The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

Learn how to practice quick decision making (pass or shoot) when on the high post and establish good basketball game rhythm. Videos two through four cover when and how to execute each option: jump shot, seal the post (pass the ball down to the player at the low post), and swing the ball (after setting the pick and sealing the post).

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

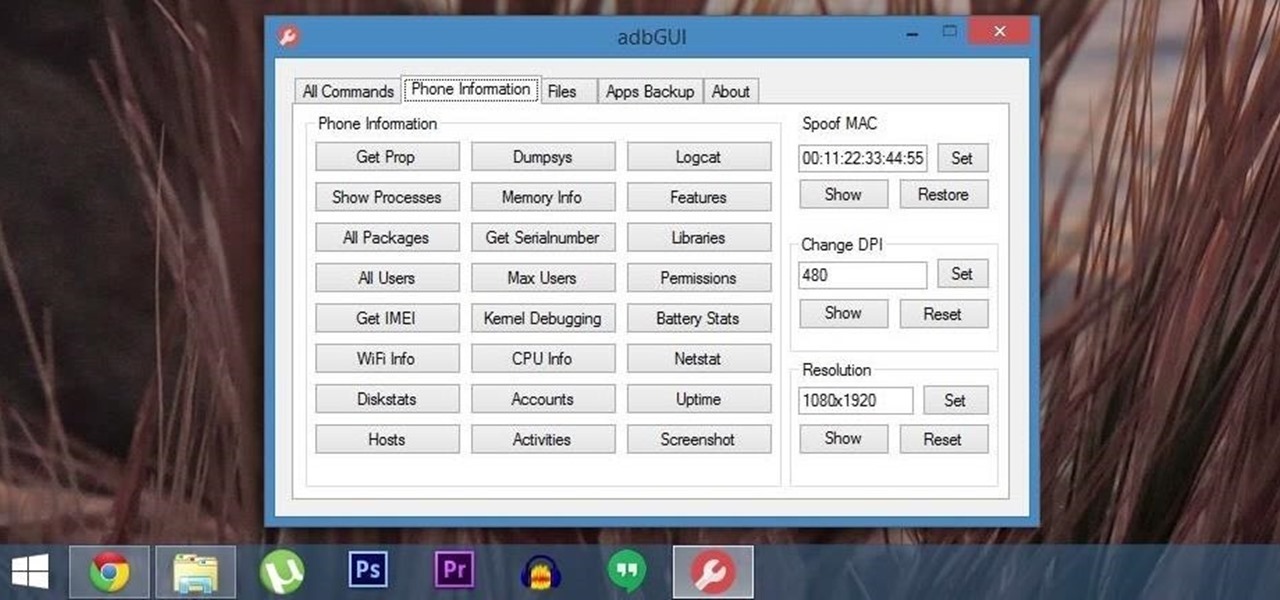
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

If you forgot about April Fool's Day, you're going to have to get creative if you want to pull off some not-so-predictable pranks last minute. To help you with that, in this video you'll learn how to set up and execute 5 of the best last-minute April Fool's Day pranks. April 1st will still be a fun day for you, your friends, and family... just watch!

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

Ah, Halloween—the funnest, but scariest day of the year. You don't just dress up and go door to door asking for candy—it's the best day to pull off scary/spooky pranks.

kicks since they require greater balance and strength than basic kicks. Learn kung fu jump kicks in this free video series on kung fu training.

Kung fu is an ancient Chinese martial art that involves using powerful punching techniques. Learn several punching combinations from a professional kung fu instructor in this free video series.

