
How To: Make Mona Lisa's Eyes Blink in Photoshop (GIF Animation)
If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa.


If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa.

You can paint the Mona Lisa with Microsoft Paint. You start by drawing dots that you need to connect to make the face. Everything needs to be colored in by the end.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Want to play the All-American Rejects' "Mona Lisa (When the World Comes Down)"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and it chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing this song on your own guitar, take a look!

This Mona Lisa necklace is really as unique and charming as it gets. Why wear the same old stringy bohemian necklace as everyone else when you can fabricate your own neck wear using vintage brooches, brass stampings, and other found knick knacks?

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to talk about group competition games. These make the party worth while. For example; if you have let's say about 14 party guest, you can divide them up into groups of 2, put 7 in one group and 7 in the other and have a different activity for each group competition. Let me show you an example. I purchased this bag of straws, M...

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

Learn how to care for your pet with help from VetVid. See how to test, diagnose and treat oral squamous cell carcinoma in cats.
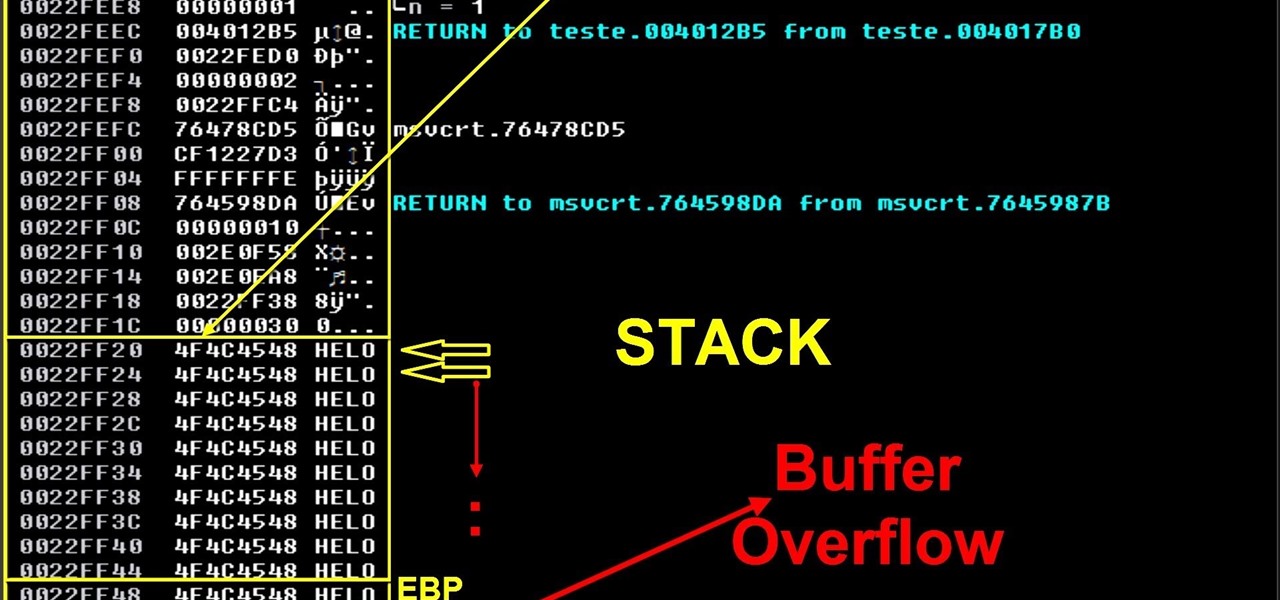
On this video I will demonstrate a simple concept of stack base overflows. This is the first part of my exploit development tutorials and after that I will demonstrate seh buffer overflow, ROP/DEP/ASLR, spraying the heap, search for bugs/think different etc.

You may or may not have heard of alt-rock band Panic! at the Disco, but a year and a half ago they released a single called "The Ballad of Mona Lisa", which had an accompanying music video that was Steampunk-themed. In fact, here's the video:

Mona from Cup Cakes Creations demonstrates the use of a Cricut Expression machine to make gift bags. She starts with the smaller gift bag found on page 115 of the instruction book. It gives the option of putting holes in the bag. She sets the machine to cut two 5-1/2" bags out of 12x12" paper, and cuts it. With the bag cut out, she explains how the bag is folded and taped with Terrifically Tacky Tape, and decorated with a 2" tag. The tag is attached with a cord, and decorated with a ribbon. T...

Many ways to help the environment are costly, but using less electricity is one measure that will save you money. Learn how to lower your electric bill with this how to video.

Some women see Halloween as a once-a-year opportunity to dress in something skimpy without dealing with as much scrutiny as usual. That can be fun, but not everyone is comfortable enough wearing so little, and the costumes are so boring and repetitive. Some of us just don't feel like freezing.

Learn how to care for your pet with help from VetVid. See how to diagnose and treat mast cell tumors in dogs.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

Learn how to care for your pet with help from VetVid. See how to recognize mast cell tumors in dogs.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

During the opening keynote of their Worldwide Developers Conference today in San Jose, Apple introduced the ARKit for the new iOS 11 that will bring augmented reality apps to millions of compatible iPhones and iPads.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

In this series of cooking videos you'll learn how to make a quick Indian meal from expert Mona Sishodia. She demonstrates how to make vegetable curry, batter-dipped and fried vegetables called Pakora, and a stuffed potato tortilla, which is a variation on a staple of the Indian diet. Mona takes you through the recipe step-by-step, explaining the ingredients and spices you'll be using and some of the health benefits of spices commonly used in Indian cooking. She shows you how to make dough for...

