
How To: Facebook Credentials Revisited
Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.


Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.
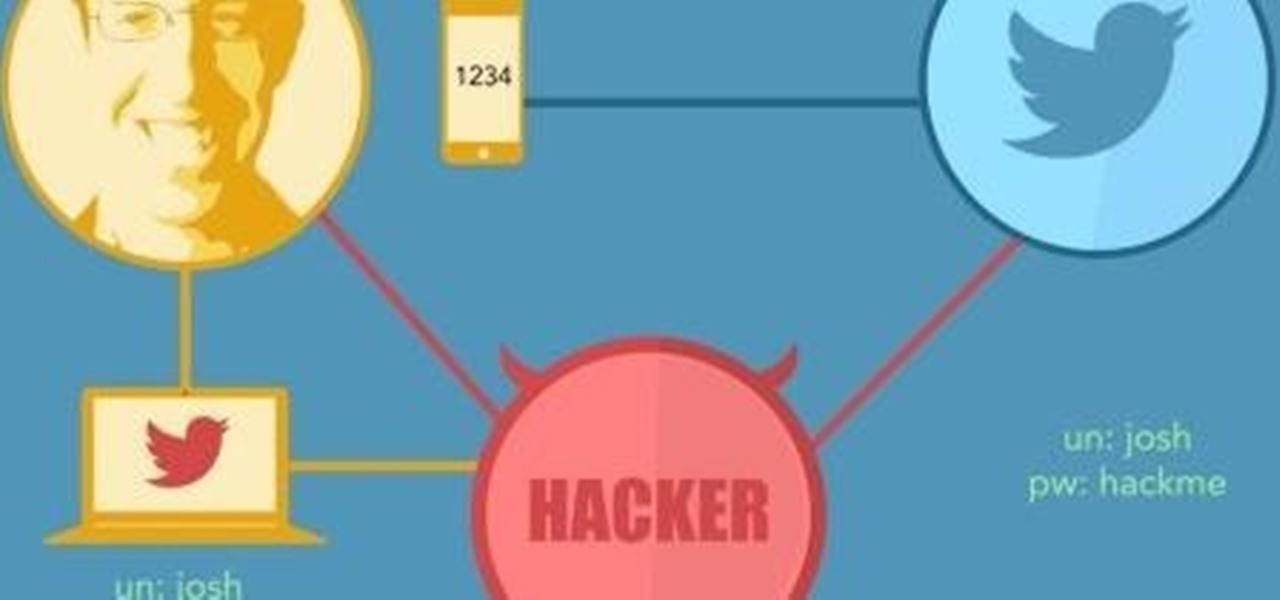
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.
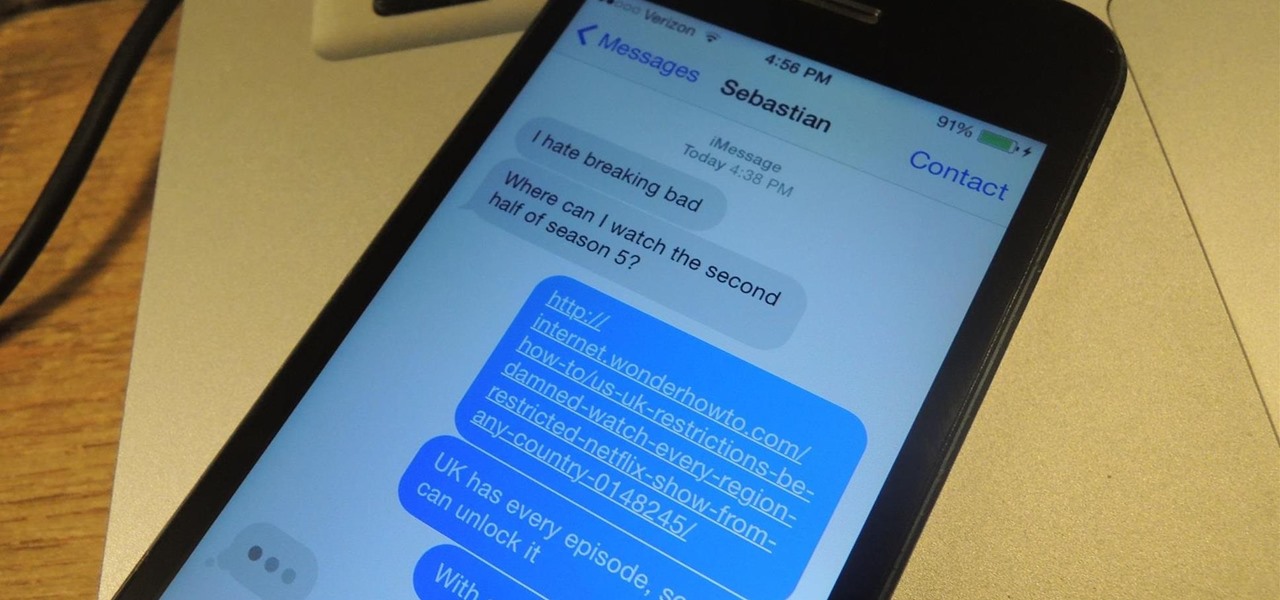
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

