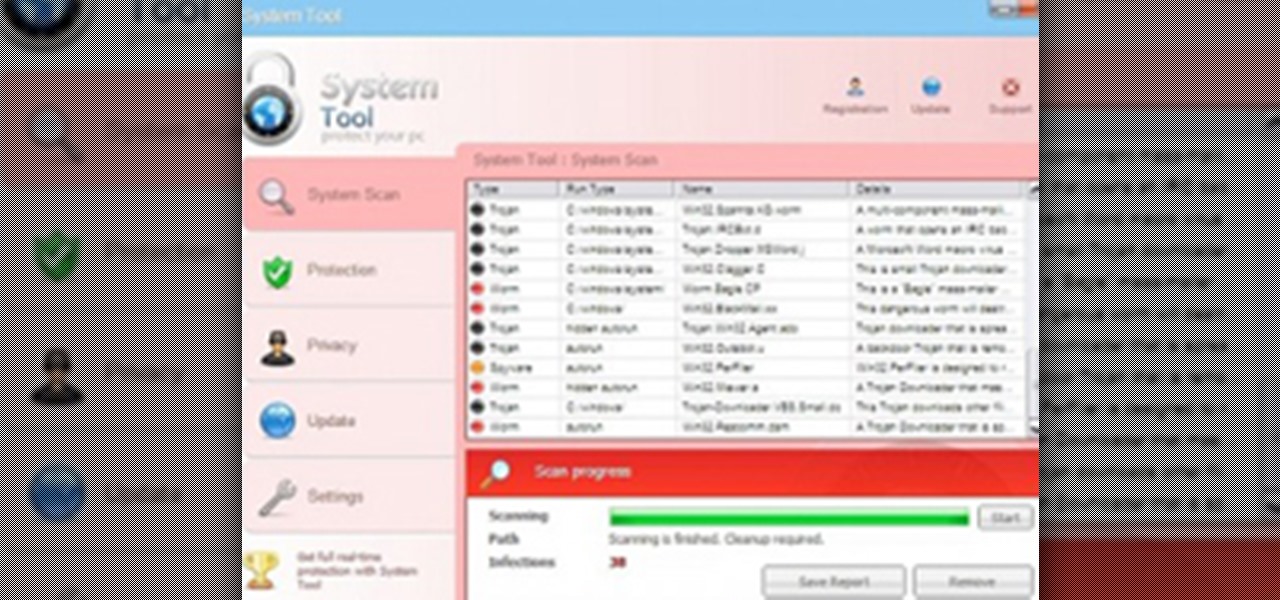
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

As a follow-up to an earlier post on surviving deadly animal attacks in the wild and another one on relieving a jellyfish sting, listed below are things you should do (and shouldn't do) if you are ever bitten or stung by potentially poisonous wild animals.

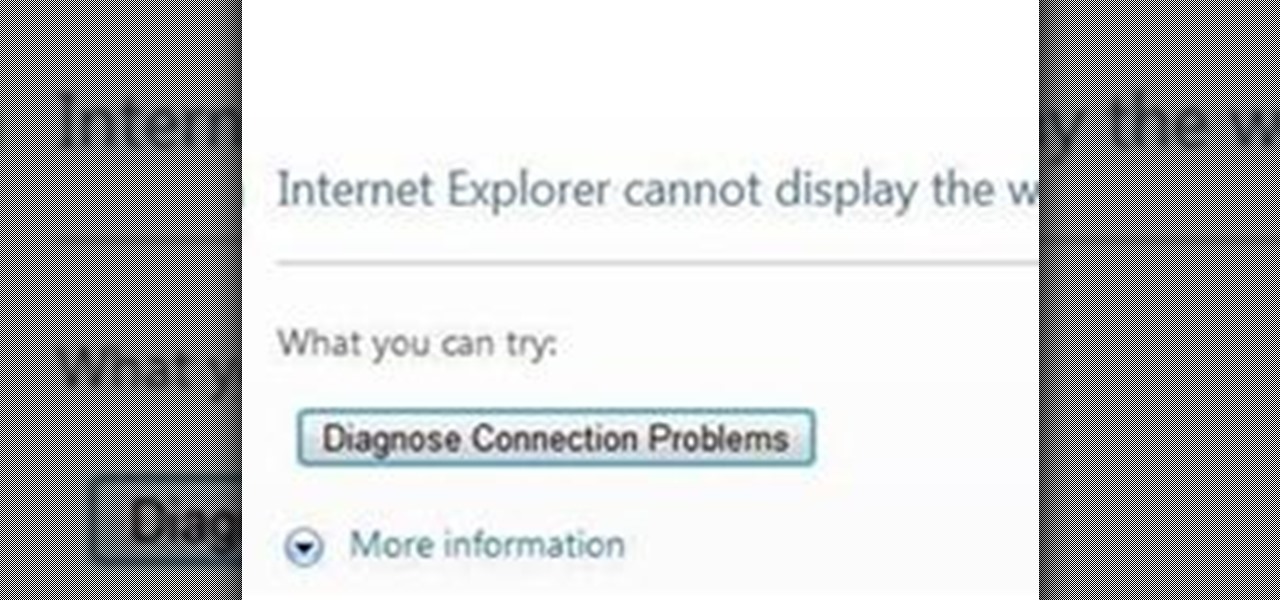
The executable file association virus deletes the "Regkey" that associates ".exe" files with the proper Windows execution. The virus can be contracted while browsing the web, from an infected file, or even from pictures and documents. Once the damage is done, Windows will show a window similar to the one below, and will ask you for the correct program with which to open the file.

