
Hacking macOS: How to Create an Undetectable Payload
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.


Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Hello friends. This is actually my first how to.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.
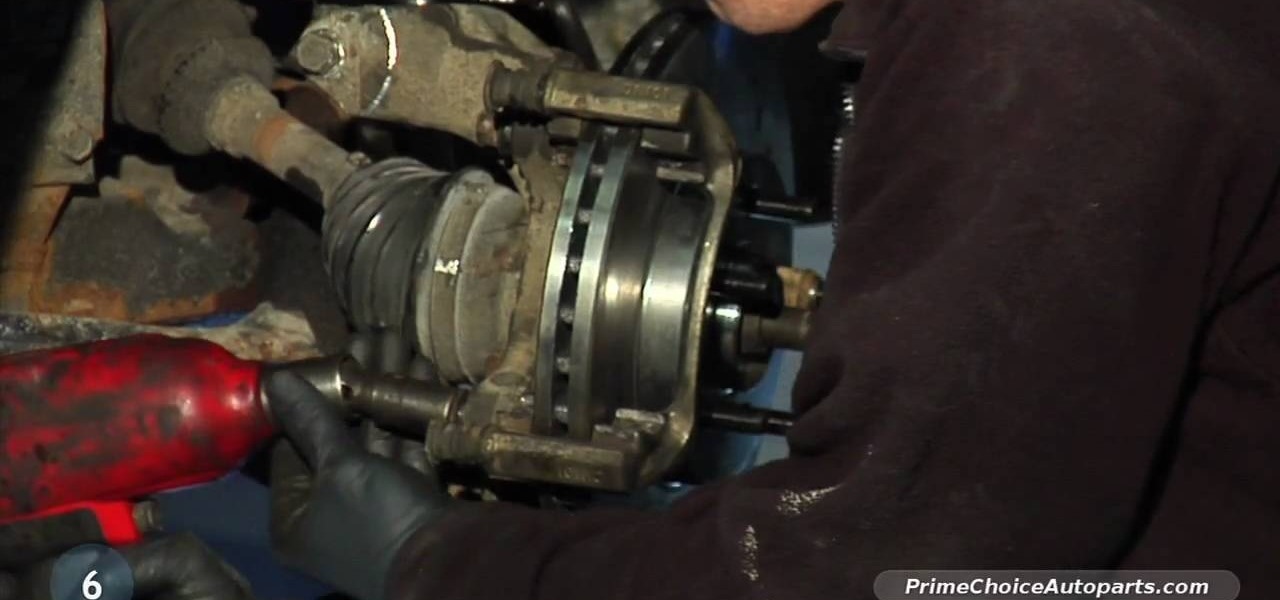
In this automotive repair video, you'll learn how to change your own brakes. Throughout this process, you'll also figure out how to remove your tire, calipers and brake pads, and how to clean the brake pad area. See how to take off the rotor and reinsert everything correctly. It's an easy process, and you don't need to be a professional mechanic to install new brake pads.

This video will help you learn how to create an Explosive rainbow color swath in Photoshop. First open a new file, keep the width 845, height 475, RGB color mode and white background.
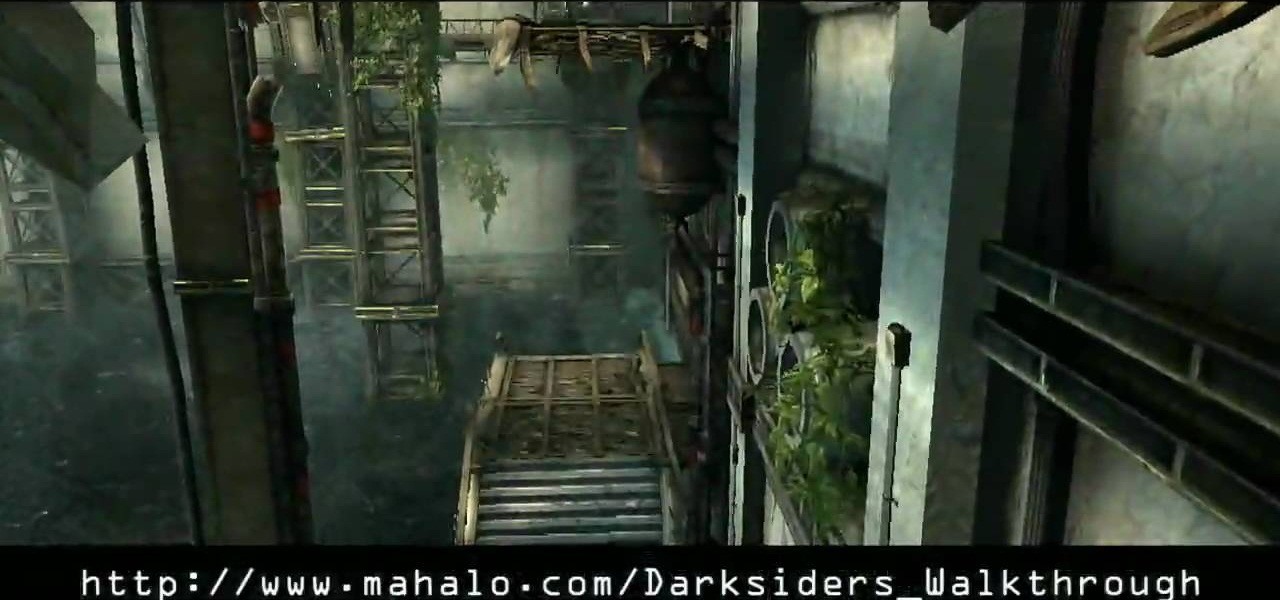
There's plenty of action on this level of the Xbox 360 game Darksiders. In the Hollows, there's Gas Mains, Tremor Gauntlet, Three Platform Room, Turntables, Pump Room, Griever, and Chronomancer. You enter way looks to have once been a train station. As you approach the Redemption lying on the ground you'll be ambushed by the Griever. Quickly pick up Redemption and begin to alternate between rapid fire shots and charge shots. You need to aim for the blue glowing belly of the monster. Dash arou...