A blue hedgehog runs at high-speed through fantasy environments collecting rings. Sounds a bit loony, but I’m of course taking about the Sonic adventure series that was made popular on the Sega Genesis. The days of cartridge 16-bit gaming has long been eclipsed, but nostalgia can get the better of the old generation of gamers. Many of you probably don’t even own a working Genesis anymore, but don’t hop on eBay for a used console just yet!

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.
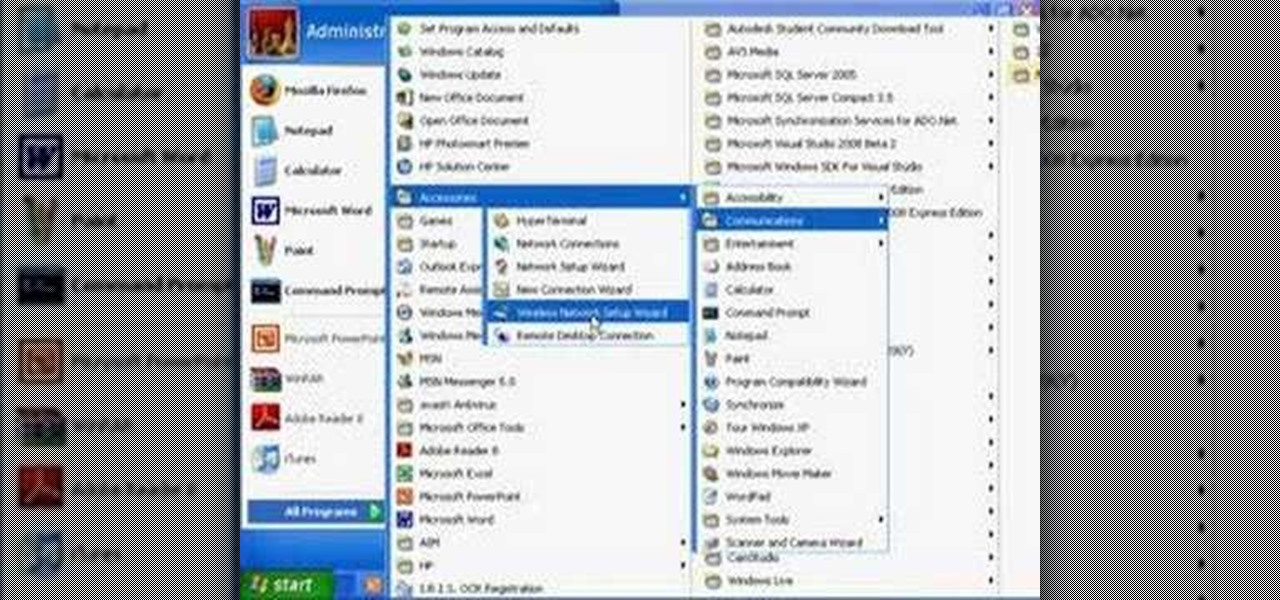
Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

Good makeup isn't when others notice you're wearing makeup, it's when they complement how beautiful you look today. You can enhance your own beauty by executing a couple tried and true makeup tricks. A little bit of makeup can go a long way.

Need a new way to impress your friends and family? Watch this video tutorial to learn how to solve the Rubik's Cube blindfolded. To solve the Rubiks Cube blindly, use the Pochmann Method. You really need to practice this method to get it down, because there are many things to keep in mind.

