A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

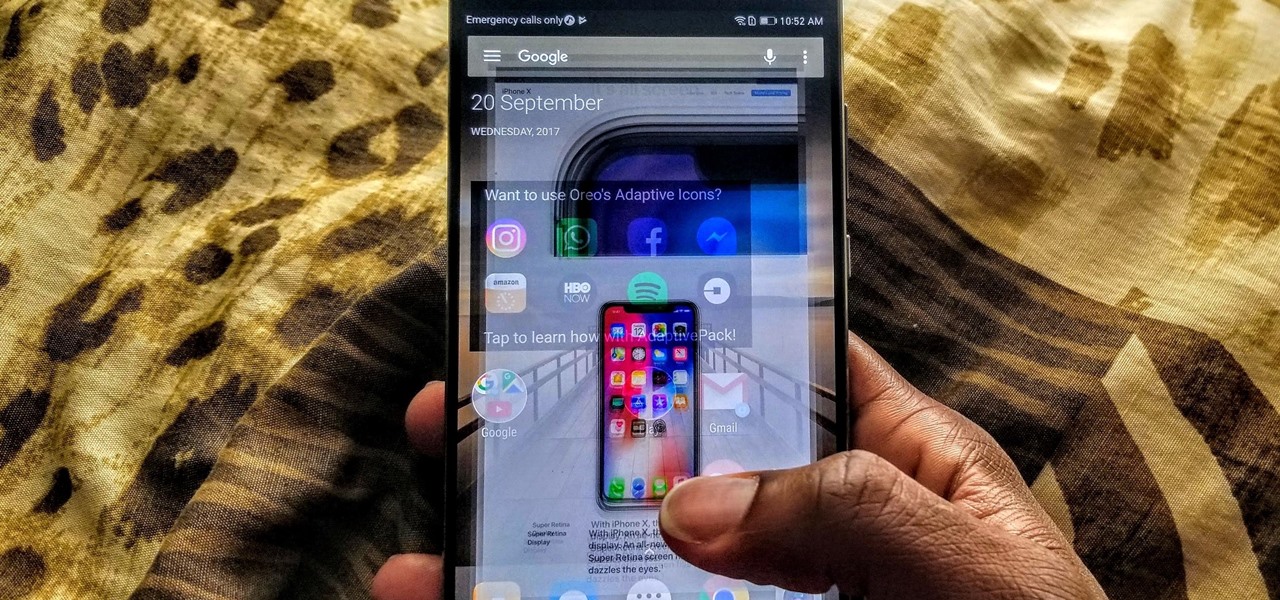
With the new iPhone X, Apple introduced a buttonless design for the first time. But without a home button, navigation within iOS 11 had to change to accommodate the new model. To solve this issue, Apple created gestures to perform the actions that the home button once executed. But while Apple users have to wait until November 3 to use these gestures, you can get these features right now on Android.

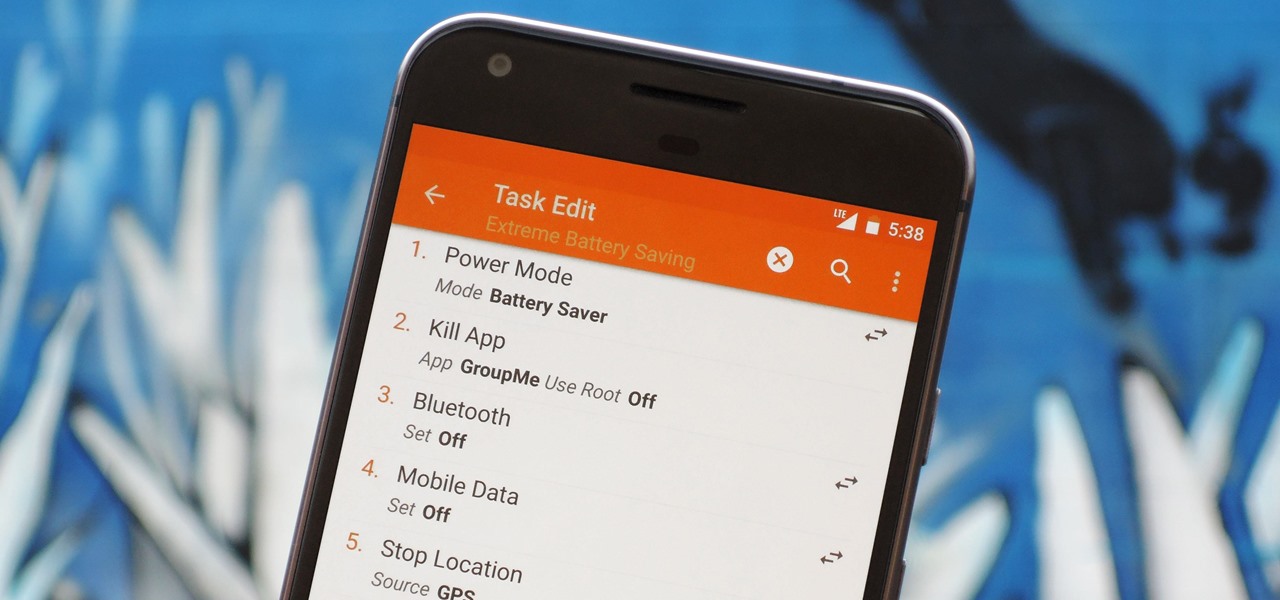
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.

