In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

Learning Aikido techniques can be accomplished by practice and by doing basic Aikido exercises. Learn Aikido techniques and exercises to help you execute Aikido moves in this free video series.

Gaining inside position on an attacker will allow you to execute a variety of strikes, kicks, takedowns and other moves. Learn self defense from the outside position in this free video series from our martial arts instructor.

Expert Village is proud to present Shaolin Kung Fu Master Bruce Wen, who shares the secrets he learned after years under the instruction of Shaolin Monks. He shows you the meditation techniques you’ll need to discipline your mind to successfully execute Shaolin punches, block, kicks and more.

In this video recipe, our expert chef will demonstrate how to make rigatoni. In this cheap and hearty dinner recipe series, you will learn easy step-by-step instructions on how to prepare the vegetables and cook the sausage to add your rigatoni. You will also get tips and advice on how season the vegetables and pasta, how to serve your meal and even how to store the left overs. This is a great meal for a large gathering, and is sure to please the whole family.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

In this street magic and illusion revealed video series, learn how to do rope magic tricks. Our expert magician will show you how to do the one handed knot trick, the three ropes to one trick, how to cut a rope in half and restore it, the ring and rope trick, and more. Get tips and pointers for executing these simple tricks for friends and strangers alike. Learn to astound and amaze…but first practice, practice, practice.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

Everyone raves about Gboard and SwiftKey, but the stock Samsung Keyboard on Galaxy devices is awesome in its own right. It's preloaded, so you don't have to do anything to get it, but at the same time, it's packed with features — even some you might not know about.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

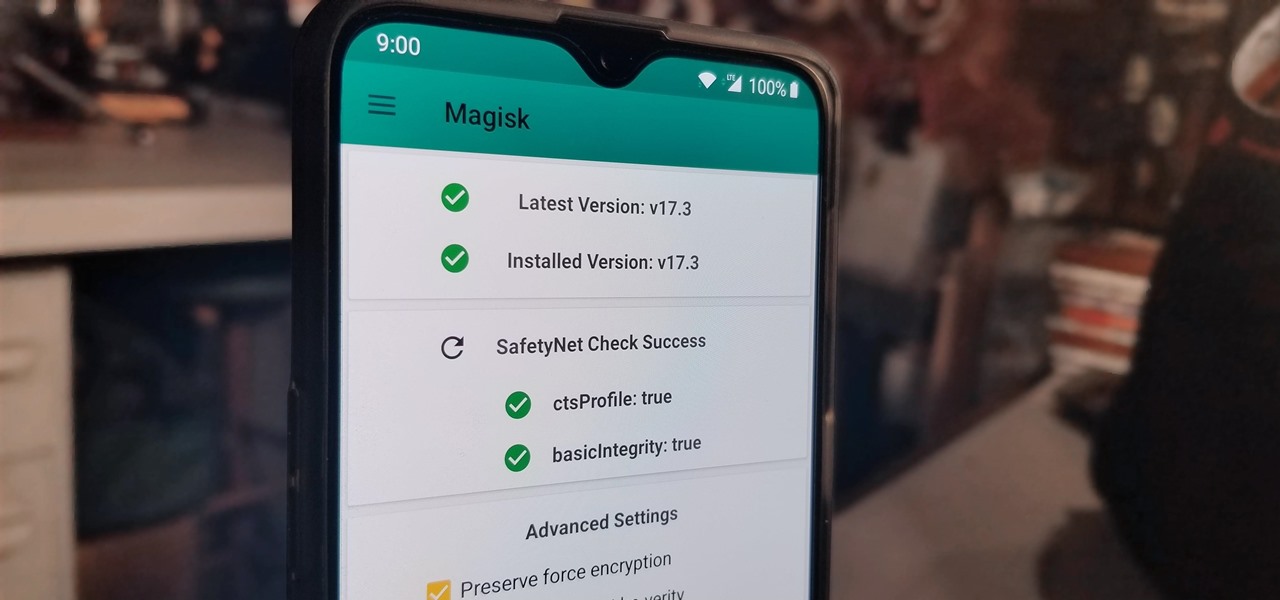
The Pixel 4 is one of the most talked-about phones of 2019, and it has many things going for it, especially in the world of rooting and modding. Just as with previous Pixel generations, unlocking the bootloader is the gateway to realizing your device's true potential. It can make way for such things as TWRP, Magisk, custom ROMs, and many other device-specific mods just the same.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Instagram has extensive tools built in for creating and editing posts and Stories, but there could always be more. Third-party apps can help you add photo and video effects for even more visually stimulating content, as well as create announcements, text-based images, and everything in between. However, now that Shortcuts exists on iOS, you may no longer need all those extra apps on your iPhone.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

When you set up your MyFitnessPal account for the first time, it asks for a checklist of personal info to create nutrition and fitness goals for you. Whatever you decide then, it's important to know that the goals provided to you are not fixed. If your doctor or nutritionist recommends a new plan, or you simply want to change up your routine, you can customize your weekly and daily goals.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.