The diving hurdle approach and take off are important steps for executing proper diving technique. Learn some tips for diving the right way from a professional instructor in this free video series.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.
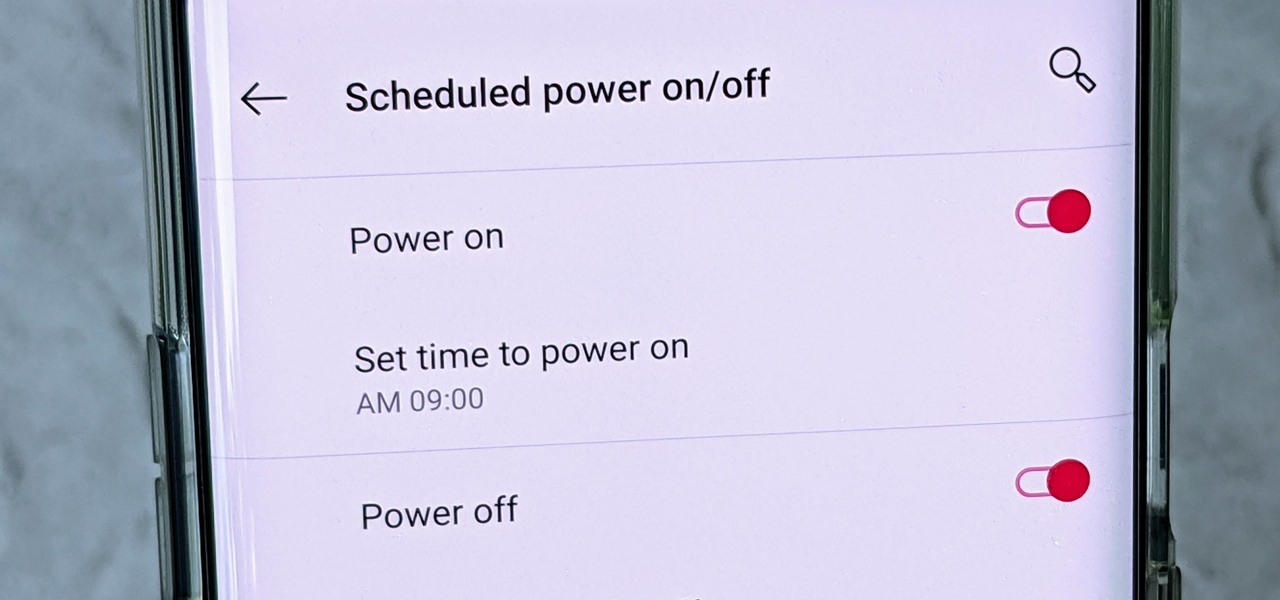
One of the more interesting power-related features for OnePlus phones is the ability to schedule a time to turn it, off then back on again. While OnePlus phones typically run blazingly fast, you can still benefit from the RAM clearing and process killing that a reboot provides. And since you can schedule this to happen overnight, you can wake up to a refreshed, restarted phone every morning.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

One of the most popular sports shows on television, Inside the NBA on TNT, gave viewers a tech-powered treat on Tuesday night by dropping them into a broadcast version of augmented reality.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

One of the biggest gripes I initially had with the LG G3 was the lack of options for the Shortcut keys, which are the volume keys that allow you to launch the camera or the QuickMemo+ app directly from the lock screen. I never use QuickMemo+, so having it as a shortcut was a complete waste of functionality.