On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is great news for the power users out there.

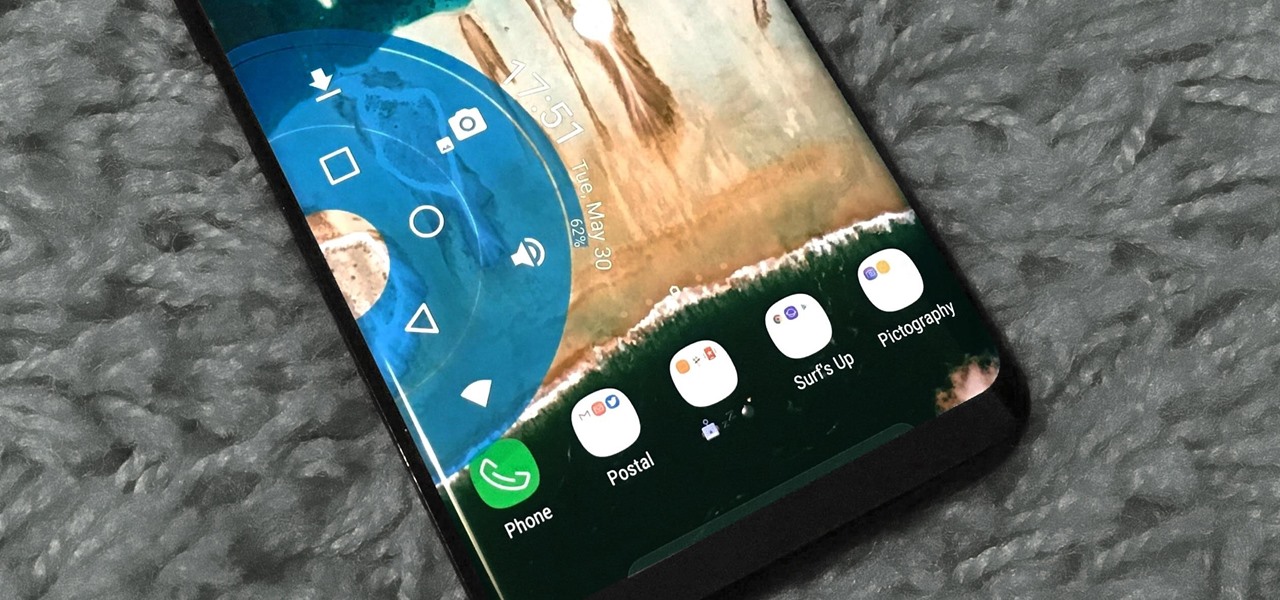
The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

One thing you'll find a lot of in the Windows Store for HoloLens is demos and mockups, but very few projects are as fully realized and fully-functioning as Muralize. Created by Magnopus, an all-female development team, Muralize first appeared in the Windows Store in late-November of 2016, and makes it easy and fun to create real-life murals using a HoloLens.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

Chris' Outrageous Cheesecake, a decedent combination of chocolate cake, brownies, cheesecake, and coconut-pecan frosting, is easily one of The Cheesecake Factory's most popular desserts. But, the price of fulfilling your cravings for this addictive treat can get up there (at about $8 a slice), and when you eat it at the restaurant you likely are limited to only one small piece.

