This video shows an updating of the famous Magdeburg experiment carried out by Otto von Guericke in 1654 using two metallic hemispheres to show the effects of atmospheric pressure - try it for yourself!

If you’re a dancer, athlete or just breaking in a new pair of shoes you know that blister can add pain and discomfort long after they’re formed. By keeping a blister sterile and away from further friction you can get your blister to heal quickly.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Access your computer's BIOS settings
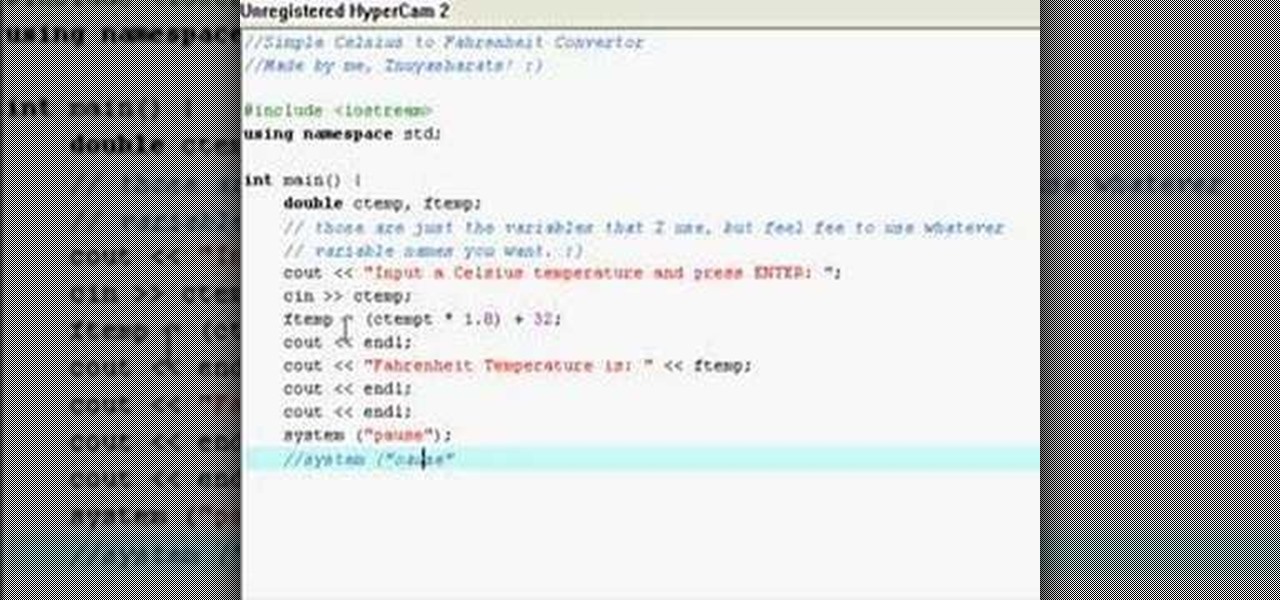
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

First you need a CRT TV, one Laptop, Headphone jack, Male and Female RCA jack, and output and input male female jack. And than one is audio cable and another one is video cable, and than connect it to your TV video out and audio out, and another one are connect to Laptops video out and audio out. And to get the video quality is good let set the Graphics property on your laptop and there are one option to TV set graphics and set them. And set the Screen Resolution and video stranded, and then ...

See how to use Wondershare DVD Copy to copy and back up DVD's on a Mac. DVD Copy for Mac is a professional DVD copy program designed for Mac OS users to copy D9 and D5 DVD movies. It can copy your DVD with the original quality 100% preserved and at the same time remove DVD protections such as CSS, RC and RCE.

Check out how to back up and copy DVDs on a Mac with iSkysoft DVD Copy. Mac DVD Copy is a fast and easy-to-use Mac DVD burner and Mac DVD copy software which can Copy DVD to DVD, such as D5 to D5, D9 to D9, and D5 to D9.

Wouldn't the rubber bands eventually provide enough pressure on the light bulb to make it shatter? You would think so, but after watching this video by Nextraker, you'll see that gently wrapping an ordinary lightbulb rubber band after rubber band, until completely covered (and then some), does not break the bulb. Even when you throw it on the ground. It's just like a bouncy ball. Now… try this with an egg. Dare you.

Learn how to hold a golf club properly in this sports video tutorial. The first thing is to allow the handle of the club to lie on the fingers of your left hand. It should lie diagonally. As you close your hand around the grip and lift the club off the ground, you should have a sensation that the handle is underneath the back of your palm and the last three fingers are applying pressure and squeezing it into your palm. The second step is to put the right hand on the golf grip in a diagonal li...

Kevin Battersby of Battersbygold explains the proper way of cleaning rubber or leather golf club grip, important for having a having more control of the club.

In this tutorial video, hosted by harrymedan, you will learn how to fix a broken or nonfunctional select button on your iPod, as well as the common causes of the select button no longer working. According to the host this problem is usually caused by the battery in the iPod itself. He suggests opening up the back of the iPod and replacing the old battery, which is usually swollen from being charged so many times, and puts pressure on the select button causing it to become inoperable. If you a...

If you ask Apple Support if the 18-watt power adapter that came with the iPhone 11 Pro, iPhone 11 Pro Max, and four different iPad models will work with the MagSafe Charger and your new iPhone 12 or 12 Pro, the answer is "yes." But that's not the whole story.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Samsung has just announced the Galaxy Note 10 and 10+. These are the latest and greatest from the largest smartphone OEM in the world. Plenty of numbers and specs have been thrown your way to showcase how good the Galaxy Note 10 is, but we wanted to simplify all this for you and key in on the most important things.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

If you recently received your new Galaxy S9 or S9+, you're probably excited to try out all of the features the flagship offers. While many of the features are self-explanatory and easy to access, there are a handful of very useful items that Samsung has buried in the settings menu. Enabling these hidden features will help you unlock the true power of your new device.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

A new iPhone is only as good as its accessories. Whether it's a case, screen protector, or charger, your iPhone's ecosystem depends on accessories to keep it powered, protected, and personal. Prices on all of these extras are going to be at an all-time low this Black Friday weekend, so we've rounded up the best deals around to help you get the essentials you want and prices you can afford.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Learn how to clean your auto engine with these great tips. • Apply spray wax to fenders to prevent spotting on the paint, from engine degreaser. • An alternator is a crucial electrical device which must be protected from water and other chemicals. as a precaution, cover it with a plastic bag and the distributor cap if it is visible. • Spray WD40 on any exposed wires to prevent water or chemicals from penetrating. • Wet underneath the hood; wet the engine; use low pressure water on the engine ...

Karthik Raj and Nishant explained about a air balloon car in this video. You just need 4 or more things to make the air balloon car. You need two rubber bands, one pen, two toy cars, and one air balloon exactly to do this air balloon car. First of all, you just take the air balloon and fix it one side of the pen which is opened two sides. Next place the pen on the top of the toy car and tie with a rubber band and make sure that the rubber band is in the middle of the toy care and not in the t...

This tutorial shows how to construct a mouth-launched air rocket. He begins with an ordinary strip of chewing gum. After removing the gun, he flattens out the wrapper. He then carefully wraps the long end of the wrapper around his index finger, leaving about half the wrapper protruding off the end of his finger. This creates a cylinder. Then he twists off the protruding end tightly and pulls it off his finger. To launch the projectile, he puts the rocket between his lips and blows. This desig...