Apple Watch doesn't include a multitasking feature like its iPhone companion, so there's no way to show active apps or swipe up to force-close one. Watch is an extension of the iPhone, not a replacement, so including a fully-functional multitasking feature seems impractical.
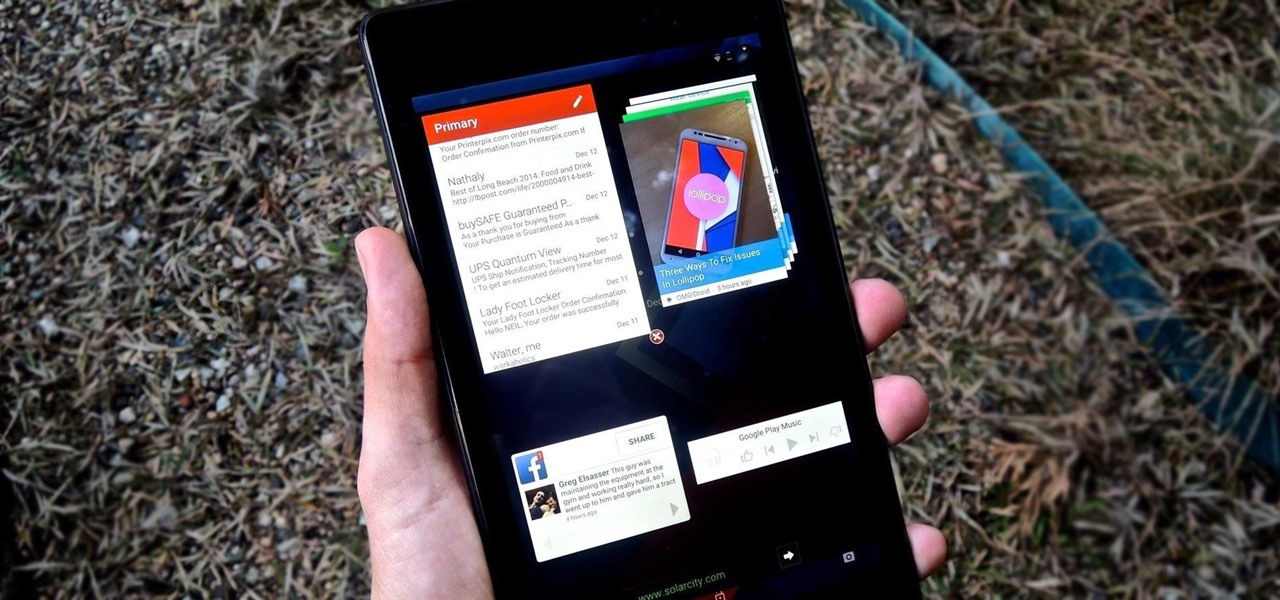
Being fixated on all of the great additions to Android 5.0 Lollipop, it can be a little difficult to take notice in the features that went missing. For instance, lock screen widgets. It's speculated that the lack of practical use for lock screen widgets and the implementation of the revamped Lollipop lock screen may have lead to their departure, but some of us want them back!
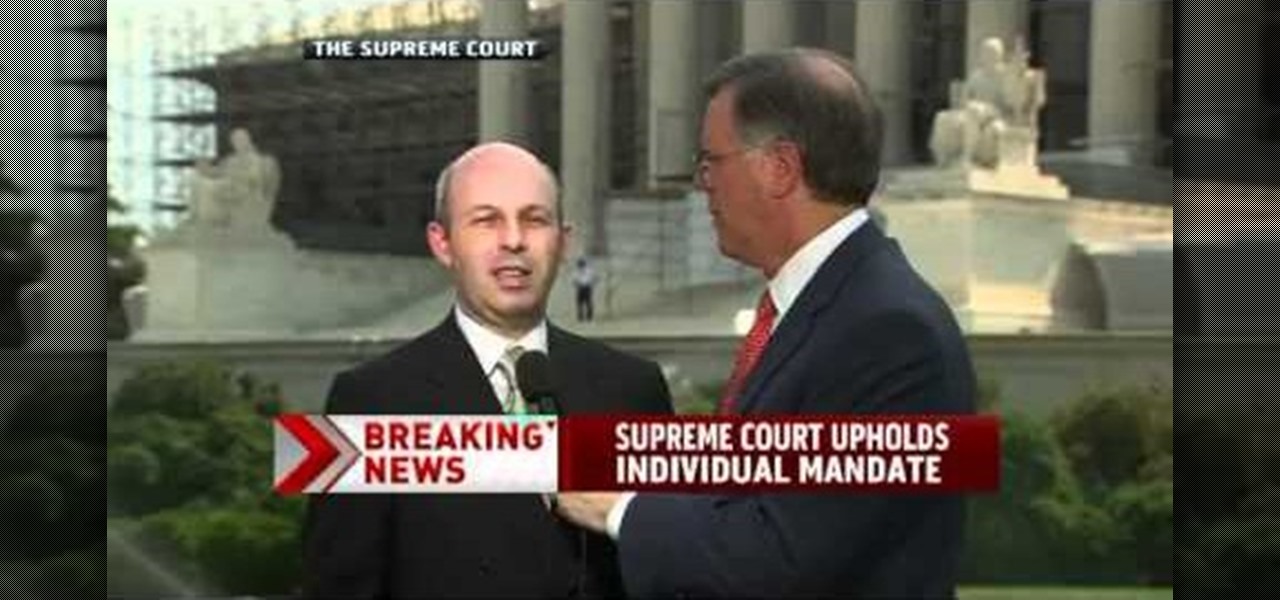
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.
Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

Master your tennis serve progressions. Be sure to click on all the video chapters to view the entire tutorial.