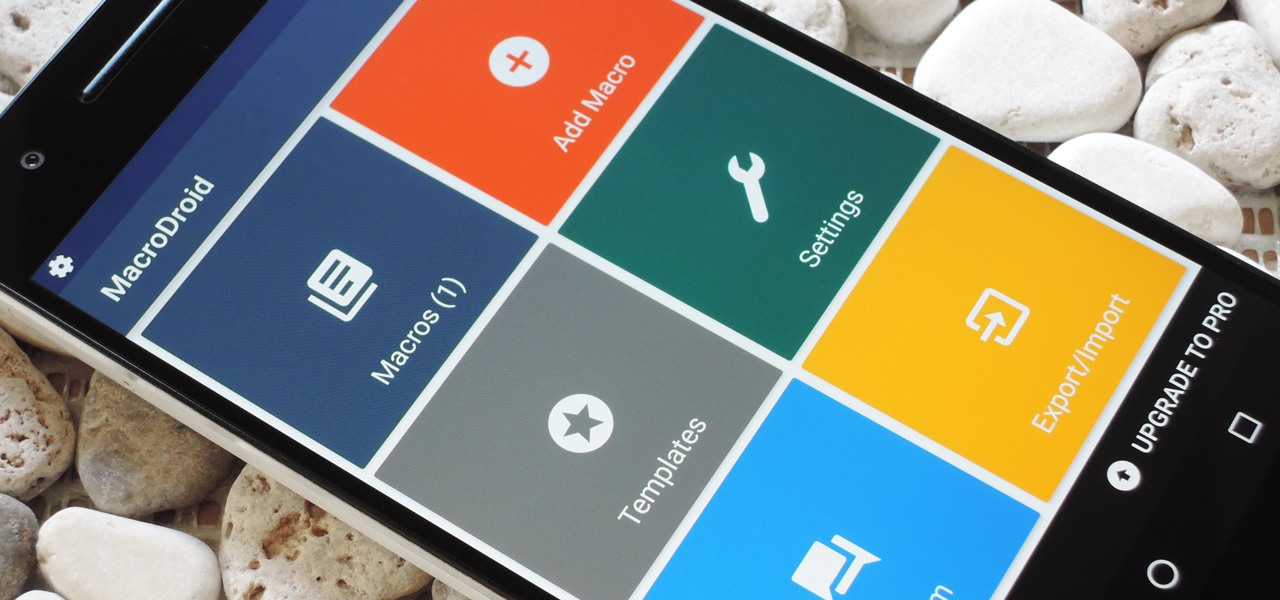
When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step in with a Tasker alternative.

The potato masher is one of the most dreaded tools in my kitchen; it always gives me flashbacks to when I had to mash potatoes for Thanksgiving dinners while growing up.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

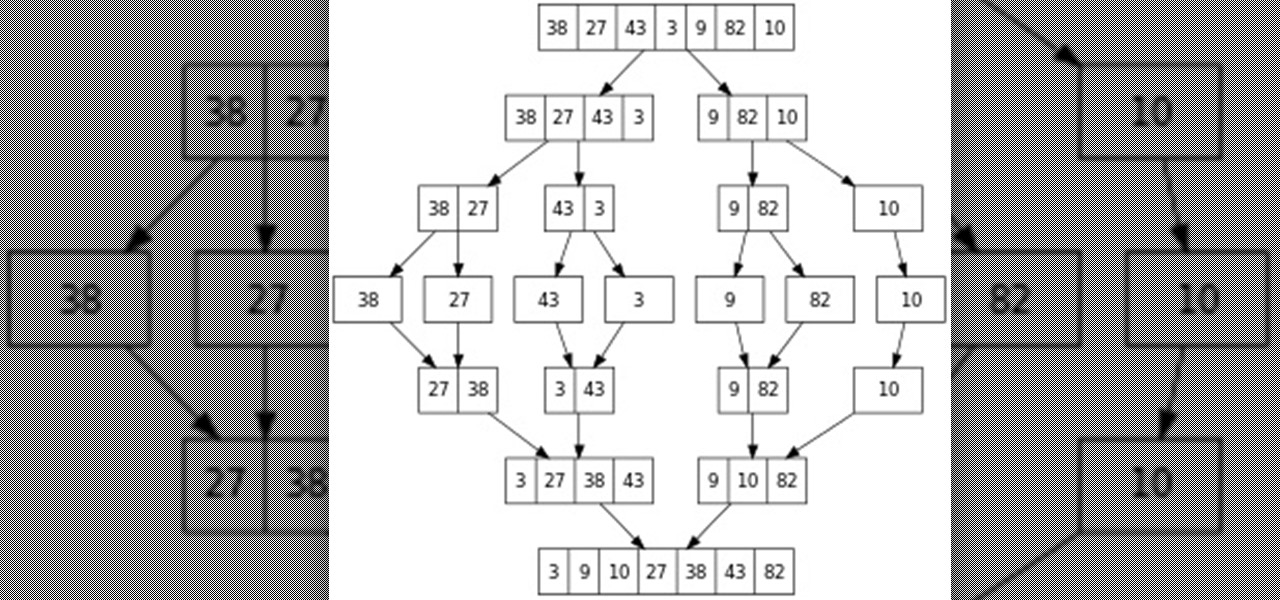
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!
Hey everyone. Only found the site a few days ago but really loving it. Been

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

The first time I encountered a deviled egg, the name freaked me out. Why was it called a deviled egg? Was it the spawn of some demonic chicken? If I ate it, would my soul be at risk?

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!