Looking for a few new April Fool’s Day pranks? You’ll be sure to get a startled look on friends faces when you catch them off guard with some unexpected alterations to their favorite foods. Just remember that what goes around comes around.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

In the tech world, when you're a small startup going up against the Goliaths and their massive marketing budgets, you're forced to find and produce something almost magical to help your product stand apart from the rest. And that's exactly what Occipital Inc. has done with their Bridge headset.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.
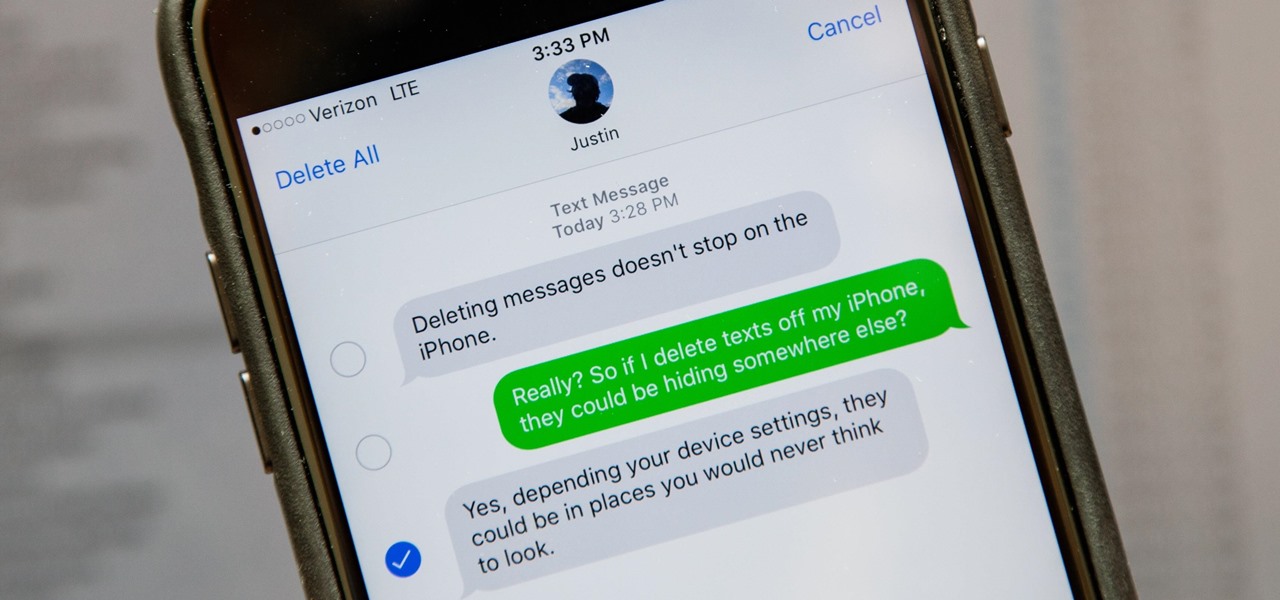
Deleting text messages on your iPhone may seem like a pretty simple task, but it's those really simple tasks that usually end up causing headaches later on. Data can stick around, even if you asked it not to, so there's always a slight chance that embarrassing and incriminating texts you supposedly deleted may end up in the wrong hands one day.
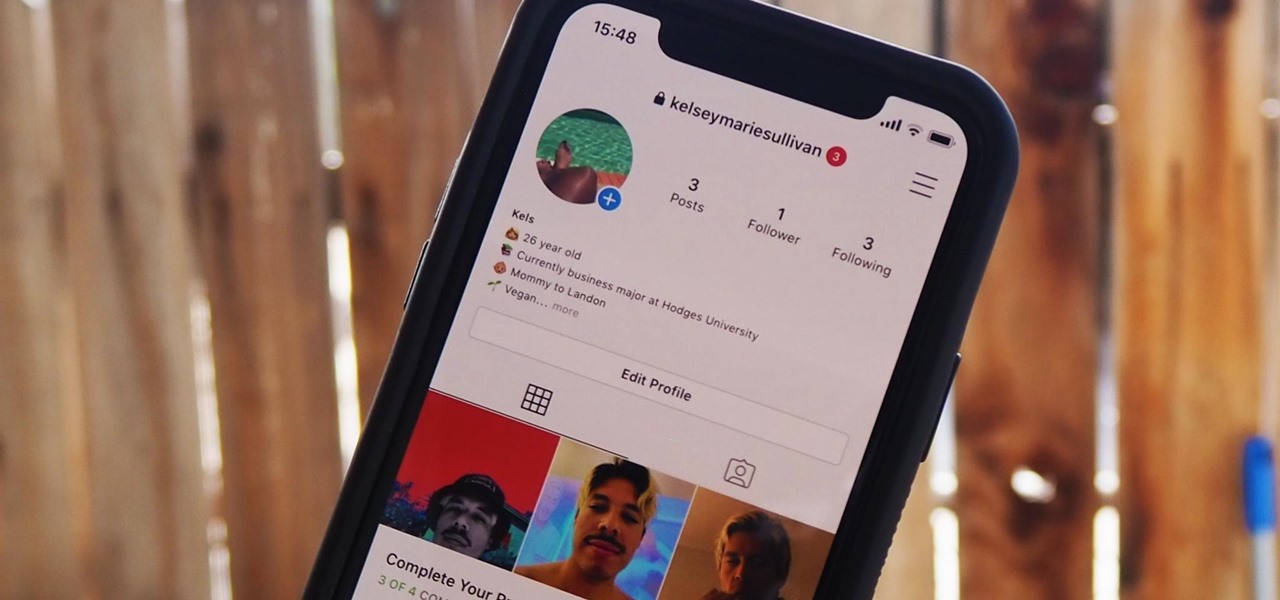
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.