Join Matt Null (NCA/Millersville/Cheer Excel), Lindsey (Fire and Ice Allstars), Carly (Seton La Salle HS), Greg (Step 1 Allstars) and EJ (IUP) as you learn how to load, set and execute an extension with a cradle dismount. Great tips for the beginning cheer leading coach or cheerleader!

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Execute the 9th puzzle, called Hat Trick, in Assassin's Creed 2. Image 1: Move the cursor onto Houdini’s torso. Image 2: Move the cursor over Gandhi’s heart. Code wheel puzzle: Your hint here is pretty obvious; there’s a big, glaring “6=1” next to Oswald’s picture. So move the red wheel so that the 6 is over the gray 1, and plug in the corresponding numbers. For more info, watch the whole gameplay.

Practice What You Preach: Just make sure you know what you're doing. Return to Leonardo in Florence and he'll use your collected codices to give you some new skills. After the cut scene, look for the marker on your map that points you to a courtyard behind Leonardo's pad. There are three new stealth kills you've learned, and you need to practice each.

Have you tried working out with reverse curls? If so you know that they are an essential part of lifting weights and strength training. This fitness how-to video demonstrates work out the bicep muscle with reverse curls. Learn about curls and weightlifting exercises in this workout video.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

We recently covered an app called Fingerprint Quick Action that let you use your fingerprint scanner to expand your notification tray like the Google Pixel, along with a few other actions. It's definitely a useful mod, but there's a similar app can make your fingerprint scanner do almost anything—literally.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Learn in this video how to use XMLSpy to create and edit XQuery documents, debug them and profile execution speed and bottlenecks, and execute them against local XML data or XML stored on a database server. XML editing can't get easier then this.

Software needed: Voodoo motion tracker, virtual dub and blender

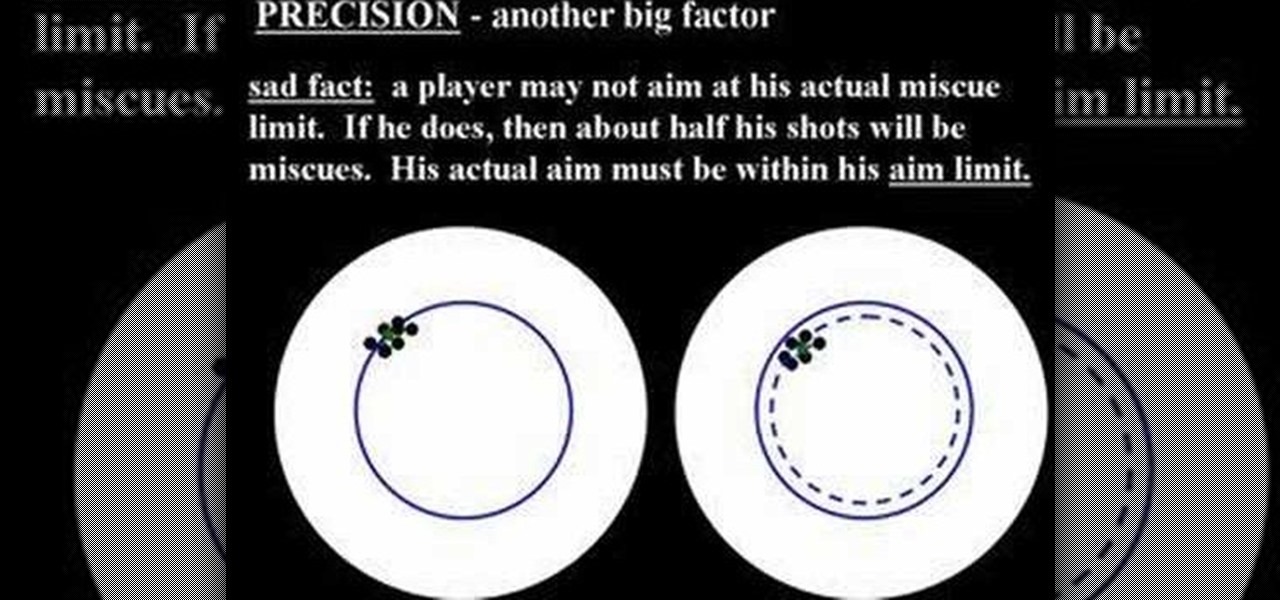
Cue ball draw refers to the way a cue ball strikes a rack of balls. In particular, if the cue ball is hit low on the ball, when it strikes a rack of balls, for the break, it will have enough backspin to wind its way back to the shooter.