Are your sinus problems getting in the way of your life? Dr. Oz of Real Age Videos provides an informative, animated video that unravels the mysteries of infected sinuses. He explains the physiology of the sinuses, and details the possible causes of sinusitis and its common symptoms, including colds and allergies. This video offers a few suggestions about current methods of medical treatments to alleviate this troublesome malady. It explains how the Balloon Sinuplasty procedure can provide ef...

Stay off the streets, lock your doors and grab your shotguns, because zombies are infecting the world over. Well… this Halloween season anyway. With the return of The Walking Dead to AMC a couple weeks ago and the subsequent renewal of a third season, it just goes to show that the undead cannot be killed.

Diseased Pariah News is a zine for and about people with HIV. It is "a patently offensive publication of, by, and for people with HIV disease (and their friends and loved ones). We are a forum for infected people to share their thoughts, feelings, art, writing and brownie recipes in an atmosphere free of teddy bears, magic rocks, and seronegative guilt." Started in the 1990s, it's up to 11 issues, 8 of which are viewable and downloadable online. It's marked by its trademark dark humor and hon...

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

So many people have searched for bypassing the time limit on Google for sites like videobb and VideoZer, I figured it was time to tell people the easiest way to bypass those 72-minute time limits without downloading any software from third-party sites. This is a very easy guide on how to use a website to bypass time limits.
Ron Paul Republicans take over Nevada GOP

If you're into entomology, then you probably recognize the name E.L. Trouvelot. After all, he was the person responsible for the outbreak of invasive gypsy moths in North America, which are now one of the most destructive foliage-eating pests in the United States.

This is a fascinating exploration by a New Hampshire public health group. Their only known function is to teach people how to properly sneeze.

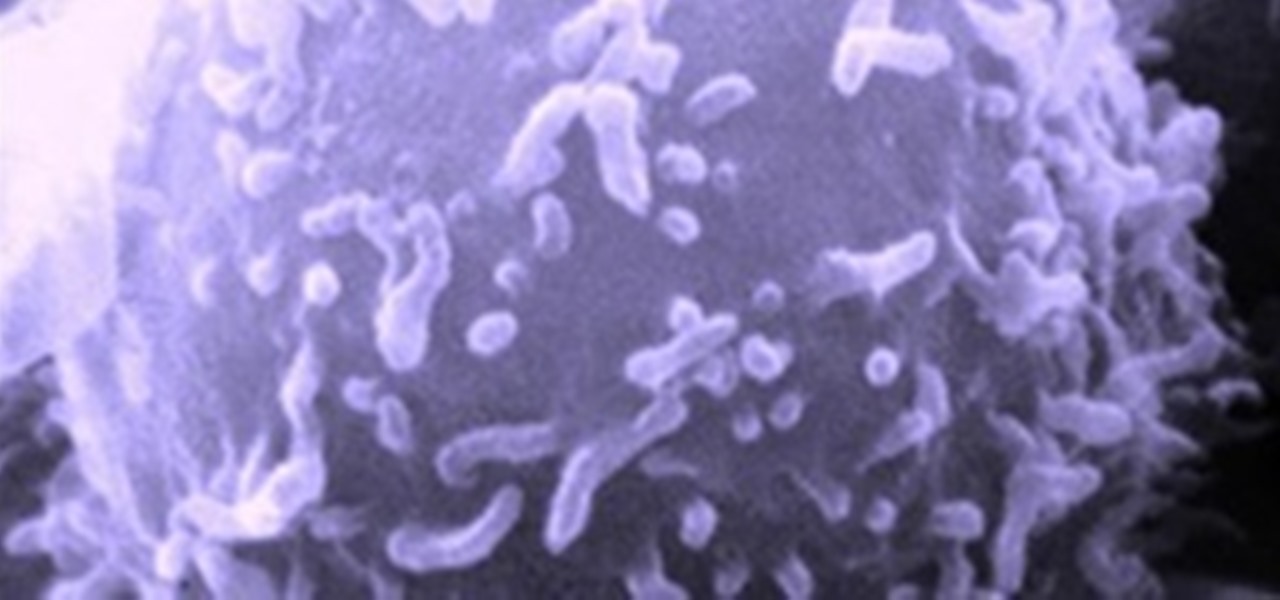
The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

What should you do in case of a major zombie outbreak? Many of the best survival techniques follow the same logic as to how you should prepare for major natural disasters; stock up on food and medical supplies, have an escape route, and form a community of people you can work with. When you're dealing with the flesh-eating undead, it also helps to invest beforehand in full body armor, weapons, and basic parkour lessons so that you know how to scale walls and jump across buildings when a horde...

In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

Could the world really be coming to an end tomorrow? Presuming you believe the biblical prediction from 89-year-old Harold Camping, May 21st, 2011 is undeniably Judgment Day. If you have confidence in that prophecy, you're probably not even reading this because you're too busy either A) preparing for the Rapture or B) sitting in your backyard bunker hoping to outwit annihilationism.

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.