Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announcements on the horizon.

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Within the gastronomic melting pot of America, pizza was first introduced in the late 19th century by Italian settlers in cities like New York, Chicago, and Philadelphia. The slice-by -slice phenomenon gained popularity when immigrant street peddlers walked the sidewalks with aromatic, sweet-smelling pies held in metal washtubs.

If you spend a lot of time reading about food, chances are you've heard about bone broth. It's all the rage these days, from high profile chefs like Marco Canora building menus around it, to celebrities like Salma Hayek using it as self-prescribed beauty regimens.

Fresh, homemade pasta definitely beats the dried stuff from the store. However, most of us aren't usually in the mood to knead dough for 10 minutes... or to clean up a sticky, doughy, floury mess afterward.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

If I could survive on one food for the rest of my life, it would be pizza. The irresistible smell of baking pizza instantly makes me feel both comforted... and hungry!

Lemons, limes, and even oranges compliment a wide variety of both food and drink: gin and tonic, poached salmon, shrimp cocktails, fajitas, and so on. And you can easily step up your hosting game by making citrus garnishes: a presentation that is both elegant and interesting.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

Sangria... the elixir of summer. When properly prepared, there are few things more refreshing and magical. If you're looking for a way to mix things up and "get out of the bottle," try one of these lovely libations before the warm weather ends: peach-mango sangria, pineapple-basil sangria, watermelon-raspberry sangria, or blueberry-plum sangria.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

Summer's coming, and that means burger season. Okay, never mind... every season is burger season. Burgers are universally loved; they're the one meal you can find at numerous fast food shacks and haute cuisine spots.

Contrary to popular belief, sushi is not the raw fish that one gets at Japanese restaurants, but the rice that comes with it. It's hard to tell whether this popular misconception led to or came about because of the primary flavors that we think of in sushi are the fish. We often say a sushi restaurant has great fish, but almost never that it has great rice.

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Lemons and limes might be among the most useful fruits in the kitchen and even beyond. Their bright, tart flavor livens up just about any dish, while their mildly acidic nature makes them incredibly useful when you want to clean your house safely. We already knew lemons were great for keeping fruits and vegetables from turning brown, deodorizing garbage disposals, disinfecting cutting boards, and neutralizing odors. But just when we thought we knew all the ways that lemons can be used around ...

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

We've all been there. You can't decide what you want to eat and, even more confusingly, you want two distinctly different things, whether it's sweet and salty, Chinese and, well, cheese. Chances are when you're in this state of indecision, you also want to make this mythically satisfying meal really, really fast.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

If you've got a birthday party to plan for a young budding scientist coming up, a little nitrogen should do the trick. In this project, I'll show you 10 "super cool" tricks with liquid nitrogen that you could try, but probably shouldn't!

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.

What happens when you find your ball deflated and there's no pump or needle in sight? You could always cancel your plans of kicking around the soccer ball or starting that pickup football game in the park. Better yet, you could be terribly clever and find another way to get air into the ball. From a pen to a balloon to a gas station, there are ways to inflate it.

There are quite a few flaws with Apple's mobile products, and one that drives me crazy is their reliance upon iTunes for all your music syncing needs. If you want a song on your iPhone, you pretty much have to use iTunes to get it on there. Either that or buy it directly from the iTunes app on your device.

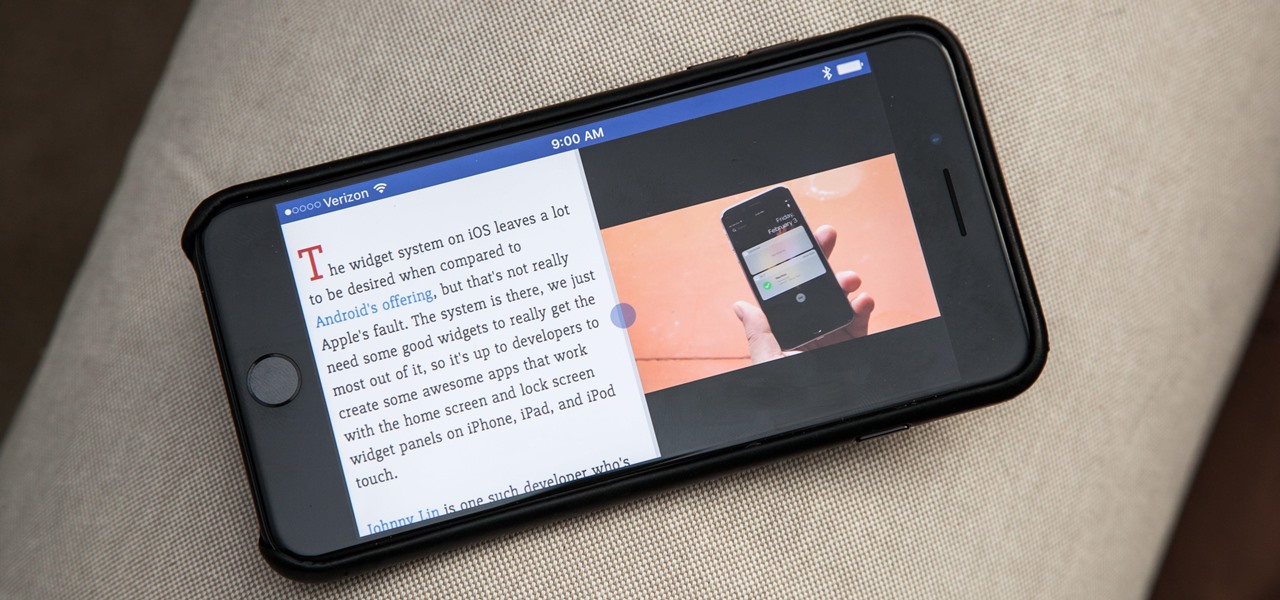
The iPhone has come a long way in its ten-year lifespan, but one thing still missing from the core user experience is native split-screen support. Sure, the displays on iPhones aren't nearly as large as an iPad's screen — which does offer "Split View" mode out of the box — but the iPhone 6 Plus, 6s Plus, and 7 Plus are definitely big enough to use two apps at the same time.