Almost 125 million people worldwide suffer from what is known as psoriasis, the skin disease that's marked by red, itchy, and scaly patches that are hurtful, if not visually god-awful. There can be a little hope though for psoriasis sufferers. Though you can treat and control psoriasis, characterized by dry scaly patches of skin, the progress is often erratic and cyclical, so be patient and consistent in executing these steps.

Levi Meeuwenberg demonstrates how to do a parkour roll. First, practice the takeoff leap. Use forward momentum to jump out. Enter the landing leaning forward with the weight in front of your feat so you fall into the roll. Be physically and mentally tense and prepared when coming into the landing. Land with your feet parallel and square in the direction where you're heading. Keep your feet a bit less than shoulder width apart. Use a bend at the hips to complete the shoulder roll. Push against...

This video describes how to prepare for and execute painting your home. To begin, you should power wash your house to remove any dirt, dust, cobwebs, etc. These would prevent the paint from setting properly, unless it was new wood. If it is new wood, you should put on a beige coat first. However you begin, you should let either method dry before moving to the next step. After it dries, you should apply a weatherproof and paint-over caulk to the cracks to keep out moisture and insects. After t...

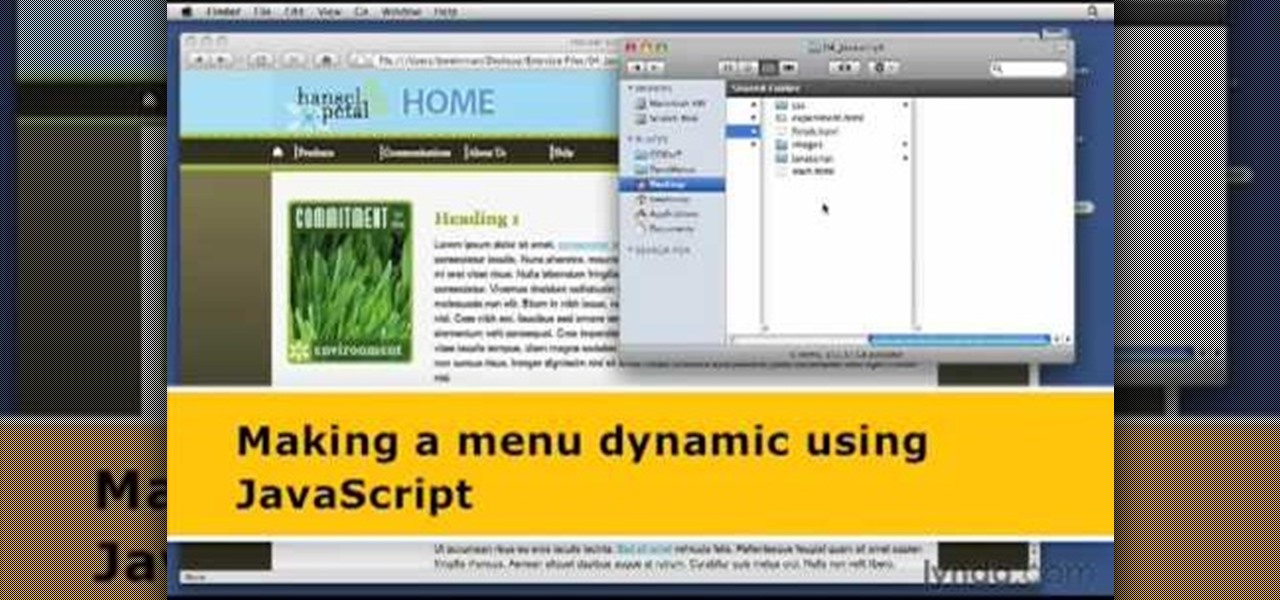
1. The following steps describes how to Create dynamic menus with html and Javascript. 2. Open the html file in Illustrator. 3. Enter the Menu.js file with <Script> Tag. 4. Create a Bulleted List of the Menus and Its Sub Menus inside a DIV Tag. 5. For Each UI List Create a Mouse over and mouse out Event for Header Menus. 6. For Mouse over Event call a Function named set Menu with MenuSubOne id as parameters 7. For Mouse out Event call a Function named named clearMenu with MenuSubOne id as par...