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

Learn how to use a medicine ball to do a squat thrust with a wall rebound. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do hold a squat while doing a power single cable wide pull down. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do speed full sit ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

This software tutorial shows you how to create good renders from 3ds Max 8. It's one thing to create cool models in 3D Studio Max but if you can't get the lighting right and output a good render, then it's pretty useless. So watch this tutorial and get tips on creating a good render in 3ds Max 8.

This tutorial is for ultra beginners in .NET, it shows how to create a simple console output and simple form in VB.NET and C#. It is done through notepad and without any IDE.

Keeping up with a yoga or any other routine can be difficult after a serious injury. This how to video demonstrates how to do a sun salutation when you have a broken foot. Avoid applying any pressure with these strategically choreographed yoga poses.

In this video we show you how to repair a basement wall that has started to push inward due to soil and water pressure.

In order to make a Pandora's Box, you first need glossy paper. The paper should basically be in the shape of a square, length 15 cm one side. Then divide the paper into 5ths. Now make 5 such folds on the paper and be sure that every fold is equidistant. Similarly, turn the paper around and start folding it from the other side too, in the same fashion. By doing this you will realize the folds have resulted in equal, similar sized boxes on the paper, 25 in total.

Jennifer Pompa suggests that the 20" easiXtend Elite is the extension to start with. It's an 8 piece extension made with human hair that's not been too processed and so looks very natural. Jennifer is wearing a Kim Kardashian look with flowing curls. The extensions can be purchased as Extensions. Blow dryer, flat iron or curling can be done to these extensions because it's real hair. The extensions come in many colors but also can be dyed to match your hair. To remove them, Jennifer unclips t...

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Lose weight while sitting on the bus, train, or in your car with these stealthy moves. You Will Need

If it's all you can do to drag yourself through the day, why not increase your stamina with these time-honored techniques. Watch this video to learn how to boost energy naturally.

Learn how to massage your dog. Man’s best friend gets stressed, too! A massage can benefit your dog’s health as well as their mood.
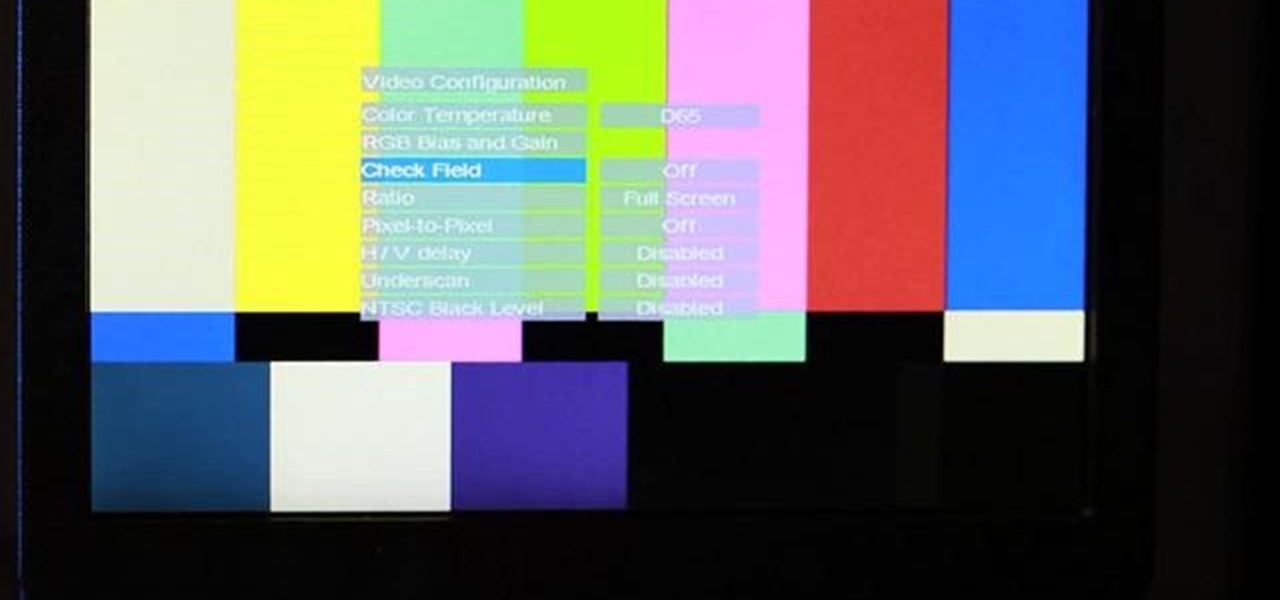
Check out this cinematography video tutorial on how to use calibrate an NTSC camera monitor, specifically a Marshall monitor.

This instructional yoga how to video demonstrates how to do an advanced yoga sun salutation called sundance of koundinyasana.

Dhokla is a gujarati snack item traditionally made from rice and daal. Try this super simple, super quick recipe using sooji (suji, semolina or cream of wheat). Watch this how to video and learn to make Instant sooji dhokla, serve with tea and impress your guests with your Indian cooking.

Learn how to squats and plyometric jump squats. Presented by Real Jock Gay Fitness Health & Life. Benefits