I chose to make this a Steampunk iPad case, but you can change the details and make it look as modern as you'd like. As I said earlier, Steampunks probably shouldn't buy iPhones or iPads, but if you're going to get one, you may as well make it look cool, right? The iPad pictured below was borrowed from a friend of mine, though I should add that this design will easily work with tablet computers of any variety, Apple, Android, or otherwise.

I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept.

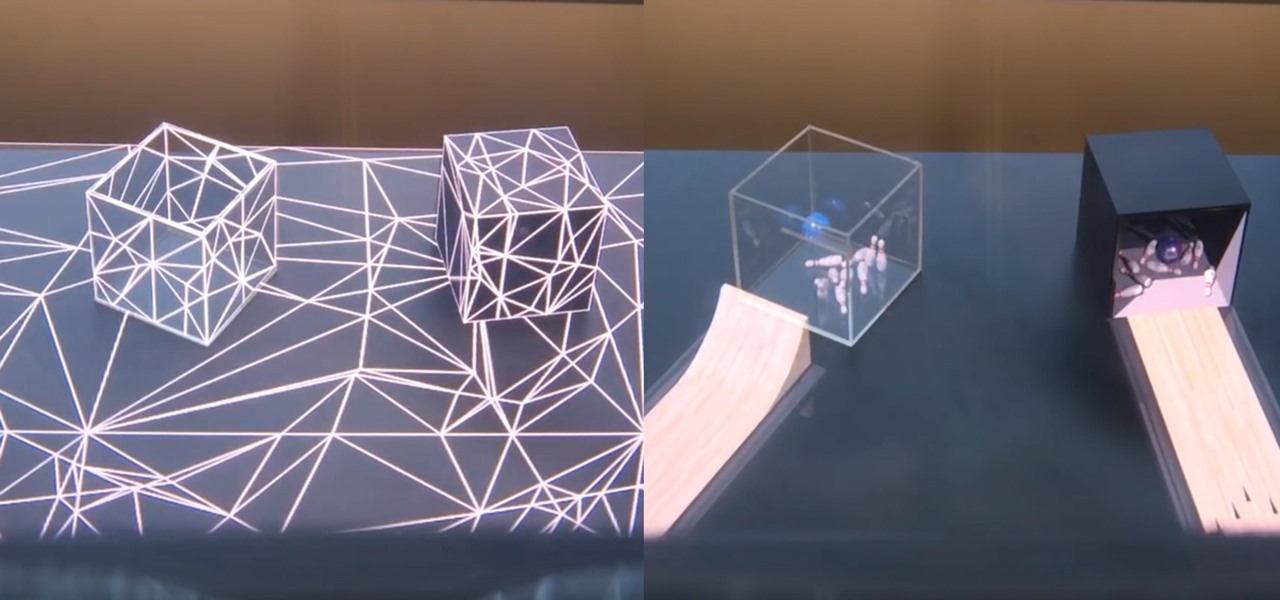
The legal battle between Epic Games and augmented reality startup Nreal isn't cooling off anytime soon.

The Lens Studio creators have published more than 1.5 million AR effects to Snapchat. One of them is Audrey Spencer, who shared her story with us and provided her insights into Lens Studio as a storytelling device. Meanwhile, Snap has added new capabilities to the platform to stoke more creativity from its creators.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.