Show off your magic skills with a little preparation and an easy trick to execute. You Will Need

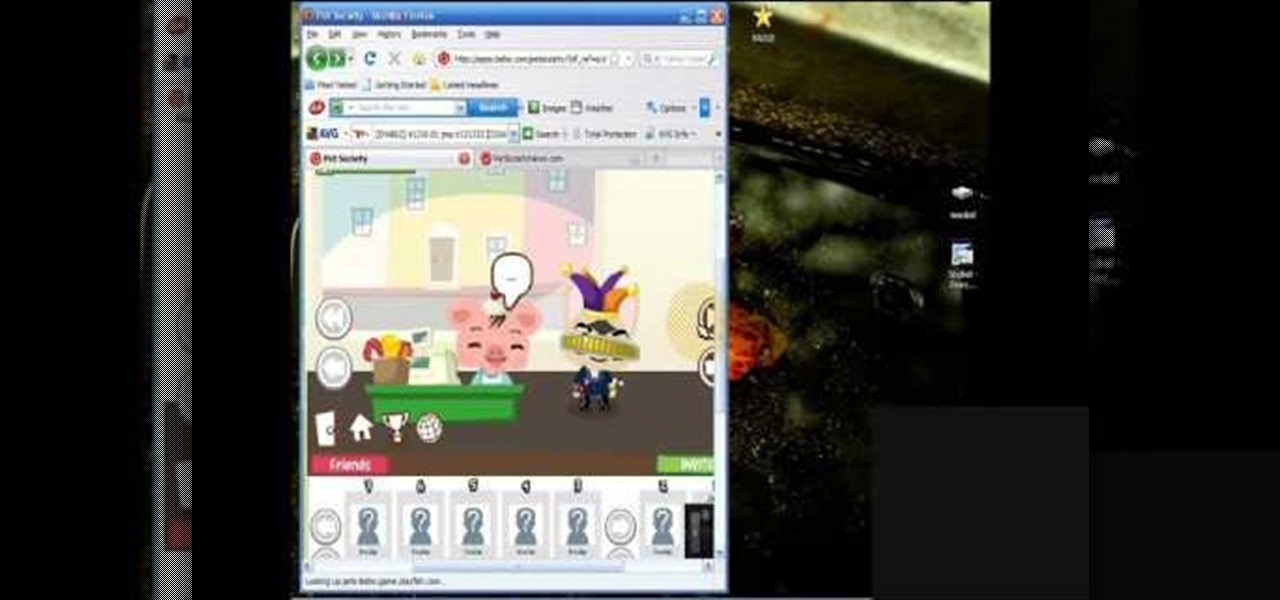
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack gold in Pet Society (09/29/09).

This game goes by a bunch of names: "fast and loose," "pricking the garter," "the endless chain," "the strap..." The object is simple: a chain is laid in a figure-eight configuration. One of the holes is the true center of the chain and will hold "fast," while the other will not hold, and is instead "loose". Follow along with this how-to video and learn how to perform the bar trick.

It's Magic 101. Can you mimic the master? This magic how-to video will show you the trick. Effect: Taking two matches from different matchbooks (one black, one brown), you cause them to visibly switch places...right under their eyes. It's demonic; it's the Quicksilver Matches.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