Improve your football game and your value to the team by memorizing and ready to execute your football playbook. Standard memorizing tools like flash cards and practice will help get you through any size playbook.
You won't even need Cheat Engine to execute some of these hacks. Take advantage of a few glitches in the game before they get patched, and earn way more xp and money than any of your friends who are playing!
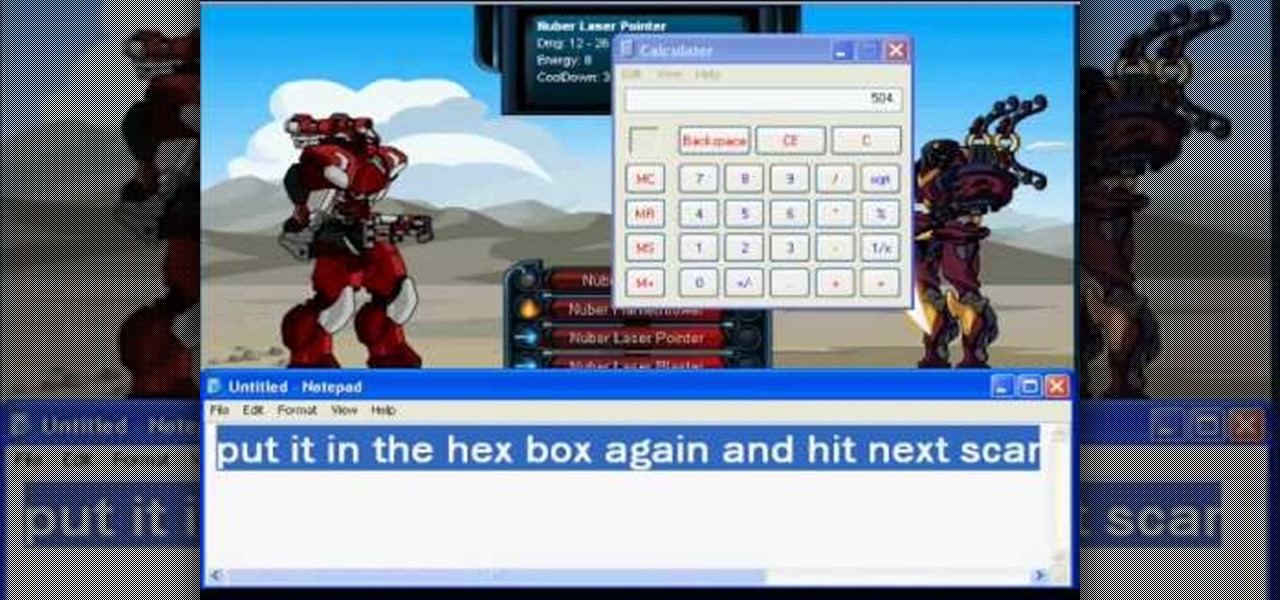
It doesn't matter how tough the monster is you're facing, you'll be able to take them down completely with just one hit! All you need is Cheat Engine (version 5.4 or 5.5) and a compatible browser to execute this hack.

Many tutorials show you how to use Cheat Engine to execute one function of one particular game - but not this one! This tutorial gives you a good understanding of what Cheat Engine can do, and how you can use it to hack nearly any game!

This tutorial shows you how to execute a speed hack when playing Roblox. All you need is the free game hacking program Cheat Engine. Open Roblox, then open Cheat Engine and use the following hack to change the speed of the game.

After you've mastered the basics of an extension, you can move on to the extended liberty cheerleading stunt. Join Matt Null (NCA/Cheer Excel/Millersville), Jhana, Dena, and Lauren (Fire and Ice Allstars), and Greg (Step 1 Allstars) as you learn step by step how to do an extended liberty.