Aikido has countless wrist grab forms and techniques for any method of martial arts self defense someone might need to call upon. Learn many of these tips from an Aikido expert in this free video clip series.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Usually, when I see a video that is captioned "wait for it," I'm quick to dismiss what could possibly come at the end of the clip. In this case, however, I was totally wrong and the final result was definitely worth the wait.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

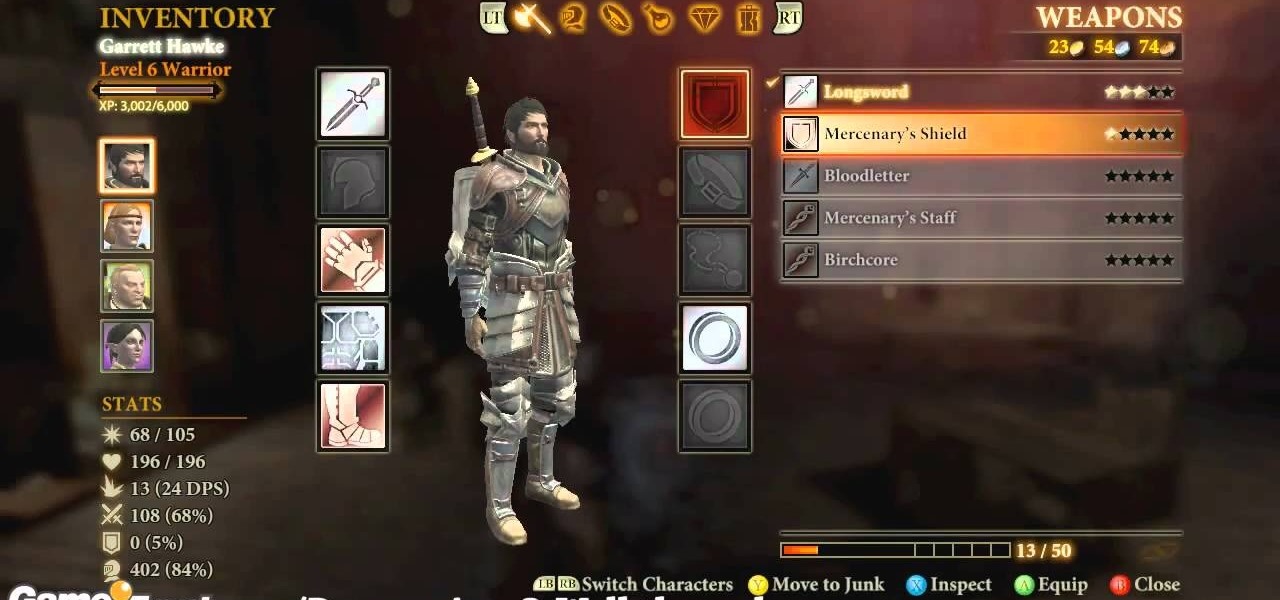
Dragon Age 2 seems to have more awesome and easy-to-execute exploitable glitches than any game in a long time. It almost seem deliberate, which would be a really awesome move on Bioware's part. This video will teach you how to use a really simple inventory glitch to max out any character's armor stat at 100% in less than a minute. You will be almost indestructible, and you can stop whenever you want if you just want a more reasonable boost.

To get the Guerilla Tactics achievement / trophy in Bulletstorm, you must execute 25 skillshots in a single Echoes map. Skillshots are the most fun part Bulletstorm. This video will give you a handy step-by-step guide to getting the achievement in Collapsed Building.

First, you will need a gallon of milk that's about a quarter full. It's best if you empty out the contents, but make sure to save it though because you will be needing it later.

Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps:

Snowboarding: Hit the Slopes With Style There was a time when simply riding a snowboard made you the extreme guy on the slopes. But now, with more people strapping on a board instead of skis, the stakes have been raised. Fortunately, we've lined up this video tutorial to keep you on the cutting edge. See how to perform an ollie on a snowboard.

Snowboarding: Hit the Slopes With Style There was a time when simply riding a snowboard made you the extreme guy on the slopes. But now, with more people strapping on a board instead of skis, the stakes have been raised. Fortunately, we've lined up this video tutorial to keep you on the cutting edge. See how to perform a frontside 720 on a snowboard.

Join professional skateboarder Ryan Smith as he teaches you how to perform a big spin on your board. This video tutorial will how you just how to do the big spin trick, perfectly.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Join Matt Null (NCA/Millersville/Cheer Excel), Lindsey (Fire and Ice Allstars), Carly (Seton La Salle HS), Greg (Step 1 Allstars) and EJ (IUP) as you learn how to load, set and execute a sponge to prep (elevator) to sponge. Great tips for the beginning cheer leading coach or cheerleader!