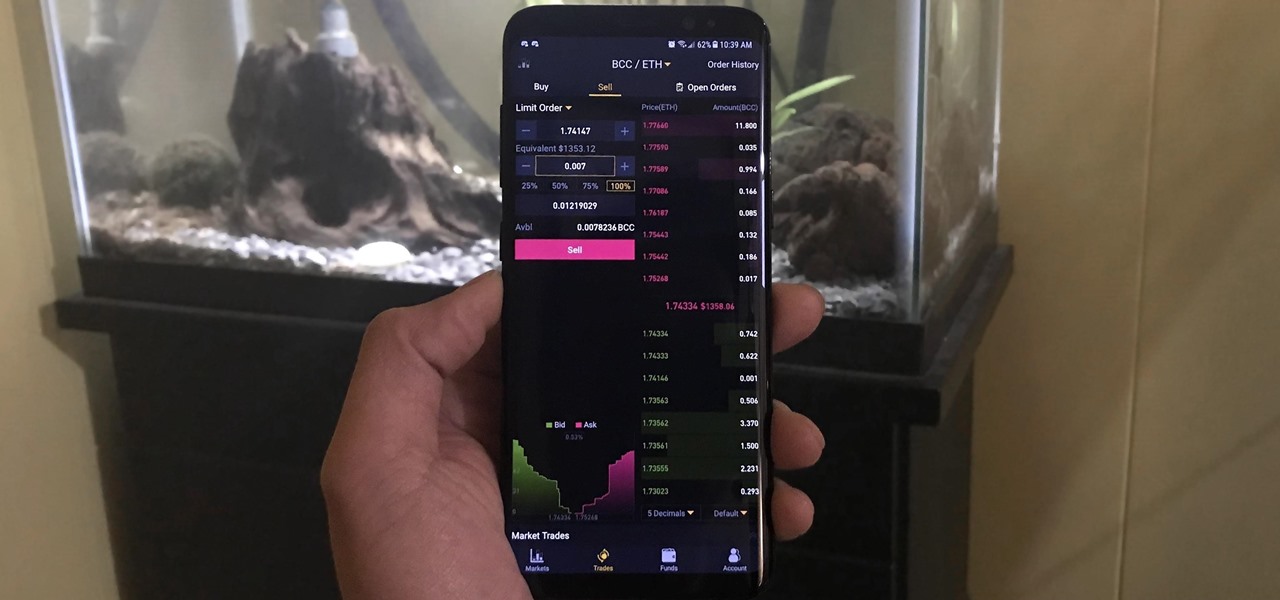
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

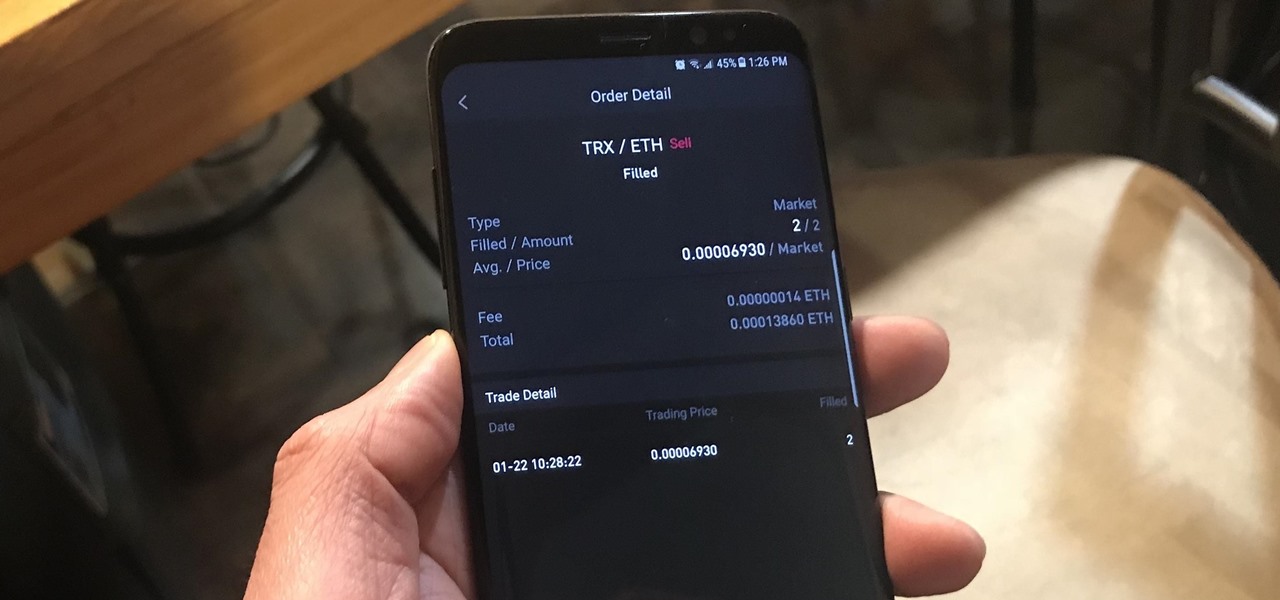
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.